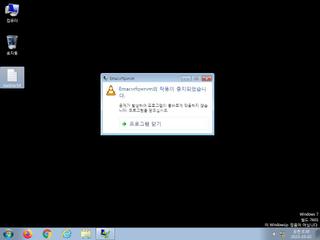
ScreenShot
| Created | 2023.10.02 08:42 | Machine | s1_win7_x6401 |
| Filename | ed1.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 30 detected (AIDetectMalware, Zusy, MachineLearning, Anomalous, Save, Hacktool, malicious, high confidence, score, TrojanX, high, Phonzy, ai score=88, unsafe, CLASSIC, Static AI, Malicious PE, susgen, ZevbaF, @m0@aywm, confidence) | ||
| md5 | d1906fd8d9e6b18ee8a134e81982e23a | ||
| sha256 | cef823e614c07e8813c9e32db81d8dc6a20d00a3e55aca97a6a5c340aa6e5d1c | ||
| ssdeep | 24576:4s9rN9YwPzIFbDslb50xVwJF5Jq9HnyKLW2U08U/7zgesADyI:t9rNWwbeP9wsnC0Z70esADyI | ||
| imphash | c1026f3bc4dbd1c7779566798486c792 | ||
| impfuzzy | 48:MrK//1wzZQwgobV2gkzRxR3Yl39jwoFHqJI4TU2FNmWc4lhHpw+pHxmkSuDgYxDC:UK//1GZQfobogkzRxRuNjdFHqJIAU2F2 | ||
Network IP location
Signature (31cnts)
| Level | Description |
|---|---|
| danger | Executed a process and injected code into it |
| danger | File has been identified by 30 AntiVirus engines on VirusTotal as malicious |
| watch | Collects information about installed applications |
| watch | Communicates with host for which no DNS query was performed |
| watch | Detects Avast Antivirus through the presence of a library |
| watch | Executes one or more WMI queries |
| watch | Harvests credentials from local FTP client softwares |
| watch | One or more of the buffers contains an embedded PE file |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| watch | Used NtSetContextThread to modify a thread in a remote process indicative of process injection |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | Executes one or more WMI queries which can be used to identify virtual machines |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | One or more potentially interesting buffers were extracted |
| notice | Performs some HTTP requests |
| notice | Queries for potentially installed applications |
| notice | Steals private information from local Internet browsers |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | One or more processes crashed |
| info | Queries for the computername |
| info | Tries to locate where the browsers are installed |
| info | Uses Windows APIs to generate a cryptographic key |
Rules (19cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | RedLine_Stealer_m_Zero | RedLine stealer | memory |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (download) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | anti_dbg | Checks if being debugged | memory |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
Suricata ids
ET INFO Microsoft net.tcp Connection Initialization Activity
ET MALWARE Redline Stealer TCP CnC Activity
ET MALWARE [ANY.RUN] RedLine Stealer Related (MC-NMF Authorization)
ET MALWARE Redline Stealer TCP CnC - Id1Response
ET MALWARE Redline Stealer Activity (Response)
ET MALWARE Possible Malicous Macro DL EXE Jul 01 2016 (userdir dotted quad)
ET INFO Executable Download from dotted-quad Host
ET POLICY PE EXE or DLL Windows file download HTTP
ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
ET MALWARE Redline Stealer TCP CnC Activity
ET MALWARE [ANY.RUN] RedLine Stealer Related (MC-NMF Authorization)
ET MALWARE Redline Stealer TCP CnC - Id1Response
ET MALWARE Redline Stealer Activity (Response)
ET MALWARE Possible Malicous Macro DL EXE Jul 01 2016 (userdir dotted quad)
ET INFO Executable Download from dotted-quad Host
ET POLICY PE EXE or DLL Windows file download HTTP
ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
PE API
IAT(Import Address Table) Library
KERNEL32.DLL
0x401000 Sleep
0x401004 GetTickCount
0x401008 RtlFillMemory
ADVAPI32.DLL
0x401010 CryptAcquireContextW
0x401014 CryptDeriveKey
MSVBVM60.DLL
0x40101c _CIcos
0x401020 _adj_fptan
0x401024 __vbaVarMove
0x401028 __vbaVarVargNofree
0x40102c __vbaFreeVar
0x401030 __vbaLenBstr
0x401034 __vbaStrVarMove
0x401038 __vbaFreeVarList
0x40103c _adj_fdiv_m64
0x401040 None
0x401044 __vbaStrErrVarCopy
0x401048 _adj_fprem1
0x40104c __vbaStrCat
0x401050 __vbaSetSystemError
0x401054 __vbaRecDestruct
0x401058 __vbaHresultCheckObj
0x40105c _adj_fdiv_m32
0x401060 __vbaAryDestruct
0x401064 __vbaObjSet
0x401068 None
0x40106c _adj_fdiv_m16i
0x401070 __vbaObjSetAddref
0x401074 _adj_fdivr_m16i
0x401078 __vbaRefVarAry
0x40107c __vbaBoolVarNull
0x401080 _CIsin
0x401084 __vbaErase
0x401088 __vbaVarCmpGt
0x40108c __vbaVarZero
0x401090 __vbaChkstk
0x401094 None
0x401098 EVENT_SINK_AddRef
0x40109c DllFunctionCall
0x4010a0 __vbaRedimPreserve
0x4010a4 _adj_fpatan
0x4010a8 __vbaRedim
0x4010ac EVENT_SINK_Release
0x4010b0 _CIsqrt
0x4010b4 EVENT_SINK_QueryInterface
0x4010b8 __vbaExceptHandler
0x4010bc None
0x4010c0 _adj_fprem
0x4010c4 _adj_fdivr_m64
0x4010c8 None
0x4010cc None
0x4010d0 __vbaFPException
0x4010d4 __vbaStrVarVal
0x4010d8 __vbaUbound
0x4010dc __vbaVarCat
0x4010e0 None
0x4010e4 _CIlog
0x4010e8 __vbaNew2
0x4010ec _adj_fdiv_m32i
0x4010f0 _adj_fdivr_m32i
0x4010f4 __vbaStrCopy
0x4010f8 __vbaI4Str
0x4010fc __vbaVarNot
0x401100 __vbaFreeStrList
0x401104 _adj_fdivr_m32
0x401108 _adj_fdiv_r
0x40110c None
0x401110 __vbaI4Var
0x401114 __vbaVarAdd
0x401118 __vbaAryLock
0x40111c __vbaVarDup
0x401120 __vbaVarCopy
0x401124 None
0x401128 _CIatan
0x40112c __vbaCastObj
0x401130 __vbaStrMove
0x401134 _allmul
0x401138 __vbaLenVarB
0x40113c _CItan
0x401140 __vbaAryUnlock
0x401144 _CIexp
0x401148 __vbaI4ErrVar
0x40114c __vbaFreeObj
0x401150 __vbaFreeStr
EAT(Export Address Table) is none
KERNEL32.DLL
0x401000 Sleep
0x401004 GetTickCount
0x401008 RtlFillMemory
ADVAPI32.DLL
0x401010 CryptAcquireContextW
0x401014 CryptDeriveKey
MSVBVM60.DLL
0x40101c _CIcos
0x401020 _adj_fptan
0x401024 __vbaVarMove
0x401028 __vbaVarVargNofree
0x40102c __vbaFreeVar
0x401030 __vbaLenBstr
0x401034 __vbaStrVarMove
0x401038 __vbaFreeVarList
0x40103c _adj_fdiv_m64
0x401040 None
0x401044 __vbaStrErrVarCopy
0x401048 _adj_fprem1
0x40104c __vbaStrCat
0x401050 __vbaSetSystemError
0x401054 __vbaRecDestruct
0x401058 __vbaHresultCheckObj
0x40105c _adj_fdiv_m32
0x401060 __vbaAryDestruct
0x401064 __vbaObjSet
0x401068 None
0x40106c _adj_fdiv_m16i
0x401070 __vbaObjSetAddref
0x401074 _adj_fdivr_m16i
0x401078 __vbaRefVarAry
0x40107c __vbaBoolVarNull
0x401080 _CIsin
0x401084 __vbaErase
0x401088 __vbaVarCmpGt
0x40108c __vbaVarZero
0x401090 __vbaChkstk
0x401094 None
0x401098 EVENT_SINK_AddRef
0x40109c DllFunctionCall
0x4010a0 __vbaRedimPreserve
0x4010a4 _adj_fpatan
0x4010a8 __vbaRedim
0x4010ac EVENT_SINK_Release
0x4010b0 _CIsqrt
0x4010b4 EVENT_SINK_QueryInterface
0x4010b8 __vbaExceptHandler
0x4010bc None
0x4010c0 _adj_fprem
0x4010c4 _adj_fdivr_m64
0x4010c8 None
0x4010cc None
0x4010d0 __vbaFPException
0x4010d4 __vbaStrVarVal
0x4010d8 __vbaUbound
0x4010dc __vbaVarCat
0x4010e0 None
0x4010e4 _CIlog
0x4010e8 __vbaNew2
0x4010ec _adj_fdiv_m32i
0x4010f0 _adj_fdivr_m32i
0x4010f4 __vbaStrCopy
0x4010f8 __vbaI4Str
0x4010fc __vbaVarNot
0x401100 __vbaFreeStrList
0x401104 _adj_fdivr_m32
0x401108 _adj_fdiv_r
0x40110c None
0x401110 __vbaI4Var
0x401114 __vbaVarAdd
0x401118 __vbaAryLock
0x40111c __vbaVarDup
0x401120 __vbaVarCopy
0x401124 None
0x401128 _CIatan
0x40112c __vbaCastObj
0x401130 __vbaStrMove
0x401134 _allmul
0x401138 __vbaLenVarB
0x40113c _CItan
0x401140 __vbaAryUnlock
0x401144 _CIexp
0x401148 __vbaI4ErrVar
0x40114c __vbaFreeObj
0x401150 __vbaFreeStr
EAT(Export Address Table) is none