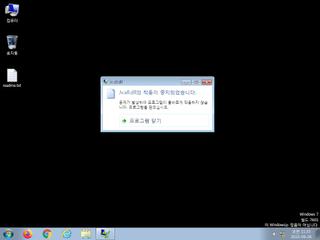
ScreenShot
| Created | 2023.09.26 11:35 | Machine | s1_win7_x6401 |
| Filename | Jv.xll | ||
| Type | PE32+ executable (DLL) (GUI) x86-64 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | |||
| md5 | f7a95d9853bbf73d695908480fa3ace2 | ||
| sha256 | 6fe992f467d89d8886137b7841f5fe8e32c484f3882afb45174fdf11215395c7 | ||
| ssdeep | 192:uU5z9iLjq2pJk+/qcJklyJOEdVLsWGQwrgAh:3z9AbJH/IwJOsO/QwrgC | ||
| imphash | fd410436ce0407a0a8f79bfce8af0bc3 | ||
| impfuzzy | 6:9mRxybmRxn5X0ZRHmRxT7mRx8Jt0yRlbmARrKXVNIV5GGaJvuqBYq0IquZzwD3:YRJRJJoARZqRNqBrKlaRa91Kq0iZzwD3 | ||
Network IP location
Signature (12cnts)
| Level | Description |
|---|---|
| watch | Communicates with host for which no DNS query was performed |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates a suspicious process |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Performs some HTTP requests |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Command line console output was observed |
| info | One or more processes crashed |
Rules (15cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| notice | Create_Service | Create a windows service | memory |
| notice | Escalate_priviledges | Escalate priviledges | memory |
| notice | Str_Win32_Http_API | Match Windows Http API call | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerException__SetConsoleCtrl | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x2bec19128 DeleteCriticalSection
0x2bec19130 EnterCriticalSection
0x2bec19138 GetLastError
0x2bec19140 InitializeCriticalSection
0x2bec19148 LeaveCriticalSection
0x2bec19150 Sleep
0x2bec19158 TlsGetValue
0x2bec19160 VirtualProtect
0x2bec19168 VirtualQuery
0x2bec19170 WinExec
msvcrt.dll
0x2bec19180 __iob_func
0x2bec19188 _amsg_exit
0x2bec19190 _initterm
0x2bec19198 _lock
0x2bec191a0 _unlock
0x2bec191a8 abort
0x2bec191b0 calloc
0x2bec191b8 free
0x2bec191c0 fwrite
0x2bec191c8 realloc
0x2bec191d0 strlen
0x2bec191d8 strncmp
0x2bec191e0 vfprintf
USER32.dll
0x2bec191f0 MessageBoxA
EAT(Export Address Table) Library
0x2bec13000 hash
0x2bec113a0 reverseString
0x2bec113f0 xlAutoOpen
KERNEL32.dll
0x2bec19128 DeleteCriticalSection
0x2bec19130 EnterCriticalSection
0x2bec19138 GetLastError
0x2bec19140 InitializeCriticalSection
0x2bec19148 LeaveCriticalSection
0x2bec19150 Sleep
0x2bec19158 TlsGetValue
0x2bec19160 VirtualProtect
0x2bec19168 VirtualQuery
0x2bec19170 WinExec
msvcrt.dll
0x2bec19180 __iob_func
0x2bec19188 _amsg_exit
0x2bec19190 _initterm
0x2bec19198 _lock
0x2bec191a0 _unlock
0x2bec191a8 abort
0x2bec191b0 calloc
0x2bec191b8 free
0x2bec191c0 fwrite
0x2bec191c8 realloc
0x2bec191d0 strlen
0x2bec191d8 strncmp
0x2bec191e0 vfprintf
USER32.dll
0x2bec191f0 MessageBoxA
EAT(Export Address Table) Library
0x2bec13000 hash
0x2bec113a0 reverseString
0x2bec113f0 xlAutoOpen