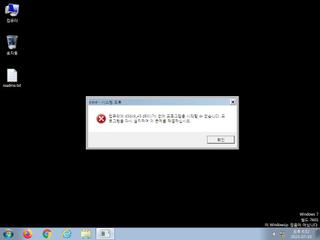
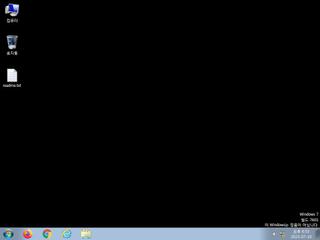
ScreenShot
| Created | 2023.07.10 18:55 | Machine | s1_win7_x6401 |
| Filename | a.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 43 detected (Common, Zygug, Sabsik, unsafe, Save, malicious, confidence, 100%, ZexaF, @JW@a8F1Mabk, ABRisk, DTZP, high confidence, VMProtect, AU suspicious, score, moderate, Static AI, Malicious PE, Meterpreter, Detected, Artemis, ai score=89, Genetic, R002H09G723, Generic@AI, RDML, rfJD1UdPqUbNFbWV83k26g, L2QP+SogAHQ, susgen) | ||
| md5 | 1d35572dfa6a564b147bad355ad1be78 | ||
| sha256 | 38e1aa092a57e10bf67da9f4e643e59dc050d683900d7ff930191a174f191778 | ||
| ssdeep | 196608:VhpnqHrY6/B0K8QSA0cv1FMEHF7vyMXwrEUxfY5PS/:Jr6uK8xvcvYe7vyAuEUsPS/ | ||
| imphash | ac18dc6a1c61398696cfd62f5dc166eb | ||
| impfuzzy | 96:odiB0UuGXeTKCdLWPCBLePQyDogt8ZLBgNh6DW/r/+TO3gWV5gTa:0jGXwKNPGysGAW/iTO3VETa | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 43 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
WS2_32.dll
0xa89000 gethostname
0xa89004 sendto
0xa89008 recvfrom
0xa8900c WSAEventSelect
0xa89010 WSAEnumNetworkEvents
0xa89014 WSACreateEvent
0xa89018 WSACloseEvent
0xa8901c htonl
0xa89020 WSAIoctl
0xa89024 htons
0xa89028 getsockname
0xa8902c listen
0xa89030 ind
0xa89034 accept
0xa89038 WSASetLastError
0xa8903c WSAGetLastError
0xa89040 WSACleanup
0xa89044 __WSAFDIsSet
0xa89048 closesocket
0xa8904c select
0xa89050 shutdown
0xa89054 WSASocketW
0xa89058 inet_pton
0xa8905c getaddrinfo
0xa89060 WSAStartup
0xa89064 getpeername
0xa89068 send
0xa8906c socket
0xa89070 ntohs
0xa89074 connect
0xa89078 recv
0xa8907c getsockopt
0xa89080 freeaddrinfo
0xa89084 ioctlsocket
0xa89088 getnameinfo
0xa8908c setsockopt
0xa89090 ntohl
ADVAPI32.dll
0xa89098 CryptHashData
0xa8909c CryptGenRandom
0xa890a0 CryptGetHashParam
0xa890a4 CryptReleaseContext
0xa890a8 CryptAcquireContextA
0xa890ac CryptDestroyHash
0xa890b0 CryptDestroyKey
0xa890b4 CryptImportKey
0xa890b8 CryptEncrypt
0xa890bc CryptCreateHash
0xa890c0 ReportEventW
0xa890c4 RegisterEventSourceW
0xa890c8 DeregisterEventSource
0xa890cc OpenProcessToken
0xa890d0 GetTokenInformation
CRYPT32.dll
0xa890d8 CryptStringToBinaryA
0xa890dc PFXImportCertStore
0xa890e0 CryptDecodeObjectEx
0xa890e4 CertAddCertificateContextToStore
0xa890e8 CertFindExtension
0xa890ec CertGetNameStringA
0xa890f0 CryptQueryObject
0xa890f4 CertCreateCertificateChainEngine
0xa890f8 CertFreeCertificateChainEngine
0xa890fc CertGetCertificateChain
0xa89100 CertFreeCertificateChain
0xa89104 CertOpenStore
0xa89108 CertFreeCertificateContext
0xa8910c CertOpenSystemStoreW
0xa89110 CertEnumCertificatesInStore
0xa89114 CertCloseStore
0xa89118 CertFindCertificateInStore
d3d9.dll
0xa89120 Direct3DCreate9
d3dx9_43.dll
0xa89128 D3DXCreateTextureFromFileInMemory
0xa8912c D3DXCreateTextureFromFileInMemoryEx
KERNEL32.dll
0xa89134 GlobalAlloc
0xa89138 GlobalFree
0xa8913c GlobalLock
0xa89140 GlobalUnlock
0xa89144 MultiByteToWideChar
0xa89148 QueryPerformanceFrequency
0xa8914c QueryPerformanceCounter
0xa89150 HeapFree
0xa89154 GetFullPathNameW
0xa89158 WriteFile
0xa8915c SetFilePointer
0xa89160 SetEndOfFile
0xa89164 WaitForSingleObject
0xa89168 CreateFileW
0xa8916c Sleep
0xa89170 LoadLibraryA
0xa89174 DeleteFileW
0xa89178 CloseHandle
0xa8917c HeapAlloc
0xa89180 GetProcAddress
0xa89184 GetProcessHeap
0xa89188 CreateProcessW
0xa8918c CreateMutexW
0xa89190 GetLastError
0xa89194 GetModuleHandleW
0xa89198 ReadFile
0xa8919c CreateThread
0xa891a0 ExitProcess
0xa891a4 GetCurrentProcess
0xa891a8 GetVolumeInformationW
0xa891ac EnterCriticalSection
0xa891b0 VirtualFree
0xa891b4 VirtualAlloc
0xa891b8 TerminateProcess
0xa891bc LeaveCriticalSection
0xa891c0 HeapReAlloc
0xa891c4 GetExitCodeProcess
0xa891c8 CreateDirectoryW
0xa891cc SetLastError
0xa891d0 InitializeCriticalSectionAndSpinCount
0xa891d4 DeleteCriticalSection
0xa891d8 GetCurrentThreadId
0xa891dc TlsAlloc
0xa891e0 TlsGetValue
0xa891e4 TlsSetValue
0xa891e8 TlsFree
0xa891ec FormatMessageW
0xa891f0 GetStdHandle
0xa891f4 GetEnvironmentVariableW
0xa891f8 GetFileType
0xa891fc GetModuleHandleExW
0xa89200 SwitchToFiber
0xa89204 DeleteFiber
0xa89208 CreateFiber
0xa8920c GetCurrentProcessId
0xa89210 GetSystemTimeAsFileTime
0xa89214 ConvertFiberToThread
0xa89218 ConvertThreadToFiber
0xa8921c FindClose
0xa89220 FindFirstFileW
0xa89224 FindNextFileW
0xa89228 WideCharToMultiByte
0xa8922c GetCommandLineA
0xa89230 LoadLibraryW
0xa89234 GetConsoleMode
0xa89238 SetConsoleMode
0xa8923c ReadConsoleA
0xa89240 ReadConsoleW
0xa89244 GetSystemTime
0xa89248 SystemTimeToFileTime
0xa8924c InitializeCriticalSectionEx
0xa89250 SleepEx
0xa89254 GetSystemDirectoryA
0xa89258 CompareStringW
0xa8925c GetTickCount
0xa89260 GetCommandLineW
0xa89264 WaitForSingleObjectEx
0xa89268 GetEnvironmentVariableA
0xa8926c PeekNamedPipe
0xa89270 WaitForMultipleObjects
0xa89274 VerSetConditionMask
0xa89278 VerifyVersionInfoA
0xa8927c CreateFileA
0xa89280 GetFileSizeEx
0xa89284 ExitThread
0xa89288 LoadLibraryExW
0xa8928c InterlockedPushEntrySList
0xa89290 RtlUnwind
0xa89294 GetStartupInfoW
0xa89298 IsDebuggerPresent
0xa8929c InitializeSListHead
0xa892a0 IsProcessorFeaturePresent
0xa892a4 SetUnhandledExceptionFilter
0xa892a8 UnhandledExceptionFilter
0xa892ac CreateEventW
0xa892b0 ResetEvent
0xa892b4 SetEvent
0xa892b8 GetStringTypeW
0xa892bc GetCPInfo
0xa892c0 CompareStringEx
0xa892c4 GetOEMCP
0xa892c8 GetACP
0xa892cc GetEnvironmentStringsW
0xa892d0 FreeEnvironmentStringsW
0xa892d4 FreeLibrary
0xa892d8 SetEnvironmentVariableW
0xa892dc IsValidCodePage
0xa892e0 FindFirstFileExW
0xa892e4 HeapSize
0xa892e8 GetCurrentDirectoryW
0xa892ec LCMapStringEx
0xa892f0 DecodePointer
0xa892f4 EncodePointer
0xa892f8 InitOnceBeginInitialize
0xa892fc InitOnceComplete
0xa89300 RaiseException
0xa89304 TryAcquireSRWLockExclusive
0xa89308 AcquireSRWLockExclusive
0xa8930c ReleaseSRWLockExclusive
0xa89310 InitializeSRWLock
0xa89314 GetConsoleOutputCP
0xa89318 GetModuleFileNameW
0xa8931c SetFilePointerEx
0xa89320 FreeLibraryAndExitThread
0xa89324 SetConsoleCtrlHandler
0xa89328 GetDriveTypeW
0xa8932c GetFileInformationByHandle
0xa89330 SystemTimeToTzSpecificLocalTime
0xa89334 MoveFileExA
0xa89338 FileTimeToSystemTime
0xa8933c LCMapStringW
0xa89340 GetLocaleInfoW
0xa89344 IsValidLocale
0xa89348 GetUserDefaultLCID
0xa8934c EnumSystemLocalesW
0xa89350 FlushFileBuffers
0xa89354 GetTimeZoneInformation
0xa89358 GetFileAttributesExW
0xa8935c GetModuleHandleA
0xa89360 WriteConsoleW
0xa89364 SetStdHandle
USER32.dll
0xa8936c GetCursorPos
0xa89370 SetCursorPos
0xa89374 ReleaseCapture
0xa89378 GetClientRect
0xa8937c SetCursor
0xa89380 SetCapture
0xa89384 LoadCursorW
0xa89388 GetForegroundWindow
0xa8938c IsChild
0xa89390 ClientToScreen
0xa89394 GetCapture
0xa89398 ScreenToClient
0xa8939c ShowWindow
0xa893a0 GetDesktopWindow
0xa893a4 PostQuitMessage
0xa893a8 RegisterClassExW
0xa893ac UnregisterClassW
0xa893b0 CreateWindowExW
0xa893b4 MessageBoxW
0xa893b8 DestroyWindow
0xa893bc GetWindowRect
0xa893c0 DefWindowProcW
0xa893c4 TranslateMessage
0xa893c8 PeekMessageW
0xa893cc DispatchMessageW
0xa893d0 GetProcessWindowStation
0xa893d4 GetUserObjectInformationW
0xa893d8 OpenClipboard
0xa893dc CloseClipboard
0xa893e0 EmptyClipboard
0xa893e4 GetClipboardData
0xa893e8 SetClipboardData
0xa893ec GetKeyState
SHELL32.dll
0xa893f4 ShellExecuteW
0xa893f8 SHGetKnownFolderPath
ole32.dll
0xa89400 CoTaskMemFree
IMM32.dll
0xa89408 ImmSetCompositionWindow
0xa8940c ImmReleaseContext
0xa89410 ImmGetContext
XINPUT1_3.dll
0xa89418 None
0xa8941c None
crypt.dll
0xa89424 BCryptGenRandom
ntdll.dll
0xa8942c RtlAdjustPrivilege
Normaliz.dll
0xa89434 IdnToAscii
WLDAP32.dll
0xa8943c None
0xa89440 None
0xa89444 None
0xa89448 None
0xa8944c None
0xa89450 None
0xa89454 None
0xa89458 None
0xa8945c None
0xa89460 None
0xa89464 None
0xa89468 None
0xa8946c None
0xa89470 None
0xa89474 None
0xa89478 None
0xa8947c None
0xa89480 None
KERNEL32.dll
0xa89488 LocalAlloc
0xa8948c LocalFree
0xa89490 GetModuleFileNameW
0xa89494 ExitProcess
0xa89498 LoadLibraryA
0xa8949c GetModuleHandleA
0xa894a0 GetProcAddress
EAT(Export Address Table) is none
WS2_32.dll
0xa89000 gethostname
0xa89004 sendto
0xa89008 recvfrom
0xa8900c WSAEventSelect
0xa89010 WSAEnumNetworkEvents
0xa89014 WSACreateEvent
0xa89018 WSACloseEvent
0xa8901c htonl
0xa89020 WSAIoctl
0xa89024 htons
0xa89028 getsockname
0xa8902c listen
0xa89030 ind
0xa89034 accept
0xa89038 WSASetLastError
0xa8903c WSAGetLastError
0xa89040 WSACleanup
0xa89044 __WSAFDIsSet
0xa89048 closesocket
0xa8904c select
0xa89050 shutdown
0xa89054 WSASocketW
0xa89058 inet_pton
0xa8905c getaddrinfo
0xa89060 WSAStartup
0xa89064 getpeername
0xa89068 send
0xa8906c socket
0xa89070 ntohs
0xa89074 connect
0xa89078 recv
0xa8907c getsockopt
0xa89080 freeaddrinfo
0xa89084 ioctlsocket
0xa89088 getnameinfo
0xa8908c setsockopt
0xa89090 ntohl
ADVAPI32.dll
0xa89098 CryptHashData
0xa8909c CryptGenRandom
0xa890a0 CryptGetHashParam
0xa890a4 CryptReleaseContext
0xa890a8 CryptAcquireContextA
0xa890ac CryptDestroyHash
0xa890b0 CryptDestroyKey
0xa890b4 CryptImportKey
0xa890b8 CryptEncrypt
0xa890bc CryptCreateHash
0xa890c0 ReportEventW
0xa890c4 RegisterEventSourceW
0xa890c8 DeregisterEventSource
0xa890cc OpenProcessToken
0xa890d0 GetTokenInformation
CRYPT32.dll
0xa890d8 CryptStringToBinaryA
0xa890dc PFXImportCertStore
0xa890e0 CryptDecodeObjectEx
0xa890e4 CertAddCertificateContextToStore
0xa890e8 CertFindExtension
0xa890ec CertGetNameStringA
0xa890f0 CryptQueryObject
0xa890f4 CertCreateCertificateChainEngine
0xa890f8 CertFreeCertificateChainEngine
0xa890fc CertGetCertificateChain
0xa89100 CertFreeCertificateChain
0xa89104 CertOpenStore
0xa89108 CertFreeCertificateContext
0xa8910c CertOpenSystemStoreW
0xa89110 CertEnumCertificatesInStore
0xa89114 CertCloseStore
0xa89118 CertFindCertificateInStore
d3d9.dll
0xa89120 Direct3DCreate9
d3dx9_43.dll
0xa89128 D3DXCreateTextureFromFileInMemory
0xa8912c D3DXCreateTextureFromFileInMemoryEx
KERNEL32.dll
0xa89134 GlobalAlloc
0xa89138 GlobalFree
0xa8913c GlobalLock
0xa89140 GlobalUnlock
0xa89144 MultiByteToWideChar
0xa89148 QueryPerformanceFrequency
0xa8914c QueryPerformanceCounter
0xa89150 HeapFree
0xa89154 GetFullPathNameW
0xa89158 WriteFile
0xa8915c SetFilePointer
0xa89160 SetEndOfFile
0xa89164 WaitForSingleObject
0xa89168 CreateFileW
0xa8916c Sleep
0xa89170 LoadLibraryA
0xa89174 DeleteFileW
0xa89178 CloseHandle
0xa8917c HeapAlloc
0xa89180 GetProcAddress
0xa89184 GetProcessHeap
0xa89188 CreateProcessW
0xa8918c CreateMutexW
0xa89190 GetLastError
0xa89194 GetModuleHandleW
0xa89198 ReadFile
0xa8919c CreateThread
0xa891a0 ExitProcess
0xa891a4 GetCurrentProcess
0xa891a8 GetVolumeInformationW
0xa891ac EnterCriticalSection
0xa891b0 VirtualFree
0xa891b4 VirtualAlloc
0xa891b8 TerminateProcess
0xa891bc LeaveCriticalSection
0xa891c0 HeapReAlloc
0xa891c4 GetExitCodeProcess
0xa891c8 CreateDirectoryW
0xa891cc SetLastError
0xa891d0 InitializeCriticalSectionAndSpinCount
0xa891d4 DeleteCriticalSection
0xa891d8 GetCurrentThreadId
0xa891dc TlsAlloc
0xa891e0 TlsGetValue
0xa891e4 TlsSetValue
0xa891e8 TlsFree
0xa891ec FormatMessageW
0xa891f0 GetStdHandle
0xa891f4 GetEnvironmentVariableW
0xa891f8 GetFileType
0xa891fc GetModuleHandleExW
0xa89200 SwitchToFiber
0xa89204 DeleteFiber
0xa89208 CreateFiber
0xa8920c GetCurrentProcessId
0xa89210 GetSystemTimeAsFileTime
0xa89214 ConvertFiberToThread
0xa89218 ConvertThreadToFiber
0xa8921c FindClose
0xa89220 FindFirstFileW
0xa89224 FindNextFileW
0xa89228 WideCharToMultiByte
0xa8922c GetCommandLineA
0xa89230 LoadLibraryW
0xa89234 GetConsoleMode
0xa89238 SetConsoleMode
0xa8923c ReadConsoleA
0xa89240 ReadConsoleW
0xa89244 GetSystemTime
0xa89248 SystemTimeToFileTime
0xa8924c InitializeCriticalSectionEx
0xa89250 SleepEx
0xa89254 GetSystemDirectoryA
0xa89258 CompareStringW
0xa8925c GetTickCount
0xa89260 GetCommandLineW
0xa89264 WaitForSingleObjectEx
0xa89268 GetEnvironmentVariableA
0xa8926c PeekNamedPipe
0xa89270 WaitForMultipleObjects
0xa89274 VerSetConditionMask
0xa89278 VerifyVersionInfoA
0xa8927c CreateFileA
0xa89280 GetFileSizeEx
0xa89284 ExitThread
0xa89288 LoadLibraryExW
0xa8928c InterlockedPushEntrySList
0xa89290 RtlUnwind
0xa89294 GetStartupInfoW
0xa89298 IsDebuggerPresent
0xa8929c InitializeSListHead
0xa892a0 IsProcessorFeaturePresent
0xa892a4 SetUnhandledExceptionFilter
0xa892a8 UnhandledExceptionFilter
0xa892ac CreateEventW
0xa892b0 ResetEvent
0xa892b4 SetEvent
0xa892b8 GetStringTypeW
0xa892bc GetCPInfo
0xa892c0 CompareStringEx
0xa892c4 GetOEMCP
0xa892c8 GetACP
0xa892cc GetEnvironmentStringsW
0xa892d0 FreeEnvironmentStringsW
0xa892d4 FreeLibrary
0xa892d8 SetEnvironmentVariableW
0xa892dc IsValidCodePage
0xa892e0 FindFirstFileExW
0xa892e4 HeapSize
0xa892e8 GetCurrentDirectoryW
0xa892ec LCMapStringEx
0xa892f0 DecodePointer
0xa892f4 EncodePointer
0xa892f8 InitOnceBeginInitialize
0xa892fc InitOnceComplete
0xa89300 RaiseException
0xa89304 TryAcquireSRWLockExclusive
0xa89308 AcquireSRWLockExclusive
0xa8930c ReleaseSRWLockExclusive
0xa89310 InitializeSRWLock
0xa89314 GetConsoleOutputCP
0xa89318 GetModuleFileNameW
0xa8931c SetFilePointerEx
0xa89320 FreeLibraryAndExitThread
0xa89324 SetConsoleCtrlHandler
0xa89328 GetDriveTypeW
0xa8932c GetFileInformationByHandle
0xa89330 SystemTimeToTzSpecificLocalTime
0xa89334 MoveFileExA
0xa89338 FileTimeToSystemTime
0xa8933c LCMapStringW
0xa89340 GetLocaleInfoW
0xa89344 IsValidLocale
0xa89348 GetUserDefaultLCID
0xa8934c EnumSystemLocalesW
0xa89350 FlushFileBuffers
0xa89354 GetTimeZoneInformation
0xa89358 GetFileAttributesExW
0xa8935c GetModuleHandleA
0xa89360 WriteConsoleW
0xa89364 SetStdHandle
USER32.dll
0xa8936c GetCursorPos
0xa89370 SetCursorPos
0xa89374 ReleaseCapture
0xa89378 GetClientRect
0xa8937c SetCursor
0xa89380 SetCapture
0xa89384 LoadCursorW
0xa89388 GetForegroundWindow
0xa8938c IsChild
0xa89390 ClientToScreen
0xa89394 GetCapture
0xa89398 ScreenToClient
0xa8939c ShowWindow
0xa893a0 GetDesktopWindow
0xa893a4 PostQuitMessage
0xa893a8 RegisterClassExW
0xa893ac UnregisterClassW
0xa893b0 CreateWindowExW
0xa893b4 MessageBoxW
0xa893b8 DestroyWindow
0xa893bc GetWindowRect
0xa893c0 DefWindowProcW
0xa893c4 TranslateMessage
0xa893c8 PeekMessageW
0xa893cc DispatchMessageW
0xa893d0 GetProcessWindowStation
0xa893d4 GetUserObjectInformationW
0xa893d8 OpenClipboard
0xa893dc CloseClipboard
0xa893e0 EmptyClipboard
0xa893e4 GetClipboardData
0xa893e8 SetClipboardData
0xa893ec GetKeyState
SHELL32.dll
0xa893f4 ShellExecuteW
0xa893f8 SHGetKnownFolderPath
ole32.dll
0xa89400 CoTaskMemFree
IMM32.dll
0xa89408 ImmSetCompositionWindow
0xa8940c ImmReleaseContext
0xa89410 ImmGetContext
XINPUT1_3.dll
0xa89418 None
0xa8941c None
crypt.dll
0xa89424 BCryptGenRandom
ntdll.dll
0xa8942c RtlAdjustPrivilege
Normaliz.dll
0xa89434 IdnToAscii
WLDAP32.dll
0xa8943c None
0xa89440 None
0xa89444 None
0xa89448 None
0xa8944c None
0xa89450 None
0xa89454 None
0xa89458 None
0xa8945c None
0xa89460 None
0xa89464 None
0xa89468 None
0xa8946c None
0xa89470 None
0xa89474 None
0xa89478 None
0xa8947c None
0xa89480 None
KERNEL32.dll
0xa89488 LocalAlloc
0xa8948c LocalFree
0xa89490 GetModuleFileNameW
0xa89494 ExitProcess
0xa89498 LoadLibraryA
0xa8949c GetModuleHandleA
0xa894a0 GetProcAddress
EAT(Export Address Table) is none