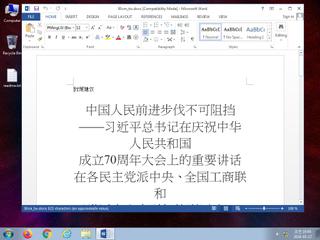
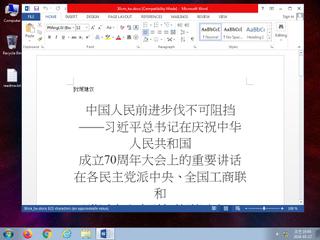
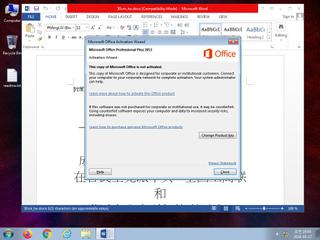
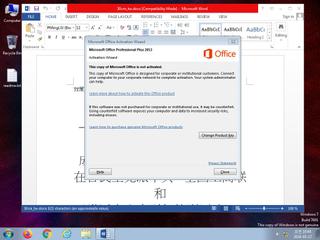
ScreenShot
| Created | 2024.05.17 10:46 | Machine | s1_win7_x6403 |
| Filename | %E4%BA%BA%E6%B0%91%E5%BA%86%E7%A5%9D%E5%AF%B9%E7%AD%96_PRC_Celebration_Renc%E2%80%AExcod.scr | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 48 detected (AIDetectMalware, Malicious, score, unsafe, Save, GenericKD, Attribute, HighConfidence, high confidence, ABES, jtlkkr, CLOUD, pdnbq, gljn, Ransomware, Ryuk, Detected, ai score=83, Ymacco, ABRisk, YGLG, ZexaF, Z@aSVErii, Floxif, FileInfector, GdSda, R002H0CEG24, Wimw, 2BEcW8y4m5U, Static AI, Malicious PE) | ||
| md5 | d60e2ed8f4d8add3b76df293875e34f9 | ||
| sha256 | d63cad89ffa803ee8bfa33c369dc5774822902597dc794f4cf31daada1a4f6a2 | ||
| ssdeep | 24576:lztyT2/n278bXIIt+53b7HVN1+ks7TWtyCRRe9cVzLB3suQ5Y3h3H:572bN1Ds7TWtyCRjB3T | ||
| imphash | bf021d909ed6651e5b77c6b4d3a2e83c | ||
| impfuzzy | 48:DNfiK1M+k02Hjj4JGhY8pzFJl61vm/Gibqgsu6T:DNfiK1Mr02Hjj4JGhXBzlMYbqgszT | ||
Network IP location
Signature (16cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 48 AntiVirus engines on VirusTotal as malicious |
| watch | Harvests credentials from local email clients |
| watch | Installs itself for autorun at Windows startup |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | An application raised an exception which may be indicative of an exploit crash |
| notice | Changes read-write memory protection to read-execute (probably to avoid detection when setting all RWX flags at the same time) |
| notice | Creates (office) documents on the filesystem |
| notice | Creates hidden or system file |
| notice | Drops a binary and executes it |
| notice | Queries for potentially installed applications |
| info | Checks amount of memory in system |
| info | Checks if process is being debugged by a debugger |
| info | Collects information to fingerprint the system (MachineGuid |
| info | One or more processes crashed |
| info | Tries to locate where the browsers are installed |
| info | Uses Windows APIs to generate a cryptographic key |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | docx | Word 2007 file format detection | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
| info | zip_file_format | ZIP file format | binaries (download) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
ADVAPI32.dll
0x4e8258 RegCreateKeyExA
0x4e825c RegSetValueExA
KERNEL32.dll
0x4e8264 CloseHandle
0x4e8268 CreateSemaphoreW
0x4e826c DeleteCriticalSection
0x4e8270 EnterCriticalSection
0x4e8274 FreeLibrary
0x4e8278 GetCurrentProcess
0x4e827c GetCurrentProcessId
0x4e8280 GetCurrentThreadId
0x4e8284 GetLastError
0x4e8288 GetModuleFileNameA
0x4e828c GetModuleHandleA
0x4e8290 GetModuleHandleW
0x4e8294 GetProcAddress
0x4e8298 GetStartupInfoA
0x4e829c GetSystemTimeAsFileTime
0x4e82a0 GetTempPathA
0x4e82a4 GetTickCount
0x4e82a8 InitializeCriticalSection
0x4e82ac IsDBCSLeadByteEx
0x4e82b0 LeaveCriticalSection
0x4e82b4 LoadLibraryA
0x4e82b8 MultiByteToWideChar
0x4e82bc QueryPerformanceCounter
0x4e82c0 ReleaseSemaphore
0x4e82c4 SetLastError
0x4e82c8 SetUnhandledExceptionFilter
0x4e82cc Sleep
0x4e82d0 TerminateProcess
0x4e82d4 TlsAlloc
0x4e82d8 TlsFree
0x4e82dc TlsGetValue
0x4e82e0 TlsSetValue
0x4e82e4 UnhandledExceptionFilter
0x4e82e8 VirtualProtect
0x4e82ec VirtualQuery
0x4e82f0 WaitForSingleObject
0x4e82f4 WideCharToMultiByte
msvcrt.dll
0x4e82fc __dllonexit
0x4e8300 __doserrno
0x4e8304 __getmainargs
0x4e8308 __initenv
0x4e830c __lconv_init
0x4e8310 __mb_cur_max
0x4e8314 __pioinfo
0x4e8318 __set_app_type
0x4e831c __setusermatherr
0x4e8320 _acmdln
0x4e8324 _amsg_exit
0x4e8328 _cexit
0x4e832c _errno
0x4e8330 _fdopen
0x4e8334 _filelengthi64
0x4e8338 _fileno
0x4e833c _fileno
0x4e8340 _fmode
0x4e8344 _fstat64
0x4e8348 _initterm
0x4e834c _iob
0x4e8350 _lock
0x4e8354 _lseeki64
0x4e8358 _onexit
0x4e835c _read
0x4e8360 _strnicmp
0x4e8364 _unlock
0x4e8368 _write
0x4e836c _write
0x4e8370 abort
0x4e8374 atoi
0x4e8378 calloc
0x4e837c exit
0x4e8380 fclose
0x4e8384 fflush
0x4e8388 fgetpos
0x4e838c fopen
0x4e8390 fprintf
0x4e8394 fputc
0x4e8398 fputs
0x4e839c fread
0x4e83a0 free
0x4e83a4 fsetpos
0x4e83a8 fwrite
0x4e83ac getc
0x4e83b0 getenv
0x4e83b4 getwc
0x4e83b8 isspace
0x4e83bc iswctype
0x4e83c0 localeconv
0x4e83c4 malloc
0x4e83c8 memchr
0x4e83cc memcmp
0x4e83d0 memcpy
0x4e83d4 memmove
0x4e83d8 memset
0x4e83dc putc
0x4e83e0 putwc
0x4e83e4 realloc
0x4e83e8 setlocale
0x4e83ec setvbuf
0x4e83f0 signal
0x4e83f4 sprintf
0x4e83f8 strchr
0x4e83fc strcmp
0x4e8400 strcoll
0x4e8404 strerror
0x4e8408 strftime
0x4e840c strlen
0x4e8410 strncmp
0x4e8414 strtoul
0x4e8418 strxfrm
0x4e841c towlower
0x4e8420 towupper
0x4e8424 ungetc
0x4e8428 ungetwc
0x4e842c vfprintf
0x4e8430 wcscoll
0x4e8434 wcsftime
0x4e8438 wcslen
0x4e843c wcsxfrm
SHELL32.dll
0x4e8444 ShellExecuteA
EAT(Export Address Table) is none
ADVAPI32.dll
0x4e8258 RegCreateKeyExA
0x4e825c RegSetValueExA
KERNEL32.dll
0x4e8264 CloseHandle
0x4e8268 CreateSemaphoreW
0x4e826c DeleteCriticalSection
0x4e8270 EnterCriticalSection
0x4e8274 FreeLibrary
0x4e8278 GetCurrentProcess
0x4e827c GetCurrentProcessId
0x4e8280 GetCurrentThreadId
0x4e8284 GetLastError
0x4e8288 GetModuleFileNameA
0x4e828c GetModuleHandleA
0x4e8290 GetModuleHandleW
0x4e8294 GetProcAddress
0x4e8298 GetStartupInfoA
0x4e829c GetSystemTimeAsFileTime
0x4e82a0 GetTempPathA
0x4e82a4 GetTickCount
0x4e82a8 InitializeCriticalSection
0x4e82ac IsDBCSLeadByteEx
0x4e82b0 LeaveCriticalSection
0x4e82b4 LoadLibraryA
0x4e82b8 MultiByteToWideChar
0x4e82bc QueryPerformanceCounter
0x4e82c0 ReleaseSemaphore
0x4e82c4 SetLastError
0x4e82c8 SetUnhandledExceptionFilter
0x4e82cc Sleep
0x4e82d0 TerminateProcess
0x4e82d4 TlsAlloc
0x4e82d8 TlsFree
0x4e82dc TlsGetValue
0x4e82e0 TlsSetValue
0x4e82e4 UnhandledExceptionFilter
0x4e82e8 VirtualProtect
0x4e82ec VirtualQuery
0x4e82f0 WaitForSingleObject
0x4e82f4 WideCharToMultiByte
msvcrt.dll
0x4e82fc __dllonexit
0x4e8300 __doserrno
0x4e8304 __getmainargs
0x4e8308 __initenv
0x4e830c __lconv_init
0x4e8310 __mb_cur_max
0x4e8314 __pioinfo
0x4e8318 __set_app_type
0x4e831c __setusermatherr
0x4e8320 _acmdln
0x4e8324 _amsg_exit
0x4e8328 _cexit
0x4e832c _errno
0x4e8330 _fdopen
0x4e8334 _filelengthi64
0x4e8338 _fileno
0x4e833c _fileno
0x4e8340 _fmode
0x4e8344 _fstat64
0x4e8348 _initterm
0x4e834c _iob
0x4e8350 _lock
0x4e8354 _lseeki64
0x4e8358 _onexit
0x4e835c _read
0x4e8360 _strnicmp
0x4e8364 _unlock
0x4e8368 _write
0x4e836c _write
0x4e8370 abort
0x4e8374 atoi
0x4e8378 calloc
0x4e837c exit
0x4e8380 fclose
0x4e8384 fflush
0x4e8388 fgetpos
0x4e838c fopen
0x4e8390 fprintf
0x4e8394 fputc
0x4e8398 fputs
0x4e839c fread
0x4e83a0 free
0x4e83a4 fsetpos
0x4e83a8 fwrite
0x4e83ac getc
0x4e83b0 getenv
0x4e83b4 getwc
0x4e83b8 isspace
0x4e83bc iswctype
0x4e83c0 localeconv
0x4e83c4 malloc
0x4e83c8 memchr
0x4e83cc memcmp
0x4e83d0 memcpy
0x4e83d4 memmove
0x4e83d8 memset
0x4e83dc putc
0x4e83e0 putwc
0x4e83e4 realloc
0x4e83e8 setlocale
0x4e83ec setvbuf
0x4e83f0 signal
0x4e83f4 sprintf
0x4e83f8 strchr
0x4e83fc strcmp
0x4e8400 strcoll
0x4e8404 strerror
0x4e8408 strftime
0x4e840c strlen
0x4e8410 strncmp
0x4e8414 strtoul
0x4e8418 strxfrm
0x4e841c towlower
0x4e8420 towupper
0x4e8424 ungetc
0x4e8428 ungetwc
0x4e842c vfprintf
0x4e8430 wcscoll
0x4e8434 wcsftime
0x4e8438 wcslen
0x4e843c wcsxfrm
SHELL32.dll
0x4e8444 ShellExecuteA
EAT(Export Address Table) is none