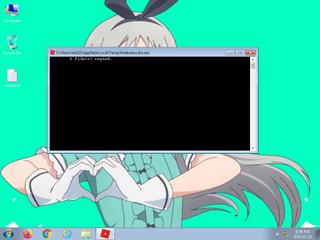
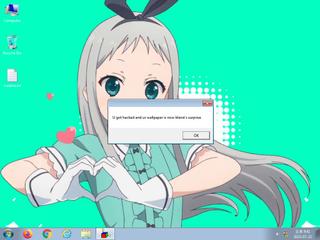
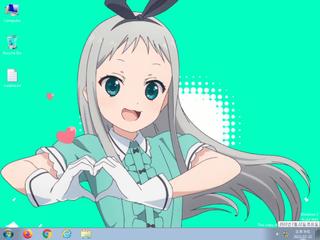
ScreenShot
| Created | 2023.07.22 21:48 | Machine | s1_win7_x6403 |
| Filename | freebobux.bin.exe | ||
| Type | PE32 executable (console) Intel 80386, for MS Windows, UPX compressed | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 32 detected (GenericKD, unsafe, V6dm, Attribute, HighConfidence, malicious, moderate confidence, BadJoke, Artemis, moderate, score, Generic Reputation PUA, HackTool, KMSAuto, Wacatac, Detected, TrojanPSW, Zbot, R002H09BL23, Zpevdo, CLOUD, susgen, PossibleThreat) | ||
| md5 | 794b00893a1b95ade9379710821ac1a4 | ||
| sha256 | 5ac42d75e244d33856971120a25bd77f2c0712177384dfa61fb90c0e7790d34c | ||
| ssdeep | 12288:QLttwyELMYnrfWxYLlHVyEaX9/7tWsGQyWkbtRoSxB:8ttIMYnoYBVyP97t99Ut | ||
| imphash | 1d88d597200c0081784c27940d743ec5 | ||
| impfuzzy | 6:dBJAEHGDzyRlbRmVOZ/GlclHgc9WNsYbtcUEYyAiWB:VA/DzqYOZOD8YyAr | ||
Network IP location
Signature (14cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 32 AntiVirus engines on VirusTotal as malicious |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| watch | The process wscript.exe wrote an executable file to disk |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | The executable is compressed using UPX |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Command line console output was observed |
| info | One or more processes crashed |
| info | The executable uses a known packer |
Rules (17cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | anti_dbg | Checks if being debugged | memory |
| info | bmp_file_format | bmp file format | binaries (download) |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.DLL
0x83d5a8 LoadLibraryA
0x83d5ac GetProcAddress
0x83d5b0 VirtualProtect
0x83d5b4 VirtualAlloc
0x83d5b8 VirtualFree
0x83d5bc ExitProcess
COMCTL32.dll
0x83d5c4 InitCommonControls
GDI32.dll
0x83d5cc SetBkColor
MSVCRT.dll
0x83d5d4 memset
OLE32.dll
0x83d5dc CoInitialize
SHELL32.dll
0x83d5e4 ShellExecuteExA
SHLWAPI.dll
0x83d5ec PathQuoteSpacesA
USER32.dll
0x83d5f4 IsChild
EAT(Export Address Table) is none
KERNEL32.DLL
0x83d5a8 LoadLibraryA
0x83d5ac GetProcAddress
0x83d5b0 VirtualProtect
0x83d5b4 VirtualAlloc
0x83d5b8 VirtualFree
0x83d5bc ExitProcess
COMCTL32.dll
0x83d5c4 InitCommonControls
GDI32.dll
0x83d5cc SetBkColor
MSVCRT.dll
0x83d5d4 memset
OLE32.dll
0x83d5dc CoInitialize
SHELL32.dll
0x83d5e4 ShellExecuteExA
SHLWAPI.dll
0x83d5ec PathQuoteSpacesA
USER32.dll
0x83d5f4 IsChild
EAT(Export Address Table) is none