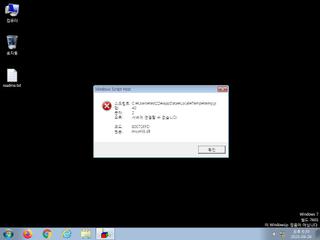
ScreenShot
| Created | 2023.09.26 18:32 | Machine | s1_win7_x6401 |
| Filename | temp.js | ||
| Type | ASCII text, with CRLF line terminators | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 8 detected (Eldorado, gen60, HTMJS, Detected) | ||
| md5 | 98647908b75a0485ad44a786e5967aa4 | ||
| sha256 | 9ac28139acecfbd136638a64c52e5cea3bd2b0c9fe933cae7b88b09c33f52a40 | ||
| ssdeep | 48:zivXcK7alQZ4m0vHTR8oxJW0JhWAJ1sZ1qoRD/7JhGz6nElyiQmnQdoXibsKLaxt:ziv987Y0JAi1QcoZJcenElybmnQdoXlL | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| danger | Connects to IP addresses that are no longer responding to requests (legitimate services will remain up-and-running usually) |
| watch | Communicates with host for which no DNS query was performed |
| notice | File has been identified by 8 AntiVirus engines on VirusTotal as malicious |
| info | One or more processes crashed |
Rules (0cnts)
| Level | Name | Description | Collection |
|---|