ScreenShot
| Created | 2023.08.10 09:48 | Machine | s1_win7_x6402 |
| Filename | NvjRTZU.wsf | ||
| Type | UTF-8 Unicode text, with very long lines, with CRLF line terminators | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | |||
| md5 | 4d0dc8bd843fdd35e8623e22e3ea8f83 | ||
| sha256 | d889ef659187fd9471e03133ad86e12bbfc5ef8af33a809b87ef9fb4fda1992d | ||
| ssdeep | 768:EP8sxP8sDoP8sxP8sDoP8sxP8sxP8sxP8sxP8sxP8sxP8sDoP8sDoP8sxP8sxP8R:r | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
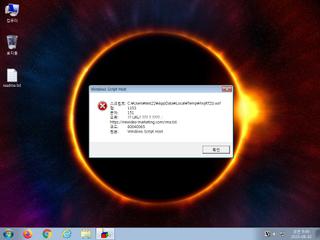
| watch | Network communications indicative of a potential document or script payload download was initiated by the process wscript.exe |
| watch | Wscript.exe initiated network communications indicative of a script based payload download |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | One or more processes crashed |
Rules (0cnts)
| Level | Name | Description | Collection |
|---|