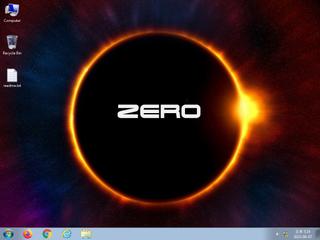
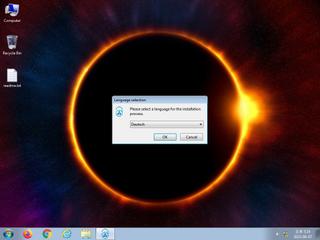
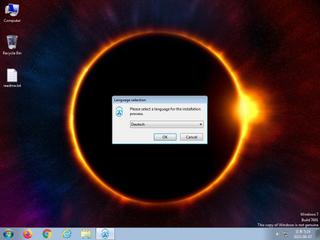
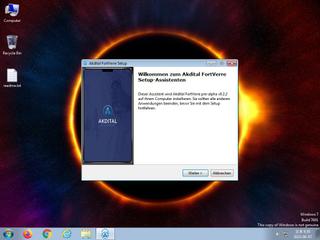
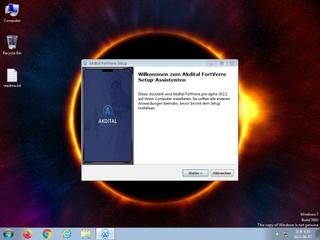
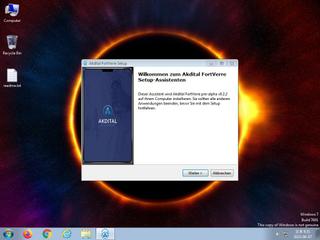
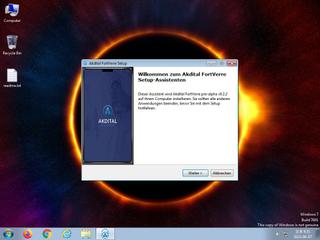
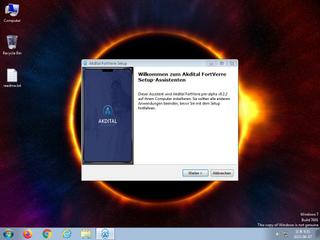
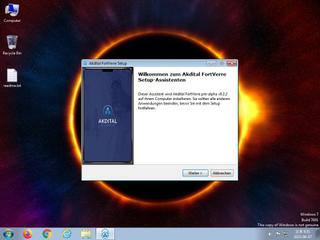
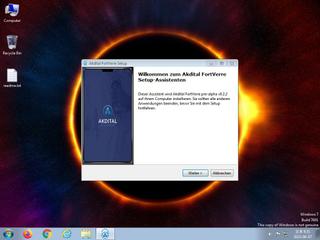
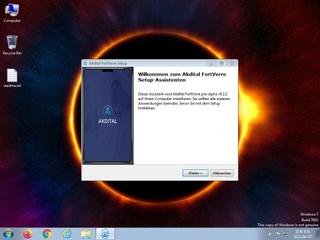
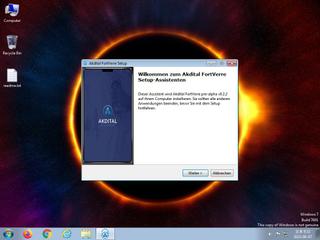
ScreenShot
| Created | 2023.06.07 17:32 | Machine | s1_win7_x6403 |
| Filename | 2d7f71dfd2399ffc78575f12b3d751fae218432618e41204ce0e9b850e25e9ac | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 19 detected (AIDetectMalware, HiddenTears, malicious, ZexaF, @x3@aGBovDii, score, Artemis, ai score=85, rexp, R002H09F223, PossibleThreat) | ||
| md5 | af1a989a2a9bd61b087cace076971f6a | ||
| sha256 | 0def45e69bd0b77b0448d57bbf6213b66a90b0b8855378271b5111d5cbdf16ee | ||
| ssdeep | 196608:HVkn9JCZxrIYF4hSeOMYjeYMeJyKpJoiSsD4RFsV4:ynOsYFs4MMbJVVSV | ||
| imphash | ad9d11227a86b863e31ddf6019cc7ab5 | ||
| impfuzzy | 96:Sw8qOTnBqZLao5FqircZmmcpF1sHx0aIH7AAJXEs0hhKSi9b:SaOrBqZbFqiKmoHRIkAJXEs0SSi9b | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| watch | File has been identified by 19 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | The executable uses a known packer |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | bmp_file_format | bmp file format | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
MSVCRT.dll
0x4c3340 memset
0x4c3344 system
0x4c3348 memcpy
0x4c334c _wfopen
0x4c3350 fseek
0x4c3354 fclose
0x4c3358 wcsncpy
0x4c335c wcslen
0x4c3360 wcscpy
0x4c3364 wcscat
0x4c3368 wcscmp
0x4c336c memmove
0x4c3370 memcmp
0x4c3374 _stricmp
0x4c3378 sscanf
0x4c337c atoi
0x4c3380 strlen
0x4c3384 strcpy
0x4c3388 strcat
0x4c338c sprintf
0x4c3390 malloc
0x4c3394 free
0x4c3398 _wstat
0x4c339c _wcsdup
0x4c33a0 strcmp
0x4c33a4 floor
0x4c33a8 ceil
0x4c33ac _CIpow
0x4c33b0 _isnan
0x4c33b4 _finite
0x4c33b8 fread
0x4c33bc longjmp
0x4c33c0 _setjmp3
0x4c33c4 ftell
0x4c33c8 wcsncmp
0x4c33cc _snwprintf
0x4c33d0 _wcsicmp
0x4c33d4 tolower
0x4c33d8 localtime
0x4c33dc mktime
0x4c33e0 _wcsnicmp
0x4c33e4 _itow
0x4c33e8 gmtime
0x4c33ec fabs
0x4c33f0 pow
0x4c33f4 ??3@YAXPAX@Z
0x4c33f8 wcsstr
0x4c33fc calloc
0x4c3400 _errno
0x4c3404 strrchr
0x4c3408 strchr
0x4c340c strncpy
0x4c3410 memchr
0x4c3414 _lseeki64
0x4c3418 realloc
0x4c341c abort
0x4c3420 _close
0x4c3424 _wopen
0x4c3428 _setmode
0x4c342c exit
0x4c3430 _open_osfhandle
0x4c3434 _strdup
0x4c3438 _snprintf
0x4c343c setlocale
0x4c3440 strncmp
0x4c3444 wctomb
0x4c3448 _get_osfhandle
0x4c344c _open
0x4c3450 toupper
0x4c3454 wcschr
0x4c3458 mbstowcs
0x4c345c frexp
0x4c3460 modf
0x4c3464 fopen
0x4c3468 strerror
0x4c346c atof
0x4c3470 abs
0x4c3474 fflush
0x4c3478 fwrite
0x4c347c __p__iob
0x4c3480 fprintf
0x4c3484 getenv
0x4c3488 _stati64
0x4c348c time
0x4c3490 _ftime
0x4c3494 _vsnwprintf
0x4c3498 cos
0x4c349c fmod
0x4c34a0 sin
KERNEL32.dll
0x4c34a8 GetModuleHandleW
0x4c34ac HeapCreate
0x4c34b0 HeapDestroy
0x4c34b4 ExitProcess
0x4c34b8 GetDiskFreeSpaceExW
0x4c34bc GetCurrentProcess
0x4c34c0 GetLastError
0x4c34c4 GetUserDefaultLangID
0x4c34c8 GetSystemInfo
0x4c34cc ExpandEnvironmentStringsW
0x4c34d0 FormatMessageW
0x4c34d4 LocalFree
0x4c34d8 OutputDebugStringW
0x4c34dc LoadLibraryW
0x4c34e0 FindResourceW
0x4c34e4 FreeLibrary
0x4c34e8 LoadResource
0x4c34ec SizeofResource
0x4c34f0 LockResource
0x4c34f4 CreateMutexW
0x4c34f8 CloseHandle
0x4c34fc BeginUpdateResourceW
0x4c3500 EndUpdateResourceW
0x4c3504 GetBinaryTypeW
0x4c3508 UpdateResourceW
0x4c350c EnterCriticalSection
0x4c3510 LeaveCriticalSection
0x4c3514 InitializeCriticalSection
0x4c3518 WaitForSingleObject
0x4c351c CreateThread
0x4c3520 HeapAlloc
0x4c3524 HeapFree
0x4c3528 Sleep
0x4c352c CreateFileW
0x4c3530 GetFileSize
0x4c3534 ReadFile
0x4c3538 GetProcAddress
0x4c353c GetCurrentProcessId
0x4c3540 GetCurrentThreadId
0x4c3544 GetEnvironmentVariableW
0x4c3548 SetEnvironmentVariableW
0x4c354c DuplicateHandle
0x4c3550 CreatePipe
0x4c3554 GetStdHandle
0x4c3558 CreateProcessW
0x4c355c GetModuleFileNameW
0x4c3560 GetProfileStringW
0x4c3564 SetFilePointer
0x4c3568 WideCharToMultiByte
0x4c356c MultiByteToWideChar
0x4c3570 SetEndOfFile
0x4c3574 WriteFile
0x4c3578 DeleteFileW
0x4c357c HeapReAlloc
0x4c3580 GetVersionExW
0x4c3584 SetLastError
0x4c3588 CopyFileW
0x4c358c FindFirstFileW
0x4c3590 FindNextFileW
0x4c3594 FindClose
0x4c3598 SetFileAttributesW
0x4c359c RemoveDirectoryW
0x4c35a0 GetDriveTypeW
0x4c35a4 GetFileAttributesW
0x4c35a8 GetTempPathW
0x4c35ac MulDiv
0x4c35b0 GetLocalTime
0x4c35b4 TlsAlloc
0x4c35b8 TlsSetValue
0x4c35bc TlsGetValue
0x4c35c0 GlobalFree
0x4c35c4 GlobalAlloc
0x4c35c8 HeapSize
0x4c35cc TlsFree
0x4c35d0 DeleteCriticalSection
0x4c35d4 InterlockedCompareExchange
0x4c35d8 InterlockedExchange
0x4c35dc VirtualAlloc
0x4c35e0 VirtualFree
0x4c35e4 IsValidCodePage
0x4c35e8 GetACP
0x4c35ec GetOEMCP
0x4c35f0 GetFileType
0x4c35f4 PeekNamedPipe
0x4c35f8 GetFileInformationByHandle
0x4c35fc GetFileAttributesA
0x4c3600 CreateFileA
0x4c3604 GetExitCodeProcess
0x4c3608 GetFullPathNameW
0x4c360c UnregisterWait
0x4c3610 GetCurrentThread
0x4c3614 RegisterWaitForSingleObject
gdiplus.dll
0x4c361c GdipDeleteFont
0x4c3620 GdipDeleteGraphics
0x4c3624 GdipDeletePath
0x4c3628 GdipDeleteMatrix
0x4c362c GdipDeletePen
0x4c3630 GdipDeleteStringFormat
0x4c3634 GdipFree
0x4c3638 GdipGetDpiX
0x4c363c GdipGetDpiY
USER32.DLL
0x4c3644 IsWindowEnabled
0x4c3648 IsWindowVisible
0x4c364c ExitWindowsEx
0x4c3650 GetActiveWindow
0x4c3654 SendMessageW
0x4c3658 GetWindowTextLengthW
0x4c365c GetSysColor
0x4c3660 SetRect
0x4c3664 GetWindowLongW
0x4c3668 RedrawWindow
0x4c366c GetDlgCtrlID
0x4c3670 GetWindowTextW
0x4c3674 ShowWindow
0x4c3678 SetForegroundWindow
0x4c367c SetWindowLongW
0x4c3680 UpdateLayeredWindow
0x4c3684 DestroyIcon
0x4c3688 EnumWindows
0x4c368c MessageBoxW
0x4c3690 PostMessageW
0x4c3694 GetForegroundWindow
0x4c3698 GetWindowThreadProcessId
0x4c369c EnableWindow
0x4c36a0 SetWindowPos
0x4c36a4 DestroyWindow
0x4c36a8 SystemParametersInfoW
0x4c36ac SetFocus
0x4c36b0 GetFocus
0x4c36b4 GetParent
0x4c36b8 GetClassNameW
0x4c36bc SetWindowTextW
0x4c36c0 CallWindowProcW
0x4c36c4 RemovePropW
0x4c36c8 GetWindowRect
0x4c36cc GetPropW
0x4c36d0 CreateWindowExW
0x4c36d4 SetPropW
0x4c36d8 SetScrollPos
0x4c36dc GetDC
0x4c36e0 InflateRect
0x4c36e4 ReleaseDC
0x4c36e8 GetWindowDC
0x4c36ec MapWindowPoints
0x4c36f0 MoveWindow
0x4c36f4 InvalidateRect
0x4c36f8 GetIconInfo
0x4c36fc UpdateWindow
0x4c3700 ReleaseCapture
0x4c3704 BeginPaint
0x4c3708 DrawStateW
0x4c370c EndPaint
0x4c3710 SetCapture
0x4c3714 ScreenToClient
0x4c3718 GetSystemMetrics
0x4c371c GetSysColorBrush
0x4c3720 DrawTextW
0x4c3724 GetWindow
0x4c3728 ValidateRect
0x4c372c ClientToScreen
0x4c3730 GetClientRect
0x4c3734 FillRect
0x4c3738 DefWindowProcW
0x4c373c LoadCursorW
0x4c3740 RegisterClassExW
0x4c3744 SetClassLongW
0x4c3748 EnumPropsExW
0x4c374c SetActiveWindow
0x4c3750 LoadIconW
0x4c3754 IsZoomed
0x4c3758 IsIconic
0x4c375c PeekMessageW
0x4c3760 MsgWaitForMultipleObjects
0x4c3764 GetMessageW
0x4c3768 TranslateAcceleratorW
0x4c376c TranslateMessage
0x4c3770 DispatchMessageW
0x4c3774 RegisterClassW
0x4c3778 AdjustWindowRectEx
0x4c377c CreateAcceleratorTableW
0x4c3780 UnregisterClassW
0x4c3784 DestroyAcceleratorTable
0x4c3788 GetMenu
0x4c378c SetTimer
0x4c3790 KillTimer
0x4c3794 DefFrameProcW
0x4c3798 EnumChildWindows
0x4c379c GetKeyState
0x4c37a0 IsChild
0x4c37a4 RegisterWindowMessageW
0x4c37a8 CreateIconFromResourceEx
0x4c37ac CreateIconFromResource
0x4c37b0 CharLowerW
0x4c37b4 DrawIconEx
GDI32.DLL
0x4c37bc StartDocW
0x4c37c0 GetMapMode
0x4c37c4 SetMapMode
0x4c37c8 GetDeviceCaps
0x4c37cc DPtoLP
0x4c37d0 StartPage
0x4c37d4 EndPage
0x4c37d8 EndDoc
0x4c37dc SetBkColor
0x4c37e0 CreateDCW
0x4c37e4 DeleteObject
0x4c37e8 GetStockObject
0x4c37ec CreateFontIndirectW
0x4c37f0 ExcludeClipRect
0x4c37f4 GetObjectType
0x4c37f8 GetObjectW
0x4c37fc SetTextColor
0x4c3800 SelectObject
0x4c3804 GetTextExtentPoint32W
0x4c3808 CreateCompatibleBitmap
0x4c380c CreateCompatibleDC
0x4c3810 DeleteDC
0x4c3814 SetStretchBltMode
0x4c3818 StretchBlt
0x4c381c CreateSolidBrush
0x4c3820 GdiGetBatchLimit
0x4c3824 GdiSetBatchLimit
0x4c3828 BitBlt
0x4c382c CreateDIBSection
0x4c3830 SetBrushOrgEx
0x4c3834 CreateBitmap
0x4c3838 SetPixel
0x4c383c GetDIBits
0x4c3840 CreateFontW
0x4c3844 SetBkMode
0x4c3848 SetTextAlign
0x4c384c TextOutW
0x4c3850 GetTextMetricsW
0x4c3854 GetPixel
COMDLG32.DLL
0x4c385c PrintDlgW
ADVAPI32.DLL
0x4c3864 OpenProcessToken
0x4c3868 LookupPrivilegeValueW
0x4c386c AdjustTokenPrivileges
0x4c3870 RegCreateKeyExW
0x4c3874 RegCloseKey
0x4c3878 RegSetValueExW
0x4c387c RegOpenKeyExW
0x4c3880 RegDeleteKeyW
0x4c3884 RegQueryValueExW
0x4c3888 RegDeleteValueW
0x4c388c RegEnumKeyExW
0x4c3890 RegEnumValueW
0x4c3894 RegQueryInfoKeyW
0x4c3898 GetUserNameW
0x4c389c CryptAcquireContextW
0x4c38a0 CryptGenRandom
0x4c38a4 CryptReleaseContext
COMCTL32.DLL
0x4c38ac InitCommonControlsEx
0x4c38b0 ImageList_Replace
0x4c38b4 ImageList_Add
0x4c38b8 ImageList_ReplaceIcon
0x4c38bc ImageList_Remove
0x4c38c0 ImageList_AddMasked
0x4c38c4 ImageList_Destroy
0x4c38c8 ImageList_Create
OLE32.DLL
0x4c38d0 CoTaskMemFree
0x4c38d4 CoInitialize
0x4c38d8 CoCreateInstance
0x4c38dc CoUninitialize
0x4c38e0 CoCreateGuid
0x4c38e4 StringFromGUID2
0x4c38e8 RevokeDragDrop
SHELL32.DLL
0x4c38f0 SHGetSpecialFolderLocation
0x4c38f4 SHGetPathFromIDListW
0x4c38f8 SHCreateDirectory
0x4c38fc SHBrowseForFolderW
0x4c3900 ExtractIconW
0x4c3904 SHGetFileInfoW
0x4c3908 ShellExecuteExW
VERSION.DLL
0x4c3910 GetFileVersionInfoSizeW
0x4c3914 GetFileVersionInfoW
0x4c3918 VerQueryValueW
EAT(Export Address Table) is none
MSVCRT.dll
0x4c3340 memset
0x4c3344 system
0x4c3348 memcpy
0x4c334c _wfopen
0x4c3350 fseek
0x4c3354 fclose
0x4c3358 wcsncpy
0x4c335c wcslen
0x4c3360 wcscpy
0x4c3364 wcscat
0x4c3368 wcscmp
0x4c336c memmove
0x4c3370 memcmp
0x4c3374 _stricmp
0x4c3378 sscanf
0x4c337c atoi
0x4c3380 strlen
0x4c3384 strcpy
0x4c3388 strcat
0x4c338c sprintf
0x4c3390 malloc
0x4c3394 free
0x4c3398 _wstat
0x4c339c _wcsdup
0x4c33a0 strcmp
0x4c33a4 floor
0x4c33a8 ceil
0x4c33ac _CIpow
0x4c33b0 _isnan
0x4c33b4 _finite
0x4c33b8 fread
0x4c33bc longjmp
0x4c33c0 _setjmp3
0x4c33c4 ftell
0x4c33c8 wcsncmp
0x4c33cc _snwprintf
0x4c33d0 _wcsicmp
0x4c33d4 tolower
0x4c33d8 localtime
0x4c33dc mktime
0x4c33e0 _wcsnicmp
0x4c33e4 _itow
0x4c33e8 gmtime
0x4c33ec fabs
0x4c33f0 pow
0x4c33f4 ??3@YAXPAX@Z
0x4c33f8 wcsstr
0x4c33fc calloc
0x4c3400 _errno
0x4c3404 strrchr
0x4c3408 strchr
0x4c340c strncpy
0x4c3410 memchr
0x4c3414 _lseeki64
0x4c3418 realloc
0x4c341c abort
0x4c3420 _close
0x4c3424 _wopen
0x4c3428 _setmode
0x4c342c exit
0x4c3430 _open_osfhandle
0x4c3434 _strdup
0x4c3438 _snprintf
0x4c343c setlocale
0x4c3440 strncmp
0x4c3444 wctomb
0x4c3448 _get_osfhandle
0x4c344c _open
0x4c3450 toupper
0x4c3454 wcschr
0x4c3458 mbstowcs
0x4c345c frexp
0x4c3460 modf
0x4c3464 fopen
0x4c3468 strerror
0x4c346c atof
0x4c3470 abs
0x4c3474 fflush
0x4c3478 fwrite
0x4c347c __p__iob
0x4c3480 fprintf
0x4c3484 getenv
0x4c3488 _stati64
0x4c348c time
0x4c3490 _ftime
0x4c3494 _vsnwprintf
0x4c3498 cos
0x4c349c fmod
0x4c34a0 sin
KERNEL32.dll
0x4c34a8 GetModuleHandleW
0x4c34ac HeapCreate
0x4c34b0 HeapDestroy
0x4c34b4 ExitProcess
0x4c34b8 GetDiskFreeSpaceExW
0x4c34bc GetCurrentProcess
0x4c34c0 GetLastError
0x4c34c4 GetUserDefaultLangID
0x4c34c8 GetSystemInfo
0x4c34cc ExpandEnvironmentStringsW
0x4c34d0 FormatMessageW
0x4c34d4 LocalFree
0x4c34d8 OutputDebugStringW
0x4c34dc LoadLibraryW
0x4c34e0 FindResourceW
0x4c34e4 FreeLibrary
0x4c34e8 LoadResource
0x4c34ec SizeofResource
0x4c34f0 LockResource
0x4c34f4 CreateMutexW
0x4c34f8 CloseHandle
0x4c34fc BeginUpdateResourceW
0x4c3500 EndUpdateResourceW
0x4c3504 GetBinaryTypeW
0x4c3508 UpdateResourceW
0x4c350c EnterCriticalSection
0x4c3510 LeaveCriticalSection
0x4c3514 InitializeCriticalSection
0x4c3518 WaitForSingleObject
0x4c351c CreateThread
0x4c3520 HeapAlloc
0x4c3524 HeapFree
0x4c3528 Sleep
0x4c352c CreateFileW
0x4c3530 GetFileSize
0x4c3534 ReadFile
0x4c3538 GetProcAddress
0x4c353c GetCurrentProcessId
0x4c3540 GetCurrentThreadId
0x4c3544 GetEnvironmentVariableW
0x4c3548 SetEnvironmentVariableW
0x4c354c DuplicateHandle
0x4c3550 CreatePipe
0x4c3554 GetStdHandle
0x4c3558 CreateProcessW
0x4c355c GetModuleFileNameW
0x4c3560 GetProfileStringW
0x4c3564 SetFilePointer
0x4c3568 WideCharToMultiByte
0x4c356c MultiByteToWideChar
0x4c3570 SetEndOfFile
0x4c3574 WriteFile
0x4c3578 DeleteFileW
0x4c357c HeapReAlloc
0x4c3580 GetVersionExW
0x4c3584 SetLastError
0x4c3588 CopyFileW
0x4c358c FindFirstFileW
0x4c3590 FindNextFileW
0x4c3594 FindClose
0x4c3598 SetFileAttributesW
0x4c359c RemoveDirectoryW
0x4c35a0 GetDriveTypeW
0x4c35a4 GetFileAttributesW
0x4c35a8 GetTempPathW
0x4c35ac MulDiv
0x4c35b0 GetLocalTime
0x4c35b4 TlsAlloc
0x4c35b8 TlsSetValue
0x4c35bc TlsGetValue
0x4c35c0 GlobalFree
0x4c35c4 GlobalAlloc
0x4c35c8 HeapSize
0x4c35cc TlsFree
0x4c35d0 DeleteCriticalSection
0x4c35d4 InterlockedCompareExchange
0x4c35d8 InterlockedExchange
0x4c35dc VirtualAlloc
0x4c35e0 VirtualFree
0x4c35e4 IsValidCodePage
0x4c35e8 GetACP
0x4c35ec GetOEMCP
0x4c35f0 GetFileType
0x4c35f4 PeekNamedPipe
0x4c35f8 GetFileInformationByHandle
0x4c35fc GetFileAttributesA
0x4c3600 CreateFileA
0x4c3604 GetExitCodeProcess
0x4c3608 GetFullPathNameW
0x4c360c UnregisterWait
0x4c3610 GetCurrentThread
0x4c3614 RegisterWaitForSingleObject
gdiplus.dll
0x4c361c GdipDeleteFont
0x4c3620 GdipDeleteGraphics
0x4c3624 GdipDeletePath
0x4c3628 GdipDeleteMatrix
0x4c362c GdipDeletePen
0x4c3630 GdipDeleteStringFormat
0x4c3634 GdipFree
0x4c3638 GdipGetDpiX
0x4c363c GdipGetDpiY
USER32.DLL
0x4c3644 IsWindowEnabled
0x4c3648 IsWindowVisible
0x4c364c ExitWindowsEx
0x4c3650 GetActiveWindow
0x4c3654 SendMessageW
0x4c3658 GetWindowTextLengthW
0x4c365c GetSysColor
0x4c3660 SetRect
0x4c3664 GetWindowLongW
0x4c3668 RedrawWindow
0x4c366c GetDlgCtrlID
0x4c3670 GetWindowTextW
0x4c3674 ShowWindow
0x4c3678 SetForegroundWindow
0x4c367c SetWindowLongW
0x4c3680 UpdateLayeredWindow
0x4c3684 DestroyIcon
0x4c3688 EnumWindows
0x4c368c MessageBoxW
0x4c3690 PostMessageW
0x4c3694 GetForegroundWindow
0x4c3698 GetWindowThreadProcessId
0x4c369c EnableWindow
0x4c36a0 SetWindowPos
0x4c36a4 DestroyWindow
0x4c36a8 SystemParametersInfoW
0x4c36ac SetFocus
0x4c36b0 GetFocus
0x4c36b4 GetParent
0x4c36b8 GetClassNameW
0x4c36bc SetWindowTextW
0x4c36c0 CallWindowProcW
0x4c36c4 RemovePropW
0x4c36c8 GetWindowRect
0x4c36cc GetPropW
0x4c36d0 CreateWindowExW
0x4c36d4 SetPropW
0x4c36d8 SetScrollPos
0x4c36dc GetDC
0x4c36e0 InflateRect
0x4c36e4 ReleaseDC
0x4c36e8 GetWindowDC
0x4c36ec MapWindowPoints
0x4c36f0 MoveWindow
0x4c36f4 InvalidateRect
0x4c36f8 GetIconInfo
0x4c36fc UpdateWindow
0x4c3700 ReleaseCapture
0x4c3704 BeginPaint
0x4c3708 DrawStateW
0x4c370c EndPaint
0x4c3710 SetCapture
0x4c3714 ScreenToClient
0x4c3718 GetSystemMetrics
0x4c371c GetSysColorBrush
0x4c3720 DrawTextW
0x4c3724 GetWindow
0x4c3728 ValidateRect
0x4c372c ClientToScreen
0x4c3730 GetClientRect
0x4c3734 FillRect
0x4c3738 DefWindowProcW
0x4c373c LoadCursorW
0x4c3740 RegisterClassExW
0x4c3744 SetClassLongW
0x4c3748 EnumPropsExW
0x4c374c SetActiveWindow
0x4c3750 LoadIconW
0x4c3754 IsZoomed
0x4c3758 IsIconic
0x4c375c PeekMessageW
0x4c3760 MsgWaitForMultipleObjects
0x4c3764 GetMessageW
0x4c3768 TranslateAcceleratorW
0x4c376c TranslateMessage
0x4c3770 DispatchMessageW
0x4c3774 RegisterClassW
0x4c3778 AdjustWindowRectEx
0x4c377c CreateAcceleratorTableW
0x4c3780 UnregisterClassW
0x4c3784 DestroyAcceleratorTable
0x4c3788 GetMenu
0x4c378c SetTimer
0x4c3790 KillTimer
0x4c3794 DefFrameProcW
0x4c3798 EnumChildWindows
0x4c379c GetKeyState
0x4c37a0 IsChild
0x4c37a4 RegisterWindowMessageW
0x4c37a8 CreateIconFromResourceEx
0x4c37ac CreateIconFromResource
0x4c37b0 CharLowerW
0x4c37b4 DrawIconEx
GDI32.DLL
0x4c37bc StartDocW
0x4c37c0 GetMapMode
0x4c37c4 SetMapMode
0x4c37c8 GetDeviceCaps
0x4c37cc DPtoLP
0x4c37d0 StartPage
0x4c37d4 EndPage
0x4c37d8 EndDoc
0x4c37dc SetBkColor
0x4c37e0 CreateDCW
0x4c37e4 DeleteObject
0x4c37e8 GetStockObject
0x4c37ec CreateFontIndirectW
0x4c37f0 ExcludeClipRect
0x4c37f4 GetObjectType
0x4c37f8 GetObjectW
0x4c37fc SetTextColor
0x4c3800 SelectObject
0x4c3804 GetTextExtentPoint32W
0x4c3808 CreateCompatibleBitmap
0x4c380c CreateCompatibleDC
0x4c3810 DeleteDC
0x4c3814 SetStretchBltMode
0x4c3818 StretchBlt
0x4c381c CreateSolidBrush
0x4c3820 GdiGetBatchLimit
0x4c3824 GdiSetBatchLimit
0x4c3828 BitBlt
0x4c382c CreateDIBSection
0x4c3830 SetBrushOrgEx
0x4c3834 CreateBitmap
0x4c3838 SetPixel
0x4c383c GetDIBits
0x4c3840 CreateFontW
0x4c3844 SetBkMode
0x4c3848 SetTextAlign
0x4c384c TextOutW
0x4c3850 GetTextMetricsW
0x4c3854 GetPixel
COMDLG32.DLL
0x4c385c PrintDlgW
ADVAPI32.DLL
0x4c3864 OpenProcessToken
0x4c3868 LookupPrivilegeValueW
0x4c386c AdjustTokenPrivileges
0x4c3870 RegCreateKeyExW
0x4c3874 RegCloseKey
0x4c3878 RegSetValueExW
0x4c387c RegOpenKeyExW
0x4c3880 RegDeleteKeyW
0x4c3884 RegQueryValueExW
0x4c3888 RegDeleteValueW
0x4c388c RegEnumKeyExW
0x4c3890 RegEnumValueW
0x4c3894 RegQueryInfoKeyW
0x4c3898 GetUserNameW
0x4c389c CryptAcquireContextW
0x4c38a0 CryptGenRandom
0x4c38a4 CryptReleaseContext
COMCTL32.DLL
0x4c38ac InitCommonControlsEx
0x4c38b0 ImageList_Replace
0x4c38b4 ImageList_Add
0x4c38b8 ImageList_ReplaceIcon
0x4c38bc ImageList_Remove
0x4c38c0 ImageList_AddMasked
0x4c38c4 ImageList_Destroy
0x4c38c8 ImageList_Create
OLE32.DLL
0x4c38d0 CoTaskMemFree
0x4c38d4 CoInitialize
0x4c38d8 CoCreateInstance
0x4c38dc CoUninitialize
0x4c38e0 CoCreateGuid
0x4c38e4 StringFromGUID2
0x4c38e8 RevokeDragDrop
SHELL32.DLL
0x4c38f0 SHGetSpecialFolderLocation
0x4c38f4 SHGetPathFromIDListW
0x4c38f8 SHCreateDirectory
0x4c38fc SHBrowseForFolderW
0x4c3900 ExtractIconW
0x4c3904 SHGetFileInfoW
0x4c3908 ShellExecuteExW
VERSION.DLL
0x4c3910 GetFileVersionInfoSizeW
0x4c3914 GetFileVersionInfoW
0x4c3918 VerQueryValueW
EAT(Export Address Table) is none