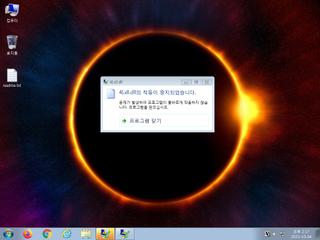
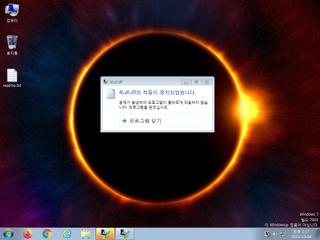
ScreenShot
| Created | 2023.10.04 14:19 | Machine | s1_win7_x6402 |
| Filename | 4I.xll | ||
| Type | PE32+ executable (DLL) (GUI) x86-64 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | |||
| md5 | b33c17701e564f148250e540bcf58c96 | ||
| sha256 | d68953754d349bdeba23b51e9f7d58b03cff4c64f73ed7a47bff043ed014f680 | ||
| ssdeep | 1536:M7pxSJsy6Nh5wFHssKjrtN/5jqzyCNwGXGhrMc450XN:oYwNh5wFHssKXnxjNCNHGzXN | ||
| imphash | f599f6d6eed879ac9612841c28ee3418 | ||
| impfuzzy | 12:jYRJRJJoAR+hqR2qBrKHlJYasTqa91KddFQJqcsaGXZn:j8fjB+kTYliHx91SDcqcFGXZn | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| notice | A process created a hidden window |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates a suspicious process |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Collects information to fingerprint the system (MachineGuid |
| info | Command line console output was observed |
| info | One or more processes crashed |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x2229b11a4 CopyFileW
0x2229b11ac DeleteCriticalSection
0x2229b11b4 EnterCriticalSection
0x2229b11bc GetLastError
0x2229b11c4 InitializeCriticalSection
0x2229b11cc IsDBCSLeadByteEx
0x2229b11d4 LeaveCriticalSection
0x2229b11dc MultiByteToWideChar
0x2229b11e4 Sleep
0x2229b11ec TlsGetValue
0x2229b11f4 VirtualProtect
0x2229b11fc VirtualQuery
0x2229b1204 WinExec
msvcrt.dll
0x2229b1214 ___lc_codepage_func
0x2229b121c ___mb_cur_max_func
0x2229b1224 __iob_func
0x2229b122c _amsg_exit
0x2229b1234 _errno
0x2229b123c _initterm
0x2229b1244 _lock
0x2229b124c _unlock
0x2229b1254 abort
0x2229b125c calloc
0x2229b1264 free
0x2229b126c fwrite
0x2229b1274 getc
0x2229b127c islower
0x2229b1284 isspace
0x2229b128c isupper
0x2229b1294 isxdigit
0x2229b129c localeconv
0x2229b12a4 malloc
0x2229b12ac memcpy
0x2229b12b4 memset
0x2229b12bc realloc
0x2229b12c4 strcat
0x2229b12cc strlen
0x2229b12d4 strncmp
0x2229b12dc strtol
0x2229b12e4 strtoul
0x2229b12ec tolower
0x2229b12f4 ungetc
0x2229b12fc vfprintf
EAT(Export Address Table) Library
0x2229ab000 hash
0x2229a1470 xlAutoOpen
0x2229a13d0 xor_decrypt
KERNEL32.dll
0x2229b11a4 CopyFileW
0x2229b11ac DeleteCriticalSection
0x2229b11b4 EnterCriticalSection
0x2229b11bc GetLastError
0x2229b11c4 InitializeCriticalSection
0x2229b11cc IsDBCSLeadByteEx
0x2229b11d4 LeaveCriticalSection
0x2229b11dc MultiByteToWideChar
0x2229b11e4 Sleep
0x2229b11ec TlsGetValue
0x2229b11f4 VirtualProtect
0x2229b11fc VirtualQuery
0x2229b1204 WinExec
msvcrt.dll
0x2229b1214 ___lc_codepage_func
0x2229b121c ___mb_cur_max_func
0x2229b1224 __iob_func
0x2229b122c _amsg_exit
0x2229b1234 _errno
0x2229b123c _initterm
0x2229b1244 _lock
0x2229b124c _unlock
0x2229b1254 abort
0x2229b125c calloc
0x2229b1264 free
0x2229b126c fwrite
0x2229b1274 getc
0x2229b127c islower
0x2229b1284 isspace
0x2229b128c isupper
0x2229b1294 isxdigit
0x2229b129c localeconv
0x2229b12a4 malloc
0x2229b12ac memcpy
0x2229b12b4 memset
0x2229b12bc realloc
0x2229b12c4 strcat
0x2229b12cc strlen
0x2229b12d4 strncmp
0x2229b12dc strtol
0x2229b12e4 strtoul
0x2229b12ec tolower
0x2229b12f4 ungetc
0x2229b12fc vfprintf
EAT(Export Address Table) Library
0x2229ab000 hash
0x2229a1470 xlAutoOpen
0x2229a13d0 xor_decrypt