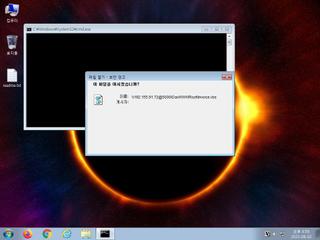
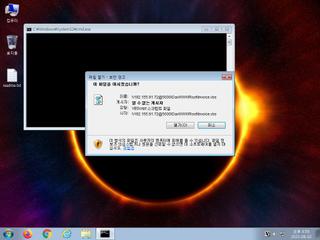
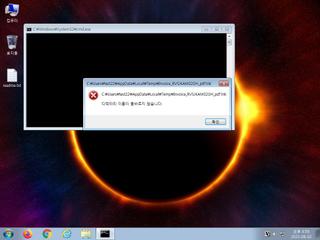
ScreenShot
| Created | 2023.08.02 17:00 | Machine | s1_win7_x6402 |
| Filename | Invoice_RVSJKAM02GH_pdf.lnk | ||
| Type | MS Windows shortcut, Points to a file or directory, Has Working directory, Icon number=0, Archive, c | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 4 detected (GenericKD, ai score=80) | ||
| md5 | ca4756de93f1356c73c37d5ce1e64405 | ||
| sha256 | 84d32881ef43a7662841c032d263478fb93c5bac82a126a0d06daf685ad7fa3c | ||
| ssdeep | 24:8DqaYbE+uLiOd8nzE58ypDCj+7ShcE+WzhjCRaEduuYjSGJntVBQeTjFxMcriWq5:8D5YY5iBze7yYShjCKjSGj3TjIbWqjO | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (7cnts)
| Level | Description |
|---|---|
| watch | Communicates with host for which no DNS query was performed |
| watch | Harvests credentials from local email clients |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Creates a shortcut to an executable file |
| notice | File has been identified by 4 AntiVirus engines on VirusTotal as malicious |
| info | Command line console output was observed |
Rules (1cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | Lnk_Format_Zero | LNK Format | binaries (upload) |
Suricata ids
ET INFO Dotted Quad Host VBS Request
ET MALWARE Possible Malicious Invoice EXE
ET MALWARE Possible Malicious Invoice EXE