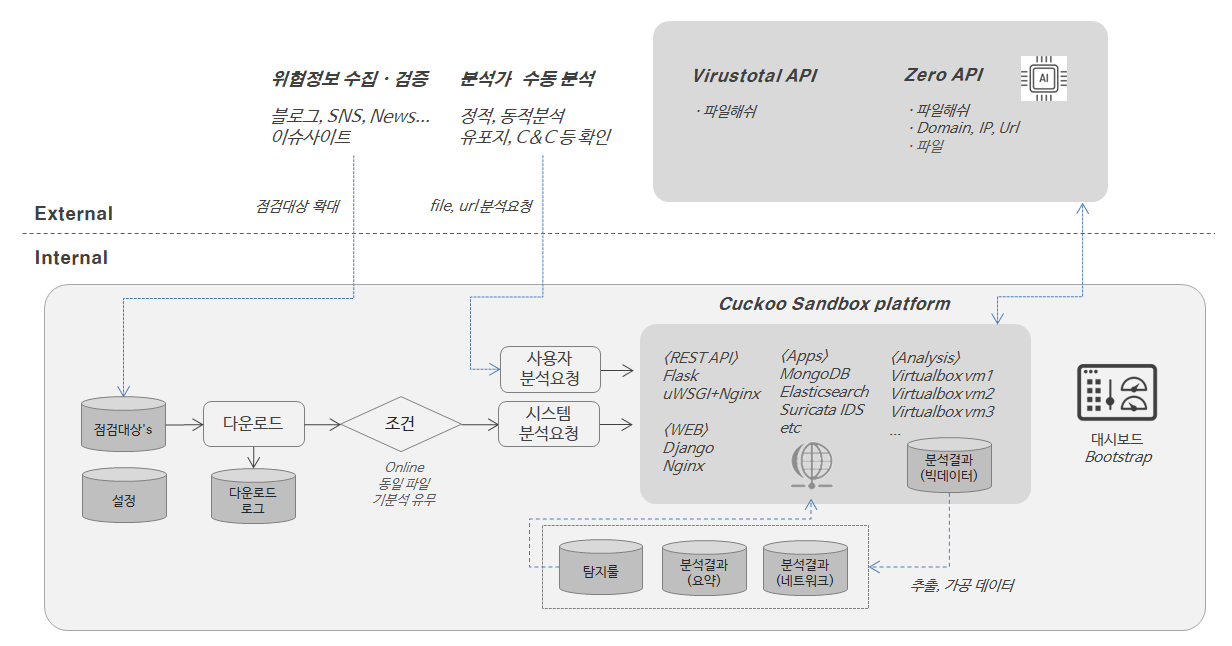
Guide - ZeroBOX
CTI Platform

Dashboard
| Menu | Description |
|---|---|
| Dashboard | Detection information in the last 30 days |
| Analysis | Checklist and user request analysis result |
| System info | System status information |
Web Scan
| Menu | Description |
|---|---|
| Web Scan | Website Threat Scanner |
User Upload
| Menu | Description |
|---|---|
| User Upload | User Upload(File, Urls) Analysis |
Report
| Menu | Description |
|---|---|
| Checklist (*) | Monitoring website analysis results |
| User | User Upload(File, Urls) Analysis Results |
| Detection (*) | Rule detection results |
| Suspicious (*) | Suspicious rule-based detection results |
Data Analysis
| Menu | Description |
|---|---|
| MAP | Cyber Threat Map (Map, Radar, XY) |
| Circle | Cyber Threat Map (Country ↔ ISP ↔ IP) |
Boards
| Menu | Description |
|---|---|
| Notice (*) | Notice, detection, and system failure information |
| News | Threat information trend collection (News, Trend) |
| Tweet | Threat information trend collection (Tweet) |
| Document | Help |
Manage (*)
| Menu | Description |
|---|---|
| Checklist | Monitoring website management |
| Rules | Detection rule management (IoC, Yara) |
| Whitelist | Whitelist management (URL, IP, Domain) |
| News list | Trend collection site management |
| User | User information management |
| Config | Manage system preferences |
Tools
| Menu | Description |
|---|---|
| Whois | Whois (similar phishing domain or distribution history check) |
| Decoder | Decrypt obfuscated code |
| Check | Domain, IP, Url, Hash or file check |
| Scan | IP, Fake DNS, Vulnerability scan(to be developed) |
| View | Site source view |