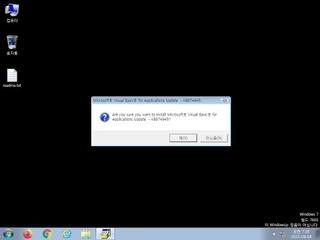
ScreenShot
| Created | 2023.09.04 07:41 | Machine | s1_win7_x6401 |
| Filename | VBA65-KB974945-x86-EN.exe | ||
| Type | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 42 detected (AIDetectMalware, malicious, high confidence, FakeAlert, unsafe, Save, Lazy, Eldorado, Attribute, HighConfidence, score, Crysan, Agen, Tgil, Expiro, high, Static AI, Suspicious PE, XWormRAT, 10AFFS0, Detected, Ekocit, ZexaF, @t0@aCgJF3ci, ai score=85, BScope, Nitol, DcRat, BNER4NzZWDL, Tnega, Tiny, confidence, 100%) | ||
| md5 | b88cc7ba6a01daf0de338ee2c656864e | ||
| sha256 | 67de54a5271a2354b492bbaf5bbead07cc1e24fd5efa94bdac2fc30f0475db1a | ||
| ssdeep | 98304:K+erVUYkek1Bqs4uzLw1Hf6QQd1LzMQmLNHDUHqvqJhRdOyY:urVsewBvHw1HyPd1LzMQ2DWqq+ | ||
| imphash | 6f462fcc6b830b77fb3fef2add9dc570 | ||
| impfuzzy | 6:HMJqz80umyRwXJxSBS0H5sD4sIWDLb4iPEcn:sJqwRSY58PLPXn | ||
Network IP location
Signature (20cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 42 AntiVirus engines on VirusTotal as malicious |
| watch | A process performed obfuscation on information about the computer or sent it to a remote location indicative of CnC Traffic/Preperations. |
| watch | The process powershell.exe wrote an executable file to disk |
| notice | A process created a hidden window |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a shortcut to an executable file |
| notice | Creates a suspicious process |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Collects information to fingerprint the system (MachineGuid |
| info | Command line console output was observed |
| info | One or more processes crashed |
| info | Queries for the computername |
| info | Uses Windows APIs to generate a cryptographic key |
Rules (14cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Emotet_RL_Gen_Zero | Win32 Trojan Emotet | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (download) |
| watch | Antivirus | Contains references to security software | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| info | CAB_file_format | CAB archive file | binaries (download) |
| info | Is_DotNET_EXE | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
msvcrt.dll
0x9d6330 malloc
0x9d6334 _sleep
0x9d6338 memset
0x9d633c strcmp
0x9d6340 strcpy
0x9d6344 getenv
0x9d6348 sprintf
0x9d634c fopen
0x9d6350 fwrite
0x9d6354 fclose
0x9d6358 __argc
0x9d635c __argv
0x9d6360 _environ
0x9d6364 _XcptFilter
0x9d6368 __set_app_type
0x9d636c _controlfp
0x9d6370 __getmainargs
0x9d6374 exit
shell32.dll
0x9d637c ShellExecuteA
kernel32.dll
0x9d6384 SetUnhandledExceptionFilter
EAT(Export Address Table) is none
msvcrt.dll
0x9d6330 malloc
0x9d6334 _sleep
0x9d6338 memset
0x9d633c strcmp
0x9d6340 strcpy
0x9d6344 getenv
0x9d6348 sprintf
0x9d634c fopen
0x9d6350 fwrite
0x9d6354 fclose
0x9d6358 __argc
0x9d635c __argv
0x9d6360 _environ
0x9d6364 _XcptFilter
0x9d6368 __set_app_type
0x9d636c _controlfp
0x9d6370 __getmainargs
0x9d6374 exit
shell32.dll
0x9d637c ShellExecuteA
kernel32.dll
0x9d6384 SetUnhandledExceptionFilter
EAT(Export Address Table) is none