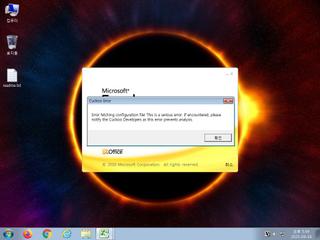
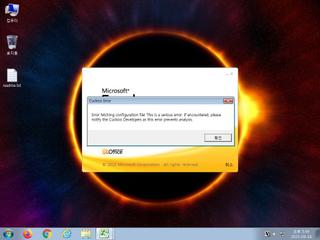
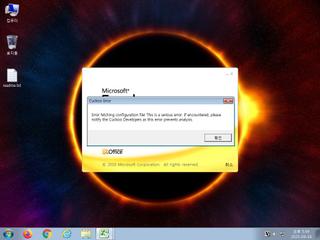
ScreenShot
| Created | 2023.09.19 17:51 | Machine | s1_win7_x6402 |
| Filename | qqdownloadftnv5.xls | ||
| Type | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 936, Name of Creating Application: Microsoft Excel, Create Time/Date: Fri Jun 5 18:17:20 2015, Last Saved Time/Date: Mon Sep 18 07:49:44 2023, Security: 0 | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 48 detected (Kagatang, Laroux, malicious, high confidence, Save, Escoper, ExcelSic, fkbqor, MRACS, MulDrop23, KANGATANG, CPACS, OLE2, Detected, Malware@#3lul0pkw0nefx, score, ai score=81, CLASSIC, Static AI, Malicious OLE, Valyria) | ||
| md5 | a0939fe019485426ee55b070d62b7352 | ||
| sha256 | 054d32f119d8fa26a040842ebf7e523a4f7203037cb42238490bbdbaf69dbb4d | ||
| ssdeep | 768:WvT2CQ6T5Lxk3hOdsylKlgryzc4bNhZFGzE+ch4LgldAlQ5rd142DuG8yC:iPxk3hOdsylKlgryzc4bNhZFGzE+ch4R | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 48 AntiVirus engines on VirusTotal as malicious |
| watch | One or more non-whitelisted processes were created |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Yara rule detected in process memory |
Rules (15cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Contains_VBA_macro_code | Detect a MS Office document with embedded VBA macro code [binaries] | binaries (upload) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| notice | Generic_PWS_Memory_Zero | PWS Memory | memory |
| notice | KeyLogger | Run a KeyLogger | memory |
| notice | ScreenShot | Take ScreenShot | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | Microsoft_Office_File_Zero | Microsoft Office File | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
| info | win_hook | Affect hook table | memory |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|