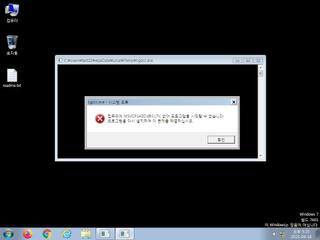
ScreenShot
| Created | 2023.09.18 17:23 | Machine | s1_win7_x6401 |
| Filename | cgpcc.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 5 detected (AIDetectMalware, Malicious, score, susgen) | ||
| md5 | 3f1eb317915ef394385d03d3b32a3967 | ||
| sha256 | 8eae8d282bb235667634a6c8ada53d8b48dd35f752cf61732071e94e109fc083 | ||
| ssdeep | 1536:yb6BsDOW3Q5AQ50fg3570FALBRbMVFweoAag:w6ODT3eAFfg35XLBRbMVFwSag | ||
| imphash | e6071fde7c8f939e596987a857a78bc8 | ||
| impfuzzy | 96:vKs5OUcOE1kH0XEJ5CZNKV8pDi+tMScT3:OoIo8pDkj | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| notice | File has been identified by 5 AntiVirus engines on VirusTotal as malicious |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | The executable uses a known packer |
| info | This executable has a PDB path |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
MSVCP140D.dll
0x140029150 ?flush@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@XZ
0x140029158 ?_Osfx@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAXXZ
0x140029160 ?fill@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBADXZ
0x140029168 ?rdbuf@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBAPEAV?$basic_streambuf@DU?$char_traits@D@std@@@2@XZ
0x140029170 ?tie@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBAPEAV?$basic_ostream@DU?$char_traits@D@std@@@2@XZ
0x140029178 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x140029180 ?sputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAA_JPEBD_J@Z
0x140029188 ?sputc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHD@Z
0x140029190 ?width@ios_base@std@@QEAA_J_J@Z
0x140029198 ?width@ios_base@std@@QEBA_JXZ
0x1400291a0 ?flags@ios_base@std@@QEBAHXZ
0x1400291a8 ?good@ios_base@std@@QEBA_NXZ
0x1400291b0 ?uncaught_exception@std@@YA_NXZ
0x1400291b8 ?_Xout_of_range@std@@YAXPEBD@Z
0x1400291c0 ?_Xlength_error@std@@YAXPEBD@Z
0x1400291c8 ??1_Lockit@std@@QEAA@XZ
0x1400291d0 ?cout@std@@3V?$basic_ostream@DU?$char_traits@D@std@@@1@A
0x1400291d8 ??0_Lockit@std@@QEAA@H@Z
VCRUNTIME140D.dll
0x140029250 memcpy
0x140029258 memmove
0x140029260 __std_exception_copy
0x140029268 __std_exception_destroy
0x140029270 _CxxThrowException
0x140029278 __C_specific_handler
0x140029280 __C_specific_handler_noexcept
0x140029288 __std_type_info_destroy_list
0x140029290 __current_exception
0x140029298 __current_exception_context
0x1400292a0 __vcrt_GetModuleFileNameW
0x1400292a8 __vcrt_GetModuleHandleW
0x1400292b0 __vcrt_LoadLibraryExW
0x1400292b8 memchr
0x1400292c0 memcmp
VCRUNTIME140_1D.dll
0x140029338 __CxxFrameHandler4
ucrtbased.dll
0x140029398 _set_new_mode
0x1400293a0 __p__commode
0x1400293a8 _free_dbg
0x1400293b0 strcpy_s
0x1400293b8 strcat_s
0x1400293c0 __stdio_common_vsprintf_s
0x1400293c8 _seh_filter_dll
0x1400293d0 _initialize_onexit_table
0x1400293d8 _register_onexit_function
0x1400293e0 _execute_onexit_table
0x1400293e8 _crt_atexit
0x1400293f0 _register_thread_local_exe_atexit_callback
0x1400293f8 terminate
0x140029400 _wmakepath_s
0x140029408 _wsplitpath_s
0x140029410 wcscpy_s
0x140029418 __p___argv
0x140029420 strlen
0x140029428 _popen
0x140029430 _pclose
0x140029438 fgets
0x140029440 feof
0x140029448 _CrtDbgReport
0x140029450 _invalid_parameter
0x140029458 _configthreadlocale
0x140029460 _cexit
0x140029468 __p___argc
0x140029470 _set_fmode
0x140029478 _exit
0x140029480 exit
0x140029488 _callnewh
0x140029490 _initterm
0x140029498 _get_initial_narrow_environment
0x1400294a0 _initialize_narrow_environment
0x1400294a8 _c_exit
0x1400294b0 _configure_narrow_argv
0x1400294b8 __setusermatherr
0x1400294c0 _set_app_type
0x1400294c8 _seh_filter_exe
0x1400294d0 _CrtDbgReportW
0x1400294d8 _crt_at_quick_exit
0x1400294e0 malloc
0x1400294e8 _initterm_e
KERNEL32.dll
0x140029000 HeapFree
0x140029008 IsDebuggerPresent
0x140029010 RaiseException
0x140029018 MultiByteToWideChar
0x140029020 WideCharToMultiByte
0x140029028 RtlCaptureContext
0x140029030 RtlLookupFunctionEntry
0x140029038 RtlVirtualUnwind
0x140029040 UnhandledExceptionFilter
0x140029048 SetUnhandledExceptionFilter
0x140029050 GetCurrentProcess
0x140029058 TerminateProcess
0x140029060 IsProcessorFeaturePresent
0x140029068 QueryPerformanceCounter
0x140029070 GetCurrentProcessId
0x140029078 GetSystemTimeAsFileTime
0x140029080 InitializeSListHead
0x140029088 GetStartupInfoW
0x140029090 GetProcAddress
0x140029098 FreeLibrary
0x1400290a0 VirtualQuery
0x1400290a8 GetProcessHeap
0x1400290b0 GetCurrentThreadId
0x1400290b8 HeapAlloc
0x1400290c0 GetLastError
0x1400290c8 GetModuleHandleW
EAT(Export Address Table) is none
MSVCP140D.dll
0x140029150 ?flush@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@XZ
0x140029158 ?_Osfx@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAXXZ
0x140029160 ?fill@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBADXZ
0x140029168 ?rdbuf@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBAPEAV?$basic_streambuf@DU?$char_traits@D@std@@@2@XZ
0x140029170 ?tie@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBAPEAV?$basic_ostream@DU?$char_traits@D@std@@@2@XZ
0x140029178 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x140029180 ?sputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAA_JPEBD_J@Z
0x140029188 ?sputc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHD@Z
0x140029190 ?width@ios_base@std@@QEAA_J_J@Z
0x140029198 ?width@ios_base@std@@QEBA_JXZ
0x1400291a0 ?flags@ios_base@std@@QEBAHXZ
0x1400291a8 ?good@ios_base@std@@QEBA_NXZ
0x1400291b0 ?uncaught_exception@std@@YA_NXZ
0x1400291b8 ?_Xout_of_range@std@@YAXPEBD@Z
0x1400291c0 ?_Xlength_error@std@@YAXPEBD@Z
0x1400291c8 ??1_Lockit@std@@QEAA@XZ
0x1400291d0 ?cout@std@@3V?$basic_ostream@DU?$char_traits@D@std@@@1@A
0x1400291d8 ??0_Lockit@std@@QEAA@H@Z
VCRUNTIME140D.dll
0x140029250 memcpy
0x140029258 memmove
0x140029260 __std_exception_copy
0x140029268 __std_exception_destroy
0x140029270 _CxxThrowException
0x140029278 __C_specific_handler
0x140029280 __C_specific_handler_noexcept
0x140029288 __std_type_info_destroy_list
0x140029290 __current_exception
0x140029298 __current_exception_context
0x1400292a0 __vcrt_GetModuleFileNameW
0x1400292a8 __vcrt_GetModuleHandleW
0x1400292b0 __vcrt_LoadLibraryExW
0x1400292b8 memchr
0x1400292c0 memcmp
VCRUNTIME140_1D.dll
0x140029338 __CxxFrameHandler4
ucrtbased.dll
0x140029398 _set_new_mode
0x1400293a0 __p__commode
0x1400293a8 _free_dbg
0x1400293b0 strcpy_s
0x1400293b8 strcat_s
0x1400293c0 __stdio_common_vsprintf_s
0x1400293c8 _seh_filter_dll
0x1400293d0 _initialize_onexit_table
0x1400293d8 _register_onexit_function
0x1400293e0 _execute_onexit_table
0x1400293e8 _crt_atexit
0x1400293f0 _register_thread_local_exe_atexit_callback
0x1400293f8 terminate
0x140029400 _wmakepath_s
0x140029408 _wsplitpath_s
0x140029410 wcscpy_s
0x140029418 __p___argv
0x140029420 strlen
0x140029428 _popen
0x140029430 _pclose
0x140029438 fgets
0x140029440 feof
0x140029448 _CrtDbgReport
0x140029450 _invalid_parameter
0x140029458 _configthreadlocale
0x140029460 _cexit
0x140029468 __p___argc
0x140029470 _set_fmode
0x140029478 _exit
0x140029480 exit
0x140029488 _callnewh
0x140029490 _initterm
0x140029498 _get_initial_narrow_environment
0x1400294a0 _initialize_narrow_environment
0x1400294a8 _c_exit
0x1400294b0 _configure_narrow_argv
0x1400294b8 __setusermatherr
0x1400294c0 _set_app_type
0x1400294c8 _seh_filter_exe
0x1400294d0 _CrtDbgReportW
0x1400294d8 _crt_at_quick_exit
0x1400294e0 malloc
0x1400294e8 _initterm_e
KERNEL32.dll
0x140029000 HeapFree
0x140029008 IsDebuggerPresent
0x140029010 RaiseException
0x140029018 MultiByteToWideChar
0x140029020 WideCharToMultiByte
0x140029028 RtlCaptureContext
0x140029030 RtlLookupFunctionEntry
0x140029038 RtlVirtualUnwind
0x140029040 UnhandledExceptionFilter
0x140029048 SetUnhandledExceptionFilter
0x140029050 GetCurrentProcess
0x140029058 TerminateProcess
0x140029060 IsProcessorFeaturePresent
0x140029068 QueryPerformanceCounter
0x140029070 GetCurrentProcessId
0x140029078 GetSystemTimeAsFileTime
0x140029080 InitializeSListHead
0x140029088 GetStartupInfoW
0x140029090 GetProcAddress
0x140029098 FreeLibrary
0x1400290a0 VirtualQuery
0x1400290a8 GetProcessHeap
0x1400290b0 GetCurrentThreadId
0x1400290b8 HeapAlloc
0x1400290c0 GetLastError
0x1400290c8 GetModuleHandleW
EAT(Export Address Table) is none