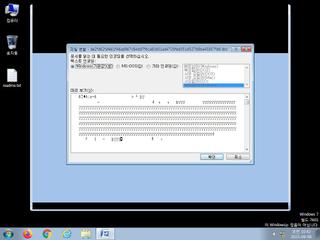
ScreenShot
| Created | 2023.09.08 10:44 | Machine | s1_win7_x6401 |
| Filename | de2fd62fafe61f46ad967c84dd7fbca80d31ad4729fed051d527d9ba45857fd6.doc | ||
| Type | Composite Document File V2 Document, Cannot read section info | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 34 detected (SAgent, malicious, high confidence, score, Valyria, Save, Eldorado, CodeLoader, CLASSIC, udrmb, OLE2, ai score=100, Kimsuky, S1649, Static AI, Malicious OLE) | ||
| md5 | f282875b9958bd3706f9063bf8c5bf14 | ||
| sha256 | de2fd62fafe61f46ad967c84dd7fbca80d31ad4729fed051d527d9ba45857fd6 | ||
| ssdeep | 384:pZSSBM46QLwAc0Le5fGbMUN0j1ZH4Tpth34WvJo7/F46y:Nfj9e5fGb7KZHNWvJob+ | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 34 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates (office) documents on the filesystem |
| notice | Creates hidden or system file |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Contains_VBA_macro_code | Detect a MS Office document with embedded VBA macro code [binaries] | binaries (upload) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| info | Microsoft_Office_File_Zero | Microsoft Office File | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|