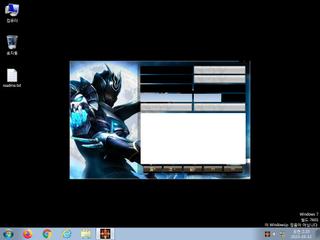
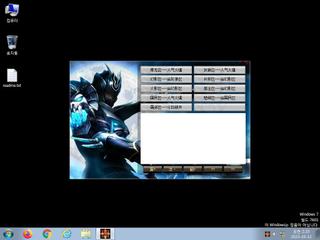
ScreenShot
| Created | 2023.10.12 02:23 | Machine | s1_win7_x6401 |
| Filename | up.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 55 detected (Graftor, GenericKD, Artemis, Asprotect, Save, malicious, confidence, 100%, ZexaF, @RZaa4faPRnb, Genus, ABApplication, GMZD, Attribute, HighConfidence, high confidence, score, xbcswp, jxonpw, TrojanX, Agen, Kqil, R03BC0DHI23, Static AI, Suspicious PE, ai score=100, Malware@#3vopj598hqcmk, Detected, R589938, TScope, unsafe, Chgt, susgen) | ||
| md5 | 5e6716377dc71d7fa5c97d778c154ce4 | ||
| sha256 | 724bfaabd60cc24321154d31edc012830a85aa2597275702364e7687d3abcf8d | ||
| ssdeep | 98304:dG94hQQPjg4HU+DTwl9zOHz7t1Q5RRlWY9HJ3CChZfYQmGkHxEWmUbpapq6LC:dGmJg+U4TIqY5BZdwnGIIUbpa3C | ||
| imphash | c9a3edae9204609d90d0770c3583acd8 | ||
| impfuzzy | 12:mDzjA9A+pZ1nd6wuRTf1E3xaZCdG4HWrMLYo01ZC3PwUK3EUe:mDnWA+pZ1swu7Eho4bHyXI3PwzE3 | ||
Network IP location
Signature (23cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 55 AntiVirus engines on VirusTotal as malicious |
| watch | Checks the presence of IDE drives in the registry |
| watch | Detects Virtual Machines through their custom firmware |
| watch | Disables proxy possibly for traffic interception |
| watch | Expresses interest in specific running processes |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Checks whether any human activity is being performed by constantly checking whether the foreground window changed |
| notice | Creates a shortcut to an executable file |
| notice | Creates executable files on the filesystem |
| notice | Foreign language identified in PE resource |
| notice | Performs some HTTP requests |
| notice | Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Collects information to fingerprint the system (MachineGuid |
| info | One or more processes crashed |
| info | Queries for the computername |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | The executable uses a known packer |
| info | The file contains an unknown PE resource name possibly indicative of a packer |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | lnk_file_format | Microsoft Windows Shortcut File Format | binaries (download) |
| info | Lnk_Format_Zero | LNK Format | binaries (download) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (5cnts) ?
Suricata ids
PE API
IAT(Import Address Table) Library
kernel32.dll
0x322bbbf4 GetProcAddress
0x322bbbf8 GetModuleHandleA
0x322bbbfc LoadLibraryA
user32.dll
0x322bbf4a GetKeyboardType
advapi32.dll
0x322bbf52 RegQueryValueExA
oleaut32.dll
0x322bbf5a SysFreeString
advapi32.dll
0x322bbf62 RegSetValueExA
version.dll
0x322bbf6a VerQueryValueA
gdi32.dll
0x322bbf72 UnrealizeObject
user32.dll
0x322bbf7a CreateWindowExA
ole32.dll
0x322bbf82 IsEqualGUID
oleaut32.dll
0x322bbf8a SafeArrayPtrOfIndex
ole32.dll
0x322bbf92 CreateStreamOnHGlobal
oleaut32.dll
0x322bbf9a CreateErrorInfo
comctl32.dll
0x322bbfa2 ImageList_SetIconSize
shell32.dll
0x322bbfaa Shell_NotifyIconA
wininet.dll
0x322bbfb2 InternetSetOptionA
urlmon.dll
0x322bbfba CoInternetCreateZoneManager
shell32.dll
0x322bbfc2 SHGetSpecialFolderLocation
wsock32.dll
0x322bbfca WSACleanup
winmm.dll
0x322bbfd2 timeGetTime
ntdll.dll
0x322bbfda NtReadVirtualMemory
ole32.dll
0x322bbfe2 PropVariantClear
advapi32.dll
0x322bbfea AddAccessAllowedAce
oleaut32.dll
0x322bbff2 VariantChangeTypeEx
kernel32.dll
0x322bbffa RaiseException
EAT(Export Address Table) is none
kernel32.dll
0x322bbbf4 GetProcAddress
0x322bbbf8 GetModuleHandleA
0x322bbbfc LoadLibraryA
user32.dll
0x322bbf4a GetKeyboardType
advapi32.dll
0x322bbf52 RegQueryValueExA
oleaut32.dll
0x322bbf5a SysFreeString
advapi32.dll
0x322bbf62 RegSetValueExA
version.dll
0x322bbf6a VerQueryValueA
gdi32.dll
0x322bbf72 UnrealizeObject
user32.dll
0x322bbf7a CreateWindowExA
ole32.dll
0x322bbf82 IsEqualGUID
oleaut32.dll
0x322bbf8a SafeArrayPtrOfIndex
ole32.dll
0x322bbf92 CreateStreamOnHGlobal
oleaut32.dll
0x322bbf9a CreateErrorInfo
comctl32.dll
0x322bbfa2 ImageList_SetIconSize
shell32.dll
0x322bbfaa Shell_NotifyIconA
wininet.dll
0x322bbfb2 InternetSetOptionA
urlmon.dll
0x322bbfba CoInternetCreateZoneManager
shell32.dll
0x322bbfc2 SHGetSpecialFolderLocation
wsock32.dll
0x322bbfca WSACleanup
winmm.dll
0x322bbfd2 timeGetTime
ntdll.dll
0x322bbfda NtReadVirtualMemory
ole32.dll
0x322bbfe2 PropVariantClear
advapi32.dll
0x322bbfea AddAccessAllowedAce
oleaut32.dll
0x322bbff2 VariantChangeTypeEx
kernel32.dll
0x322bbffa RaiseException
EAT(Export Address Table) is none