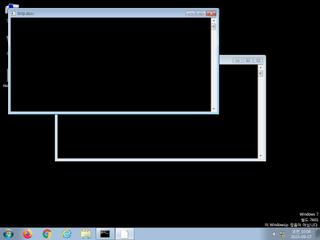
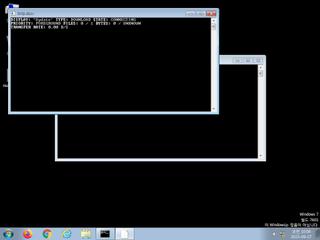
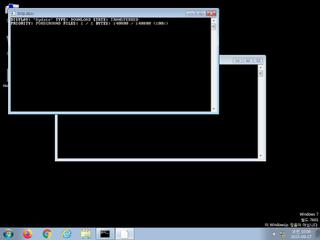
ScreenShot
| Created | 2023.09.27 10:07 | Machine | s1_win7_x6401 |
| Filename | 3ntp.docx.lnk | ||
| Type | MS Windows shortcut, Item id list present, Points to a file or directory, Has Description string, Has Relative path, Has command line arguments, Icon number=0, Archive, ctime=Wed Oct 6 04:31:17 2021, mtime=Sat Sep 23 12:44:40 2023, atime=Wed Oct 6 04:31 | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 29 detected (WinLNK, GenBadur, FBRQ, Pantera, many, Bitsldr, Camelot, genw, Ncnw, LnkGen, LNKEXEC, DownLnk, Outbreak, AggBITSAbuse, Detected, ai score=89, Link, DoubleRun, Probably Heur, LNKScript, BitsAdmin, CLASSIC) | ||
| md5 | 10f3245bc055a7e6eec1bedd7d12e711 | ||
| sha256 | f54692a2ffa5029e44823a4f6b67151477b18cba62d3ea2137452f0b113948c9 | ||
| ssdeep | 24:8w/0IJ3q3c/wT+MacqJM9BGPJ+/p9mlsiiWjECu5CwdRqaq3O0Kap1deOm:8w/z3DzcqJwGnsiiWjECcREb1gO | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (14cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 29 AntiVirus engines on VirusTotal as malicious |
| watch | BITSAdmin Tool has been invoked to download a file |
| watch | Communicates with host for which no DNS query was performed |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| watch | Uses suspicious command line tools or Windows utilities |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates a shortcut to an executable file |
| notice | Creates a suspicious process |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Performs some HTTP requests |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Command line console output was observed |
Rules (35cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Network_Downloader | File Downloader | memory |
| watch | schtasks_Zero | task schedule | memory |
| notice | Code_injection | Code injection with CreateRemoteThread in a remote process | memory |
| notice | Create_Service | Create a windows service | memory |
| notice | Escalate_priviledges | Escalate priviledges | memory |
| notice | Generic_PWS_Memory_Zero | PWS Memory | memory |
| notice | KeyLogger | Run a KeyLogger | memory |
| notice | local_credential_Steal | Steal credential | memory |
| notice | Network_DGA | Communication using DGA | memory |
| notice | Network_DNS | Communications use DNS | memory |
| notice | Network_FTP | Communications over FTP | memory |
| notice | Network_HTTP | Communications over HTTP | memory |
| notice | Network_P2P_Win | Communications over P2P network | memory |
| notice | Network_TCP_Socket | Communications over RAW Socket | memory |
| notice | ScreenShot | Take ScreenShot | memory |
| notice | Sniff_Audio | Record Audio | memory |
| notice | Str_Win32_Http_API | Match Windows Http API call | memory |
| notice | Str_Win32_Internet_API | Match Windows Inet API call | memory |
| info | anti_dbg | Checks if being debugged | memory |
| info | antisb_threatExpert | Anti-Sandbox checks for ThreatExpert | memory |
| info | Check_Dlls | (no description) | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerCheck__RemoteAPI | (no description) | memory |
| info | DebuggerException__ConsoleCtrl | (no description) | memory |
| info | DebuggerException__SetConsoleCtrl | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | lnk_file_format | Microsoft Windows Shortcut File Format | binaries (upload) |
| info | Lnk_Format_Zero | LNK Format | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
| info | win_hook | Affect hook table | memory |
Suricata ids
ET INFO Executable Download from dotted-quad Host
ET HUNTING Suspicious BITS EXE DL From Dotted Quad
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
ET HUNTING Suspicious BITS EXE DL From Dotted Quad
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response