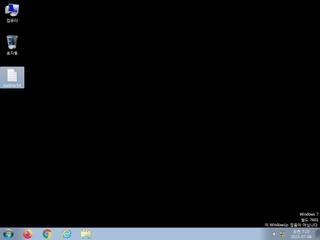
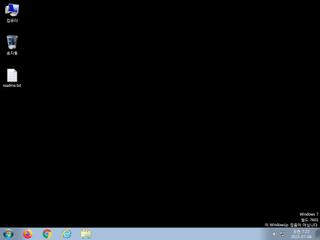
ScreenShot
| Created | 2023.07.06 07:30 | Machine | s1_win7_x6401 |
| Filename | Project_8.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | |||
| VT API (file) | |||
| md5 | ed7cf64192cd90aac14b69cdd202f30d | ||
| sha256 | 8f5d2c5facf4702e4a6338b5224d9526d4761535901acf27f43992024340ccb0 | ||
| ssdeep | 6144:vS5n9peabtzHGx9LkLpSywZ3dMTHaXusO6EXxPapUTOVP66O1/hNiyXnxrSYJ:vsnHeaK9LaT+/+hFqZZIJESUY | ||
| imphash | 1a5e4ddad4ba385b765de613acbb20f9 | ||
| impfuzzy | 12:0jDMyI5ZGnAK6JlXfHYZ8vhU43YPXJ1XJqNa4UP0T75jSNbu4GdeGPvWlfV5G:0jDMN/SDom8vaL4N1oq75GNb0rHWl3G | ||
Network IP location
Signature (10cnts)
| Level | Description |
|---|---|
| danger | Connects to IP addresses that are no longer responding to requests (legitimate services will remain up-and-running usually) |
| watch | Communicates with host for which no DNS query was performed |
| notice | A process created a hidden window |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | The file contains an unknown PE resource name possibly indicative of a packer |
Rules (11cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x406000 CloseHandle
0x406004 HeapAlloc
0x406008 HeapFree
0x40600c GetProcessHeap
0x406010 GetProcAddress
0x406014 lstrlenA
0x406018 GetModuleHandleExW
0x40601c ExitProcess
0x406020 Sleep
0x406024 LoadLibraryExW
0x406028 GetModuleFileNameW
0x40602c FreeLibrary
0x406030 VirtualQuery
0x406034 GetLastError
0x406038 GetModuleHandleW
0x40603c GetStartupInfoW
0x406040 InitializeSListHead
0x406044 GetSystemTimeAsFileTime
0x406048 GetCurrentThreadId
0x40604c GetCurrentProcessId
0x406050 QueryPerformanceCounter
0x406054 IsProcessorFeaturePresent
0x406058 TerminateProcess
0x40605c GetCurrentProcess
0x406060 SetUnhandledExceptionFilter
0x406064 UnhandledExceptionFilter
0x406068 WideCharToMultiByte
0x40606c MultiByteToWideChar
0x406070 RaiseException
0x406074 IsDebuggerPresent
msvcrt.dll
0x40607c _msize
0x406080 ?terminate@@YAXXZ
0x406084 realloc
0x406088 _errno
0x40608c _wcmdln
0x406090 __wgetmainargs
0x406094 __set_app_type
0x406098 _XcptFilter
0x40609c free
0x4060a0 _controlfp_s
0x4060a4 strcat_s
0x4060a8 strcpy_s
0x4060ac __p__commode
0x4060b0 _set_fmode
0x4060b4 _initterm_e
0x4060b8 _initterm
0x4060bc _except_handler4_common
0x4060c0 memset
0x4060c4 ?_set_new_mode@@YAHH@Z
0x4060c8 __CxxFrameHandler3
0x4060cc _amsg_exit
EAT(Export Address Table) is none
KERNEL32.dll
0x406000 CloseHandle
0x406004 HeapAlloc
0x406008 HeapFree
0x40600c GetProcessHeap
0x406010 GetProcAddress
0x406014 lstrlenA
0x406018 GetModuleHandleExW
0x40601c ExitProcess
0x406020 Sleep
0x406024 LoadLibraryExW
0x406028 GetModuleFileNameW
0x40602c FreeLibrary
0x406030 VirtualQuery
0x406034 GetLastError
0x406038 GetModuleHandleW
0x40603c GetStartupInfoW
0x406040 InitializeSListHead
0x406044 GetSystemTimeAsFileTime
0x406048 GetCurrentThreadId
0x40604c GetCurrentProcessId
0x406050 QueryPerformanceCounter
0x406054 IsProcessorFeaturePresent
0x406058 TerminateProcess
0x40605c GetCurrentProcess
0x406060 SetUnhandledExceptionFilter
0x406064 UnhandledExceptionFilter
0x406068 WideCharToMultiByte
0x40606c MultiByteToWideChar
0x406070 RaiseException
0x406074 IsDebuggerPresent
msvcrt.dll
0x40607c _msize
0x406080 ?terminate@@YAXXZ
0x406084 realloc
0x406088 _errno
0x40608c _wcmdln
0x406090 __wgetmainargs
0x406094 __set_app_type
0x406098 _XcptFilter
0x40609c free
0x4060a0 _controlfp_s
0x4060a4 strcat_s
0x4060a8 strcpy_s
0x4060ac __p__commode
0x4060b0 _set_fmode
0x4060b4 _initterm_e
0x4060b8 _initterm
0x4060bc _except_handler4_common
0x4060c0 memset
0x4060c4 ?_set_new_mode@@YAHH@Z
0x4060c8 __CxxFrameHandler3
0x4060cc _amsg_exit
EAT(Export Address Table) is none