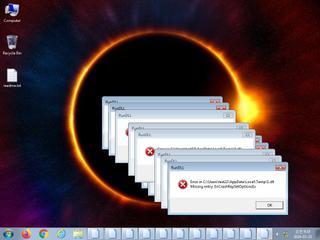
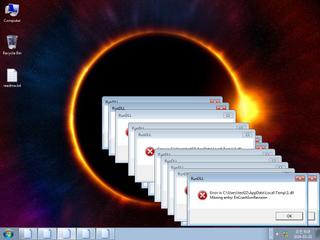
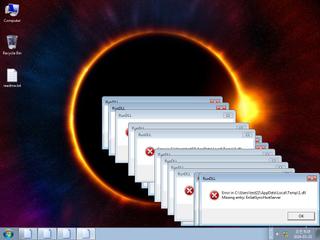
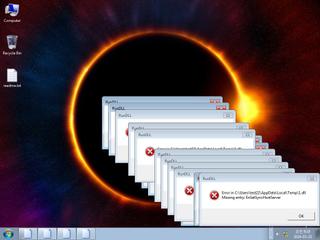
ScreenShot
| Created | 2024.03.25 09:22 | Machine | s1_win7_x6403 |
| Filename | 1.dll | ||
| Type | PE32 executable (DLL) (console) Intel 80386 (stripped to external PDB), for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 40 detected (Malicious, score, DeepScan, Marte, unsafe, Vy7j, confidence, 100%, Attribute, HighConfidence, DropperX, Cobalt, CobaltStrike, CLOUD, Swrort, njwxa, Detected, ai score=89, ABRisk, QHEN, GdSda, R002H01CL24, Gkjl, PossibleThreat) | ||
| md5 | aa7554fb38eb05288f7a74735999e920 | ||
| sha256 | 96cf74926856e25b18f6c12c13e8093200a0b89db345ad0511c77659d0d25f1f | ||
| ssdeep | 192:T8Ueko0awm9s2yHvWXomicRHwjfqgGou:gbk2yPW4A+f9P | ||
| imphash | e9e98df639c35c794fd44c3163bacf7b | ||
| impfuzzy | 6:9mRxybmRxVrOi5XtE0ZRHmRx9ujGMK9T7mRx8Jt0yRlbmAhHGVIV5GGCJvuqBYq9:YRJR+iJ2oAR7l9qRNqRmiRC91Kq0iZn | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 40 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | One or more processes crashed |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x649070ac DeleteCriticalSection
0x649070b0 EnterCriticalSection
0x649070b4 GetCurrentProcess
0x649070b8 GetLastError
0x649070bc GetModuleHandleA
0x649070c0 InitializeCriticalSection
0x649070c4 K32GetModuleInformation
0x649070c8 LeaveCriticalSection
0x649070cc Sleep
0x649070d0 TlsGetValue
0x649070d4 VirtualProtect
0x649070d8 VirtualQuery
0x649070dc WriteProcessMemory
msvcrt.dll
0x649070e4 _amsg_exit
0x649070e8 _initterm
0x649070ec _iob
0x649070f0 _lock
0x649070f4 _unlock
0x649070f8 abort
0x649070fc calloc
0x64907100 free
0x64907104 fwrite
0x64907108 realloc
0x6490710c strlen
0x64907110 strncmp
0x64907114 vfprintf
EAT(Export Address Table) Library
0x649060d7 EnAPMDataRepSubmitReport
0x64906117 EnAnrDumpRepExceptionFilter
0x6490615d EnAnrDumpRepSubmitReport
0x6490619d EnCrashRepClearInfo
0x649061d3 EnCrashRepCreateDumpFile
0x64906213 EnCrashRepCreateStackFile
0x64906255 EnCrashRepExceptionFilter
0x64906297 EnCrashRepSetDeviceId
0x649062d1 EnCrashRepSetInfo
0x64906303 EnCrashRepSetOptions
0x6490633b EnCrashRepSetOptionsEx
0x64906377 EnCrashRepSubmitReport
0x649063b3 EnCrashRepSubmitReportEx
0x649063f3 EnCrashSvnRevision
0x64906427 EnGetAnrDumpFileName
0x6490645f EnSetSyncHostServer
KERNEL32.dll
0x649070ac DeleteCriticalSection
0x649070b0 EnterCriticalSection
0x649070b4 GetCurrentProcess
0x649070b8 GetLastError
0x649070bc GetModuleHandleA
0x649070c0 InitializeCriticalSection
0x649070c4 K32GetModuleInformation
0x649070c8 LeaveCriticalSection
0x649070cc Sleep
0x649070d0 TlsGetValue
0x649070d4 VirtualProtect
0x649070d8 VirtualQuery
0x649070dc WriteProcessMemory
msvcrt.dll
0x649070e4 _amsg_exit
0x649070e8 _initterm
0x649070ec _iob
0x649070f0 _lock
0x649070f4 _unlock
0x649070f8 abort
0x649070fc calloc
0x64907100 free
0x64907104 fwrite
0x64907108 realloc
0x6490710c strlen
0x64907110 strncmp
0x64907114 vfprintf
EAT(Export Address Table) Library
0x649060d7 EnAPMDataRepSubmitReport
0x64906117 EnAnrDumpRepExceptionFilter
0x6490615d EnAnrDumpRepSubmitReport
0x6490619d EnCrashRepClearInfo
0x649061d3 EnCrashRepCreateDumpFile
0x64906213 EnCrashRepCreateStackFile
0x64906255 EnCrashRepExceptionFilter
0x64906297 EnCrashRepSetDeviceId
0x649062d1 EnCrashRepSetInfo
0x64906303 EnCrashRepSetOptions
0x6490633b EnCrashRepSetOptionsEx
0x64906377 EnCrashRepSubmitReport
0x649063b3 EnCrashRepSubmitReportEx
0x649063f3 EnCrashSvnRevision
0x64906427 EnGetAnrDumpFileName
0x6490645f EnSetSyncHostServer