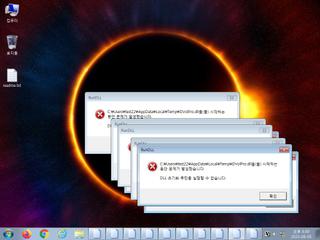
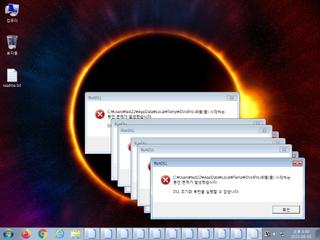
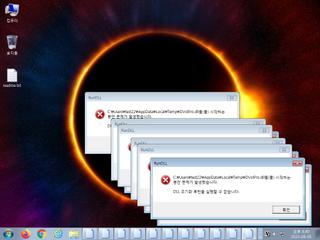
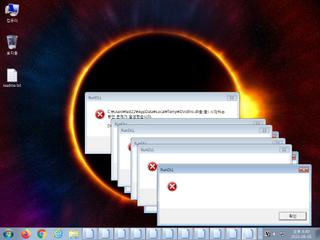
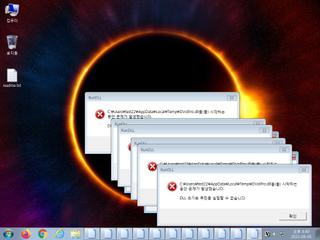
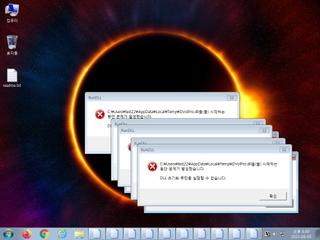
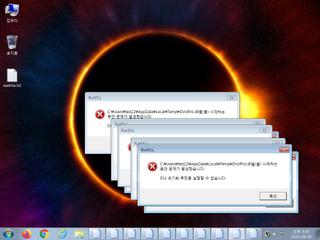
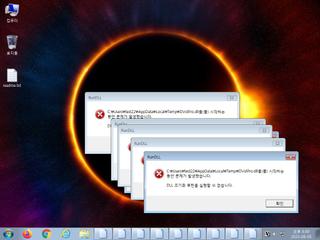
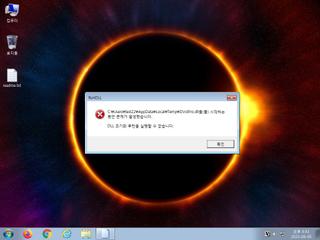
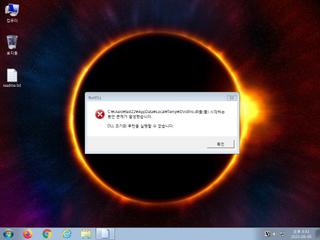
ScreenShot
| Created | 2023.06.05 16:43 | Machine | s1_win7_x6402 |
| Filename | DVolPro.dll | ||
| Type | PE32 executable (DLL) (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 36 detected (malicious, high confidence, GenericKD, Artemis, Vku9, VMProtect, ZedlaF, @aW8tn2pi, ABRisk, BJTL, Attribute, HighConfidence, Generic@AI, RDML, 8DA6E998ht54ldGUo3Pn6g, ai score=84, Detected, unsafe, RnkBend, R002H09EH23, susgen) | ||
| md5 | 30e1d0c1941167612a1da0bb79a03be8 | ||
| sha256 | 01fd9d0fefc8a123f59347eb48de14336d641b22440ba20b6724f506b0a892ad | ||
| ssdeep | 196608:MqwXvaXu8N9GEFH20R85wLIhiNz6aWSzJUovW:6AH2I8czN+tSzJxW | ||
| imphash | 6b3259bfd5a1809cf0bcb645c8a4a5f7 | ||
| impfuzzy | 12:v8FjQ5kBZGoQtXJxZGb9AJcDfA5kLfP9m:voQ58QtXJHc9NDI5Q8 | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 36 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
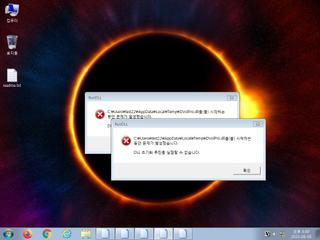
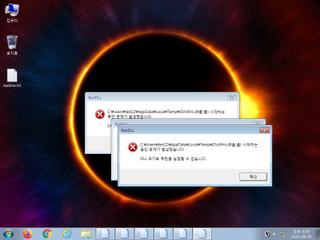
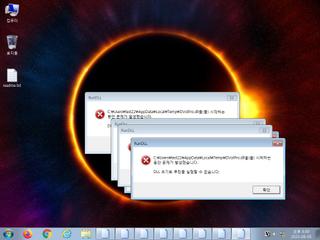
| info | One or more processes crashed |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | This executable has a PDB path |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x107ae000 GetVersionExW
USER32.dll
0x107ae008 CharUpperW
ADVAPI32.dll
0x107ae010 SetFileSecurityW
WTSAPI32.dll
0x107ae018 WTSSendMessageW
KERNEL32.dll
0x107ae020 VirtualQuery
USER32.dll
0x107ae028 GetProcessWindowStation
KERNEL32.dll
0x107ae030 LocalAlloc
0x107ae034 LocalFree
0x107ae038 GetModuleFileNameW
0x107ae03c GetProcessAffinityMask
0x107ae040 SetProcessAffinityMask
0x107ae044 SetThreadAffinityMask
0x107ae048 Sleep
0x107ae04c ExitProcess
0x107ae050 FreeLibrary
0x107ae054 LoadLibraryA
0x107ae058 GetModuleHandleA
0x107ae05c GetProcAddress
USER32.dll
0x107ae064 GetProcessWindowStation
0x107ae068 GetUserObjectInformationW
EAT(Export Address Table) Library
0x10009350 RARGetDllVersion
0x1000a110 RAROpenArchive
0x10009d60 RAROpenArchiveEx
0x100096c0 RARProcessFile
0x100096e0 RARProcessFileW
0x10009c40 RARReadHeader
0x100097e0 RARReadHeaderEx
0x10009290 RARSetCallback
0x10009270 RARSetChangeVolProc
0x100092d0 RARSetPassword
0x100092b0 RARSetProcessDataProc
0x10009bf0 VolPro
KERNEL32.dll
0x107ae000 GetVersionExW
USER32.dll
0x107ae008 CharUpperW
ADVAPI32.dll
0x107ae010 SetFileSecurityW
WTSAPI32.dll
0x107ae018 WTSSendMessageW
KERNEL32.dll
0x107ae020 VirtualQuery
USER32.dll
0x107ae028 GetProcessWindowStation
KERNEL32.dll
0x107ae030 LocalAlloc
0x107ae034 LocalFree
0x107ae038 GetModuleFileNameW
0x107ae03c GetProcessAffinityMask
0x107ae040 SetProcessAffinityMask
0x107ae044 SetThreadAffinityMask
0x107ae048 Sleep
0x107ae04c ExitProcess
0x107ae050 FreeLibrary
0x107ae054 LoadLibraryA
0x107ae058 GetModuleHandleA
0x107ae05c GetProcAddress
USER32.dll
0x107ae064 GetProcessWindowStation
0x107ae068 GetUserObjectInformationW
EAT(Export Address Table) Library
0x10009350 RARGetDllVersion
0x1000a110 RAROpenArchive
0x10009d60 RAROpenArchiveEx
0x100096c0 RARProcessFile
0x100096e0 RARProcessFileW
0x10009c40 RARReadHeader
0x100097e0 RARReadHeaderEx
0x10009290 RARSetCallback
0x10009270 RARSetChangeVolProc
0x100092d0 RARSetPassword
0x100092b0 RARSetProcessDataProc
0x10009bf0 VolPro