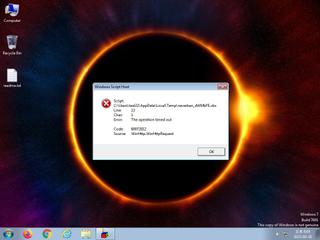
ScreenShot
| Created | 2023.09.26 18:05 | Machine | s1_win7_x6403_us |
| Filename | neverban_dWMkPE.vbs | ||
| Type | ASCII text, with very long lines, with CRLF line terminators | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 5 detected () | ||
| md5 | 1bd0900f5c260ec597662cbcdb396d4a | ||
| sha256 | a184fa874e95c0338f6d966d41454b8a6e40c416f5ee710e21362f9af94dcd9e | ||
| ssdeep | 48:IDKsFeq8Q1O6Z+20CfFENmWLFPR9OaaoYFF6ab:ID7X8WOKiCfuvFPRJqz | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| watch | Communicates with host for which no DNS query was performed |
| watch | Network communications indicative of a potential document or script payload download was initiated by the process wscript.exe |
| watch | Wscript.exe initiated network communications indicative of a script based payload download |
| notice | File has been identified by 5 AntiVirus engines on VirusTotal as malicious |
Rules (0cnts)
| Level | Name | Description | Collection |
|---|