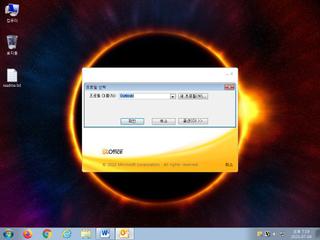
ScreenShot
| Created | 2023.07.04 19:22 | Machine | s1_win7_x6402 |
| Filename | visalostpassp.doc | ||
| Type | Composite Document File V2 Document, Little Endian, Os: MacOS, Version 7.11, Code page: 10000, Title | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 41 detected (malicious, high confidence, score, Emeka, Save, Hdfk, Psycho, Melissa, Thus, byppsa, CLASSIC, Cybernet, OLE2, Class, Static AI, Malicious OLE, Jerk, ai score=80, secu, Detected, q@MM, Valyria, Moat) | ||
| md5 | d0807bfc6b65ec81e4c2cb6bc91d026c | ||
| sha256 | 1184252bed47270fdb5d853d07279cb2b01e61e3fe960bf8a69c56db2605d67d | ||
| ssdeep | 1536:BFjfZgpYdRm/BjljrEQ1OkVKybVTOMlKNw0zqpTxD0dR1Cwxrt3r8aOt0My8LAFp:XLd6UeOHQXKNwqq18RNJr8xt0/dr | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (7cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 41 AntiVirus engines on VirusTotal as malicious |
| danger | Connects to an IP address that is no longer responding to requests (legitimate services will remain up-and-running usually) |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates (office) documents on the filesystem |
| notice | Creates hidden or system file |
| notice | Word document hooks document close |
| notice | Word document hooks document open |
Rules (2cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Contains_VBA_macro_code | Detect a MS Office document with embedded VBA macro code [binaries] | binaries (upload) |
| info | Microsoft_Office_File_Zero | Microsoft Office File | binaries (upload) |