| Created |
2023.07.19 09:10 |
Machine |
s1_win7_x6402 |
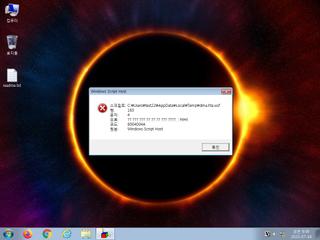
| Filename |
dma.hta |
| Type |
HTML document, ASCII text, with very long lines, with CRLF line terminators |
| AI Score |
Not founds |
Behavior Score |
|
| ZERO API |
file : clean |
| VT API (file) |
17 detected (Electryon, Kryptik, Dinihou, dnzdga, ai score=88, suspected of VBS, EncodedMalware, TOPIS, na7CvnGpXAG, Outbreak) |
| md5 |
9302aa42d7bd92c8bfe93a441fe7b147 |
| sha256 |
5931d0fcbee63ad38f2e564ed922316351650703d78a76d8af5ffc35b2732ede |
| ssdeep |
768:PgKBcO1E+jUdqhL8TAjTlESkuG4SVQpUdksfEfuA1hk7:PgK7UgJqAjRESkuG4S6UWssm4hk7 |
| imphash |
|
| impfuzzy |
|