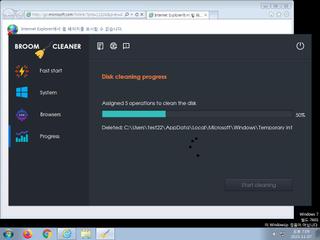
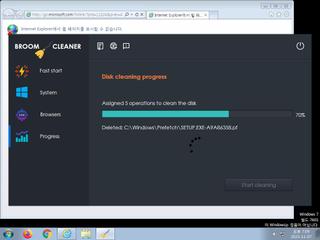
ScreenShot
| Created | 2023.11.07 19:21 | Machine | s1_win7_x6401 |
| Filename | WWW14_64.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | |||
| md5 | b79c2d99b9899e66e9a3c16b5bc407cb | ||
| sha256 | 1f0a1a7674ad868c99421fc13b0457de7ab612ca5948ae7cd045db355720e1fd | ||
| ssdeep | 98304:ch71+dABvnMM6JWksKAzvCC1UpqrC8asFDFc+kQzKQL:ch71+8vnMM6JWksKkUpQD6FerL | ||
| imphash | 46afc61b34fb8e20ac7399f0df86ba31 | ||
| impfuzzy | 6:aZRHmR1A4GVzRgKLbXwNbsOajtlJoZ/OiBJAEnERGDW:KAR1A4GZRgIwxvqTOZGqAJcDW | ||
Network IP location
Signature (47cnts)
| Level | Description |
|---|---|
| danger | Connects to IP addresses that are no longer responding to requests (legitimate services will remain up-and-running usually) |
| danger | Disables Windows Security features |
| danger | Executed a process and injected code into it |
| watch | Allocates execute permission to another process indicative of possible code injection |
| watch | Attempts to identify installed AV products by installation directory |
| watch | Collects information about installed applications |
| watch | Communicates with host for which no DNS query was performed |
| watch | Deletes a large number of files from the system indicative of ransomware |
| watch | Detects Avast Antivirus through the presence of a library |
| watch | Detects VirtualBox through the presence of a file |
| watch | Drops 125 unknown file mime types indicative of ransomware writing encrypted files back to disk |
| watch | Drops a binary and executes it |
| watch | Harvests credentials from local FTP client softwares |
| watch | Network activity contains more than one unique useragent |
| watch | Potential code injection by writing to the memory of another process |
| watch | Resumed a suspended thread in a remote process potentially indicative of process injection |
| watch | Used NtSetContextThread to modify a thread in a remote process indicative of process injection |
| notice | A process created a hidden window |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | An executable file was downloaded by the processes www14_64.exe |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
| notice | Checks adapter addresses which can be used to detect virtual network interfaces |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates executable files on the filesystem |
| notice | Creates hidden or system file |
| notice | Drops an executable to the user AppData folder |
| notice | Expresses interest in specific running processes |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Looks up the external IP address |
| notice | One or more potentially interesting buffers were extracted |
| notice | Performs some HTTP requests |
| notice | Queries for potentially installed applications |
| notice | Queries the disk size which could be used to detect virtual machine with small fixed size or dynamic allocation |
| notice | Searches running processes potentially to identify processes for sandbox evasion |
| notice | Sends data using the HTTP POST Method |
| notice | Steals private information from local Internet browsers |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| notice | Uses Windows utilities for basic Windows functionality |
| notice | Yara rule detected in process memory |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Collects information to fingerprint the system (MachineGuid |
| info | One or more processes crashed |
| info | Queries for the computername |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | Tries to locate where the browsers are installed |
| info | Uses Windows APIs to generate a cryptographic key |
Rules (42cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | HermeticWiper_Zero | HermeticWiper | binaries (download) |
| danger | MALWARE_Win_VT_RedLine | Detects RedLine infostealer | binaries (download) |
| danger | NPKI_Zero | File included NPKI | binaries (download) |
| danger | RedLine_Stealer_b_Zero | RedLine stealer | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | NSIS_Installer | Null Soft Installer | binaries (download) |
| warning | Suspicious_Obfuscation_Script | Suspicious obfuscation script | binaries (download) |
| watch | Admin_Tool_IN_Zero | Admin Tool Sysinternals | binaries (download) |
| watch | Antivirus | Contains references to security software | binaries (download) |
| watch | ConfuserEx_Zero | Confuser .NET | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| watch | Win32_Trojan_PWS_Net_1_Zero | Win32 Trojan PWS .NET Azorult | binaries (download) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (download) |
| notice | Javascript_Blob | use blob(Binary Large Objec) javascript | binaries (download) |
| info | anti_dbg | Checks if being debugged | memory |
| info | bmp_file_format | bmp file format | binaries (download) |
| info | CAB_file_format | CAB archive file | binaries (download) |
| info | DebuggerCheck__GlobalFlags | (no description) | memory |
| info | DebuggerCheck__QueryInfo | (no description) | memory |
| info | DebuggerHiding__Active | (no description) | memory |
| info | DebuggerHiding__Thread | (no description) | memory |
| info | disable_dep | Bypass DEP | memory |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (download) |
| info | icon_file_format | icon file format | binaries (download) |
| info | Is_DotNET_EXE | (no description) | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (download) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | JPEG_Format_Zero | JPEG Format | binaries (download) |
| info | Microsoft_Office_File_Zero | Microsoft Office File | binaries (download) |
| info | mzp_file_format | MZP(Delphi) file format | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | PNG_Format_Zero | PNG Format | binaries (download) |
| info | SEH__vectored | (no description) | memory |
| info | ThreadControl__Context | (no description) | memory |
| info | zip_file_format | ZIP file format | binaries (download) |
Network (68cnts) ?
Suricata ids
ET MALWARE Win32/BeamWinHTTP CnC Activity M2 (GET)
SURICATA Applayer Mismatch protocol both directions
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com)
ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io)
ET MALWARE Single char EXE direct download likely trojan (multiple families)
ET INFO Executable Download from dotted-quad Host
ET INFO Packed Executable Download
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
SURICATA TLS invalid record type
SURICATA TLS invalid record/traffic
ET INFO Microsoft net.tcp Connection Initialization Activity
ET MALWARE [ANY.RUN] RedLine Stealer Related (MC-NMF Authorization)
ET MALWARE Redline Stealer TCP CnC Activity - MSValue (Outbound)
ET MALWARE Redline Stealer TCP CnC Activity
ET MALWARE Redline Stealer TCP CnC - Id1Response
ET MALWARE Redline Stealer Activity (Response)
ET INFO TLS Handshake Failure
ET MALWARE Redline Stealer TCP CnC Activity - MSValue (Response)
ET INFO External IP Lookup Domain (iplogger .com in DNS lookup)
ET INFO External IP Lookup Domain (iplogger .com in TLS SNI)
SURICATA Applayer Mismatch protocol both directions
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET INFO Observed External IP Lookup Domain in TLS SNI (api .myip .com)
ET POLICY Possible External IP Lookup Domain Observed in SNI (ipinfo. io)
ET MALWARE Single char EXE direct download likely trojan (multiple families)
ET INFO Executable Download from dotted-quad Host
ET INFO Packed Executable Download
ET POLICY PE EXE or DLL Windows file download HTTP
ET HUNTING SUSPICIOUS Dotted Quad Host MZ Response
ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)
SURICATA TLS invalid record type
SURICATA TLS invalid record/traffic
ET INFO Microsoft net.tcp Connection Initialization Activity
ET MALWARE [ANY.RUN] RedLine Stealer Related (MC-NMF Authorization)
ET MALWARE Redline Stealer TCP CnC Activity - MSValue (Outbound)
ET MALWARE Redline Stealer TCP CnC Activity
ET MALWARE Redline Stealer TCP CnC - Id1Response
ET MALWARE Redline Stealer Activity (Response)
ET INFO TLS Handshake Failure
ET MALWARE Redline Stealer TCP CnC Activity - MSValue (Response)
ET INFO External IP Lookup Domain (iplogger .com in DNS lookup)
ET INFO External IP Lookup Domain (iplogger .com in TLS SNI)
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x14057b000 InitializeCriticalSectionEx
USER32.dll
0x14057b010 CharNextA
ADVAPI32.dll
0x14057b020 RegCloseKey
SHELL32.dll
0x14057b030 ShellExecuteA
ole32.dll
0x14057b040 CoCreateInstance
KERNEL32.dll
0x14057b050 GetSystemTimeAsFileTime
KERNEL32.dll
0x14057b060 HeapAlloc
0x14057b068 HeapFree
0x14057b070 ExitProcess
0x14057b078 LoadLibraryA
0x14057b080 GetModuleHandleA
0x14057b088 GetProcAddress
EAT(Export Address Table) is none
KERNEL32.dll
0x14057b000 InitializeCriticalSectionEx
USER32.dll
0x14057b010 CharNextA
ADVAPI32.dll
0x14057b020 RegCloseKey
SHELL32.dll
0x14057b030 ShellExecuteA
ole32.dll
0x14057b040 CoCreateInstance
KERNEL32.dll
0x14057b050 GetSystemTimeAsFileTime
KERNEL32.dll
0x14057b060 HeapAlloc
0x14057b068 HeapFree
0x14057b070 ExitProcess
0x14057b078 LoadLibraryA
0x14057b080 GetModuleHandleA
0x14057b088 GetProcAddress
EAT(Export Address Table) is none