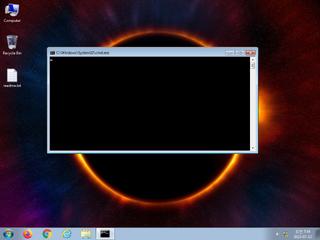
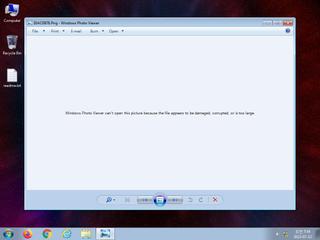
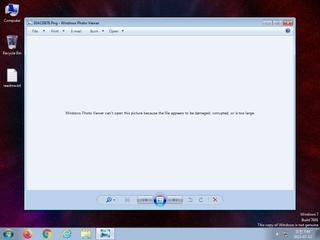
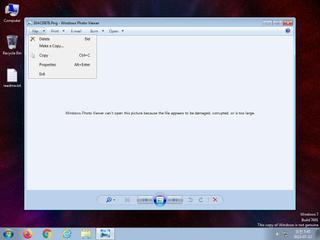
ScreenShot
| Created | 2023.07.12 07:49 | Machine | s1_win7_x6403 |
| Filename | 20AC0B78.Png | ||
| Type | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last P | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | |||
| VT API (file) | 45 detected (Agentb, GenericKD, Bulz, GenericRXAA, Convagent, Save, Eldorado, multiple detections, R002H06BC22, DirtyMoe, Malicious, score, kkyd, PurpleFox, CLASSIC, Generic Reputation PUA, Black, Gen2, Packed2, FUPORFLEX, SMYEBDR, VMProtect, ojena, ai score=88, Tiggre, GenericMC, Malware@#rpgmzhl7y5ey, many, Detected, ZedlaF, rG4@aWpFvhd, BScope, susgen, PossibleThreat) | ||
| md5 | 9c84926dac4e5e7037747c49f58f1724 | ||
| sha256 | ee013d9ff7050f96c3ff91d49e90bb60f3a2fb4d41efd918e6cb8aac6cf94e47 | ||
| ssdeep | 24576:eruDXXh3j04BMeRocDP1Nxyq7KDOJjkDOk4TB4McL8dfbfr7KCN5nQ6BAMVUTH:e+Xx4i5ooIq7iOJwyZeL8dfv7jN5nQ6I | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (1cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 45 AntiVirus engines on VirusTotal as malicious |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| info | CAB_file_format | CAB archive file | binaries (upload) |
| info | Microsoft_Office_File_Zero | Microsoft Office File | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|