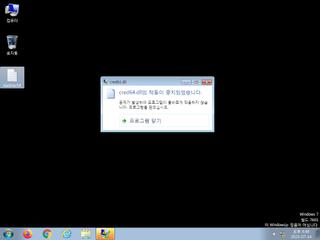
ScreenShot
| Created | 2023.07.14 16:48 | Machine | s1_win7_x6401 |
| Filename | cred64.dll | ||
| Type | PE32+ executable (DLL) (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 51 detected (Common, Malicious, score, Cerbu, Trojanpws, Artemis, Amadey, Save, TrojanPSW, confidence, 100%, ABRisk, SYIP, Attribute, HighConfidence, high confidence, Zusy, PWSX, Gencirc, AGEN, R002C0DG723, Steal, Detected, ai score=87, unsafe, Convagent, 7c4j9hQ2SPS, ilbTmXZSw+Y, susgen) | ||
| md5 | 5ac4952f9d0b64a682762d2ef24c48dc | ||
| sha256 | b73a969f9b129f8e89c49f1697078480af1d922ce10607fe3b851d9f6bb428b3 | ||
| ssdeep | 24576:4aSMLyrm87DcT+RZCPbZ1HslyolNVwkVGivKBDy:8m87DcTsZ6Z1HDWrVGivKBDy | ||
| imphash | 907e684baa019f5bd80cf160486e7eec | ||
| impfuzzy | 96:DpvZtu7Ze6BF1V5g4uQaR6xbDtQ8Bg99tFzzNTk:7tu7Z3Fzay+7fTk | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 51 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | Checks if process is being debugged by a debugger |
| info | One or more processes crashed |
| info | Queries for the computername |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | This executable has a PDB path |
| info | Tries to locate where the browsers are installed |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | infoStealer_browser_b_Zero | browser info stealer | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
CRYPT32.dll
0x1800d7058 CryptUnprotectData
KERNEL32.dll
0x1800d7068 LeaveCriticalSection
0x1800d7070 InitializeCriticalSection
0x1800d7078 SetFilePointer
0x1800d7080 GetFullPathNameA
0x1800d7088 SetEndOfFile
0x1800d7090 UnlockFileEx
0x1800d7098 GetTempPathW
0x1800d70a0 CreateMutexW
0x1800d70a8 WaitForSingleObject
0x1800d70b0 CreateFileW
0x1800d70b8 GetFileAttributesW
0x1800d70c0 GetCurrentThreadId
0x1800d70c8 UnmapViewOfFile
0x1800d70d0 HeapValidate
0x1800d70d8 HeapSize
0x1800d70e0 MultiByteToWideChar
0x1800d70e8 Sleep
0x1800d70f0 GetTempPathA
0x1800d70f8 FormatMessageW
0x1800d7100 GetDiskFreeSpaceA
0x1800d7108 GetLastError
0x1800d7110 GetFileAttributesA
0x1800d7118 GetFileAttributesExW
0x1800d7120 OutputDebugStringW
0x1800d7128 CreateFileA
0x1800d7130 LoadLibraryA
0x1800d7138 WaitForSingleObjectEx
0x1800d7140 DeleteFileA
0x1800d7148 DeleteFileW
0x1800d7150 HeapReAlloc
0x1800d7158 CloseHandle
0x1800d7160 GetSystemInfo
0x1800d7168 LoadLibraryW
0x1800d7170 HeapAlloc
0x1800d7178 HeapCompact
0x1800d7180 HeapDestroy
0x1800d7188 UnlockFile
0x1800d7190 GetProcAddress
0x1800d7198 CreateFileMappingA
0x1800d71a0 LocalFree
0x1800d71a8 LockFileEx
0x1800d71b0 GetFileSize
0x1800d71b8 DeleteCriticalSection
0x1800d71c0 GetCurrentProcessId
0x1800d71c8 GetProcessHeap
0x1800d71d0 SystemTimeToFileTime
0x1800d71d8 FreeLibrary
0x1800d71e0 WideCharToMultiByte
0x1800d71e8 GetSystemTimeAsFileTime
0x1800d71f0 GetSystemTime
0x1800d71f8 FormatMessageA
0x1800d7200 CreateFileMappingW
0x1800d7208 MapViewOfFile
0x1800d7210 QueryPerformanceCounter
0x1800d7218 GetTickCount
0x1800d7220 FlushFileBuffers
0x1800d7228 SetHandleInformation
0x1800d7230 FindFirstFileA
0x1800d7238 Wow64DisableWow64FsRedirection
0x1800d7240 K32GetModuleFileNameExW
0x1800d7248 FindNextFileA
0x1800d7250 CreatePipe
0x1800d7258 PeekNamedPipe
0x1800d7260 lstrlenA
0x1800d7268 FindClose
0x1800d7270 GetCurrentDirectoryA
0x1800d7278 lstrcatA
0x1800d7280 OpenProcess
0x1800d7288 SetCurrentDirectoryA
0x1800d7290 CreateToolhelp32Snapshot
0x1800d7298 ProcessIdToSessionId
0x1800d72a0 CopyFileA
0x1800d72a8 Wow64RevertWow64FsRedirection
0x1800d72b0 Process32NextW
0x1800d72b8 Process32FirstW
0x1800d72c0 CreateThread
0x1800d72c8 CreateProcessA
0x1800d72d0 CreateDirectoryA
0x1800d72d8 WriteConsoleW
0x1800d72e0 OutputDebugStringA
0x1800d72e8 GetDiskFreeSpaceW
0x1800d72f0 WriteFile
0x1800d72f8 GetFullPathNameW
0x1800d7300 EnterCriticalSection
0x1800d7308 HeapFree
0x1800d7310 HeapCreate
0x1800d7318 TryEnterCriticalSection
0x1800d7320 ReadFile
0x1800d7328 AreFileApisANSI
0x1800d7330 LockFile
0x1800d7338 ReadConsoleW
0x1800d7340 SetFilePointerEx
0x1800d7348 GetConsoleMode
0x1800d7350 GetConsoleCP
0x1800d7358 SetEnvironmentVariableW
0x1800d7360 FreeEnvironmentStringsW
0x1800d7368 GetEnvironmentStringsW
0x1800d7370 GetCommandLineW
0x1800d7378 GetCommandLineA
0x1800d7380 GetOEMCP
0x1800d7388 GetACP
0x1800d7390 IsValidCodePage
0x1800d7398 FindNextFileW
0x1800d73a0 FindFirstFileExW
0x1800d73a8 SetStdHandle
0x1800d73b0 GetCurrentDirectoryW
0x1800d73b8 RtlCaptureContext
0x1800d73c0 RtlLookupFunctionEntry
0x1800d73c8 RtlVirtualUnwind
0x1800d73d0 IsDebuggerPresent
0x1800d73d8 UnhandledExceptionFilter
0x1800d73e0 SetUnhandledExceptionFilter
0x1800d73e8 GetStartupInfoW
0x1800d73f0 IsProcessorFeaturePresent
0x1800d73f8 GetModuleHandleW
0x1800d7400 InitializeSListHead
0x1800d7408 SetLastError
0x1800d7410 InitializeCriticalSectionAndSpinCount
0x1800d7418 SwitchToThread
0x1800d7420 TlsAlloc
0x1800d7428 TlsGetValue
0x1800d7430 TlsSetValue
0x1800d7438 TlsFree
0x1800d7440 EncodePointer
0x1800d7448 DecodePointer
0x1800d7450 GetCPInfo
0x1800d7458 CompareStringW
0x1800d7460 LCMapStringW
0x1800d7468 GetLocaleInfoW
0x1800d7470 GetStringTypeW
0x1800d7478 RtlUnwindEx
0x1800d7480 RtlPcToFileHeader
0x1800d7488 RaiseException
0x1800d7490 InterlockedFlushSList
0x1800d7498 LoadLibraryExW
0x1800d74a0 ExitThread
0x1800d74a8 FreeLibraryAndExitThread
0x1800d74b0 GetModuleHandleExW
0x1800d74b8 GetDriveTypeW
0x1800d74c0 GetFileInformationByHandle
0x1800d74c8 GetFileType
0x1800d74d0 SystemTimeToTzSpecificLocalTime
0x1800d74d8 FileTimeToSystemTime
0x1800d74e0 GetCurrentProcess
0x1800d74e8 TerminateProcess
0x1800d74f0 ExitProcess
0x1800d74f8 GetModuleFileNameW
0x1800d7500 IsValidLocale
0x1800d7508 GetUserDefaultLCID
0x1800d7510 EnumSystemLocalesW
0x1800d7518 GetTimeZoneInformation
0x1800d7520 GetStdHandle
ADVAPI32.dll
0x1800d7000 GetSidSubAuthorityCount
0x1800d7008 RegEnumValueW
0x1800d7010 RegCloseKey
0x1800d7018 RegQueryInfoKeyW
0x1800d7020 RegQueryValueExA
0x1800d7028 RegOpenKeyExA
0x1800d7030 GetSidSubAuthority
0x1800d7038 GetUserNameA
0x1800d7040 LookupAccountNameA
0x1800d7048 GetSidIdentifierAuthority
SHELL32.dll
0x1800d7530 SHGetFolderPathA
0x1800d7538 SHFileOperationA
WININET.dll
0x1800d7548 HttpOpenRequestA
0x1800d7550 InternetWriteFile
0x1800d7558 InternetReadFile
0x1800d7560 InternetConnectA
0x1800d7568 HttpSendRequestA
0x1800d7570 InternetCloseHandle
0x1800d7578 InternetOpenA
0x1800d7580 HttpAddRequestHeadersA
0x1800d7588 HttpSendRequestExW
0x1800d7590 HttpEndRequestA
0x1800d7598 InternetOpenW
crypt.dll
0x1800d75a8 BCryptOpenAlgorithmProvider
0x1800d75b0 BCryptSetProperty
0x1800d75b8 BCryptGenerateSymmetricKey
0x1800d75c0 BCryptDecrypt
EAT(Export Address Table) Library
0x1800a65d0 Main
0x1800044d0 Save
CRYPT32.dll
0x1800d7058 CryptUnprotectData
KERNEL32.dll
0x1800d7068 LeaveCriticalSection
0x1800d7070 InitializeCriticalSection
0x1800d7078 SetFilePointer
0x1800d7080 GetFullPathNameA
0x1800d7088 SetEndOfFile
0x1800d7090 UnlockFileEx
0x1800d7098 GetTempPathW
0x1800d70a0 CreateMutexW
0x1800d70a8 WaitForSingleObject
0x1800d70b0 CreateFileW
0x1800d70b8 GetFileAttributesW
0x1800d70c0 GetCurrentThreadId
0x1800d70c8 UnmapViewOfFile
0x1800d70d0 HeapValidate
0x1800d70d8 HeapSize
0x1800d70e0 MultiByteToWideChar
0x1800d70e8 Sleep
0x1800d70f0 GetTempPathA
0x1800d70f8 FormatMessageW
0x1800d7100 GetDiskFreeSpaceA
0x1800d7108 GetLastError
0x1800d7110 GetFileAttributesA
0x1800d7118 GetFileAttributesExW
0x1800d7120 OutputDebugStringW
0x1800d7128 CreateFileA
0x1800d7130 LoadLibraryA
0x1800d7138 WaitForSingleObjectEx
0x1800d7140 DeleteFileA
0x1800d7148 DeleteFileW
0x1800d7150 HeapReAlloc
0x1800d7158 CloseHandle
0x1800d7160 GetSystemInfo
0x1800d7168 LoadLibraryW
0x1800d7170 HeapAlloc
0x1800d7178 HeapCompact
0x1800d7180 HeapDestroy
0x1800d7188 UnlockFile
0x1800d7190 GetProcAddress
0x1800d7198 CreateFileMappingA
0x1800d71a0 LocalFree
0x1800d71a8 LockFileEx
0x1800d71b0 GetFileSize
0x1800d71b8 DeleteCriticalSection
0x1800d71c0 GetCurrentProcessId
0x1800d71c8 GetProcessHeap
0x1800d71d0 SystemTimeToFileTime
0x1800d71d8 FreeLibrary
0x1800d71e0 WideCharToMultiByte
0x1800d71e8 GetSystemTimeAsFileTime
0x1800d71f0 GetSystemTime
0x1800d71f8 FormatMessageA
0x1800d7200 CreateFileMappingW
0x1800d7208 MapViewOfFile
0x1800d7210 QueryPerformanceCounter
0x1800d7218 GetTickCount
0x1800d7220 FlushFileBuffers
0x1800d7228 SetHandleInformation
0x1800d7230 FindFirstFileA
0x1800d7238 Wow64DisableWow64FsRedirection
0x1800d7240 K32GetModuleFileNameExW
0x1800d7248 FindNextFileA
0x1800d7250 CreatePipe
0x1800d7258 PeekNamedPipe
0x1800d7260 lstrlenA
0x1800d7268 FindClose
0x1800d7270 GetCurrentDirectoryA
0x1800d7278 lstrcatA
0x1800d7280 OpenProcess
0x1800d7288 SetCurrentDirectoryA
0x1800d7290 CreateToolhelp32Snapshot
0x1800d7298 ProcessIdToSessionId
0x1800d72a0 CopyFileA
0x1800d72a8 Wow64RevertWow64FsRedirection
0x1800d72b0 Process32NextW
0x1800d72b8 Process32FirstW
0x1800d72c0 CreateThread
0x1800d72c8 CreateProcessA
0x1800d72d0 CreateDirectoryA
0x1800d72d8 WriteConsoleW
0x1800d72e0 OutputDebugStringA
0x1800d72e8 GetDiskFreeSpaceW
0x1800d72f0 WriteFile
0x1800d72f8 GetFullPathNameW
0x1800d7300 EnterCriticalSection
0x1800d7308 HeapFree
0x1800d7310 HeapCreate
0x1800d7318 TryEnterCriticalSection
0x1800d7320 ReadFile
0x1800d7328 AreFileApisANSI
0x1800d7330 LockFile
0x1800d7338 ReadConsoleW
0x1800d7340 SetFilePointerEx
0x1800d7348 GetConsoleMode
0x1800d7350 GetConsoleCP
0x1800d7358 SetEnvironmentVariableW
0x1800d7360 FreeEnvironmentStringsW
0x1800d7368 GetEnvironmentStringsW
0x1800d7370 GetCommandLineW
0x1800d7378 GetCommandLineA
0x1800d7380 GetOEMCP
0x1800d7388 GetACP
0x1800d7390 IsValidCodePage
0x1800d7398 FindNextFileW
0x1800d73a0 FindFirstFileExW
0x1800d73a8 SetStdHandle
0x1800d73b0 GetCurrentDirectoryW
0x1800d73b8 RtlCaptureContext
0x1800d73c0 RtlLookupFunctionEntry
0x1800d73c8 RtlVirtualUnwind
0x1800d73d0 IsDebuggerPresent
0x1800d73d8 UnhandledExceptionFilter
0x1800d73e0 SetUnhandledExceptionFilter
0x1800d73e8 GetStartupInfoW
0x1800d73f0 IsProcessorFeaturePresent
0x1800d73f8 GetModuleHandleW
0x1800d7400 InitializeSListHead
0x1800d7408 SetLastError
0x1800d7410 InitializeCriticalSectionAndSpinCount
0x1800d7418 SwitchToThread
0x1800d7420 TlsAlloc
0x1800d7428 TlsGetValue
0x1800d7430 TlsSetValue
0x1800d7438 TlsFree
0x1800d7440 EncodePointer
0x1800d7448 DecodePointer
0x1800d7450 GetCPInfo
0x1800d7458 CompareStringW
0x1800d7460 LCMapStringW
0x1800d7468 GetLocaleInfoW
0x1800d7470 GetStringTypeW
0x1800d7478 RtlUnwindEx
0x1800d7480 RtlPcToFileHeader
0x1800d7488 RaiseException
0x1800d7490 InterlockedFlushSList
0x1800d7498 LoadLibraryExW
0x1800d74a0 ExitThread
0x1800d74a8 FreeLibraryAndExitThread
0x1800d74b0 GetModuleHandleExW
0x1800d74b8 GetDriveTypeW
0x1800d74c0 GetFileInformationByHandle
0x1800d74c8 GetFileType
0x1800d74d0 SystemTimeToTzSpecificLocalTime
0x1800d74d8 FileTimeToSystemTime
0x1800d74e0 GetCurrentProcess
0x1800d74e8 TerminateProcess
0x1800d74f0 ExitProcess
0x1800d74f8 GetModuleFileNameW
0x1800d7500 IsValidLocale
0x1800d7508 GetUserDefaultLCID
0x1800d7510 EnumSystemLocalesW
0x1800d7518 GetTimeZoneInformation
0x1800d7520 GetStdHandle
ADVAPI32.dll
0x1800d7000 GetSidSubAuthorityCount
0x1800d7008 RegEnumValueW
0x1800d7010 RegCloseKey
0x1800d7018 RegQueryInfoKeyW
0x1800d7020 RegQueryValueExA
0x1800d7028 RegOpenKeyExA
0x1800d7030 GetSidSubAuthority
0x1800d7038 GetUserNameA
0x1800d7040 LookupAccountNameA
0x1800d7048 GetSidIdentifierAuthority
SHELL32.dll
0x1800d7530 SHGetFolderPathA
0x1800d7538 SHFileOperationA
WININET.dll
0x1800d7548 HttpOpenRequestA
0x1800d7550 InternetWriteFile
0x1800d7558 InternetReadFile
0x1800d7560 InternetConnectA
0x1800d7568 HttpSendRequestA
0x1800d7570 InternetCloseHandle
0x1800d7578 InternetOpenA
0x1800d7580 HttpAddRequestHeadersA
0x1800d7588 HttpSendRequestExW
0x1800d7590 HttpEndRequestA
0x1800d7598 InternetOpenW
crypt.dll
0x1800d75a8 BCryptOpenAlgorithmProvider
0x1800d75b0 BCryptSetProperty
0x1800d75b8 BCryptGenerateSymmetricKey
0x1800d75c0 BCryptDecrypt
EAT(Export Address Table) Library
0x1800a65d0 Main
0x1800044d0 Save