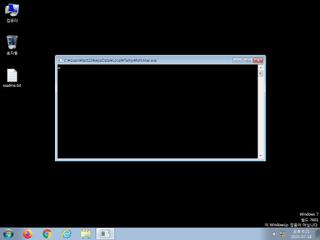
ScreenShot
| Created | 2023.07.18 18:30 | Machine | s1_win7_x6401 |
| Filename | lolMiner.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | |||
| VT API (file) | 43 detected (Lazy, Artemis, CoinMiner, V4dy, Miners, grayware, confidence, ABApplication, FEOG, Attribute, HighConfidence, malicious, moderate confidence, RiskTool, BitCoinMiner, ootc, MiscX, FalseSign, Uwhl, Tool, high, score, Generic Reputation PUA, Detected, Miner3, ai score=79, unsafe, HackTool, zgu3mDMiJD, Igent, bZ90oo, susgen, Miner) | ||
| md5 | 055eaec478c4a8490041b8fa3db1119d | ||
| sha256 | 2d4adb8e894b22d6c60c3877995ba5e9845ec6005fc95382c395396eb84b1e73 | ||
| ssdeep | 196608:83OKhONe8nIO7AEXz+992YhlXPBaPS0yc+PfSWUQpdiRNC:83OKIe8eEq99Xhl/BuTQpdd | ||
| imphash | 21e7596d2b02d580d9a6679904cdb8d4 | ||
| impfuzzy | 6:omRgAAKXKBJAEoZ/OEGDzyRkNXYEJ5/ML1KcA5RMRQnqW3JvA:omRgAAdABZG/Dzpzt5RMRd | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 43 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is compressed using UPX |
| info | Checks if process is being debugged by a debugger |
Rules (2cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
ADVAPI32.dll
0x14475a2a4 RegCloseKey
CRYPT32.dll
0x14475a2b4 CertOpenStore
KERNEL32.DLL
0x14475a2c4 LoadLibraryA
0x14475a2cc ExitProcess
0x14475a2d4 GetProcAddress
0x14475a2dc VirtualProtect
MSWSOCK.dll
0x14475a2ec AcceptEx
Normaliz.dll
0x14475a2fc IdnToAscii
SETUPAPI.dll
0x14475a30c SetupDiGetClassDevsA
USER32.dll
0x14475a31c ShowWindow
WLDAP32.dll
0x14475a32c None
WS2_32.dll
0x14475a33c gethostname
EAT(Export Address Table) is none
ADVAPI32.dll
0x14475a2a4 RegCloseKey
CRYPT32.dll
0x14475a2b4 CertOpenStore
KERNEL32.DLL
0x14475a2c4 LoadLibraryA
0x14475a2cc ExitProcess
0x14475a2d4 GetProcAddress
0x14475a2dc VirtualProtect
MSWSOCK.dll
0x14475a2ec AcceptEx
Normaliz.dll
0x14475a2fc IdnToAscii
SETUPAPI.dll
0x14475a30c SetupDiGetClassDevsA
USER32.dll
0x14475a31c ShowWindow
WLDAP32.dll
0x14475a32c None
WS2_32.dll
0x14475a33c gethostname
EAT(Export Address Table) is none