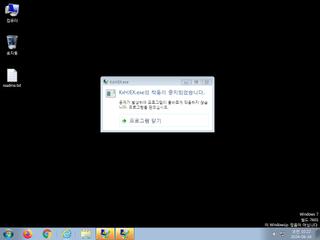
ScreenShot
| Created | 2024.06.16 10:26 | Machine | s1_win7_x6401 |
| Filename | jiali.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 45 detected (FamVT, DumpModuleInfectiousNME, Nimnul, Wapomi, Unsafe, VJadtre, Save, malicious, Windows, Threat, score, Mikcer, Banload, cstqaj, Real Protect, high, Jadtre, Wali, KA@558nxg, Ramnit, Detected, Probably Heur, ExeHeaderL, GenAsa, iFI0cidiERI, ai score=80, CoinMiner, confidence, 100%) | ||
| md5 | 6c63f5db1f5beff0a1cb3af035ca3d4c | ||
| sha256 | 565e3379fa532b07aac8fb1b9dbdd6673fdac87c399a7800235c88e7dabe7f28 | ||
| ssdeep | 24576:JBbdrmZoGk/52SCUAO55ksXy4gE47he4wtL/xExlzXyD:Jr3/5PkO553eEQwtqx | ||
| imphash | 245788be5f7374c2353736518c2959b3 | ||
| impfuzzy | 192:wPRNM0GoCUUqT0bTzSsEsCcRcocaKSZAQCE:eMEpTHEt0E | ||
Network IP location
Signature (15cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 45 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| watch | Deletes executed files from disk |
| notice | A process created a hidden window |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Checks for the Locally Unique Identifier on the system for a suspicious privilege |
| notice | Creates executable files on the filesystem |
| notice | Drops a binary and executes it |
| notice | Drops an executable to the user AppData folder |
| notice | Foreign language identified in PE resource |
| notice | Searches running processes potentially to identify processes for sandbox evasion |
| info | Command line console output was observed |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | The file contains an unknown PE resource name possibly indicative of a packer |
| info | Tries to locate where the browsers are installed |
Rules (21cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | ASPack_Zero | ASPack packed file | binaries (download) |
| watch | ASPack_Zero | ASPack packed file | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (download) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | Network_Downloader | File Downloader | binaries (download) |
| watch | Network_Downloader | File Downloader | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (download) |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (download) |
| info | DllRegisterServer_Zero | execute regsvr32.exe | binaries (upload) |
| info | IsPE32 | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (7cnts) ?
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x47c170 lstrcmpiA
0x47c174 SetEndOfFile
0x47c178 UnlockFile
0x47c17c LockFile
0x47c180 FlushFileBuffers
0x47c184 SetFilePointer
0x47c188 DuplicateHandle
0x47c18c lstrcpynA
0x47c190 SetLastError
0x47c194 FileTimeToLocalFileTime
0x47c198 FileTimeToSystemTime
0x47c19c LocalFree
0x47c1a0 InterlockedDecrement
0x47c1a4 GetCurrentProcess
0x47c1a8 GetWindowsDirectoryA
0x47c1ac GetSystemDirectoryA
0x47c1b0 CreateSemaphoreA
0x47c1b4 ResumeThread
0x47c1b8 ReleaseSemaphore
0x47c1bc EnterCriticalSection
0x47c1c0 LeaveCriticalSection
0x47c1c4 SetStdHandle
0x47c1c8 IsBadCodePtr
0x47c1cc IsBadReadPtr
0x47c1d0 CompareStringW
0x47c1d4 CompareStringA
0x47c1d8 SetUnhandledExceptionFilter
0x47c1dc GetStringTypeW
0x47c1e0 GetStringTypeA
0x47c1e4 IsBadWritePtr
0x47c1e8 VirtualAlloc
0x47c1ec LCMapStringW
0x47c1f0 LCMapStringA
0x47c1f4 SetEnvironmentVariableA
0x47c1f8 VirtualFree
0x47c1fc HeapCreate
0x47c200 HeapDestroy
0x47c204 GetEnvironmentVariableA
0x47c208 GetFileType
0x47c20c GetStdHandle
0x47c210 SetHandleCount
0x47c214 GetEnvironmentStringsW
0x47c218 GetEnvironmentStrings
0x47c21c FreeEnvironmentStringsW
0x47c220 FreeEnvironmentStringsA
0x47c224 UnhandledExceptionFilter
0x47c228 GetACP
0x47c22c HeapSize
0x47c230 TerminateProcess
0x47c234 GetLocalTime
0x47c238 GetSystemTime
0x47c23c GetTimeZoneInformation
0x47c240 RaiseException
0x47c244 GetProfileStringA
0x47c248 WriteFile
0x47c24c WaitForMultipleObjects
0x47c250 CreateFileA
0x47c254 SetEvent
0x47c258 FindResourceA
0x47c25c LoadResource
0x47c260 LockResource
0x47c264 ReadFile
0x47c268 GetModuleFileNameA
0x47c26c WideCharToMultiByte
0x47c270 MultiByteToWideChar
0x47c274 GetCurrentThreadId
0x47c278 ExitProcess
0x47c27c GlobalSize
0x47c280 GlobalFree
0x47c284 DeleteCriticalSection
0x47c288 InitializeCriticalSection
0x47c28c lstrcatA
0x47c290 lstrlenA
0x47c294 WinExec
0x47c298 lstrcpyA
0x47c29c FindNextFileA
0x47c2a0 GlobalReAlloc
0x47c2a4 HeapFree
0x47c2a8 HeapReAlloc
0x47c2ac GetProcessHeap
0x47c2b0 HeapAlloc
0x47c2b4 GetFullPathNameA
0x47c2b8 FreeLibrary
0x47c2bc LoadLibraryA
0x47c2c0 GetLastError
0x47c2c4 GetVersionExA
0x47c2c8 WritePrivateProfileStringA
0x47c2cc CreateThread
0x47c2d0 CreateEventA
0x47c2d4 Sleep
0x47c2d8 GlobalAlloc
0x47c2dc GlobalLock
0x47c2e0 GlobalUnlock
0x47c2e4 GetTempPathA
0x47c2e8 FindFirstFileA
0x47c2ec FindClose
0x47c2f0 RtlUnwind
0x47c2f4 GetStartupInfoA
0x47c2f8 GetOEMCP
0x47c2fc GetCPInfo
0x47c300 GetProcessVersion
0x47c304 SetErrorMode
0x47c308 GlobalFlags
0x47c30c GetCurrentThread
0x47c310 GetFileTime
0x47c314 GetFileSize
0x47c318 TlsGetValue
0x47c31c LocalReAlloc
0x47c320 TlsSetValue
0x47c324 TlsFree
0x47c328 GlobalHandle
0x47c32c TlsAlloc
0x47c330 GetFileAttributesA
0x47c334 SetCurrentDirectoryA
0x47c338 GetVolumeInformationA
0x47c33c GetModuleHandleA
0x47c340 GetProcAddress
0x47c344 MulDiv
0x47c348 GetCommandLineA
0x47c34c GetTickCount
0x47c350 CreateProcessA
0x47c354 WaitForSingleObject
0x47c358 CloseHandle
0x47c35c GlobalDeleteAtom
0x47c360 LocalAlloc
0x47c364 lstrcmpA
0x47c368 GetVersion
0x47c36c GlobalGetAtomNameA
0x47c370 GlobalAddAtomA
0x47c374 GlobalFindAtomA
0x47c378 InterlockedIncrement
USER32.dll
0x47c3a0 GetScrollPos
0x47c3a4 WaitForInputIdle
0x47c3a8 wsprintfA
0x47c3ac CloseClipboard
0x47c3b0 GetClipboardData
0x47c3b4 OpenClipboard
0x47c3b8 SetClipboardData
0x47c3bc EmptyClipboard
0x47c3c0 GetSystemMetrics
0x47c3c4 GetCursorPos
0x47c3c8 MessageBoxA
0x47c3cc SetWindowPos
0x47c3d0 SendMessageA
0x47c3d4 DestroyCursor
0x47c3d8 SetParent
0x47c3dc IsWindow
0x47c3e0 PostMessageA
0x47c3e4 GetTopWindow
0x47c3e8 GetParent
0x47c3ec GetFocus
0x47c3f0 GetClientRect
0x47c3f4 InvalidateRect
0x47c3f8 ValidateRect
0x47c3fc UpdateWindow
0x47c400 EqualRect
0x47c404 GetWindowRect
0x47c408 SetForegroundWindow
0x47c40c DestroyMenu
0x47c410 IsChild
0x47c414 ReleaseDC
0x47c418 IsRectEmpty
0x47c41c FillRect
0x47c420 GetDC
0x47c424 SetCursor
0x47c428 LoadCursorA
0x47c42c SetCursorPos
0x47c430 SetActiveWindow
0x47c434 GetSysColor
0x47c438 SetWindowLongA
0x47c43c GetWindowLongA
0x47c440 RedrawWindow
0x47c444 EnableWindow
0x47c448 IsWindowVisible
0x47c44c OffsetRect
0x47c450 PtInRect
0x47c454 DestroyIcon
0x47c458 IntersectRect
0x47c45c InflateRect
0x47c460 SetRect
0x47c464 SetScrollPos
0x47c468 SetScrollRange
0x47c46c GetScrollRange
0x47c470 SetCapture
0x47c474 GetCapture
0x47c478 ReleaseCapture
0x47c47c GetForegroundWindow
0x47c480 LoadIconA
0x47c484 TranslateMessage
0x47c488 DrawFrameControl
0x47c48c DrawEdge
0x47c490 DrawFocusRect
0x47c494 WindowFromPoint
0x47c498 GetMessageA
0x47c49c DispatchMessageA
0x47c4a0 SetRectEmpty
0x47c4a4 RegisterClipboardFormatA
0x47c4a8 CreateIconFromResourceEx
0x47c4ac CreateIconFromResource
0x47c4b0 DrawIconEx
0x47c4b4 CreatePopupMenu
0x47c4b8 AppendMenuA
0x47c4bc ModifyMenuA
0x47c4c0 CreateMenu
0x47c4c4 CreateAcceleratorTableA
0x47c4c8 GetDlgCtrlID
0x47c4cc GetSubMenu
0x47c4d0 EnableMenuItem
0x47c4d4 ClientToScreen
0x47c4d8 EnumDisplaySettingsA
0x47c4dc LoadImageA
0x47c4e0 SystemParametersInfoA
0x47c4e4 ShowWindow
0x47c4e8 IsWindowEnabled
0x47c4ec TranslateAcceleratorA
0x47c4f0 GetKeyState
0x47c4f4 CopyAcceleratorTableA
0x47c4f8 PostQuitMessage
0x47c4fc IsZoomed
0x47c500 GetClassInfoA
0x47c504 DefWindowProcA
0x47c508 GetSystemMenu
0x47c50c DeleteMenu
0x47c510 GetMenu
0x47c514 SetMenu
0x47c518 GetWindowTextA
0x47c51c GetWindowTextLengthA
0x47c520 CharUpperA
0x47c524 GetWindowDC
0x47c528 BeginPaint
0x47c52c EndPaint
0x47c530 TabbedTextOutA
0x47c534 DrawTextA
0x47c538 GrayStringA
0x47c53c GetDlgItem
0x47c540 DestroyWindow
0x47c544 CreateDialogIndirectParamA
0x47c548 EndDialog
0x47c54c GetNextDlgTabItem
0x47c550 GetWindowPlacement
0x47c554 RegisterWindowMessageA
0x47c558 GetLastActivePopup
0x47c55c GetMessageTime
0x47c560 RemovePropA
0x47c564 CallWindowProcA
0x47c568 GetPropA
0x47c56c UnhookWindowsHookEx
0x47c570 SetPropA
0x47c574 GetClassLongA
0x47c578 CallNextHookEx
0x47c57c SetWindowsHookExA
0x47c580 CreateWindowExA
0x47c584 GetMenuItemID
0x47c588 GetMenuItemCount
0x47c58c RegisterClassA
0x47c590 UnregisterClassA
0x47c594 AdjustWindowRectEx
0x47c598 MapWindowPoints
0x47c59c SendDlgItemMessageA
0x47c5a0 ScrollWindowEx
0x47c5a4 IsDialogMessageA
0x47c5a8 SetWindowTextA
0x47c5ac MoveWindow
0x47c5b0 CheckMenuItem
0x47c5b4 SetMenuItemBitmaps
0x47c5b8 GetMenuState
0x47c5bc GetMenuCheckMarkDimensions
0x47c5c0 GetClassNameA
0x47c5c4 GetDesktopWindow
0x47c5c8 LoadStringA
0x47c5cc GetSysColorBrush
0x47c5d0 PeekMessageA
0x47c5d4 IsIconic
0x47c5d8 SetFocus
0x47c5dc GetActiveWindow
0x47c5e0 GetWindow
0x47c5e4 DestroyAcceleratorTable
0x47c5e8 SetWindowRgn
0x47c5ec GetMessagePos
0x47c5f0 ScreenToClient
0x47c5f4 ChildWindowFromPointEx
0x47c5f8 CopyRect
0x47c5fc LoadBitmapA
0x47c600 WinHelpA
0x47c604 KillTimer
0x47c608 SetTimer
GDI32.dll
0x47c024 GetClipRgn
0x47c028 CreatePolygonRgn
0x47c02c SelectClipRgn
0x47c030 DeleteObject
0x47c034 CreateDIBitmap
0x47c038 GetSystemPaletteEntries
0x47c03c CreatePalette
0x47c040 StretchBlt
0x47c044 SelectPalette
0x47c048 RealizePalette
0x47c04c GetDIBits
0x47c050 GetWindowExtEx
0x47c054 GetViewportOrgEx
0x47c058 GetWindowOrgEx
0x47c05c BeginPath
0x47c060 EndPath
0x47c064 PathToRegion
0x47c068 CreateEllipticRgn
0x47c06c CreateRoundRectRgn
0x47c070 GetTextColor
0x47c074 GetBkMode
0x47c078 GetBkColor
0x47c07c GetROP2
0x47c080 GetStretchBltMode
0x47c084 GetPolyFillMode
0x47c088 CreateCompatibleBitmap
0x47c08c CreateDCA
0x47c090 CreateBitmap
0x47c094 SelectObject
0x47c098 GetObjectA
0x47c09c CreatePen
0x47c0a0 SetStretchBltMode
0x47c0a4 CombineRgn
0x47c0a8 CreateRectRgn
0x47c0ac FillRgn
0x47c0b0 CreateSolidBrush
0x47c0b4 GetStockObject
0x47c0b8 CreateFontIndirectA
0x47c0bc EndPage
0x47c0c0 EndDoc
0x47c0c4 DeleteDC
0x47c0c8 StartDocA
0x47c0cc StartPage
0x47c0d0 BitBlt
0x47c0d4 CreateCompatibleDC
0x47c0d8 Ellipse
0x47c0dc Rectangle
0x47c0e0 LPtoDP
0x47c0e4 DPtoLP
0x47c0e8 GetCurrentObject
0x47c0ec RoundRect
0x47c0f0 GetTextExtentPoint32A
0x47c0f4 GetDeviceCaps
0x47c0f8 SaveDC
0x47c0fc RestoreDC
0x47c100 SetBkMode
0x47c104 SetPolyFillMode
0x47c108 SetROP2
0x47c10c SetTextColor
0x47c110 SetMapMode
0x47c114 SetViewportOrgEx
0x47c118 OffsetViewportOrgEx
0x47c11c SetViewportExtEx
0x47c120 ScaleViewportExtEx
0x47c124 SetWindowOrgEx
0x47c128 SetWindowExtEx
0x47c12c ScaleWindowExtEx
0x47c130 GetClipBox
0x47c134 ExcludeClipRect
0x47c138 MoveToEx
0x47c13c LineTo
0x47c140 CreateRectRgnIndirect
0x47c144 SetBkColor
0x47c148 PatBlt
0x47c14c GetTextMetricsA
0x47c150 Escape
0x47c154 ExtTextOutA
0x47c158 TextOutA
0x47c15c RectVisible
0x47c160 PtVisible
0x47c164 GetViewportExtEx
0x47c168 ExtSelectClipRgn
WINMM.dll
0x47c610 midiStreamRestart
0x47c614 midiStreamClose
0x47c618 midiOutReset
0x47c61c midiStreamStop
0x47c620 midiStreamOut
0x47c624 midiOutPrepareHeader
0x47c628 midiStreamProperty
0x47c62c midiStreamOpen
0x47c630 midiOutUnprepareHeader
0x47c634 waveOutOpen
0x47c638 waveOutGetNumDevs
0x47c63c waveOutClose
0x47c640 waveOutReset
0x47c644 waveOutPause
0x47c648 waveOutWrite
0x47c64c waveOutPrepareHeader
0x47c650 waveOutUnprepareHeader
WINSPOOL.DRV
0x47c658 ClosePrinter
0x47c65c DocumentPropertiesA
0x47c660 OpenPrinterA
ADVAPI32.dll
0x47c000 RegCloseKey
0x47c004 RegOpenKeyExA
0x47c008 RegSetValueExA
0x47c00c RegQueryValueA
0x47c010 RegCreateKeyExA
SHELL32.dll
0x47c390 ShellExecuteA
0x47c394 Shell_NotifyIconA
0x47c398 SHGetSpecialFolderPathA
ole32.dll
0x47c6a4 OleInitialize
0x47c6a8 OleUninitialize
0x47c6ac CLSIDFromString
OLEAUT32.dll
0x47c380 UnRegisterTypeLib
0x47c384 RegisterTypeLib
0x47c388 LoadTypeLib
COMCTL32.dll
0x47c018 ImageList_Destroy
0x47c01c None
WS2_32.dll
0x47c668 recv
0x47c66c getpeername
0x47c670 accept
0x47c674 recvfrom
0x47c678 ioctlsocket
0x47c67c WSAAsyncSelect
0x47c680 closesocket
0x47c684 inet_ntoa
0x47c688 WSACleanup
comdlg32.dll
0x47c690 GetFileTitleA
0x47c694 GetSaveFileNameA
0x47c698 GetOpenFileNameA
0x47c69c ChooseColorA
EAT(Export Address Table) is none
KERNEL32.dll
0x47c170 lstrcmpiA
0x47c174 SetEndOfFile
0x47c178 UnlockFile
0x47c17c LockFile
0x47c180 FlushFileBuffers
0x47c184 SetFilePointer
0x47c188 DuplicateHandle
0x47c18c lstrcpynA
0x47c190 SetLastError
0x47c194 FileTimeToLocalFileTime
0x47c198 FileTimeToSystemTime
0x47c19c LocalFree
0x47c1a0 InterlockedDecrement
0x47c1a4 GetCurrentProcess
0x47c1a8 GetWindowsDirectoryA
0x47c1ac GetSystemDirectoryA
0x47c1b0 CreateSemaphoreA
0x47c1b4 ResumeThread
0x47c1b8 ReleaseSemaphore
0x47c1bc EnterCriticalSection
0x47c1c0 LeaveCriticalSection
0x47c1c4 SetStdHandle
0x47c1c8 IsBadCodePtr
0x47c1cc IsBadReadPtr
0x47c1d0 CompareStringW
0x47c1d4 CompareStringA
0x47c1d8 SetUnhandledExceptionFilter
0x47c1dc GetStringTypeW
0x47c1e0 GetStringTypeA
0x47c1e4 IsBadWritePtr
0x47c1e8 VirtualAlloc
0x47c1ec LCMapStringW
0x47c1f0 LCMapStringA
0x47c1f4 SetEnvironmentVariableA
0x47c1f8 VirtualFree
0x47c1fc HeapCreate
0x47c200 HeapDestroy
0x47c204 GetEnvironmentVariableA
0x47c208 GetFileType
0x47c20c GetStdHandle
0x47c210 SetHandleCount
0x47c214 GetEnvironmentStringsW
0x47c218 GetEnvironmentStrings
0x47c21c FreeEnvironmentStringsW
0x47c220 FreeEnvironmentStringsA
0x47c224 UnhandledExceptionFilter
0x47c228 GetACP
0x47c22c HeapSize
0x47c230 TerminateProcess
0x47c234 GetLocalTime
0x47c238 GetSystemTime
0x47c23c GetTimeZoneInformation
0x47c240 RaiseException
0x47c244 GetProfileStringA
0x47c248 WriteFile
0x47c24c WaitForMultipleObjects
0x47c250 CreateFileA
0x47c254 SetEvent
0x47c258 FindResourceA
0x47c25c LoadResource
0x47c260 LockResource
0x47c264 ReadFile
0x47c268 GetModuleFileNameA
0x47c26c WideCharToMultiByte
0x47c270 MultiByteToWideChar
0x47c274 GetCurrentThreadId
0x47c278 ExitProcess
0x47c27c GlobalSize
0x47c280 GlobalFree
0x47c284 DeleteCriticalSection
0x47c288 InitializeCriticalSection
0x47c28c lstrcatA
0x47c290 lstrlenA
0x47c294 WinExec
0x47c298 lstrcpyA
0x47c29c FindNextFileA
0x47c2a0 GlobalReAlloc
0x47c2a4 HeapFree
0x47c2a8 HeapReAlloc
0x47c2ac GetProcessHeap
0x47c2b0 HeapAlloc
0x47c2b4 GetFullPathNameA
0x47c2b8 FreeLibrary
0x47c2bc LoadLibraryA
0x47c2c0 GetLastError
0x47c2c4 GetVersionExA
0x47c2c8 WritePrivateProfileStringA
0x47c2cc CreateThread
0x47c2d0 CreateEventA
0x47c2d4 Sleep
0x47c2d8 GlobalAlloc
0x47c2dc GlobalLock
0x47c2e0 GlobalUnlock
0x47c2e4 GetTempPathA
0x47c2e8 FindFirstFileA
0x47c2ec FindClose
0x47c2f0 RtlUnwind
0x47c2f4 GetStartupInfoA
0x47c2f8 GetOEMCP
0x47c2fc GetCPInfo
0x47c300 GetProcessVersion
0x47c304 SetErrorMode
0x47c308 GlobalFlags
0x47c30c GetCurrentThread
0x47c310 GetFileTime
0x47c314 GetFileSize
0x47c318 TlsGetValue
0x47c31c LocalReAlloc
0x47c320 TlsSetValue
0x47c324 TlsFree
0x47c328 GlobalHandle
0x47c32c TlsAlloc
0x47c330 GetFileAttributesA
0x47c334 SetCurrentDirectoryA
0x47c338 GetVolumeInformationA
0x47c33c GetModuleHandleA
0x47c340 GetProcAddress
0x47c344 MulDiv
0x47c348 GetCommandLineA
0x47c34c GetTickCount
0x47c350 CreateProcessA
0x47c354 WaitForSingleObject
0x47c358 CloseHandle
0x47c35c GlobalDeleteAtom
0x47c360 LocalAlloc
0x47c364 lstrcmpA
0x47c368 GetVersion
0x47c36c GlobalGetAtomNameA
0x47c370 GlobalAddAtomA
0x47c374 GlobalFindAtomA
0x47c378 InterlockedIncrement
USER32.dll
0x47c3a0 GetScrollPos
0x47c3a4 WaitForInputIdle
0x47c3a8 wsprintfA
0x47c3ac CloseClipboard
0x47c3b0 GetClipboardData
0x47c3b4 OpenClipboard
0x47c3b8 SetClipboardData
0x47c3bc EmptyClipboard
0x47c3c0 GetSystemMetrics
0x47c3c4 GetCursorPos
0x47c3c8 MessageBoxA
0x47c3cc SetWindowPos
0x47c3d0 SendMessageA
0x47c3d4 DestroyCursor
0x47c3d8 SetParent
0x47c3dc IsWindow
0x47c3e0 PostMessageA
0x47c3e4 GetTopWindow
0x47c3e8 GetParent
0x47c3ec GetFocus
0x47c3f0 GetClientRect
0x47c3f4 InvalidateRect
0x47c3f8 ValidateRect
0x47c3fc UpdateWindow
0x47c400 EqualRect
0x47c404 GetWindowRect
0x47c408 SetForegroundWindow
0x47c40c DestroyMenu
0x47c410 IsChild
0x47c414 ReleaseDC
0x47c418 IsRectEmpty
0x47c41c FillRect
0x47c420 GetDC
0x47c424 SetCursor
0x47c428 LoadCursorA
0x47c42c SetCursorPos
0x47c430 SetActiveWindow
0x47c434 GetSysColor
0x47c438 SetWindowLongA
0x47c43c GetWindowLongA
0x47c440 RedrawWindow
0x47c444 EnableWindow
0x47c448 IsWindowVisible
0x47c44c OffsetRect
0x47c450 PtInRect
0x47c454 DestroyIcon
0x47c458 IntersectRect
0x47c45c InflateRect
0x47c460 SetRect
0x47c464 SetScrollPos
0x47c468 SetScrollRange
0x47c46c GetScrollRange
0x47c470 SetCapture
0x47c474 GetCapture
0x47c478 ReleaseCapture
0x47c47c GetForegroundWindow
0x47c480 LoadIconA
0x47c484 TranslateMessage
0x47c488 DrawFrameControl
0x47c48c DrawEdge
0x47c490 DrawFocusRect
0x47c494 WindowFromPoint
0x47c498 GetMessageA
0x47c49c DispatchMessageA
0x47c4a0 SetRectEmpty
0x47c4a4 RegisterClipboardFormatA
0x47c4a8 CreateIconFromResourceEx
0x47c4ac CreateIconFromResource
0x47c4b0 DrawIconEx
0x47c4b4 CreatePopupMenu
0x47c4b8 AppendMenuA
0x47c4bc ModifyMenuA
0x47c4c0 CreateMenu
0x47c4c4 CreateAcceleratorTableA
0x47c4c8 GetDlgCtrlID
0x47c4cc GetSubMenu
0x47c4d0 EnableMenuItem
0x47c4d4 ClientToScreen
0x47c4d8 EnumDisplaySettingsA
0x47c4dc LoadImageA
0x47c4e0 SystemParametersInfoA
0x47c4e4 ShowWindow
0x47c4e8 IsWindowEnabled
0x47c4ec TranslateAcceleratorA
0x47c4f0 GetKeyState
0x47c4f4 CopyAcceleratorTableA
0x47c4f8 PostQuitMessage
0x47c4fc IsZoomed
0x47c500 GetClassInfoA
0x47c504 DefWindowProcA
0x47c508 GetSystemMenu
0x47c50c DeleteMenu
0x47c510 GetMenu
0x47c514 SetMenu
0x47c518 GetWindowTextA
0x47c51c GetWindowTextLengthA
0x47c520 CharUpperA
0x47c524 GetWindowDC
0x47c528 BeginPaint
0x47c52c EndPaint
0x47c530 TabbedTextOutA
0x47c534 DrawTextA
0x47c538 GrayStringA
0x47c53c GetDlgItem
0x47c540 DestroyWindow
0x47c544 CreateDialogIndirectParamA
0x47c548 EndDialog
0x47c54c GetNextDlgTabItem
0x47c550 GetWindowPlacement
0x47c554 RegisterWindowMessageA
0x47c558 GetLastActivePopup
0x47c55c GetMessageTime
0x47c560 RemovePropA
0x47c564 CallWindowProcA
0x47c568 GetPropA
0x47c56c UnhookWindowsHookEx
0x47c570 SetPropA
0x47c574 GetClassLongA
0x47c578 CallNextHookEx
0x47c57c SetWindowsHookExA
0x47c580 CreateWindowExA
0x47c584 GetMenuItemID
0x47c588 GetMenuItemCount
0x47c58c RegisterClassA
0x47c590 UnregisterClassA
0x47c594 AdjustWindowRectEx
0x47c598 MapWindowPoints
0x47c59c SendDlgItemMessageA
0x47c5a0 ScrollWindowEx
0x47c5a4 IsDialogMessageA
0x47c5a8 SetWindowTextA
0x47c5ac MoveWindow
0x47c5b0 CheckMenuItem
0x47c5b4 SetMenuItemBitmaps
0x47c5b8 GetMenuState
0x47c5bc GetMenuCheckMarkDimensions
0x47c5c0 GetClassNameA
0x47c5c4 GetDesktopWindow
0x47c5c8 LoadStringA
0x47c5cc GetSysColorBrush
0x47c5d0 PeekMessageA
0x47c5d4 IsIconic
0x47c5d8 SetFocus
0x47c5dc GetActiveWindow
0x47c5e0 GetWindow
0x47c5e4 DestroyAcceleratorTable
0x47c5e8 SetWindowRgn
0x47c5ec GetMessagePos
0x47c5f0 ScreenToClient
0x47c5f4 ChildWindowFromPointEx
0x47c5f8 CopyRect
0x47c5fc LoadBitmapA
0x47c600 WinHelpA
0x47c604 KillTimer
0x47c608 SetTimer
GDI32.dll
0x47c024 GetClipRgn
0x47c028 CreatePolygonRgn
0x47c02c SelectClipRgn
0x47c030 DeleteObject
0x47c034 CreateDIBitmap
0x47c038 GetSystemPaletteEntries
0x47c03c CreatePalette
0x47c040 StretchBlt
0x47c044 SelectPalette
0x47c048 RealizePalette
0x47c04c GetDIBits
0x47c050 GetWindowExtEx
0x47c054 GetViewportOrgEx
0x47c058 GetWindowOrgEx
0x47c05c BeginPath
0x47c060 EndPath
0x47c064 PathToRegion
0x47c068 CreateEllipticRgn
0x47c06c CreateRoundRectRgn
0x47c070 GetTextColor
0x47c074 GetBkMode
0x47c078 GetBkColor
0x47c07c GetROP2
0x47c080 GetStretchBltMode
0x47c084 GetPolyFillMode
0x47c088 CreateCompatibleBitmap
0x47c08c CreateDCA
0x47c090 CreateBitmap
0x47c094 SelectObject
0x47c098 GetObjectA
0x47c09c CreatePen
0x47c0a0 SetStretchBltMode
0x47c0a4 CombineRgn
0x47c0a8 CreateRectRgn
0x47c0ac FillRgn
0x47c0b0 CreateSolidBrush
0x47c0b4 GetStockObject
0x47c0b8 CreateFontIndirectA
0x47c0bc EndPage
0x47c0c0 EndDoc
0x47c0c4 DeleteDC
0x47c0c8 StartDocA
0x47c0cc StartPage
0x47c0d0 BitBlt
0x47c0d4 CreateCompatibleDC
0x47c0d8 Ellipse
0x47c0dc Rectangle
0x47c0e0 LPtoDP
0x47c0e4 DPtoLP
0x47c0e8 GetCurrentObject
0x47c0ec RoundRect
0x47c0f0 GetTextExtentPoint32A
0x47c0f4 GetDeviceCaps
0x47c0f8 SaveDC
0x47c0fc RestoreDC
0x47c100 SetBkMode
0x47c104 SetPolyFillMode
0x47c108 SetROP2
0x47c10c SetTextColor
0x47c110 SetMapMode
0x47c114 SetViewportOrgEx
0x47c118 OffsetViewportOrgEx
0x47c11c SetViewportExtEx
0x47c120 ScaleViewportExtEx
0x47c124 SetWindowOrgEx
0x47c128 SetWindowExtEx
0x47c12c ScaleWindowExtEx
0x47c130 GetClipBox
0x47c134 ExcludeClipRect
0x47c138 MoveToEx
0x47c13c LineTo
0x47c140 CreateRectRgnIndirect
0x47c144 SetBkColor
0x47c148 PatBlt
0x47c14c GetTextMetricsA
0x47c150 Escape
0x47c154 ExtTextOutA
0x47c158 TextOutA
0x47c15c RectVisible
0x47c160 PtVisible
0x47c164 GetViewportExtEx
0x47c168 ExtSelectClipRgn
WINMM.dll
0x47c610 midiStreamRestart
0x47c614 midiStreamClose
0x47c618 midiOutReset
0x47c61c midiStreamStop
0x47c620 midiStreamOut
0x47c624 midiOutPrepareHeader
0x47c628 midiStreamProperty
0x47c62c midiStreamOpen
0x47c630 midiOutUnprepareHeader
0x47c634 waveOutOpen
0x47c638 waveOutGetNumDevs
0x47c63c waveOutClose
0x47c640 waveOutReset
0x47c644 waveOutPause
0x47c648 waveOutWrite
0x47c64c waveOutPrepareHeader
0x47c650 waveOutUnprepareHeader
WINSPOOL.DRV
0x47c658 ClosePrinter
0x47c65c DocumentPropertiesA
0x47c660 OpenPrinterA
ADVAPI32.dll
0x47c000 RegCloseKey
0x47c004 RegOpenKeyExA
0x47c008 RegSetValueExA
0x47c00c RegQueryValueA
0x47c010 RegCreateKeyExA
SHELL32.dll
0x47c390 ShellExecuteA
0x47c394 Shell_NotifyIconA
0x47c398 SHGetSpecialFolderPathA
ole32.dll
0x47c6a4 OleInitialize
0x47c6a8 OleUninitialize
0x47c6ac CLSIDFromString
OLEAUT32.dll
0x47c380 UnRegisterTypeLib
0x47c384 RegisterTypeLib
0x47c388 LoadTypeLib
COMCTL32.dll
0x47c018 ImageList_Destroy
0x47c01c None
WS2_32.dll
0x47c668 recv
0x47c66c getpeername
0x47c670 accept
0x47c674 recvfrom
0x47c678 ioctlsocket
0x47c67c WSAAsyncSelect
0x47c680 closesocket
0x47c684 inet_ntoa
0x47c688 WSACleanup
comdlg32.dll
0x47c690 GetFileTitleA
0x47c694 GetSaveFileNameA
0x47c698 GetOpenFileNameA
0x47c69c ChooseColorA
EAT(Export Address Table) is none