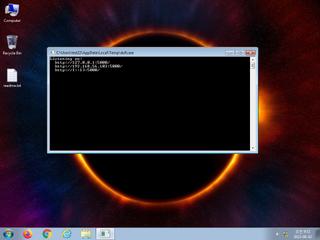
ScreenShot
| Created | 2023.08.02 10:13 | Machine | s1_win7_x6403 |
| Filename | dufs.exe | ||
| Type | PE32 executable (console) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 3 detected (AIDetectMalware, Attribute, HighConfidence, Generic@AI, RDML, g9tlQQ3qcgqApBUE3kO1nw) | ||
| md5 | 20a308e65c20ff7de1f2a1cd047464b5 | ||
| sha256 | ad91669c04a71d1adedd3800fcfb505734e442a891a532e1ad18c54b05acc98d | ||
| ssdeep | 49152:zJWNjg2jZws6aBeNio8njOpQ7EsIU6iHWm2lOZjS:zajgKZwieH8aqW+V | ||
| imphash | 178ccf246b8347cf38428a657085a6d6 | ||
| impfuzzy | 96:NrxrWrfWaPJzXPljtek7jhQH49yIiNg04jmFa:rWrfWY/qkpQHsDW4jmFa | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | File has been identified by 3 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Command line console output was observed |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
kernel32.dll
0x5830c0 InitOnceBeginInitialize
0x5830c4 TlsAlloc
0x5830c8 InitOnceComplete
0x5830cc TlsFree
0x5830d0 WaitForSingleObject
0x5830d4 MultiByteToWideChar
0x5830d8 WriteConsoleW
0x5830dc SetLastError
0x5830e0 GetCurrentDirectoryW
0x5830e4 WaitForSingleObjectEx
0x5830e8 LoadLibraryA
0x5830ec GetCurrentProcess
0x5830f0 CreateMutexA
0x5830f4 ReleaseMutex
0x5830f8 GetEnvironmentVariableW
0x5830fc GetModuleHandleW
0x583100 GetProcAddress
0x583104 GetCommandLineW
0x583108 GetModuleFileNameW
0x58310c CreateFileW
0x583110 GetFullPathNameW
0x583114 GetFinalPathNameByHandleW
0x583118 SetFilePointerEx
0x58311c FindNextFileW
0x583120 CreateDirectoryW
0x583124 GetModuleHandleA
0x583128 FindClose
0x58312c GetFileInformationByHandle
0x583130 GetQueuedCompletionStatusEx
0x583134 GetFileType
0x583138 SetFileCompletionNotificationModes
0x58313c QueryPerformanceCounter
0x583140 QueryPerformanceFrequency
0x583144 GetSystemTimeAsFileTime
0x583148 RtlCaptureContext
0x58314c AcquireSRWLockShared
0x583150 ReleaseSRWLockShared
0x583154 DeleteFileW
0x583158 SetFileInformationByHandle
0x58315c DuplicateHandle
0x583160 SleepConditionVariableSRW
0x583164 WakeAllConditionVariable
0x583168 PostQueuedCompletionStatus
0x58316c WakeConditionVariable
0x583170 AcquireSRWLockExclusive
0x583174 SwitchToThread
0x583178 GetCurrentThreadId
0x58317c SystemTimeToTzSpecificLocalTime
0x583180 SetConsoleCtrlHandler
0x583184 CreateThread
0x583188 GetCurrentProcessId
0x58318c SetHandleInformation
0x583190 GetCurrentThread
0x583194 GetSystemInfo
0x583198 FindFirstFileW
0x58319c SetThreadStackGuarantee
0x5831a0 AddVectoredExceptionHandler
0x5831a4 CreateIoCompletionPort
0x5831a8 InitializeSListHead
0x5831ac IsDebuggerPresent
0x5831b0 UnhandledExceptionFilter
0x5831b4 SetUnhandledExceptionFilter
0x5831b8 IsProcessorFeaturePresent
0x5831bc GetStdHandle
0x5831c0 ReleaseSRWLockExclusive
0x5831c4 SystemTimeToFileTime
0x5831c8 TlsSetValue
0x5831cc TlsGetValue
0x5831d0 SetConsoleTextAttribute
0x5831d4 ExitProcess
0x5831d8 GetConsoleScreenBufferInfo
0x5831dc SetConsoleMode
0x5831e0 GetConsoleMode
0x5831e4 HeapReAlloc
0x5831e8 HeapFree
0x5831ec GetProcessHeap
0x5831f0 HeapAlloc
0x5831f4 MoveFileExW
0x5831f8 CopyFileExW
0x5831fc CloseHandle
0x583200 TryAcquireSRWLockExclusive
0x583204 GetLastError
0x583208 FormatMessageW
0x58320c GetFileInformationByHandleEx
0x583210 TerminateProcess
ws2_32.dll
0x583234 recv
0x583238 getsockname
0x58323c WSACleanup
0x583240 WSAStartup
0x583244 freeaddrinfo
0x583248 WSASend
0x58324c shutdown
0x583250 WSASocketW
0x583254 send
0x583258 WSAIoctl
0x58325c setsockopt
0x583260 accept
0x583264 closesocket
0x583268 WSAGetLastError
0x58326c ioctlsocket
0x583270 listen
0x583274 ind
0x583278 getaddrinfo
iphlpapi.dll
0x5830b8 GetAdaptersAddresses
ntdll.dll
0x583218 RtlNtStatusToDosError
0x58321c NtDeviceIoControlFile
0x583220 NtCancelIoFileEx
0x583224 NtWriteFile
0x583228 NtCreateFile
0x58322c NtReadFile
crypt.dll
0x5830b0 BCryptGenRandom
advapi32.dll
0x583028 SystemFunction036
VCRUNTIME140.dll
0x583000 memmove
0x583004 memcpy
0x583008 _except_handler4_common
0x58300c memcmp
0x583010 memset
0x583014 _CxxThrowException
0x583018 __CxxFrameHandler3
0x58301c __current_exception
0x583020 __current_exception_context
api-ms-win-crt-string-l1-1-0.dll
0x5830a8 strlen
api-ms-win-crt-runtime-l1-1-0.dll
0x58304c exit
0x583050 _exit
0x583054 __p___argc
0x583058 _c_exit
0x58305c _register_thread_local_exe_atexit_callback
0x583060 _initterm
0x583064 _set_app_type
0x583068 _get_initial_narrow_environment
0x58306c _initialize_onexit_table
0x583070 _register_onexit_function
0x583074 _initialize_narrow_environment
0x583078 _configure_narrow_argv
0x58307c _crt_atexit
0x583080 _controlfp_s
0x583084 terminate
0x583088 _initterm_e
0x58308c __p___argv
0x583090 _seh_filter_exe
0x583094 _cexit
api-ms-win-crt-math-l1-1-0.dll
0x583044 __setusermatherr
api-ms-win-crt-stdio-l1-1-0.dll
0x58309c __p__commode
0x5830a0 _set_fmode
api-ms-win-crt-locale-l1-1-0.dll
0x58303c _configthreadlocale
api-ms-win-crt-heap-l1-1-0.dll
0x583030 _set_new_mode
0x583034 free
EAT(Export Address Table) is none
kernel32.dll
0x5830c0 InitOnceBeginInitialize
0x5830c4 TlsAlloc
0x5830c8 InitOnceComplete
0x5830cc TlsFree
0x5830d0 WaitForSingleObject
0x5830d4 MultiByteToWideChar
0x5830d8 WriteConsoleW
0x5830dc SetLastError
0x5830e0 GetCurrentDirectoryW
0x5830e4 WaitForSingleObjectEx
0x5830e8 LoadLibraryA
0x5830ec GetCurrentProcess
0x5830f0 CreateMutexA
0x5830f4 ReleaseMutex
0x5830f8 GetEnvironmentVariableW
0x5830fc GetModuleHandleW
0x583100 GetProcAddress
0x583104 GetCommandLineW
0x583108 GetModuleFileNameW
0x58310c CreateFileW
0x583110 GetFullPathNameW
0x583114 GetFinalPathNameByHandleW
0x583118 SetFilePointerEx
0x58311c FindNextFileW
0x583120 CreateDirectoryW
0x583124 GetModuleHandleA
0x583128 FindClose
0x58312c GetFileInformationByHandle
0x583130 GetQueuedCompletionStatusEx
0x583134 GetFileType
0x583138 SetFileCompletionNotificationModes
0x58313c QueryPerformanceCounter
0x583140 QueryPerformanceFrequency
0x583144 GetSystemTimeAsFileTime
0x583148 RtlCaptureContext
0x58314c AcquireSRWLockShared
0x583150 ReleaseSRWLockShared
0x583154 DeleteFileW
0x583158 SetFileInformationByHandle
0x58315c DuplicateHandle
0x583160 SleepConditionVariableSRW
0x583164 WakeAllConditionVariable
0x583168 PostQueuedCompletionStatus
0x58316c WakeConditionVariable
0x583170 AcquireSRWLockExclusive
0x583174 SwitchToThread
0x583178 GetCurrentThreadId
0x58317c SystemTimeToTzSpecificLocalTime
0x583180 SetConsoleCtrlHandler
0x583184 CreateThread
0x583188 GetCurrentProcessId
0x58318c SetHandleInformation
0x583190 GetCurrentThread
0x583194 GetSystemInfo
0x583198 FindFirstFileW
0x58319c SetThreadStackGuarantee
0x5831a0 AddVectoredExceptionHandler
0x5831a4 CreateIoCompletionPort
0x5831a8 InitializeSListHead
0x5831ac IsDebuggerPresent
0x5831b0 UnhandledExceptionFilter
0x5831b4 SetUnhandledExceptionFilter
0x5831b8 IsProcessorFeaturePresent
0x5831bc GetStdHandle
0x5831c0 ReleaseSRWLockExclusive
0x5831c4 SystemTimeToFileTime
0x5831c8 TlsSetValue
0x5831cc TlsGetValue
0x5831d0 SetConsoleTextAttribute
0x5831d4 ExitProcess
0x5831d8 GetConsoleScreenBufferInfo
0x5831dc SetConsoleMode
0x5831e0 GetConsoleMode
0x5831e4 HeapReAlloc
0x5831e8 HeapFree
0x5831ec GetProcessHeap
0x5831f0 HeapAlloc
0x5831f4 MoveFileExW
0x5831f8 CopyFileExW
0x5831fc CloseHandle
0x583200 TryAcquireSRWLockExclusive
0x583204 GetLastError
0x583208 FormatMessageW
0x58320c GetFileInformationByHandleEx
0x583210 TerminateProcess
ws2_32.dll
0x583234 recv
0x583238 getsockname
0x58323c WSACleanup
0x583240 WSAStartup
0x583244 freeaddrinfo
0x583248 WSASend
0x58324c shutdown
0x583250 WSASocketW
0x583254 send
0x583258 WSAIoctl
0x58325c setsockopt
0x583260 accept
0x583264 closesocket
0x583268 WSAGetLastError
0x58326c ioctlsocket
0x583270 listen
0x583274 ind
0x583278 getaddrinfo
iphlpapi.dll
0x5830b8 GetAdaptersAddresses
ntdll.dll
0x583218 RtlNtStatusToDosError
0x58321c NtDeviceIoControlFile
0x583220 NtCancelIoFileEx
0x583224 NtWriteFile
0x583228 NtCreateFile
0x58322c NtReadFile
crypt.dll
0x5830b0 BCryptGenRandom
advapi32.dll
0x583028 SystemFunction036
VCRUNTIME140.dll
0x583000 memmove
0x583004 memcpy
0x583008 _except_handler4_common
0x58300c memcmp
0x583010 memset
0x583014 _CxxThrowException
0x583018 __CxxFrameHandler3
0x58301c __current_exception
0x583020 __current_exception_context
api-ms-win-crt-string-l1-1-0.dll
0x5830a8 strlen
api-ms-win-crt-runtime-l1-1-0.dll
0x58304c exit
0x583050 _exit
0x583054 __p___argc
0x583058 _c_exit
0x58305c _register_thread_local_exe_atexit_callback
0x583060 _initterm
0x583064 _set_app_type
0x583068 _get_initial_narrow_environment
0x58306c _initialize_onexit_table
0x583070 _register_onexit_function
0x583074 _initialize_narrow_environment
0x583078 _configure_narrow_argv
0x58307c _crt_atexit
0x583080 _controlfp_s
0x583084 terminate
0x583088 _initterm_e
0x58308c __p___argv
0x583090 _seh_filter_exe
0x583094 _cexit
api-ms-win-crt-math-l1-1-0.dll
0x583044 __setusermatherr
api-ms-win-crt-stdio-l1-1-0.dll
0x58309c __p__commode
0x5830a0 _set_fmode
api-ms-win-crt-locale-l1-1-0.dll
0x58303c _configthreadlocale
api-ms-win-crt-heap-l1-1-0.dll
0x583030 _set_new_mode
0x583034 free
EAT(Export Address Table) is none