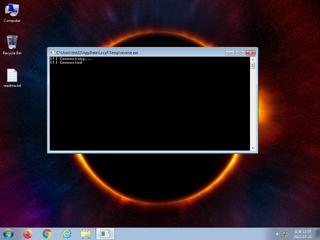
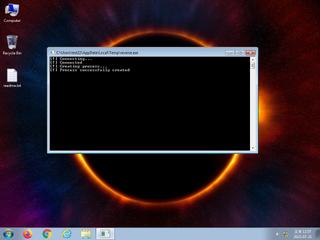
ScreenShot
| Created | 2023.07.21 13:01 | Machine | s1_win7_x6403 |
| Filename | reverse.exe | ||
| Type | PE32 executable (console) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | |||
| VT API (file) | 32 detected (AIDetectMalware, unsafe, Reverseshell, Vtf3, ZexaF, c0Y@aSjvDyg, Eldorado, Attribute, HighConfidence, malicious, high confidence, score, GenericKD, high, Static AI, Suspicious PE, Casdet, Detected, Chgt, CLOUD, Outbreak, susgen, confidence, 100%) | ||
| md5 | 80cc187a15b6b6340385922631bad640 | ||
| sha256 | 8e40b48d06466da3b63341dc62dd0403c57fc2f017317d842ea86d601dde38e5 | ||
| ssdeep | 384:0jXpuEDKOlrP95I4GS1dQhNz7YrgAlBCxIgVbPeuaBU3losjuzZ6UwYRGZqm7aLm:MuEDlV70HA6zPP3lLuzZPKq9WvlnZxb | ||
| imphash | e623cecc3195834a15144a4d38dde690 | ||
| impfuzzy | 24:gfCejrOov1lDIcLVbj9X53Qr9WNOq6QGMZSAKkuRT:gfCCaVc5tXlhNOq6QGxT | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 32 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| notice | Creates a suspicious process |
| info | Command line console output was observed |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x408170 CloseHandle
0x408174 CreateProcessA
0x408178 DeleteCriticalSection
0x40817c EnterCriticalSection
0x408180 ExitProcess
0x408184 FindClose
0x408188 FindFirstFileA
0x40818c FindNextFileA
0x408190 FreeLibrary
0x408194 GetCommandLineA
0x408198 GetLastError
0x40819c GetModuleHandleA
0x4081a0 GetProcAddress
0x4081a4 InitializeCriticalSection
0x4081a8 LeaveCriticalSection
0x4081ac LoadLibraryA
0x4081b0 SetUnhandledExceptionFilter
0x4081b4 TlsGetValue
0x4081b8 VirtualProtect
0x4081bc VirtualQuery
0x4081c0 WaitForSingleObject
msvcrt.dll
0x4081c8 _strdup
0x4081cc _stricoll
msvcrt.dll
0x4081d4 __getmainargs
0x4081d8 __mb_cur_max
0x4081dc __p__environ
0x4081e0 __p__fmode
0x4081e4 __set_app_type
0x4081e8 _cexit
0x4081ec _errno
0x4081f0 _fpreset
0x4081f4 _fullpath
0x4081f8 _iob
0x4081fc _isctype
0x408200 _onexit
0x408204 _pctype
0x408208 _setmode
0x40820c abort
0x408210 atexit
0x408214 calloc
0x408218 free
0x40821c fwrite
0x408220 malloc
0x408224 mbstowcs
0x408228 memcpy
0x40822c memset
0x408230 puts
0x408234 realloc
0x408238 setlocale
0x40823c signal
0x408240 strcoll
0x408244 strlen
0x408248 tolower
0x40824c vfprintf
0x408250 wcstombs
WS2_32.dll
0x408258 WSACleanup
0x40825c WSAConnect
0x408260 WSASocketA
0x408264 WSAStartup
0x408268 closesocket
0x40826c htons
0x408270 inet_addr
0x408274 recv
EAT(Export Address Table) is none
KERNEL32.dll
0x408170 CloseHandle
0x408174 CreateProcessA
0x408178 DeleteCriticalSection
0x40817c EnterCriticalSection
0x408180 ExitProcess
0x408184 FindClose
0x408188 FindFirstFileA
0x40818c FindNextFileA
0x408190 FreeLibrary
0x408194 GetCommandLineA
0x408198 GetLastError
0x40819c GetModuleHandleA
0x4081a0 GetProcAddress
0x4081a4 InitializeCriticalSection
0x4081a8 LeaveCriticalSection
0x4081ac LoadLibraryA
0x4081b0 SetUnhandledExceptionFilter
0x4081b4 TlsGetValue
0x4081b8 VirtualProtect
0x4081bc VirtualQuery
0x4081c0 WaitForSingleObject
msvcrt.dll
0x4081c8 _strdup
0x4081cc _stricoll
msvcrt.dll
0x4081d4 __getmainargs
0x4081d8 __mb_cur_max
0x4081dc __p__environ
0x4081e0 __p__fmode
0x4081e4 __set_app_type
0x4081e8 _cexit
0x4081ec _errno
0x4081f0 _fpreset
0x4081f4 _fullpath
0x4081f8 _iob
0x4081fc _isctype
0x408200 _onexit
0x408204 _pctype
0x408208 _setmode
0x40820c abort
0x408210 atexit
0x408214 calloc
0x408218 free
0x40821c fwrite
0x408220 malloc
0x408224 mbstowcs
0x408228 memcpy
0x40822c memset
0x408230 puts
0x408234 realloc
0x408238 setlocale
0x40823c signal
0x408240 strcoll
0x408244 strlen
0x408248 tolower
0x40824c vfprintf
0x408250 wcstombs
WS2_32.dll
0x408258 WSACleanup
0x40825c WSAConnect
0x408260 WSASocketA
0x408264 WSAStartup
0x408268 closesocket
0x40826c htons
0x408270 inet_addr
0x408274 recv
EAT(Export Address Table) is none