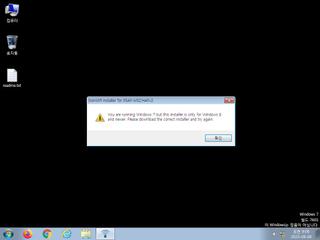
ScreenShot
| Created | 2023.08.09 09:12 | Machine | s1_win7_x6401 |
| Filename | Revolution_Makerspace_Certificate_Installer.exe | ||
| Type | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, Nullsoft Installer sel | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 7 detected (AIDetectMalware, Malicious, moderate, score, GrayWare, ZenVPN, Autoit, confidence, 100%) | ||
| md5 | faeb62b6240705a8af7152198449e64a | ||
| sha256 | 039f3a8d173f835d3e71cfc8433ead08f9975f8b6d9afd7d28bb76d54f7f38bf | ||
| ssdeep | 12288:4cp8NYTcQBQnHW52sOMbrG90Jjj5b47Jk62:4g8qQQBQHxshnT | ||
| imphash | 28a099a911237a28521d8b7ea250f089 | ||
| impfuzzy | 48:vWj6E8uNOTtgaJ2pj4kOBXEG9del1xEl/1/6U0Tha8ESvS55w4yo4RVOtrF8tLQj:vEhetgy2pjl6/7ODo | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates executable files on the filesystem |
| notice | Drops an executable to the user AppData folder |
| notice | File has been identified by 7 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | One or more processes crashed |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (9cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | bmp_file_format | bmp file format | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
ADVAPI32.dll
0x7ab340 RegCloseKey
0x7ab344 RegCreateKeyExA
0x7ab348 RegDeleteKeyA
0x7ab34c RegDeleteValueA
0x7ab350 RegEnumKeyA
0x7ab354 RegEnumValueA
0x7ab358 RegOpenKeyExA
0x7ab35c RegQueryValueExA
0x7ab360 RegSetValueExA
COMCTL32.DLL
0x7ab368 ImageList_AddMasked
0x7ab36c ImageList_Create
0x7ab370 ImageList_Destroy
0x7ab374 InitCommonControls
GDI32.dll
0x7ab37c CreateBrushIndirect
0x7ab380 CreateFontIndirectA
0x7ab384 DeleteObject
0x7ab388 GetDeviceCaps
0x7ab38c SelectObject
0x7ab390 SetBkColor
0x7ab394 SetBkMode
0x7ab398 SetTextColor
KERNEL32.dll
0x7ab3a0 CloseHandle
0x7ab3a4 CompareFileTime
0x7ab3a8 CopyFileA
0x7ab3ac CreateDirectoryA
0x7ab3b0 CreateFileA
0x7ab3b4 CreateProcessA
0x7ab3b8 CreateThread
0x7ab3bc DeleteFileA
0x7ab3c0 ExitProcess
0x7ab3c4 ExpandEnvironmentStringsA
0x7ab3c8 FindClose
0x7ab3cc FindFirstFileA
0x7ab3d0 FindNextFileA
0x7ab3d4 FreeLibrary
0x7ab3d8 GetCommandLineA
0x7ab3dc GetCurrentProcess
0x7ab3e0 GetDiskFreeSpaceA
0x7ab3e4 GetExitCodeProcess
0x7ab3e8 GetFileAttributesA
0x7ab3ec GetFileSize
0x7ab3f0 GetFullPathNameA
0x7ab3f4 GetLastError
0x7ab3f8 GetModuleFileNameA
0x7ab3fc GetModuleHandleA
0x7ab400 GetPrivateProfileStringA
0x7ab404 GetProcAddress
0x7ab408 GetShortPathNameA
0x7ab40c GetSystemDirectoryA
0x7ab410 GetTempFileNameA
0x7ab414 GetTempPathA
0x7ab418 GetTickCount
0x7ab41c GetVersion
0x7ab420 GetWindowsDirectoryA
0x7ab424 GlobalAlloc
0x7ab428 GlobalFree
0x7ab42c GlobalLock
0x7ab430 GlobalUnlock
0x7ab434 LoadLibraryA
0x7ab438 LoadLibraryExA
0x7ab43c MoveFileA
0x7ab440 MulDiv
0x7ab444 MultiByteToWideChar
0x7ab448 ReadFile
0x7ab44c RemoveDirectoryA
0x7ab450 SearchPathA
0x7ab454 SetCurrentDirectoryA
0x7ab458 SetErrorMode
0x7ab45c SetFileAttributesA
0x7ab460 SetFilePointer
0x7ab464 SetFileTime
0x7ab468 Sleep
0x7ab46c WaitForSingleObject
0x7ab470 WriteFile
0x7ab474 WritePrivateProfileStringA
0x7ab478 lstrcatA
0x7ab47c lstrcmpA
0x7ab480 lstrcmpiA
0x7ab484 lstrcpynA
0x7ab488 lstrlenA
ole32.dll
0x7ab490 CoCreateInstance
0x7ab494 CoTaskMemFree
0x7ab498 OleInitialize
0x7ab49c OleUninitialize
SHELL32.DLL
0x7ab4a4 SHBrowseForFolderA
0x7ab4a8 SHFileOperationA
0x7ab4ac SHGetFileInfoA
0x7ab4b0 SHGetPathFromIDListA
0x7ab4b4 SHGetSpecialFolderLocation
0x7ab4b8 ShellExecuteA
USER32.dll
0x7ab4c0 AppendMenuA
0x7ab4c4 BeginPaint
0x7ab4c8 CallWindowProcA
0x7ab4cc CharNextA
0x7ab4d0 CharPrevA
0x7ab4d4 CheckDlgButton
0x7ab4d8 CloseClipboard
0x7ab4dc CreateDialogParamA
0x7ab4e0 CreatePopupMenu
0x7ab4e4 CreateWindowExA
0x7ab4e8 DefWindowProcA
0x7ab4ec DestroyWindow
0x7ab4f0 DialogBoxParamA
0x7ab4f4 DispatchMessageA
0x7ab4f8 DrawTextA
0x7ab4fc EmptyClipboard
0x7ab500 EnableMenuItem
0x7ab504 EnableWindow
0x7ab508 EndDialog
0x7ab50c EndPaint
0x7ab510 ExitWindowsEx
0x7ab514 FillRect
0x7ab518 FindWindowExA
0x7ab51c GetClassInfoA
0x7ab520 GetClientRect
0x7ab524 GetDC
0x7ab528 GetDlgItem
0x7ab52c GetDlgItemTextA
0x7ab530 GetMessagePos
0x7ab534 GetSysColor
0x7ab538 GetSystemMenu
0x7ab53c GetSystemMetrics
0x7ab540 GetWindowLongA
0x7ab544 GetWindowRect
0x7ab548 InvalidateRect
0x7ab54c IsWindow
0x7ab550 IsWindowEnabled
0x7ab554 IsWindowVisible
0x7ab558 LoadBitmapA
0x7ab55c LoadCursorA
0x7ab560 LoadImageA
0x7ab564 MessageBoxIndirectA
0x7ab568 OpenClipboard
0x7ab56c PeekMessageA
0x7ab570 PostQuitMessage
0x7ab574 RegisterClassA
0x7ab578 ScreenToClient
0x7ab57c SendMessageA
0x7ab580 SendMessageTimeoutA
0x7ab584 SetClassLongA
0x7ab588 SetClipboardData
0x7ab58c SetCursor
0x7ab590 SetDlgItemTextA
0x7ab594 SetForegroundWindow
0x7ab598 SetTimer
0x7ab59c SetWindowLongA
0x7ab5a0 SetWindowPos
0x7ab5a4 SetWindowTextA
0x7ab5a8 ShowWindow
0x7ab5ac SystemParametersInfoA
0x7ab5b0 TrackPopupMenu
0x7ab5b4 wsprintfA
VERSION.dll
0x7ab5bc GetFileVersionInfoA
0x7ab5c0 GetFileVersionInfoSizeA
0x7ab5c4 VerQueryValueA
EAT(Export Address Table) is none
ADVAPI32.dll
0x7ab340 RegCloseKey
0x7ab344 RegCreateKeyExA
0x7ab348 RegDeleteKeyA
0x7ab34c RegDeleteValueA
0x7ab350 RegEnumKeyA
0x7ab354 RegEnumValueA
0x7ab358 RegOpenKeyExA
0x7ab35c RegQueryValueExA
0x7ab360 RegSetValueExA
COMCTL32.DLL
0x7ab368 ImageList_AddMasked
0x7ab36c ImageList_Create
0x7ab370 ImageList_Destroy
0x7ab374 InitCommonControls
GDI32.dll
0x7ab37c CreateBrushIndirect
0x7ab380 CreateFontIndirectA
0x7ab384 DeleteObject
0x7ab388 GetDeviceCaps
0x7ab38c SelectObject
0x7ab390 SetBkColor
0x7ab394 SetBkMode
0x7ab398 SetTextColor
KERNEL32.dll
0x7ab3a0 CloseHandle
0x7ab3a4 CompareFileTime
0x7ab3a8 CopyFileA
0x7ab3ac CreateDirectoryA
0x7ab3b0 CreateFileA
0x7ab3b4 CreateProcessA
0x7ab3b8 CreateThread
0x7ab3bc DeleteFileA
0x7ab3c0 ExitProcess
0x7ab3c4 ExpandEnvironmentStringsA
0x7ab3c8 FindClose
0x7ab3cc FindFirstFileA
0x7ab3d0 FindNextFileA
0x7ab3d4 FreeLibrary
0x7ab3d8 GetCommandLineA
0x7ab3dc GetCurrentProcess
0x7ab3e0 GetDiskFreeSpaceA
0x7ab3e4 GetExitCodeProcess
0x7ab3e8 GetFileAttributesA
0x7ab3ec GetFileSize
0x7ab3f0 GetFullPathNameA
0x7ab3f4 GetLastError
0x7ab3f8 GetModuleFileNameA
0x7ab3fc GetModuleHandleA
0x7ab400 GetPrivateProfileStringA
0x7ab404 GetProcAddress
0x7ab408 GetShortPathNameA
0x7ab40c GetSystemDirectoryA
0x7ab410 GetTempFileNameA
0x7ab414 GetTempPathA
0x7ab418 GetTickCount
0x7ab41c GetVersion
0x7ab420 GetWindowsDirectoryA
0x7ab424 GlobalAlloc
0x7ab428 GlobalFree
0x7ab42c GlobalLock
0x7ab430 GlobalUnlock
0x7ab434 LoadLibraryA
0x7ab438 LoadLibraryExA
0x7ab43c MoveFileA
0x7ab440 MulDiv
0x7ab444 MultiByteToWideChar
0x7ab448 ReadFile
0x7ab44c RemoveDirectoryA
0x7ab450 SearchPathA
0x7ab454 SetCurrentDirectoryA
0x7ab458 SetErrorMode
0x7ab45c SetFileAttributesA
0x7ab460 SetFilePointer
0x7ab464 SetFileTime
0x7ab468 Sleep
0x7ab46c WaitForSingleObject
0x7ab470 WriteFile
0x7ab474 WritePrivateProfileStringA
0x7ab478 lstrcatA
0x7ab47c lstrcmpA
0x7ab480 lstrcmpiA
0x7ab484 lstrcpynA
0x7ab488 lstrlenA
ole32.dll
0x7ab490 CoCreateInstance
0x7ab494 CoTaskMemFree
0x7ab498 OleInitialize
0x7ab49c OleUninitialize
SHELL32.DLL
0x7ab4a4 SHBrowseForFolderA
0x7ab4a8 SHFileOperationA
0x7ab4ac SHGetFileInfoA
0x7ab4b0 SHGetPathFromIDListA
0x7ab4b4 SHGetSpecialFolderLocation
0x7ab4b8 ShellExecuteA
USER32.dll
0x7ab4c0 AppendMenuA
0x7ab4c4 BeginPaint
0x7ab4c8 CallWindowProcA
0x7ab4cc CharNextA
0x7ab4d0 CharPrevA
0x7ab4d4 CheckDlgButton
0x7ab4d8 CloseClipboard
0x7ab4dc CreateDialogParamA
0x7ab4e0 CreatePopupMenu
0x7ab4e4 CreateWindowExA
0x7ab4e8 DefWindowProcA
0x7ab4ec DestroyWindow
0x7ab4f0 DialogBoxParamA
0x7ab4f4 DispatchMessageA
0x7ab4f8 DrawTextA
0x7ab4fc EmptyClipboard
0x7ab500 EnableMenuItem
0x7ab504 EnableWindow
0x7ab508 EndDialog
0x7ab50c EndPaint
0x7ab510 ExitWindowsEx
0x7ab514 FillRect
0x7ab518 FindWindowExA
0x7ab51c GetClassInfoA
0x7ab520 GetClientRect
0x7ab524 GetDC
0x7ab528 GetDlgItem
0x7ab52c GetDlgItemTextA
0x7ab530 GetMessagePos
0x7ab534 GetSysColor
0x7ab538 GetSystemMenu
0x7ab53c GetSystemMetrics
0x7ab540 GetWindowLongA
0x7ab544 GetWindowRect
0x7ab548 InvalidateRect
0x7ab54c IsWindow
0x7ab550 IsWindowEnabled
0x7ab554 IsWindowVisible
0x7ab558 LoadBitmapA
0x7ab55c LoadCursorA
0x7ab560 LoadImageA
0x7ab564 MessageBoxIndirectA
0x7ab568 OpenClipboard
0x7ab56c PeekMessageA
0x7ab570 PostQuitMessage
0x7ab574 RegisterClassA
0x7ab578 ScreenToClient
0x7ab57c SendMessageA
0x7ab580 SendMessageTimeoutA
0x7ab584 SetClassLongA
0x7ab588 SetClipboardData
0x7ab58c SetCursor
0x7ab590 SetDlgItemTextA
0x7ab594 SetForegroundWindow
0x7ab598 SetTimer
0x7ab59c SetWindowLongA
0x7ab5a0 SetWindowPos
0x7ab5a4 SetWindowTextA
0x7ab5a8 ShowWindow
0x7ab5ac SystemParametersInfoA
0x7ab5b0 TrackPopupMenu
0x7ab5b4 wsprintfA
VERSION.dll
0x7ab5bc GetFileVersionInfoA
0x7ab5c0 GetFileVersionInfoSizeA
0x7ab5c4 VerQueryValueA
EAT(Export Address Table) is none