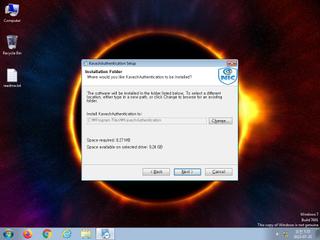
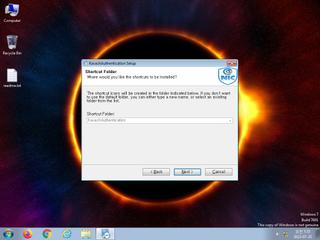
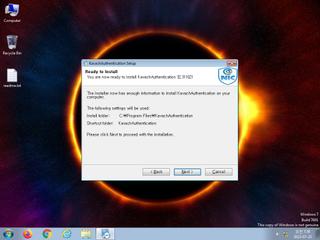
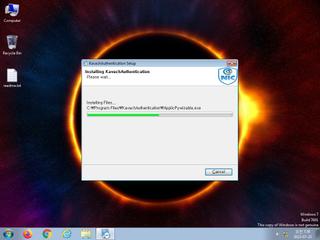
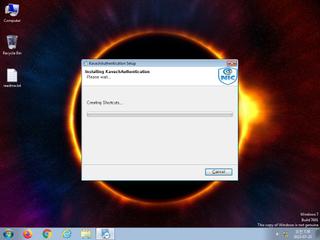
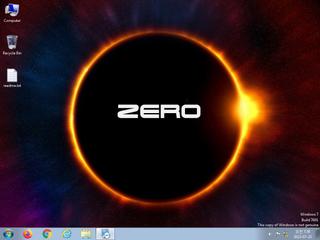
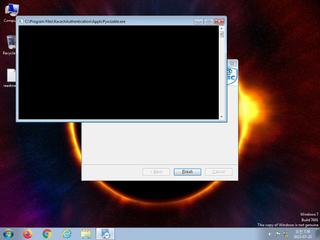
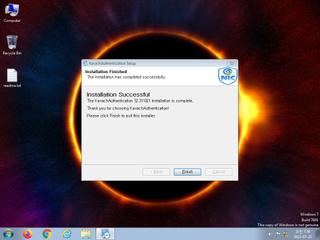
ScreenShot
| Created | 2023.07.25 07:45 | Machine | s1_win7_x6403 |
| Filename | KavachAuthentication%20Updater.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 18 detected (malicious, moderate confidence, Artemis, V9fv, score, AGEN, Generic ML PUA, CoinMiner, Casdet, Detected, SparkRat, Biodata, GNVQ1TR) | ||
| md5 | 2e66189aa1b6fd345a9c13124844ebbc | ||
| sha256 | bdee4edbe7adf842b519a47d964e64b219700b2ba1d7faf4b899e34bd63006b7 | ||
| ssdeep | 98304:4CPL/ezqAMdGUFI6wJ1cak9pnNhtxVHeI30CPFCxfM30pkN7Ij5giDHX:4gL/ezTgA1LkNH+g0zxML7mR | ||
| imphash | 838dd9fbdbb409224ad0e13122a109ae | ||
| impfuzzy | 48:hylnpVOIb16mecfYtbMZ0cfGT+KQ4zuFbv:hylpVNb1PecfYtbM6cmgv | ||
Network IP location
Signature (15cnts)
| Level | Description |
|---|---|
| watch | Detects the presence of Wine emulator |
| watch | Drops a binary and executes it |
| watch | File has been identified by 18 AntiVirus engines on VirusTotal as malicious |
| watch | Looks for the Windows Idle Time to determine the uptime |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a shortcut to an executable file |
| notice | Creates executable files on the filesystem |
| notice | Potentially malicious URLs were found in the process memory dump |
| notice | Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Collects information to fingerprint the system (MachineGuid |
| info | Queries for the computername |
Rules (45cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Emotet_1_Zero | Win32 Trojan Emotet | binaries (download) |
| danger | Win32_Trojan_Emotet_1_Zero | Win32 Trojan Emotet | binaries (upload) |
| watch | Antivirus | Contains references to security software | binaries (download) |
| watch | ASPack_Zero | ASPack packed file | binaries (download) |
| watch | ASPack_Zero | ASPack packed file | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | Network_Downloader | File Downloader | binaries (download) |
| watch | Network_Downloader | File Downloader | binaries (upload) |
| watch | Network_Downloader | File Downloader | memory |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | Create_Service | Create a windows service | memory |
| notice | Escalate_priviledges | Escalate priviledges | memory |
| notice | Generic_PWS_Memory_Zero | PWS Memory | memory |
| notice | KeyLogger | Run a KeyLogger | memory |
| notice | Network_DNS | Communications use DNS | memory |
| notice | Network_HTTP | Communications over HTTP | memory |
| notice | Network_TCP_Socket | Communications over RAW Socket | memory |
| notice | Persistence | Install itself for autorun at Windows startup | memory |
| notice | ScreenShot | Take ScreenShot | memory |
| notice | Str_Win32_Http_API | Match Windows Http API call | memory |
| notice | Str_Win32_Internet_API | Match Windows Inet API call | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | bmp_file_format | bmp file format | binaries (download) |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerException__ConsoleCtrl | (no description) | memory |
| info | DebuggerException__SetConsoleCtrl | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_antivirus | Disable AntiVirus | memory |
| info | disable_dep | Bypass DEP | memory |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | JPEG_Format_Zero | JPEG Format | binaries (download) |
| info | Lnk_Format_Zero | LNK Format | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
| info | win_hook | Affect hook table | memory |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x140008018 LoadLibraryA
0x140008020 lstrcpyA
0x140008028 lstrcatA
0x140008030 lstrlenA
0x140008038 GetSystemDirectoryA
0x140008040 GetProcAddress
0x140008048 GetModuleHandleA
0x140008050 _lclose
0x140008058 GetModuleFileNameA
0x140008060 _lread
0x140008068 _llseek
0x140008070 _lopen
0x140008078 _lwrite
0x140008080 _lcreat
0x140008088 CreateDirectoryA
0x140008090 SetCurrentDirectoryA
0x140008098 GetDiskFreeSpaceA
0x1400080a0 GetFileAttributesA
0x1400080a8 CompareStringA
0x1400080b0 DeleteFileA
0x1400080b8 GetTempPathA
0x1400080c0 GetCurrentDirectoryA
0x1400080c8 CloseHandle
0x1400080d0 GetExitCodeProcess
0x1400080d8 GetLastError
0x1400080e0 LocalFree
0x1400080e8 GetCurrentProcess
0x1400080f0 MoveFileExA
0x1400080f8 GetStringTypeW
0x140008100 MultiByteToWideChar
0x140008108 LCMapStringW
0x140008110 HeapReAlloc
0x140008118 HeapSize
0x140008120 IsValidCodePage
0x140008128 Sleep
0x140008130 RemoveDirectoryA
0x140008138 FreeLibrary
0x140008140 GetOEMCP
0x140008148 GetACP
0x140008150 GetModuleHandleW
0x140008158 ExitProcess
0x140008160 DecodePointer
0x140008168 HeapFree
0x140008170 HeapAlloc
0x140008178 GetCommandLineA
0x140008180 GetStartupInfoW
0x140008188 InitializeCriticalSectionAndSpinCount
0x140008190 DeleteCriticalSection
0x140008198 LeaveCriticalSection
0x1400081a0 EnterCriticalSection
0x1400081a8 EncodePointer
0x1400081b0 LoadLibraryW
0x1400081b8 UnhandledExceptionFilter
0x1400081c0 SetUnhandledExceptionFilter
0x1400081c8 IsDebuggerPresent
0x1400081d0 RtlVirtualUnwind
0x1400081d8 RtlLookupFunctionEntry
0x1400081e0 RtlCaptureContext
0x1400081e8 TerminateProcess
0x1400081f0 FlsGetValue
0x1400081f8 FlsSetValue
0x140008200 FlsFree
0x140008208 SetLastError
0x140008210 GetCurrentThreadId
0x140008218 FlsAlloc
0x140008220 RtlUnwindEx
0x140008228 WriteFile
0x140008230 GetStdHandle
0x140008238 GetModuleFileNameW
0x140008240 HeapSetInformation
0x140008248 GetVersion
0x140008250 HeapCreate
0x140008258 FreeEnvironmentStringsW
0x140008260 WideCharToMultiByte
0x140008268 GetEnvironmentStringsW
0x140008270 SetHandleCount
0x140008278 GetFileType
0x140008280 QueryPerformanceCounter
0x140008288 GetTickCount
0x140008290 GetCurrentProcessId
0x140008298 GetSystemTimeAsFileTime
0x1400082a0 GetCPInfo
USER32.dll
0x1400082c0 TranslateMessage
0x1400082c8 DispatchMessageA
0x1400082d0 PeekMessageA
0x1400082d8 wsprintfA
0x1400082e0 LoadCursorA
0x1400082e8 SetCursor
0x1400082f0 MessageBoxA
0x1400082f8 MsgWaitForMultipleObjects
ADVAPI32.dll
0x140008000 GetTokenInformation
0x140008008 OpenProcessToken
SHELL32.dll
0x1400082b0 ShellExecuteExA
EAT(Export Address Table) is none
KERNEL32.dll
0x140008018 LoadLibraryA
0x140008020 lstrcpyA
0x140008028 lstrcatA
0x140008030 lstrlenA
0x140008038 GetSystemDirectoryA
0x140008040 GetProcAddress
0x140008048 GetModuleHandleA
0x140008050 _lclose
0x140008058 GetModuleFileNameA
0x140008060 _lread
0x140008068 _llseek
0x140008070 _lopen
0x140008078 _lwrite
0x140008080 _lcreat
0x140008088 CreateDirectoryA
0x140008090 SetCurrentDirectoryA
0x140008098 GetDiskFreeSpaceA
0x1400080a0 GetFileAttributesA
0x1400080a8 CompareStringA
0x1400080b0 DeleteFileA
0x1400080b8 GetTempPathA
0x1400080c0 GetCurrentDirectoryA
0x1400080c8 CloseHandle
0x1400080d0 GetExitCodeProcess
0x1400080d8 GetLastError
0x1400080e0 LocalFree
0x1400080e8 GetCurrentProcess
0x1400080f0 MoveFileExA
0x1400080f8 GetStringTypeW
0x140008100 MultiByteToWideChar
0x140008108 LCMapStringW
0x140008110 HeapReAlloc
0x140008118 HeapSize
0x140008120 IsValidCodePage
0x140008128 Sleep
0x140008130 RemoveDirectoryA
0x140008138 FreeLibrary
0x140008140 GetOEMCP
0x140008148 GetACP
0x140008150 GetModuleHandleW
0x140008158 ExitProcess
0x140008160 DecodePointer
0x140008168 HeapFree
0x140008170 HeapAlloc
0x140008178 GetCommandLineA
0x140008180 GetStartupInfoW
0x140008188 InitializeCriticalSectionAndSpinCount
0x140008190 DeleteCriticalSection
0x140008198 LeaveCriticalSection
0x1400081a0 EnterCriticalSection
0x1400081a8 EncodePointer
0x1400081b0 LoadLibraryW
0x1400081b8 UnhandledExceptionFilter
0x1400081c0 SetUnhandledExceptionFilter
0x1400081c8 IsDebuggerPresent
0x1400081d0 RtlVirtualUnwind
0x1400081d8 RtlLookupFunctionEntry
0x1400081e0 RtlCaptureContext
0x1400081e8 TerminateProcess
0x1400081f0 FlsGetValue
0x1400081f8 FlsSetValue
0x140008200 FlsFree
0x140008208 SetLastError
0x140008210 GetCurrentThreadId
0x140008218 FlsAlloc
0x140008220 RtlUnwindEx
0x140008228 WriteFile
0x140008230 GetStdHandle
0x140008238 GetModuleFileNameW
0x140008240 HeapSetInformation
0x140008248 GetVersion
0x140008250 HeapCreate
0x140008258 FreeEnvironmentStringsW
0x140008260 WideCharToMultiByte
0x140008268 GetEnvironmentStringsW
0x140008270 SetHandleCount
0x140008278 GetFileType
0x140008280 QueryPerformanceCounter
0x140008288 GetTickCount
0x140008290 GetCurrentProcessId
0x140008298 GetSystemTimeAsFileTime
0x1400082a0 GetCPInfo
USER32.dll
0x1400082c0 TranslateMessage
0x1400082c8 DispatchMessageA
0x1400082d0 PeekMessageA
0x1400082d8 wsprintfA
0x1400082e0 LoadCursorA
0x1400082e8 SetCursor
0x1400082f0 MessageBoxA
0x1400082f8 MsgWaitForMultipleObjects
ADVAPI32.dll
0x140008000 GetTokenInformation
0x140008008 OpenProcessToken
SHELL32.dll
0x1400082b0 ShellExecuteExA
EAT(Export Address Table) is none