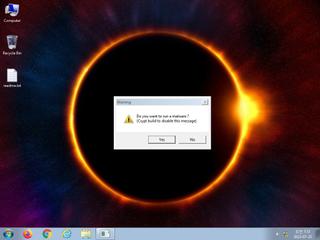
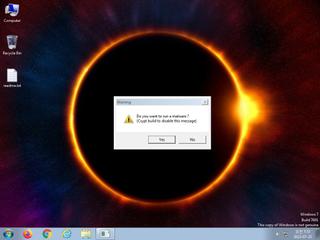
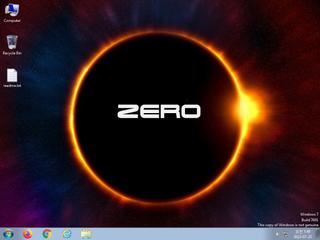
ScreenShot
| Created | 2023.07.25 07:51 | Machine | s1_win7_x6403 |
| Filename | LummaC2.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | |||
| md5 | 16f2d0aa122b49bd7f7ca17eb28e5df5 | ||
| sha256 | d5998de73a2e6ac2fafe81270e33b6a9fd8cef605cb56603456029b8b598c077 | ||
| ssdeep | 12288:alJxRPSvnEVL9MtT6Mgzwni786xNPB8bKbb:altSS9M56Mgz3BxNZt | ||
| imphash | 67ce5c1f8081cdf08e5f30c58a340ff6 | ||
| impfuzzy | 48:UXXOtCt6x3Bn1Lqb1hBjO6rRRgly4rzF5bMcLEhOhb6:IXCCt6jn1LQhVO6rR69voAh+ | ||
Network IP location
Signature (15cnts)
| Level | Description |
|---|---|
| watch | Appends a known CryptoMix ransomware file extension to files that have been encrypted |
| watch | Attempts to access Bitcoin/ALTCoin wallets |
| watch | Collects information about installed applications |
| watch | Detects Virtual Machines through their custom firmware |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | One or more potentially interesting buffers were extracted |
| notice | Performs some HTTP requests |
| notice | Queries for potentially installed applications |
| notice | Repeatedly searches for a not-found process |
| notice | Searches running processes potentially to identify processes for sandbox evasion |
| notice | Sends data using the HTTP POST Method |
| notice | Steals private information from local Internet browsers |
| info | Checks amount of memory in system |
| info | Queries for the computername |
| info | Tries to locate where the browsers are installed |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (5cnts) ?
Suricata ids
ET MALWARE Win32/Lumma Stealer Data Exfiltration Attempt M2
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x45e240 CloseHandle
0x45e244 CompareStringW
0x45e248 CreateDirectoryW
0x45e24c CreateFileA
0x45e250 CreateFileW
0x45e254 CreateProcessW
0x45e258 DecodePointer
0x45e25c DeleteCriticalSection
0x45e260 DeleteFileW
0x45e264 EncodePointer
0x45e268 EnterCriticalSection
0x45e26c ExitProcess
0x45e270 ExpandEnvironmentStringsW
0x45e274 FileTimeToSystemTime
0x45e278 FindClose
0x45e27c FindFirstFileExW
0x45e280 FindNextFileW
0x45e284 FlushFileBuffers
0x45e288 FreeEnvironmentStringsW
0x45e28c FreeLibrary
0x45e290 GetACP
0x45e294 GetCPInfo
0x45e298 GetCommandLineA
0x45e29c GetCommandLineW
0x45e2a0 GetComputerNameExA
0x45e2a4 GetConsoleMode
0x45e2a8 GetConsoleOutputCP
0x45e2ac GetCurrentDirectoryW
0x45e2b0 GetCurrentProcess
0x45e2b4 GetCurrentProcessId
0x45e2b8 GetCurrentThreadId
0x45e2bc GetDriveTypeW
0x45e2c0 GetEnvironmentStringsW
0x45e2c4 GetFileInformationByHandle
0x45e2c8 GetFileSizeEx
0x45e2cc GetFileType
0x45e2d0 GetFullPathNameW
0x45e2d4 GetLastError
0x45e2d8 GetModuleFileNameA
0x45e2dc GetModuleFileNameW
0x45e2e0 GetModuleHandleExW
0x45e2e4 GetModuleHandleW
0x45e2e8 GetOEMCP
0x45e2ec GetProcAddress
0x45e2f0 GetProcessHeap
0x45e2f4 GetStartupInfoW
0x45e2f8 GetStdHandle
0x45e2fc GetStringTypeW
0x45e300 GetSystemTimeAsFileTime
0x45e304 GetTimeZoneInformation
0x45e308 HeapAlloc
0x45e30c HeapFree
0x45e310 HeapReAlloc
0x45e314 HeapSize
0x45e318 InitializeCriticalSectionAndSpinCount
0x45e31c InitializeSListHead
0x45e320 IsDebuggerPresent
0x45e324 IsProcessorFeaturePresent
0x45e328 IsValidCodePage
0x45e32c LCMapStringW
0x45e330 LeaveCriticalSection
0x45e334 LoadLibraryA
0x45e338 LoadLibraryExW
0x45e33c LoadLibraryW
0x45e340 MultiByteToWideChar
0x45e344 PeekNamedPipe
0x45e348 QueryPerformanceCounter
0x45e34c RaiseException
0x45e350 ReadConsoleW
0x45e354 ReadFile
0x45e358 RtlUnwind
0x45e35c SetEndOfFile
0x45e360 SetEnvironmentVariableW
0x45e364 SetFilePointerEx
0x45e368 SetFileTime
0x45e36c SetLastError
0x45e370 SetStdHandle
0x45e374 SetUnhandledExceptionFilter
0x45e378 SystemTimeToFileTime
0x45e37c SystemTimeToTzSpecificLocalTime
0x45e380 TerminateProcess
0x45e384 TlsAlloc
0x45e388 TlsFree
0x45e38c TlsGetValue
0x45e390 TlsSetValue
0x45e394 TzSpecificLocalTimeToSystemTime
0x45e398 UnhandledExceptionFilter
0x45e39c WideCharToMultiByte
0x45e3a0 WinExec
0x45e3a4 WriteConsoleW
0x45e3a8 WriteFile
0x45e3ac lstrcatW
0x45e3b0 lstrcmpW
0x45e3b4 lstrcmpiW
0x45e3b8 lstrlenW
USER32.dll
0x45e3c0 EnumDisplayDevicesA
0x45e3c4 GetDC
0x45e3c8 GetDesktopWindow
0x45e3cc GetSystemMetrics
0x45e3d0 ReleaseDC
0x45e3d4 SystemParametersInfoW
0x45e3d8 wsprintfW
GDI32.dll
0x45e3e0 BitBlt
0x45e3e4 CreateCompatibleBitmap
0x45e3e8 CreateCompatibleDC
0x45e3ec CreateDCW
0x45e3f0 DeleteDC
0x45e3f4 DeleteObject
0x45e3f8 GetDIBits
0x45e3fc GetObjectW
0x45e400 SelectObject
ADVAPI32.dll
0x45e408 RegCloseKey
0x45e40c RegEnumKeyExW
0x45e410 RegOpenKeyExW
0x45e414 RegQueryValueExW
WINHTTP.dll
0x45e41c WinHttpCloseHandle
0x45e420 WinHttpConnect
0x45e424 WinHttpCrackUrl
0x45e428 WinHttpOpen
0x45e42c WinHttpOpenRequest
0x45e430 WinHttpQueryDataAvailable
0x45e434 WinHttpReadData
0x45e438 WinHttpReceiveResponse
0x45e43c WinHttpSendRequest
WININET.dll
0x45e444 InternetQueryDataAvailable
0x45e448 InternetReadFile
CRYPT32.dll
0x45e450 CryptStringToBinaryA
EAT(Export Address Table) is none
KERNEL32.dll
0x45e240 CloseHandle
0x45e244 CompareStringW
0x45e248 CreateDirectoryW
0x45e24c CreateFileA
0x45e250 CreateFileW
0x45e254 CreateProcessW
0x45e258 DecodePointer
0x45e25c DeleteCriticalSection
0x45e260 DeleteFileW
0x45e264 EncodePointer
0x45e268 EnterCriticalSection
0x45e26c ExitProcess
0x45e270 ExpandEnvironmentStringsW
0x45e274 FileTimeToSystemTime
0x45e278 FindClose
0x45e27c FindFirstFileExW
0x45e280 FindNextFileW
0x45e284 FlushFileBuffers
0x45e288 FreeEnvironmentStringsW
0x45e28c FreeLibrary
0x45e290 GetACP
0x45e294 GetCPInfo
0x45e298 GetCommandLineA
0x45e29c GetCommandLineW
0x45e2a0 GetComputerNameExA
0x45e2a4 GetConsoleMode
0x45e2a8 GetConsoleOutputCP
0x45e2ac GetCurrentDirectoryW
0x45e2b0 GetCurrentProcess
0x45e2b4 GetCurrentProcessId
0x45e2b8 GetCurrentThreadId
0x45e2bc GetDriveTypeW
0x45e2c0 GetEnvironmentStringsW
0x45e2c4 GetFileInformationByHandle
0x45e2c8 GetFileSizeEx
0x45e2cc GetFileType
0x45e2d0 GetFullPathNameW
0x45e2d4 GetLastError
0x45e2d8 GetModuleFileNameA
0x45e2dc GetModuleFileNameW
0x45e2e0 GetModuleHandleExW
0x45e2e4 GetModuleHandleW
0x45e2e8 GetOEMCP
0x45e2ec GetProcAddress
0x45e2f0 GetProcessHeap
0x45e2f4 GetStartupInfoW
0x45e2f8 GetStdHandle
0x45e2fc GetStringTypeW
0x45e300 GetSystemTimeAsFileTime
0x45e304 GetTimeZoneInformation
0x45e308 HeapAlloc
0x45e30c HeapFree
0x45e310 HeapReAlloc
0x45e314 HeapSize
0x45e318 InitializeCriticalSectionAndSpinCount
0x45e31c InitializeSListHead
0x45e320 IsDebuggerPresent
0x45e324 IsProcessorFeaturePresent
0x45e328 IsValidCodePage
0x45e32c LCMapStringW
0x45e330 LeaveCriticalSection
0x45e334 LoadLibraryA
0x45e338 LoadLibraryExW
0x45e33c LoadLibraryW
0x45e340 MultiByteToWideChar
0x45e344 PeekNamedPipe
0x45e348 QueryPerformanceCounter
0x45e34c RaiseException
0x45e350 ReadConsoleW
0x45e354 ReadFile
0x45e358 RtlUnwind
0x45e35c SetEndOfFile
0x45e360 SetEnvironmentVariableW
0x45e364 SetFilePointerEx
0x45e368 SetFileTime
0x45e36c SetLastError
0x45e370 SetStdHandle
0x45e374 SetUnhandledExceptionFilter
0x45e378 SystemTimeToFileTime
0x45e37c SystemTimeToTzSpecificLocalTime
0x45e380 TerminateProcess
0x45e384 TlsAlloc
0x45e388 TlsFree
0x45e38c TlsGetValue
0x45e390 TlsSetValue
0x45e394 TzSpecificLocalTimeToSystemTime
0x45e398 UnhandledExceptionFilter
0x45e39c WideCharToMultiByte
0x45e3a0 WinExec
0x45e3a4 WriteConsoleW
0x45e3a8 WriteFile
0x45e3ac lstrcatW
0x45e3b0 lstrcmpW
0x45e3b4 lstrcmpiW
0x45e3b8 lstrlenW
USER32.dll
0x45e3c0 EnumDisplayDevicesA
0x45e3c4 GetDC
0x45e3c8 GetDesktopWindow
0x45e3cc GetSystemMetrics
0x45e3d0 ReleaseDC
0x45e3d4 SystemParametersInfoW
0x45e3d8 wsprintfW
GDI32.dll
0x45e3e0 BitBlt
0x45e3e4 CreateCompatibleBitmap
0x45e3e8 CreateCompatibleDC
0x45e3ec CreateDCW
0x45e3f0 DeleteDC
0x45e3f4 DeleteObject
0x45e3f8 GetDIBits
0x45e3fc GetObjectW
0x45e400 SelectObject
ADVAPI32.dll
0x45e408 RegCloseKey
0x45e40c RegEnumKeyExW
0x45e410 RegOpenKeyExW
0x45e414 RegQueryValueExW
WINHTTP.dll
0x45e41c WinHttpCloseHandle
0x45e420 WinHttpConnect
0x45e424 WinHttpCrackUrl
0x45e428 WinHttpOpen
0x45e42c WinHttpOpenRequest
0x45e430 WinHttpQueryDataAvailable
0x45e434 WinHttpReadData
0x45e438 WinHttpReceiveResponse
0x45e43c WinHttpSendRequest
WININET.dll
0x45e444 InternetQueryDataAvailable
0x45e448 InternetReadFile
CRYPT32.dll
0x45e450 CryptStringToBinaryA
EAT(Export Address Table) is none