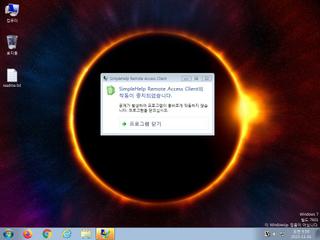
ScreenShot
| Created | 2023.11.01 09:58 | Machine | s1_win7_x6402 |
| Filename | questionnaire.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 13 detected (Artemis, unsafe, RemoteAdmin, Remsim, Hacktool, CLOUD, Generic Reputation PUA, Tool, MALICIOUS, susgen) | ||
| md5 | 065f0871b6025b8e61f35a188bca1d5c | ||
| sha256 | a2ae5e994c0b515cadd425cfda4d4ae33b71893c45b702e1f8c1a495dc1b440f | ||
| ssdeep | 49152:D2bzQS8PygnTnAJrvdJEiOYsNmRUxpV4Geb:9RnTn6rFJpLsMR6KRb | ||
| imphash | 6b43713c2dcdf19e54a9964767500d9f | ||
| impfuzzy | 48:ReX7ry8dumEAl5ZOqcZZGw99QPpCxmzcVTcUY0tmyLIlrz/3pgn1dnHSeXxCGl+M:KvumEAl5ZlcZZGw/0omzMwx0tQNAyiq8 | ||
Network IP location
Signature (8cnts)
| Level | Description |
|---|---|
| watch | Communicates with host for which no DNS query was performed |
| watch | Deletes executed files from disk |
| watch | File has been identified by 13 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Creates executable files on the filesystem |
| info | Checks amount of memory in system |
| info | One or more processes crashed |
Rules (10cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (download) |
| info | ftp_command | ftp command | binaries (download) |
| info | IsPE64 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Suricata ids
PE API
IAT(Import Address Table) Library
WINMM.dll
0x444558 timeGetTime
WININET.dll
0x4444f0 InternetQueryOptionA
0x4444f8 InternetCloseHandle
0x444500 InternetOpenA
0x444508 HttpSendRequestA
0x444510 InternetErrorDlg
0x444518 HttpOpenRequestA
0x444520 InternetSetOptionA
0x444528 InternetReadFile
0x444530 InternetCrackUrlA
0x444538 InternetConnectA
0x444540 InternetOpenUrlA
0x444548 HttpQueryInfoA
VERSION.dll
0x4444a8 GetFileVersionInfoSizeA
0x4444b0 GetFileVersionInfoA
0x4444b8 VerQueryValueA
WINHTTP.dll
0x4444c8 WinHttpGetIEProxyConfigForCurrentUser
0x4444d0 WinHttpCloseHandle
0x4444d8 WinHttpOpen
0x4444e0 WinHttpGetProxyForUrl
COMCTL32.dll
0x444040 InitCommonControlsEx
KERNEL32.dll
0x444050 GetLocaleInfoA
0x444058 GetStringTypeW
0x444060 LCMapStringW
0x444068 LCMapStringA
0x444070 RtlLookupFunctionEntry
0x444078 RtlVirtualUnwind
0x444080 GetCurrentProcessId
0x444088 GetTickCount
0x444090 QueryPerformanceCounter
0x444098 GetStringTypeA
0x4440a0 HeapReAlloc
0x4440a8 MoveFileExA
0x4440b0 FreeLibrary
0x4440b8 Sleep
0x4440c0 GetProcAddress
0x4440c8 LoadLibraryA
0x4440d0 GetVersion
0x4440d8 WaitForSingleObject
0x4440e0 SetEvent
0x4440e8 TerminateThread
0x4440f0 CreateEventA
0x4440f8 GetLastError
0x444100 GetModuleHandleA
0x444108 CloseHandle
0x444110 CreateMutexA
0x444118 ReleaseMutex
0x444120 CreateThread
0x444128 SetEnvironmentVariableA
0x444130 GlobalFree
0x444138 DeleteFileA
0x444140 InitializeCriticalSection
0x444148 LeaveCriticalSection
0x444150 SetStdHandle
0x444158 DeleteCriticalSection
0x444160 GetExitCodeProcess
0x444168 CreateProcessA
0x444170 GetCurrentDirectoryA
0x444178 lstrlenA
0x444180 FormatMessageA
0x444188 GetShortPathNameA
0x444190 SetCurrentDirectoryA
0x444198 LocalAlloc
0x4441a0 GetVersionExA
0x4441a8 LocalFree
0x4441b0 GetEnvironmentStringsW
0x4441b8 FreeEnvironmentStringsW
0x4441c0 GetEnvironmentStrings
0x4441c8 FreeEnvironmentStringsA
0x4441d0 SetFilePointer
0x4441d8 HeapSize
0x4441e0 ReadFile
0x4441e8 FlushFileBuffers
0x4441f0 GetConsoleMode
0x4441f8 GetConsoleCP
0x444200 GetStartupInfoA
0x444208 GetFileType
0x444210 SetHandleCount
0x444218 GetOEMCP
0x444220 GetACP
0x444228 GetCPInfo
0x444230 FlsAlloc
0x444238 TlsSetValue
0x444240 SetLastError
0x444248 FlsFree
0x444250 TlsFree
0x444258 FlsSetValue
0x444260 WriteConsoleA
0x444268 GetConsoleOutputCP
0x444270 WriteConsoleW
0x444278 CreateFileA
0x444280 CompareStringA
0x444288 CompareStringW
0x444290 SetEndOfFile
0x444298 EnterCriticalSection
0x4442a0 RaiseException
0x4442a8 HeapFree
0x4442b0 HeapAlloc
0x4442b8 FileTimeToSystemTime
0x4442c0 FileTimeToLocalFileTime
0x4442c8 FindFirstFileA
0x4442d0 FindNextFileA
0x4442d8 FindClose
0x4442e0 MoveFileA
0x4442e8 ExitProcess
0x4442f0 GetCurrentProcess
0x4442f8 GetDateFormatA
0x444300 GetTimeFormatA
0x444308 GetDriveTypeA
0x444310 GetFullPathNameA
0x444318 GetTimeZoneInformation
0x444320 GetSystemTimeAsFileTime
0x444328 ExitThread
0x444330 GetCurrentThreadId
0x444338 MultiByteToWideChar
0x444340 WideCharToMultiByte
0x444348 GetFileAttributesA
0x444350 CreateDirectoryA
0x444358 RemoveDirectoryA
0x444360 GetCommandLineA
0x444368 GetProcessHeap
0x444370 HeapSetInformation
0x444378 HeapCreate
0x444380 WriteFile
0x444388 GetStdHandle
0x444390 GetModuleFileNameA
0x444398 RtlUnwindEx
0x4443a0 TerminateProcess
0x4443a8 UnhandledExceptionFilter
0x4443b0 SetUnhandledExceptionFilter
0x4443b8 IsDebuggerPresent
0x4443c0 RtlCaptureContext
0x4443c8 FlsGetValue
USER32.dll
0x4443d8 SetTimer
0x4443e0 GetWindowRect
0x4443e8 KillTimer
0x4443f0 SetWindowPos
0x4443f8 GetDesktopWindow
0x444400 DestroyWindow
0x444408 GetMessageA
0x444410 GetWindowLongPtrA
0x444418 PostThreadMessageA
0x444420 MonitorFromPoint
0x444428 LoadIconA
0x444430 SendMessageA
0x444438 GetMonitorInfoA
0x444440 TranslateMessage
0x444448 CreateWindowExA
0x444450 PeekMessageA
0x444458 DefWindowProcA
0x444460 GetCursorPos
0x444468 ShowWindow
0x444470 SetWindowLongPtrA
0x444478 DispatchMessageA
0x444480 SystemParametersInfoA
0x444488 LoadCursorA
0x444490 ValidateRect
0x444498 RegisterClassA
ADVAPI32.dll
0x444000 GetExplicitEntriesFromAclA
0x444008 GetNamedSecurityInfoA
0x444010 GetUserNameA
0x444018 EqualSid
0x444020 ConvertStringSidToSidA
0x444028 SetNamedSecurityInfoA
0x444030 SetEntriesInAclA
EAT(Export Address Table) is none
WINMM.dll
0x444558 timeGetTime
WININET.dll
0x4444f0 InternetQueryOptionA
0x4444f8 InternetCloseHandle
0x444500 InternetOpenA
0x444508 HttpSendRequestA
0x444510 InternetErrorDlg
0x444518 HttpOpenRequestA
0x444520 InternetSetOptionA
0x444528 InternetReadFile
0x444530 InternetCrackUrlA
0x444538 InternetConnectA
0x444540 InternetOpenUrlA
0x444548 HttpQueryInfoA
VERSION.dll
0x4444a8 GetFileVersionInfoSizeA
0x4444b0 GetFileVersionInfoA
0x4444b8 VerQueryValueA
WINHTTP.dll
0x4444c8 WinHttpGetIEProxyConfigForCurrentUser
0x4444d0 WinHttpCloseHandle
0x4444d8 WinHttpOpen
0x4444e0 WinHttpGetProxyForUrl
COMCTL32.dll
0x444040 InitCommonControlsEx
KERNEL32.dll
0x444050 GetLocaleInfoA
0x444058 GetStringTypeW
0x444060 LCMapStringW
0x444068 LCMapStringA
0x444070 RtlLookupFunctionEntry
0x444078 RtlVirtualUnwind
0x444080 GetCurrentProcessId
0x444088 GetTickCount
0x444090 QueryPerformanceCounter
0x444098 GetStringTypeA
0x4440a0 HeapReAlloc
0x4440a8 MoveFileExA
0x4440b0 FreeLibrary
0x4440b8 Sleep
0x4440c0 GetProcAddress
0x4440c8 LoadLibraryA
0x4440d0 GetVersion
0x4440d8 WaitForSingleObject
0x4440e0 SetEvent
0x4440e8 TerminateThread
0x4440f0 CreateEventA
0x4440f8 GetLastError
0x444100 GetModuleHandleA
0x444108 CloseHandle
0x444110 CreateMutexA
0x444118 ReleaseMutex
0x444120 CreateThread
0x444128 SetEnvironmentVariableA
0x444130 GlobalFree
0x444138 DeleteFileA
0x444140 InitializeCriticalSection
0x444148 LeaveCriticalSection
0x444150 SetStdHandle
0x444158 DeleteCriticalSection
0x444160 GetExitCodeProcess
0x444168 CreateProcessA
0x444170 GetCurrentDirectoryA
0x444178 lstrlenA
0x444180 FormatMessageA
0x444188 GetShortPathNameA
0x444190 SetCurrentDirectoryA
0x444198 LocalAlloc
0x4441a0 GetVersionExA
0x4441a8 LocalFree
0x4441b0 GetEnvironmentStringsW
0x4441b8 FreeEnvironmentStringsW
0x4441c0 GetEnvironmentStrings
0x4441c8 FreeEnvironmentStringsA
0x4441d0 SetFilePointer
0x4441d8 HeapSize
0x4441e0 ReadFile
0x4441e8 FlushFileBuffers
0x4441f0 GetConsoleMode
0x4441f8 GetConsoleCP
0x444200 GetStartupInfoA
0x444208 GetFileType
0x444210 SetHandleCount
0x444218 GetOEMCP
0x444220 GetACP
0x444228 GetCPInfo
0x444230 FlsAlloc
0x444238 TlsSetValue
0x444240 SetLastError
0x444248 FlsFree
0x444250 TlsFree
0x444258 FlsSetValue
0x444260 WriteConsoleA
0x444268 GetConsoleOutputCP
0x444270 WriteConsoleW
0x444278 CreateFileA
0x444280 CompareStringA
0x444288 CompareStringW
0x444290 SetEndOfFile
0x444298 EnterCriticalSection
0x4442a0 RaiseException
0x4442a8 HeapFree
0x4442b0 HeapAlloc
0x4442b8 FileTimeToSystemTime
0x4442c0 FileTimeToLocalFileTime
0x4442c8 FindFirstFileA
0x4442d0 FindNextFileA
0x4442d8 FindClose
0x4442e0 MoveFileA
0x4442e8 ExitProcess
0x4442f0 GetCurrentProcess
0x4442f8 GetDateFormatA
0x444300 GetTimeFormatA
0x444308 GetDriveTypeA
0x444310 GetFullPathNameA
0x444318 GetTimeZoneInformation
0x444320 GetSystemTimeAsFileTime
0x444328 ExitThread
0x444330 GetCurrentThreadId
0x444338 MultiByteToWideChar
0x444340 WideCharToMultiByte
0x444348 GetFileAttributesA
0x444350 CreateDirectoryA
0x444358 RemoveDirectoryA
0x444360 GetCommandLineA
0x444368 GetProcessHeap
0x444370 HeapSetInformation
0x444378 HeapCreate
0x444380 WriteFile
0x444388 GetStdHandle
0x444390 GetModuleFileNameA
0x444398 RtlUnwindEx
0x4443a0 TerminateProcess
0x4443a8 UnhandledExceptionFilter
0x4443b0 SetUnhandledExceptionFilter
0x4443b8 IsDebuggerPresent
0x4443c0 RtlCaptureContext
0x4443c8 FlsGetValue
USER32.dll
0x4443d8 SetTimer
0x4443e0 GetWindowRect
0x4443e8 KillTimer
0x4443f0 SetWindowPos
0x4443f8 GetDesktopWindow
0x444400 DestroyWindow
0x444408 GetMessageA
0x444410 GetWindowLongPtrA
0x444418 PostThreadMessageA
0x444420 MonitorFromPoint
0x444428 LoadIconA
0x444430 SendMessageA
0x444438 GetMonitorInfoA
0x444440 TranslateMessage
0x444448 CreateWindowExA
0x444450 PeekMessageA
0x444458 DefWindowProcA
0x444460 GetCursorPos
0x444468 ShowWindow
0x444470 SetWindowLongPtrA
0x444478 DispatchMessageA
0x444480 SystemParametersInfoA
0x444488 LoadCursorA
0x444490 ValidateRect
0x444498 RegisterClassA
ADVAPI32.dll
0x444000 GetExplicitEntriesFromAclA
0x444008 GetNamedSecurityInfoA
0x444010 GetUserNameA
0x444018 EqualSid
0x444020 ConvertStringSidToSidA
0x444028 SetNamedSecurityInfoA
0x444030 SetEntriesInAclA
EAT(Export Address Table) is none