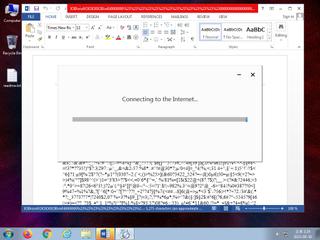
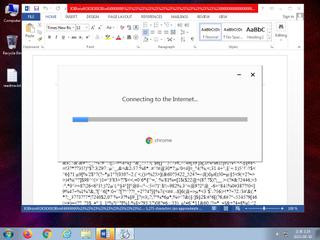
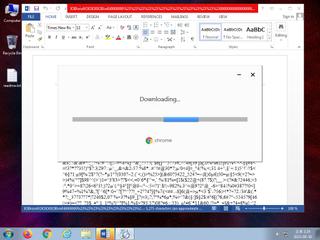
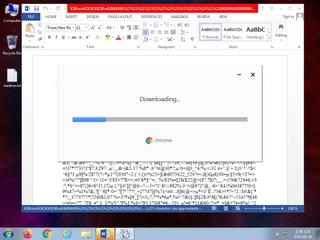
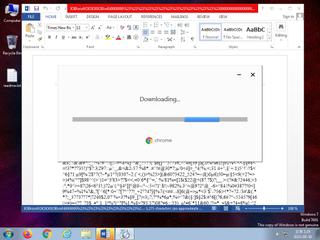
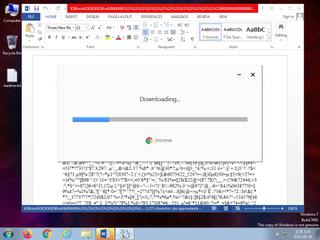
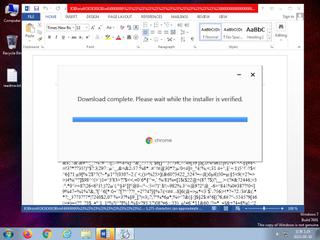
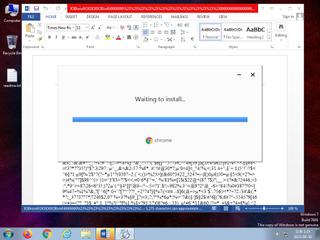
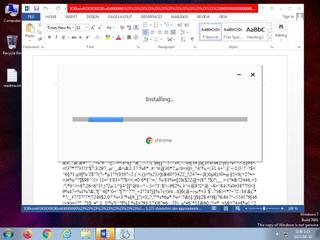
ScreenShot
| Created | 2023.09.30 13:33 | Machine | s1_win7_x6403 |
| Filename | IOI0ioio0OIOIO0IOI0ioi0i0000000%23%23%23%23%23%23%23%23%23%23%23%23%23%23000000000000000000%23%23%23%23%23%23%23%23%23%23%23%23%23%2300000000.doc | ||
| Type | ISO-8859 text, with very long lines, with CRLF, CR, LF line terminators | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 29 detected (ObfsObjDat, Save, CVE-2017-1188, multiple detections, Malicious, score, CVE-2018-0802, dinbqn, CLASSIC, Malformed, CVE-2018-0798, RTFMALFORM, Wacatac, Detected, Malform, RTFObfustream, ai score=84, Probably Heur, RTFBadHeader) | ||
| md5 | 750637aa4adce8ce221b8d8755dbbaf8 | ||
| sha256 | 2e850540fca520336d35447b1592d9d4ee27b139c83ffec3b12bc6d31fdc4f2f | ||
| ssdeep | 384:dEhzWuGu5+nEEKFBe4FGa27Y6QJI8dvDhQfCecbYryaUHuEz:w6pEEKFQoYY6MIOSfTKHaoz | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (10cnts)
| Level | Description |
|---|---|
| warning | File has been identified by 29 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| notice | An application raised an exception which may be indicative of an exploit crash |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
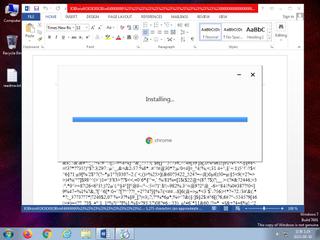
| notice | Creates (office) documents on the filesystem |
| notice | Creates hidden or system file |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Performs some HTTP requests |
| notice | Sends data using the HTTP POST Method |
| info | One or more processes crashed |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | MS_RTF_Suspicious_documents | Suspicious documents using RTF document OLE object | binaries (upload) |
| warning | SUSP_INDICATOR_RTF_MalVer_Objects | Detects RTF documents with non-standard version and embedding one of the object mostly observed in exploit (e.g. CVE-2017-11882) documents. | binaries (upload) |
| info | Rich_Text_Format_Zero | Rich Text Format Signature Zero | binaries (upload) |
Network (33cnts) ?
Suricata ids
ET INFO Executable Download from dotted-quad Host
ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M1
ET POLICY PE EXE or DLL Windows file download HTTP
ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M2
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET INFO EXE - Served Attached HTTP
ET INFO Observed Google DNS over HTTPS Domain (dns .google in TLS SNI)
ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M1
ET POLICY PE EXE or DLL Windows file download HTTP
ET MALWARE Likely Evil EXE download from dotted Quad by MSXMLHTTP M2
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET INFO EXE - Served Attached HTTP
ET INFO Observed Google DNS over HTTPS Domain (dns .google in TLS SNI)