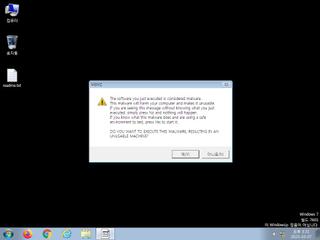
ScreenShot
| Created | 2023.10.07 15:33 | Machine | s1_win7_x6401 |
| Filename | a3d5715a81f2fbeb_memz.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 65 detected (AIDetectMalware, DiskWriter, tnbd, Malicious, score, Mauvaise, S2299117, unsafe, AgentWDCR, Save, KillMBR, BKSD, RJSJ, Deltree Trojan, high confidence, Zmem, ekeock, MalwareX, Gencirc, Rozena, MEMZWIPER, high, EncPk, TLUCQP, ai score=100, TSGeneric, Malware@#azw7fthdwxzq, Dynamer, Detected, BScope, Boot, KTSE, Igent, bUFeyO, susgen, confidence, 100%) | ||
| md5 | 19dbec50735b5f2a72d4199c4e184960 | ||
| sha256 | a3d5715a81f2fbeb5f76c88c9c21eeee87142909716472f911ff6950c790c24d | ||
| ssdeep | 192:sIvxdXSQeWSg9JJS/lcIEiwqZKBkDFR43xWTM3LHn8f26gyr6yfFCj3r:sMVSaSEglcIqq3agmLc+6gyWqFCj | ||
| imphash | 52753d226ff5a8a88caf9829928cd5d1 | ||
| impfuzzy | 24:StO7sq8RApzJDILwkgTz3zrzi/QgSLk5rAbw3FEU0v/KA5JdAAMxxxryFzzzCajS:vqaZmL/gfDrz9gSY5rAbuFl0v/KA5JGl | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 65 AntiVirus engines on VirusTotal as malicious |
| info | Checks amount of memory in system |
| info | One or more processes crashed |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x402024 WriteFile
0x402028 CloseHandle
0x40202c lstrcmpA
0x402030 lstrcmpW
0x402034 LoadLibraryA
0x402038 GetModuleFileNameW
0x40203c GetCommandLineW
0x402040 Sleep
0x402044 SetPriorityClass
0x402048 CreateToolhelp32Snapshot
0x40204c Process32FirstW
0x402050 Process32NextW
0x402054 GlobalAlloc
0x402058 GlobalFree
0x40205c lstrlenW
0x402060 GetCurrentThreadId
0x402064 CreateThread
0x402068 ExitProcess
0x40206c GetCurrentProcess
0x402070 OpenProcess
0x402074 LocalFree
0x402078 LocalAlloc
0x40207c CreateFileA
0x402080 GetProcAddress
USER32.dll
0x4020a4 GetWindowRect
0x4020a8 MessageBoxW
0x4020ac SetCursorPos
0x4020b0 GetCursorPos
0x4020b4 GetDesktopWindow
0x4020b8 EnumChildWindows
0x4020bc CallNextHookEx
0x4020c0 LoadIconW
0x4020c4 ReleaseDC
0x4020c8 UnhookWindowsHookEx
0x4020cc MessageBoxA
0x4020d0 GetSystemMetrics
0x4020d4 CreateWindowExA
0x4020d8 RegisterClassExA
0x4020dc DefWindowProcW
0x4020e0 ExitWindowsEx
0x4020e4 DispatchMessageW
0x4020e8 TranslateMessage
0x4020ec GetWindowDC
0x4020f0 DrawIcon
0x4020f4 SendInput
0x4020f8 SendMessageTimeoutW
0x4020fc GetMessageW
0x402100 SetWindowsHookExW
GDI32.dll
0x402018 BitBlt
0x40201c StretchBlt
ADVAPI32.dll
0x402000 OpenProcessToken
0x402004 AdjustTokenPrivileges
0x402008 LookupPrivilegeValueW
0x40200c CryptAcquireContextW
0x402010 CryptGenRandom
SHELL32.dll
0x402090 CommandLineToArgvW
0x402094 ShellExecuteW
0x402098 ShellExecuteA
0x40209c ShellExecuteExW
WINMM.dll
0x402108 PlaySoundA
PSAPI.DLL
0x402088 GetProcessImageFileNameA
EAT(Export Address Table) is none
KERNEL32.dll
0x402024 WriteFile
0x402028 CloseHandle
0x40202c lstrcmpA
0x402030 lstrcmpW
0x402034 LoadLibraryA
0x402038 GetModuleFileNameW
0x40203c GetCommandLineW
0x402040 Sleep
0x402044 SetPriorityClass
0x402048 CreateToolhelp32Snapshot
0x40204c Process32FirstW
0x402050 Process32NextW
0x402054 GlobalAlloc
0x402058 GlobalFree
0x40205c lstrlenW
0x402060 GetCurrentThreadId
0x402064 CreateThread
0x402068 ExitProcess
0x40206c GetCurrentProcess
0x402070 OpenProcess
0x402074 LocalFree
0x402078 LocalAlloc
0x40207c CreateFileA
0x402080 GetProcAddress
USER32.dll
0x4020a4 GetWindowRect
0x4020a8 MessageBoxW
0x4020ac SetCursorPos
0x4020b0 GetCursorPos
0x4020b4 GetDesktopWindow
0x4020b8 EnumChildWindows
0x4020bc CallNextHookEx
0x4020c0 LoadIconW
0x4020c4 ReleaseDC
0x4020c8 UnhookWindowsHookEx
0x4020cc MessageBoxA
0x4020d0 GetSystemMetrics
0x4020d4 CreateWindowExA
0x4020d8 RegisterClassExA
0x4020dc DefWindowProcW
0x4020e0 ExitWindowsEx
0x4020e4 DispatchMessageW
0x4020e8 TranslateMessage
0x4020ec GetWindowDC
0x4020f0 DrawIcon
0x4020f4 SendInput
0x4020f8 SendMessageTimeoutW
0x4020fc GetMessageW
0x402100 SetWindowsHookExW
GDI32.dll
0x402018 BitBlt
0x40201c StretchBlt
ADVAPI32.dll
0x402000 OpenProcessToken
0x402004 AdjustTokenPrivileges
0x402008 LookupPrivilegeValueW
0x40200c CryptAcquireContextW
0x402010 CryptGenRandom
SHELL32.dll
0x402090 CommandLineToArgvW
0x402094 ShellExecuteW
0x402098 ShellExecuteA
0x40209c ShellExecuteExW
WINMM.dll
0x402108 PlaySoundA
PSAPI.DLL
0x402088 GetProcessImageFileNameA
EAT(Export Address Table) is none