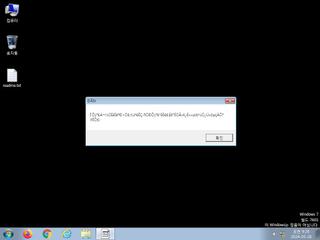
ScreenShot
| Created | 2024.05.28 09:54 | Machine | s1_win7_x6401 |
| Filename | s.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 51 detected (AIDetectMalware, Scar, mip4, malicious, high confidence, score, Trojanpws, Qqpass, Fragtor, unsafe, Save, BlackMoon, Attribute, HighConfidence, A suspicious, Artemis, Tiggre, GenericML, xnet, R002C0WEM24, high, Detected, ai score=84, Blamon, HeurC, KVMH012, Sabsik, 1DPEYYJ, Eldorado, ZexaF, fnW@aqHJFXd, BScope, Chgt, Static AI, Malicious PE, susgen, confidence) | ||
| md5 | bc6d39d7372c8f38fcc60cf3ce2a48f1 | ||
| sha256 | e16d917f8e8f1cc779afeb88129d77640500689fc746685e3f98db725f40a1cf | ||
| ssdeep | 24576:MD+Fbw9dZB0mq9oscc2V+ZFSJ9P7NWm9x8zqXdWoPLuRWgMybwX:MD+Fbw9dPylGB2RWgMybw | ||
| imphash | 581943411ae1f1dda1b12d4641ef7036 | ||
| impfuzzy | 192:T00BfLmiJPgUb7JgE1jQLHWDuIT9QIUB52XDe1CW9fWcnc1PhXtA52Hr8k+ULx:T00BfdRV7JD1jQW9pze4RaSPhXaIHr5r | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 51 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | Checks amount of memory in system |
| info | One or more processes crashed |
Rules (8cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | Network_Downloader | File Downloader | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
WINMM.dll
0x4b8324 PlaySoundA
KERNEL32.dll
0x4b804c FindFirstFileW
0x4b8050 FindClose
0x4b8054 VirtualQueryEx
0x4b8058 lstrcpynA
0x4b805c CreateThread
0x4b8060 CreateWaitableTimerA
0x4b8064 SetWaitableTimer
0x4b8068 lstrcpyn
0x4b806c GetModuleHandleA
0x4b8070 VirtualAlloc
0x4b8074 VirtualFree
0x4b8078 LoadLibraryA
0x4b807c GetProcAddress
0x4b8080 CreateFileA
0x4b8084 ResetEvent
0x4b8088 WriteFile
0x4b808c CancelIo
0x4b8090 ReadFile
0x4b8094 GetProcessHeap
0x4b8098 ExitProcess
0x4b809c HeapAlloc
0x4b80a0 HeapReAlloc
0x4b80a4 HeapFree
0x4b80a8 IsBadReadPtr
0x4b80ac DeleteFileA
0x4b80b0 GetModuleFileNameA
0x4b80b4 Sleep
0x4b80b8 GetUserDefaultLCID
0x4b80bc GlobalUnlock
0x4b80c0 GetTickCount
0x4b80c4 SetFileAttributesA
0x4b80c8 GetPrivateProfileStringA
0x4b80cc LCMapStringA
0x4b80d0 GetCommandLineA
0x4b80d4 FreeLibrary
0x4b80d8 EnterCriticalSection
0x4b80dc LeaveCriticalSection
0x4b80e0 GetTempPathA
0x4b80e4 GetFileAttributesA
0x4b80e8 RtlMoveMemory
0x4b80ec GlobalLock
0x4b80f0 GetSystemDirectoryA
0x4b80f4 InitializeCriticalSection
0x4b80f8 GetWindowsDirectoryA
0x4b80fc FileTimeToSystemTime
0x4b8100 FileTimeToLocalFileTime
0x4b8104 SetFilePointer
0x4b8108 UnmapViewOfFile
0x4b810c SystemTimeToFileTime
0x4b8110 GetCurrentDirectoryA
0x4b8114 LocalFileTimeToFileTime
0x4b8118 CreateDirectoryA
0x4b811c GlobalAlloc
0x4b8120 WideCharToMultiByte
0x4b8124 lstrlenW
0x4b8128 GetCurrentDirectoryW
0x4b812c WaitForSingleObject
0x4b8130 MultiByteToWideChar
0x4b8134 LocalFree
0x4b8138 LocalAlloc
0x4b813c TerminateProcess
0x4b8140 OpenProcess
0x4b8144 GetCurrentProcess
0x4b8148 GetCurrentProcessId
0x4b814c CloseHandle
0x4b8150 Process32Next
0x4b8154 Process32First
0x4b8158 CreateToolhelp32Snapshot
0x4b815c CreateEventA
0x4b8160 OpenEventA
0x4b8164 DeleteCriticalSection
0x4b8168 GetFileSize
0x4b816c SetFileTime
ole32.dll
0x4b8558 CLSIDFromString
0x4b855c OleRun
0x4b8560 CoCreateInstance
0x4b8564 CLSIDFromProgID
0x4b8568 CLSIDFromString
0x4b856c OleFlushClipboard
0x4b8570 CoInitialize
0x4b8574 OleInitialize
0x4b8578 OleIsCurrentClipboard
0x4b857c OleUninitialize
0x4b8580 CoRevokeClassObject
0x4b8584 CoRegisterMessageFilter
0x4b8588 CoInitialize
0x4b858c CoUninitialize
0x4b8590 OleRun
0x4b8594 CoFreeUnusedLibraries
0x4b8598 CoCreateInstance
0x4b859c CLSIDFromProgID
0x4b85a0 CoUninitialize
USER32.dll
0x4b8274 GetDC
0x4b8278 ReleaseDC
0x4b827c OpenClipboard
0x4b8280 EmptyClipboard
0x4b8284 CloseClipboard
0x4b8288 GetForegroundWindow
0x4b828c UnhookWindowsHookEx
0x4b8290 GetCursorInfo
0x4b8294 GetIconInfo
0x4b8298 DrawIcon
0x4b829c MsgWaitForMultipleObjects
0x4b82a0 SendInput
0x4b82a4 SetWindowsHookExA
0x4b82a8 SetClipboardData
0x4b82ac GetCursorPos
0x4b82b0 PeekMessageA
0x4b82b4 GetSystemMetrics
0x4b82b8 wsprintfA
0x4b82bc MessageBoxA
0x4b82c0 DispatchMessageA
0x4b82c4 TranslateMessage
0x4b82c8 GetMessageA
0x4b82cc SetTimer
0x4b82d0 MessageBoxTimeoutA
0x4b82d4 CallNextHookEx
ADVAPI32.dll
0x4b8000 OpenProcessToken
0x4b8004 AllocateAndInitializeSid
0x4b8008 GetTokenInformation
0x4b800c EqualSid
0x4b8010 FreeSid
GDI32.dll
0x4b8018 GetDeviceCaps
0x4b801c CreateCompatibleDC
0x4b8020 CreateDIBSection
0x4b8024 SelectObject
0x4b8028 BitBlt
0x4b802c GetDIBits
0x4b8030 GetDIBColorTable
0x4b8034 StretchBlt
0x4b8038 GetBitmapBits
0x4b803c DeleteObject
0x4b8040 CreateCompatibleBitmap
0x4b8044 DeleteDC
OLEAUT32.dll
0x4b81e8 VariantInit
0x4b81ec SafeArrayAllocDescriptor
0x4b81f0 SafeArrayAllocData
0x4b81f4 SafeArrayGetDim
0x4b81f8 SafeArrayGetLBound
0x4b81fc SafeArrayGetUBound
0x4b8200 SafeArrayAccessData
0x4b8204 SafeArrayUnaccessData
0x4b8208 SafeArrayGetElemsize
0x4b820c SysFreeString
0x4b8210 VarR8FromCy
0x4b8214 VarR8FromBool
0x4b8218 VariantChangeType
0x4b821c LoadTypeLib
0x4b8220 LHashValOfNameSys
0x4b8224 RegisterTypeLib
0x4b8228 VariantCopy
0x4b822c SafeArrayCreate
0x4b8230 SysAllocString
0x4b8234 VariantClear
0x4b8238 SafeArrayDestroy
0x4b823c SystemTimeToVariantTime
SHELL32.dll
0x4b8258 ShellExecuteA
0x4b825c SHGetSpecialFolderPathA
0x4b8260 ShellExecuteExW
WINHTTP.dll
0x4b82dc WinHttpCrackUrl
0x4b82e0 WinHttpOpen
0x4b82e4 WinHttpSetTimeouts
0x4b82e8 WinHttpConnect
0x4b82ec WinHttpOpenRequest
0x4b82f0 WinHttpQueryHeaders
0x4b82f4 WinHttpSetCredentials
0x4b82f8 WinHttpCloseHandle
0x4b82fc WinHttpSetOption
0x4b8300 WinHttpAddRequestHeaders
0x4b8304 WinHttpSendRequest
0x4b8308 WinHttpReceiveResponse
0x4b830c WinHttpQueryDataAvailable
0x4b8310 WinHttpReadData
0x4b8314 WinHttpCheckPlatform
WININET.dll
0x4b831c DeleteUrlCacheEntry
urlmon.dll
0x4b8610 URLDownloadToFileA
SHLWAPI.dll
0x4b8268 PathFindExtensionA
0x4b826c PathFileExistsA
SETUPAPI.dll
0x4b8244 SetupDiGetClassDevsA
0x4b8248 SetupDiGetDeviceInterfaceDetailA
0x4b824c SetupDiDestroyDeviceInfoList
0x4b8250 SetupDiEnumDeviceInterfaces
user32.dll
0x4b8618 MessageBoxA
0x4b861c GetWindowRect
0x4b8620 WindowFromPoint
0x4b8624 CallWindowProcA
0x4b8628 GetWindow
0x4b862c SendMessageTimeoutA
0x4b8630 wsprintfA
0x4b8634 DispatchMessageA
0x4b8638 TranslateMessage
0x4b863c RegisterWindowMessageA
0x4b8640 GetMessageA
0x4b8644 PeekMessageA
0x4b8648 GetCursorPos
0x4b864c GetClassNameA
0x4b8650 EnumChildWindows
0x4b8654 SetFocus
0x4b8658 GetSystemMetrics
0x4b865c GetWindowPlacement
0x4b8660 IsIconic
0x4b8664 SystemParametersInfoA
0x4b8668 SetForegroundWindow
0x4b866c GetForegroundWindow
0x4b8670 GetMessagePos
0x4b8674 GetMessageTime
0x4b8678 DefWindowProcA
0x4b867c RemovePropA
0x4b8680 GetPropA
0x4b8684 SetPropA
0x4b8688 GetClassLongA
0x4b868c CreateWindowExA
0x4b8690 DestroyWindow
0x4b8694 GetMenuItemID
0x4b8698 GetMenuCheckMarkDimensions
0x4b869c GetMenu
0x4b86a0 RegisterClassA
0x4b86a4 GetClassInfoA
0x4b86a8 WinHelpA
0x4b86ac GetCapture
0x4b86b0 GetTopWindow
0x4b86b4 PostQuitMessage
0x4b86b8 PostMessageA
0x4b86bc SendMessageA
0x4b86c0 SetCursor
0x4b86c4 EnableWindow
0x4b86c8 GetWindowLongA
0x4b86cc IsWindowEnabled
0x4b86d0 GetLastActivePopup
0x4b86d4 GetParent
0x4b86d8 SetWindowsHookExA
0x4b86dc IsWindowVisible
0x4b86e0 ValidateRect
0x4b86e4 CallNextHookEx
0x4b86e8 GetKeyState
0x4b86ec GetActiveWindow
0x4b86f0 GetNextDlgTabItem
0x4b86f4 GetFocus
0x4b86f8 EnableMenuItem
0x4b86fc CheckMenuItem
0x4b8700 SetMenuItemBitmaps
0x4b8704 ModifyMenuA
0x4b8708 GetMenuState
0x4b870c LoadBitmapA
0x4b8710 RegisterClipboardFormatA
0x4b8714 UnhookWindowsHookEx
0x4b8718 UnregisterClassA
0x4b871c PtInRect
0x4b8720 ClientToScreen
0x4b8724 SetWindowTextA
0x4b8728 GetWindowTextA
0x4b872c GetMenuItemCount
0x4b8730 GetDC
0x4b8734 ReleaseDC
0x4b8738 TabbedTextOutA
0x4b873c DrawTextA
0x4b8740 GrayStringA
0x4b8744 GetDlgItem
0x4b8748 EndDialog
0x4b874c CreateDialogIndirectParamA
0x4b8750 DestroyMenu
0x4b8754 PostThreadMessageA
0x4b8758 LoadStringA
0x4b875c GetSysColorBrush
0x4b8760 LoadCursorA
0x4b8764 LoadIconA
0x4b8768 UpdateWindow
0x4b876c MapWindowPoints
0x4b8770 GetSysColor
0x4b8774 SetActiveWindow
0x4b8778 IsWindow
0x4b877c AdjustWindowRectEx
0x4b8780 GetClientRect
0x4b8784 CopyRect
0x4b8788 ShowWindow
0x4b878c GetSubMenu
0x4b8790 SendDlgItemMessageA
0x4b8794 IsDialogMessageA
0x4b8798 SetWindowLongA
0x4b879c SetWindowPos
0x4b87a0 GetDlgCtrlID
kernel32.dll
0x4b83d0 GlobalAlloc
0x4b83d4 GlobalLock
0x4b83d8 GlobalUnlock
0x4b83dc GlobalFree
0x4b83e0 GetUserDefaultLCID
0x4b83e4 IsBadReadPtr
0x4b83e8 HeapFree
0x4b83ec HeapReAlloc
0x4b83f0 HeapAlloc
0x4b83f4 ExitProcess
0x4b83f8 GetProcessHeap
0x4b83fc WriteProcessMemory
0x4b8400 GetProcAddress
0x4b8404 LoadLibraryA
0x4b8408 lstrcpyn
0x4b840c lstrcatA
0x4b8410 SetHandleCount
0x4b8414 GetStringTypeW
0x4b8418 IsBadCodePtr
0x4b841c SetStdHandle
0x4b8420 FreeEnvironmentStringsW
0x4b8424 FreeEnvironmentStringsA
0x4b8428 GetStartupInfoA
0x4b842c GetFileType
0x4b8430 GetModuleHandleA
0x4b8434 GetStdHandle
0x4b8438 GetACP
0x4b843c HeapSize
0x4b8440 RaiseException
0x4b8444 TerminateProcess
0x4b8448 RtlUnwind
0x4b844c GetCommandLineA
0x4b8450 GetOEMCP
0x4b8454 GetCPInfo
0x4b8458 FlushFileBuffers
0x4b845c SetFilePointer
0x4b8460 WriteFile
0x4b8464 GetCurrentProcess
0x4b8468 GetProcessVersion
0x4b846c FormatMessageA
0x4b8470 LoadResource
0x4b8474 LockResource
0x4b8478 GlobalGetAtomNameA
0x4b847c GlobalAddAtomA
0x4b8480 GlobalFindAtomA
0x4b8484 GetLastError
0x4b8488 SetLastError
0x4b848c InterlockedIncrement
0x4b8490 WritePrivateProfileStringA
0x4b8494 GlobalFlags
0x4b8498 MulDiv
0x4b849c GetVersion
0x4b84a0 lstrcpyA
0x4b84a4 SetErrorMode
0x4b84a8 InterlockedDecrement
0x4b84ac TlsGetValue
0x4b84b0 LocalReAlloc
0x4b84b4 TlsSetValue
0x4b84b8 EnterCriticalSection
0x4b84bc GlobalReAlloc
0x4b84c0 LeaveCriticalSection
0x4b84c4 TlsFree
0x4b84c8 GlobalHandle
0x4b84cc DeleteCriticalSection
0x4b84d0 TlsAlloc
0x4b84d4 InitializeCriticalSection
0x4b84d8 LocalFree
0x4b84dc LocalAlloc
0x4b84e0 lstrlenA
0x4b84e4 GetTickCount
0x4b84e8 CloseHandle
0x4b84ec GetModuleFileNameA
0x4b84f0 GlobalDeleteAtom
0x4b84f4 lstrcmpA
0x4b84f8 lstrcmpiA
0x4b84fc GetCurrentThread
0x4b8500 GetCurrentThreadId
0x4b8504 GetStringTypeA
0x4b8508 GetEnvironmentStrings
0x4b850c GetEnvironmentStringsW
0x4b8510 SetUnhandledExceptionFilter
0x4b8514 IsBadWritePtr
0x4b8518 VirtualAlloc
0x4b851c LCMapStringW
0x4b8520 VirtualFree
0x4b8524 HeapCreate
0x4b8528 HeapDestroy
0x4b852c GetVersionExA
0x4b8530 GetEnvironmentVariableA
0x4b8534 Sleep
0x4b8538 FreeLibrary
0x4b853c LCMapStringA
0x4b8540 RtlFillMemory
0x4b8544 WideCharToMultiByte
0x4b8548 lstrcpynA
0x4b854c MultiByteToWideChar
0x4b8550 FindResourceA
advapi32.dll
0x4b832c RegCloseKey
0x4b8330 RegOpenKeyExA
0x4b8334 CryptGetHashParam
0x4b8338 CryptDestroyHash
0x4b833c CryptHashData
0x4b8340 CryptReleaseContext
0x4b8344 CryptCreateHash
0x4b8348 CryptAcquireContextA
0x4b834c RegSetValueExA
0x4b8350 RegCreateKeyExA
crypt32.dll
0x4b8360 CryptBinaryToStringA
0x4b8364 CryptStringToBinaryA
oleacc.dll
0x4b85a8 ObjectFromLresult
gdi32.dll
0x4b836c SetWindowExtEx
0x4b8370 ScaleViewportExtEx
0x4b8374 SetViewportExtEx
0x4b8378 ScaleWindowExtEx
0x4b837c SetViewportOrgEx
0x4b8380 GetClipBox
0x4b8384 PtVisible
0x4b8388 RectVisible
0x4b838c TextOutA
0x4b8390 SetMapMode
0x4b8394 Escape
0x4b8398 GetObjectA
0x4b839c CreateBitmap
0x4b83a0 DeleteObject
0x4b83a4 SaveDC
0x4b83a8 GetDeviceCaps
0x4b83ac RestoreDC
0x4b83b0 DeleteDC
0x4b83b4 SelectObject
0x4b83b8 GetStockObject
0x4b83bc SetBkColor
0x4b83c0 OffsetViewportOrgEx
0x4b83c4 ExtTextOutA
0x4b83c8 SetTextColor
winspool.drv
0x4b87a8 DocumentPropertiesA
0x4b87ac OpenPrinterA
0x4b87b0 ClosePrinter
comctl32.dll
0x4b8358 None
oledlg.dll
0x4b8608 None
oleaut32.dll
0x4b85b0 SafeArrayGetElemsize
0x4b85b4 SafeArrayUnaccessData
0x4b85b8 SafeArrayAccessData
0x4b85bc VariantChangeType
0x4b85c0 VariantInit
0x4b85c4 SafeArrayAllocDescriptor
0x4b85c8 SafeArrayAllocData
0x4b85cc SafeArrayGetDim
0x4b85d0 SafeArrayGetLBound
0x4b85d4 SysFreeString
0x4b85d8 VariantCopy
0x4b85dc SafeArrayDestroy
0x4b85e0 VariantClear
0x4b85e4 SysAllocString
0x4b85e8 SafeArrayCreate
0x4b85ec RegisterTypeLib
0x4b85f0 LHashValOfNameSys
0x4b85f4 LoadTypeLib
0x4b85f8 VarR8FromBool
0x4b85fc VarR8FromCy
0x4b8600 SafeArrayGetUBound
MSVCRT.dll
0x4b8174 _except_handler3
0x4b8178 tolower
0x4b817c __CxxFrameHandler
0x4b8180 strncmp
0x4b8184 memmove
0x4b8188 realloc
0x4b818c strrchr
0x4b8190 modf
0x4b8194 _CIfmod
0x4b8198 _CIpow
0x4b819c floor
0x4b81a0 strtod
0x4b81a4 rand
0x4b81a8 srand
0x4b81ac atoi
0x4b81b0 atof
0x4b81b4 strchr
0x4b81b8 ??3@YAXPAX@Z
0x4b81bc ??2@YAPAXI@Z
0x4b81c0 malloc
0x4b81c4 free
0x4b81c8 _ftol
0x4b81cc _i64toa
0x4b81d0 calloc
0x4b81d4 _mbsstr
0x4b81d8 div
0x4b81dc atol
0x4b81e0 sprintf
EAT(Export Address Table) is none
WINMM.dll
0x4b8324 PlaySoundA
KERNEL32.dll
0x4b804c FindFirstFileW
0x4b8050 FindClose
0x4b8054 VirtualQueryEx
0x4b8058 lstrcpynA
0x4b805c CreateThread
0x4b8060 CreateWaitableTimerA
0x4b8064 SetWaitableTimer
0x4b8068 lstrcpyn
0x4b806c GetModuleHandleA
0x4b8070 VirtualAlloc
0x4b8074 VirtualFree
0x4b8078 LoadLibraryA
0x4b807c GetProcAddress
0x4b8080 CreateFileA
0x4b8084 ResetEvent
0x4b8088 WriteFile
0x4b808c CancelIo
0x4b8090 ReadFile
0x4b8094 GetProcessHeap
0x4b8098 ExitProcess
0x4b809c HeapAlloc
0x4b80a0 HeapReAlloc
0x4b80a4 HeapFree
0x4b80a8 IsBadReadPtr
0x4b80ac DeleteFileA
0x4b80b0 GetModuleFileNameA
0x4b80b4 Sleep
0x4b80b8 GetUserDefaultLCID
0x4b80bc GlobalUnlock
0x4b80c0 GetTickCount
0x4b80c4 SetFileAttributesA
0x4b80c8 GetPrivateProfileStringA
0x4b80cc LCMapStringA
0x4b80d0 GetCommandLineA
0x4b80d4 FreeLibrary
0x4b80d8 EnterCriticalSection
0x4b80dc LeaveCriticalSection
0x4b80e0 GetTempPathA
0x4b80e4 GetFileAttributesA
0x4b80e8 RtlMoveMemory
0x4b80ec GlobalLock
0x4b80f0 GetSystemDirectoryA
0x4b80f4 InitializeCriticalSection
0x4b80f8 GetWindowsDirectoryA
0x4b80fc FileTimeToSystemTime
0x4b8100 FileTimeToLocalFileTime
0x4b8104 SetFilePointer
0x4b8108 UnmapViewOfFile
0x4b810c SystemTimeToFileTime
0x4b8110 GetCurrentDirectoryA
0x4b8114 LocalFileTimeToFileTime
0x4b8118 CreateDirectoryA
0x4b811c GlobalAlloc
0x4b8120 WideCharToMultiByte
0x4b8124 lstrlenW
0x4b8128 GetCurrentDirectoryW
0x4b812c WaitForSingleObject
0x4b8130 MultiByteToWideChar
0x4b8134 LocalFree
0x4b8138 LocalAlloc
0x4b813c TerminateProcess
0x4b8140 OpenProcess
0x4b8144 GetCurrentProcess
0x4b8148 GetCurrentProcessId
0x4b814c CloseHandle
0x4b8150 Process32Next
0x4b8154 Process32First
0x4b8158 CreateToolhelp32Snapshot
0x4b815c CreateEventA
0x4b8160 OpenEventA
0x4b8164 DeleteCriticalSection
0x4b8168 GetFileSize
0x4b816c SetFileTime
ole32.dll
0x4b8558 CLSIDFromString
0x4b855c OleRun
0x4b8560 CoCreateInstance
0x4b8564 CLSIDFromProgID
0x4b8568 CLSIDFromString
0x4b856c OleFlushClipboard
0x4b8570 CoInitialize
0x4b8574 OleInitialize
0x4b8578 OleIsCurrentClipboard
0x4b857c OleUninitialize
0x4b8580 CoRevokeClassObject
0x4b8584 CoRegisterMessageFilter
0x4b8588 CoInitialize
0x4b858c CoUninitialize
0x4b8590 OleRun
0x4b8594 CoFreeUnusedLibraries
0x4b8598 CoCreateInstance
0x4b859c CLSIDFromProgID
0x4b85a0 CoUninitialize
USER32.dll
0x4b8274 GetDC
0x4b8278 ReleaseDC
0x4b827c OpenClipboard
0x4b8280 EmptyClipboard
0x4b8284 CloseClipboard
0x4b8288 GetForegroundWindow
0x4b828c UnhookWindowsHookEx
0x4b8290 GetCursorInfo
0x4b8294 GetIconInfo
0x4b8298 DrawIcon
0x4b829c MsgWaitForMultipleObjects
0x4b82a0 SendInput
0x4b82a4 SetWindowsHookExA
0x4b82a8 SetClipboardData
0x4b82ac GetCursorPos
0x4b82b0 PeekMessageA
0x4b82b4 GetSystemMetrics
0x4b82b8 wsprintfA
0x4b82bc MessageBoxA
0x4b82c0 DispatchMessageA
0x4b82c4 TranslateMessage
0x4b82c8 GetMessageA
0x4b82cc SetTimer
0x4b82d0 MessageBoxTimeoutA
0x4b82d4 CallNextHookEx
ADVAPI32.dll
0x4b8000 OpenProcessToken
0x4b8004 AllocateAndInitializeSid
0x4b8008 GetTokenInformation
0x4b800c EqualSid
0x4b8010 FreeSid
GDI32.dll
0x4b8018 GetDeviceCaps
0x4b801c CreateCompatibleDC
0x4b8020 CreateDIBSection
0x4b8024 SelectObject
0x4b8028 BitBlt
0x4b802c GetDIBits
0x4b8030 GetDIBColorTable
0x4b8034 StretchBlt
0x4b8038 GetBitmapBits
0x4b803c DeleteObject
0x4b8040 CreateCompatibleBitmap
0x4b8044 DeleteDC
OLEAUT32.dll
0x4b81e8 VariantInit
0x4b81ec SafeArrayAllocDescriptor
0x4b81f0 SafeArrayAllocData
0x4b81f4 SafeArrayGetDim
0x4b81f8 SafeArrayGetLBound
0x4b81fc SafeArrayGetUBound
0x4b8200 SafeArrayAccessData
0x4b8204 SafeArrayUnaccessData
0x4b8208 SafeArrayGetElemsize
0x4b820c SysFreeString
0x4b8210 VarR8FromCy
0x4b8214 VarR8FromBool
0x4b8218 VariantChangeType
0x4b821c LoadTypeLib
0x4b8220 LHashValOfNameSys
0x4b8224 RegisterTypeLib
0x4b8228 VariantCopy
0x4b822c SafeArrayCreate
0x4b8230 SysAllocString
0x4b8234 VariantClear
0x4b8238 SafeArrayDestroy
0x4b823c SystemTimeToVariantTime
SHELL32.dll
0x4b8258 ShellExecuteA
0x4b825c SHGetSpecialFolderPathA
0x4b8260 ShellExecuteExW
WINHTTP.dll
0x4b82dc WinHttpCrackUrl
0x4b82e0 WinHttpOpen
0x4b82e4 WinHttpSetTimeouts
0x4b82e8 WinHttpConnect
0x4b82ec WinHttpOpenRequest
0x4b82f0 WinHttpQueryHeaders
0x4b82f4 WinHttpSetCredentials
0x4b82f8 WinHttpCloseHandle
0x4b82fc WinHttpSetOption
0x4b8300 WinHttpAddRequestHeaders
0x4b8304 WinHttpSendRequest
0x4b8308 WinHttpReceiveResponse
0x4b830c WinHttpQueryDataAvailable
0x4b8310 WinHttpReadData
0x4b8314 WinHttpCheckPlatform
WININET.dll
0x4b831c DeleteUrlCacheEntry
urlmon.dll
0x4b8610 URLDownloadToFileA
SHLWAPI.dll
0x4b8268 PathFindExtensionA
0x4b826c PathFileExistsA
SETUPAPI.dll
0x4b8244 SetupDiGetClassDevsA
0x4b8248 SetupDiGetDeviceInterfaceDetailA
0x4b824c SetupDiDestroyDeviceInfoList
0x4b8250 SetupDiEnumDeviceInterfaces
user32.dll
0x4b8618 MessageBoxA
0x4b861c GetWindowRect
0x4b8620 WindowFromPoint
0x4b8624 CallWindowProcA
0x4b8628 GetWindow
0x4b862c SendMessageTimeoutA
0x4b8630 wsprintfA
0x4b8634 DispatchMessageA
0x4b8638 TranslateMessage
0x4b863c RegisterWindowMessageA
0x4b8640 GetMessageA
0x4b8644 PeekMessageA
0x4b8648 GetCursorPos
0x4b864c GetClassNameA
0x4b8650 EnumChildWindows
0x4b8654 SetFocus
0x4b8658 GetSystemMetrics
0x4b865c GetWindowPlacement
0x4b8660 IsIconic
0x4b8664 SystemParametersInfoA
0x4b8668 SetForegroundWindow
0x4b866c GetForegroundWindow
0x4b8670 GetMessagePos
0x4b8674 GetMessageTime
0x4b8678 DefWindowProcA
0x4b867c RemovePropA
0x4b8680 GetPropA
0x4b8684 SetPropA
0x4b8688 GetClassLongA
0x4b868c CreateWindowExA
0x4b8690 DestroyWindow
0x4b8694 GetMenuItemID
0x4b8698 GetMenuCheckMarkDimensions
0x4b869c GetMenu
0x4b86a0 RegisterClassA
0x4b86a4 GetClassInfoA
0x4b86a8 WinHelpA
0x4b86ac GetCapture
0x4b86b0 GetTopWindow
0x4b86b4 PostQuitMessage
0x4b86b8 PostMessageA
0x4b86bc SendMessageA
0x4b86c0 SetCursor
0x4b86c4 EnableWindow
0x4b86c8 GetWindowLongA
0x4b86cc IsWindowEnabled
0x4b86d0 GetLastActivePopup
0x4b86d4 GetParent
0x4b86d8 SetWindowsHookExA
0x4b86dc IsWindowVisible
0x4b86e0 ValidateRect
0x4b86e4 CallNextHookEx
0x4b86e8 GetKeyState
0x4b86ec GetActiveWindow
0x4b86f0 GetNextDlgTabItem
0x4b86f4 GetFocus
0x4b86f8 EnableMenuItem
0x4b86fc CheckMenuItem
0x4b8700 SetMenuItemBitmaps
0x4b8704 ModifyMenuA
0x4b8708 GetMenuState
0x4b870c LoadBitmapA
0x4b8710 RegisterClipboardFormatA
0x4b8714 UnhookWindowsHookEx
0x4b8718 UnregisterClassA
0x4b871c PtInRect
0x4b8720 ClientToScreen
0x4b8724 SetWindowTextA
0x4b8728 GetWindowTextA
0x4b872c GetMenuItemCount
0x4b8730 GetDC
0x4b8734 ReleaseDC
0x4b8738 TabbedTextOutA
0x4b873c DrawTextA
0x4b8740 GrayStringA
0x4b8744 GetDlgItem
0x4b8748 EndDialog
0x4b874c CreateDialogIndirectParamA
0x4b8750 DestroyMenu
0x4b8754 PostThreadMessageA
0x4b8758 LoadStringA
0x4b875c GetSysColorBrush
0x4b8760 LoadCursorA
0x4b8764 LoadIconA
0x4b8768 UpdateWindow
0x4b876c MapWindowPoints
0x4b8770 GetSysColor
0x4b8774 SetActiveWindow
0x4b8778 IsWindow
0x4b877c AdjustWindowRectEx
0x4b8780 GetClientRect
0x4b8784 CopyRect
0x4b8788 ShowWindow
0x4b878c GetSubMenu
0x4b8790 SendDlgItemMessageA
0x4b8794 IsDialogMessageA
0x4b8798 SetWindowLongA
0x4b879c SetWindowPos
0x4b87a0 GetDlgCtrlID
kernel32.dll
0x4b83d0 GlobalAlloc
0x4b83d4 GlobalLock
0x4b83d8 GlobalUnlock
0x4b83dc GlobalFree
0x4b83e0 GetUserDefaultLCID
0x4b83e4 IsBadReadPtr
0x4b83e8 HeapFree
0x4b83ec HeapReAlloc
0x4b83f0 HeapAlloc
0x4b83f4 ExitProcess
0x4b83f8 GetProcessHeap
0x4b83fc WriteProcessMemory
0x4b8400 GetProcAddress
0x4b8404 LoadLibraryA
0x4b8408 lstrcpyn
0x4b840c lstrcatA
0x4b8410 SetHandleCount
0x4b8414 GetStringTypeW
0x4b8418 IsBadCodePtr
0x4b841c SetStdHandle
0x4b8420 FreeEnvironmentStringsW
0x4b8424 FreeEnvironmentStringsA
0x4b8428 GetStartupInfoA
0x4b842c GetFileType
0x4b8430 GetModuleHandleA
0x4b8434 GetStdHandle
0x4b8438 GetACP
0x4b843c HeapSize
0x4b8440 RaiseException
0x4b8444 TerminateProcess
0x4b8448 RtlUnwind
0x4b844c GetCommandLineA
0x4b8450 GetOEMCP
0x4b8454 GetCPInfo
0x4b8458 FlushFileBuffers
0x4b845c SetFilePointer
0x4b8460 WriteFile
0x4b8464 GetCurrentProcess
0x4b8468 GetProcessVersion
0x4b846c FormatMessageA
0x4b8470 LoadResource
0x4b8474 LockResource
0x4b8478 GlobalGetAtomNameA
0x4b847c GlobalAddAtomA
0x4b8480 GlobalFindAtomA
0x4b8484 GetLastError
0x4b8488 SetLastError
0x4b848c InterlockedIncrement
0x4b8490 WritePrivateProfileStringA
0x4b8494 GlobalFlags
0x4b8498 MulDiv
0x4b849c GetVersion
0x4b84a0 lstrcpyA
0x4b84a4 SetErrorMode
0x4b84a8 InterlockedDecrement
0x4b84ac TlsGetValue
0x4b84b0 LocalReAlloc
0x4b84b4 TlsSetValue
0x4b84b8 EnterCriticalSection
0x4b84bc GlobalReAlloc
0x4b84c0 LeaveCriticalSection
0x4b84c4 TlsFree
0x4b84c8 GlobalHandle
0x4b84cc DeleteCriticalSection
0x4b84d0 TlsAlloc
0x4b84d4 InitializeCriticalSection
0x4b84d8 LocalFree
0x4b84dc LocalAlloc
0x4b84e0 lstrlenA
0x4b84e4 GetTickCount
0x4b84e8 CloseHandle
0x4b84ec GetModuleFileNameA
0x4b84f0 GlobalDeleteAtom
0x4b84f4 lstrcmpA
0x4b84f8 lstrcmpiA
0x4b84fc GetCurrentThread
0x4b8500 GetCurrentThreadId
0x4b8504 GetStringTypeA
0x4b8508 GetEnvironmentStrings
0x4b850c GetEnvironmentStringsW
0x4b8510 SetUnhandledExceptionFilter
0x4b8514 IsBadWritePtr
0x4b8518 VirtualAlloc
0x4b851c LCMapStringW
0x4b8520 VirtualFree
0x4b8524 HeapCreate
0x4b8528 HeapDestroy
0x4b852c GetVersionExA
0x4b8530 GetEnvironmentVariableA
0x4b8534 Sleep
0x4b8538 FreeLibrary
0x4b853c LCMapStringA
0x4b8540 RtlFillMemory
0x4b8544 WideCharToMultiByte
0x4b8548 lstrcpynA
0x4b854c MultiByteToWideChar
0x4b8550 FindResourceA
advapi32.dll
0x4b832c RegCloseKey
0x4b8330 RegOpenKeyExA
0x4b8334 CryptGetHashParam
0x4b8338 CryptDestroyHash
0x4b833c CryptHashData
0x4b8340 CryptReleaseContext
0x4b8344 CryptCreateHash
0x4b8348 CryptAcquireContextA
0x4b834c RegSetValueExA
0x4b8350 RegCreateKeyExA
crypt32.dll
0x4b8360 CryptBinaryToStringA
0x4b8364 CryptStringToBinaryA
oleacc.dll
0x4b85a8 ObjectFromLresult
gdi32.dll
0x4b836c SetWindowExtEx
0x4b8370 ScaleViewportExtEx
0x4b8374 SetViewportExtEx
0x4b8378 ScaleWindowExtEx
0x4b837c SetViewportOrgEx
0x4b8380 GetClipBox
0x4b8384 PtVisible
0x4b8388 RectVisible
0x4b838c TextOutA
0x4b8390 SetMapMode
0x4b8394 Escape
0x4b8398 GetObjectA
0x4b839c CreateBitmap
0x4b83a0 DeleteObject
0x4b83a4 SaveDC
0x4b83a8 GetDeviceCaps
0x4b83ac RestoreDC
0x4b83b0 DeleteDC
0x4b83b4 SelectObject
0x4b83b8 GetStockObject
0x4b83bc SetBkColor
0x4b83c0 OffsetViewportOrgEx
0x4b83c4 ExtTextOutA
0x4b83c8 SetTextColor
winspool.drv
0x4b87a8 DocumentPropertiesA
0x4b87ac OpenPrinterA
0x4b87b0 ClosePrinter
comctl32.dll
0x4b8358 None
oledlg.dll
0x4b8608 None
oleaut32.dll
0x4b85b0 SafeArrayGetElemsize
0x4b85b4 SafeArrayUnaccessData
0x4b85b8 SafeArrayAccessData
0x4b85bc VariantChangeType
0x4b85c0 VariantInit
0x4b85c4 SafeArrayAllocDescriptor
0x4b85c8 SafeArrayAllocData
0x4b85cc SafeArrayGetDim
0x4b85d0 SafeArrayGetLBound
0x4b85d4 SysFreeString
0x4b85d8 VariantCopy
0x4b85dc SafeArrayDestroy
0x4b85e0 VariantClear
0x4b85e4 SysAllocString
0x4b85e8 SafeArrayCreate
0x4b85ec RegisterTypeLib
0x4b85f0 LHashValOfNameSys
0x4b85f4 LoadTypeLib
0x4b85f8 VarR8FromBool
0x4b85fc VarR8FromCy
0x4b8600 SafeArrayGetUBound
MSVCRT.dll
0x4b8174 _except_handler3
0x4b8178 tolower
0x4b817c __CxxFrameHandler
0x4b8180 strncmp
0x4b8184 memmove
0x4b8188 realloc
0x4b818c strrchr
0x4b8190 modf
0x4b8194 _CIfmod
0x4b8198 _CIpow
0x4b819c floor
0x4b81a0 strtod
0x4b81a4 rand
0x4b81a8 srand
0x4b81ac atoi
0x4b81b0 atof
0x4b81b4 strchr
0x4b81b8 ??3@YAXPAX@Z
0x4b81bc ??2@YAPAXI@Z
0x4b81c0 malloc
0x4b81c4 free
0x4b81c8 _ftol
0x4b81cc _i64toa
0x4b81d0 calloc
0x4b81d4 _mbsstr
0x4b81d8 div
0x4b81dc atol
0x4b81e0 sprintf
EAT(Export Address Table) is none