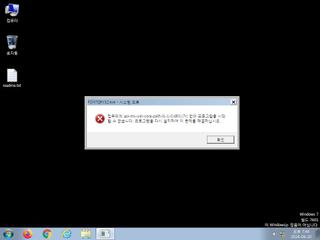
ScreenShot
| Created | 2024.06.20 19:45 | Machine | s1_win7_x6401 |
| Filename | FONTQRY32.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 1 detected (AIDetectMalware) | ||
| md5 | aa20ff0db8694e6fd98760cb00c1bf74 | ||
| sha256 | c090dafc961f938a3d71cce7734366cada620926e99f372dd392f841a0996fef | ||
| ssdeep | 1536:wx3UK2B44dsCTbHPZezjQfHsQVQg7xzOGcwB7q8TUawK75RpIx8xP:i3UK2rs4bvZezjQfHsQVQg7xzOGL7q8p | ||
| imphash | e58d540bae0f571aaaec474cb0272e40 | ||
| impfuzzy | 24:ky915Du9w0TBYmLQAGOLTwYgMLOyWNwyWPWUJiUKMO+YLSyKQaocAD4Tg9bzAOv7:P1snBYPA7viNgV9RYLStQwE1L4IrBSA | ||
Network IP location
Signature (2cnts)
| Level | Description |
|---|---|
| notice | File has been identified by one AntiVirus engine on VirusTotal as malicious |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (6cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x14000ab88 CloseHandle
0x14000ab90 CreateFileW
0x14000ab98 EnumCalendarInfoW
0x14000aba0 FindClose
0x14000aba8 FindFirstFileW
0x14000abb0 FindNextFileW
0x14000abb8 GetCurrentProcess
0x14000abc0 GetCurrentProcessId
0x14000abc8 GetCurrentThreadId
0x14000abd0 GetFileSize
0x14000abd8 GetModuleFileNameW
0x14000abe0 GetModuleHandleA
0x14000abe8 GetModuleHandleW
0x14000abf0 GetProcAddress
0x14000abf8 GetStartupInfoW
0x14000ac00 GetSystemDirectoryW
0x14000ac08 GetSystemTimeAsFileTime
0x14000ac10 InitializeSListHead
0x14000ac18 IsDebuggerPresent
0x14000ac20 IsProcessorFeaturePresent
0x14000ac28 QueryPerformanceCounter
0x14000ac30 ReadFile
0x14000ac38 RtlCaptureContext
0x14000ac40 RtlLookupFunctionEntry
0x14000ac48 RtlVirtualUnwind
0x14000ac50 SetFilePointer
0x14000ac58 SetUnhandledExceptionFilter
0x14000ac60 TerminateProcess
0x14000ac68 UnhandledExceptionFilter
0x14000ac70 VirtualProtect
0x14000ac78 WriteProcessMemory
MSVCP140.dll
0x14000ac88 ?_Xlength_error@std@@YAXPEBD@Z
api-ms-win-core-path-l1-1-0.dll
0x14000ac98 PathCchRemoveFileSpec
VCRUNTIME140.dll
0x14000aca8 _CxxThrowException
0x14000acb0 __C_specific_handler
0x14000acb8 __CxxFrameHandler3
0x14000acc0 __current_exception
0x14000acc8 __current_exception_context
0x14000acd0 __std_exception_copy
0x14000acd8 __std_exception_destroy
0x14000ace0 memcpy
0x14000ace8 memmove
0x14000acf0 memset
api-ms-win-crt-stdio-l1-1-0.dll
0x14000ad00 __p__commode
0x14000ad08 __stdio_common_vswprintf
0x14000ad10 _set_fmode
api-ms-win-crt-runtime-l1-1-0.dll
0x14000ad20 _c_exit
0x14000ad28 _cexit
0x14000ad30 _configure_narrow_argv
0x14000ad38 _crt_atexit
0x14000ad40 _exit
0x14000ad48 _get_narrow_winmain_command_line
0x14000ad50 _initialize_narrow_environment
0x14000ad58 _initialize_onexit_table
0x14000ad60 _initterm
0x14000ad68 _initterm_e
0x14000ad70 _invalid_parameter_noinfo_noreturn
0x14000ad78 _register_onexit_function
0x14000ad80 _register_thread_local_exe_atexit_callback
0x14000ad88 _seh_filter_exe
0x14000ad90 _set_app_type
0x14000ad98 exit
0x14000ada0 terminate
api-ms-win-crt-string-l1-1-0.dll
0x14000adb0 _stricmp
0x14000adb8 strlen
0x14000adc0 wcscat_s
api-ms-win-crt-heap-l1-1-0.dll
0x14000add0 _callnewh
0x14000add8 _set_new_mode
0x14000ade0 free
0x14000ade8 malloc
api-ms-win-crt-math-l1-1-0.dll
0x14000adf8 __setusermatherr
api-ms-win-crt-locale-l1-1-0.dll
0x14000ae08 _configthreadlocale
EAT(Export Address Table) is none
KERNEL32.dll
0x14000ab88 CloseHandle
0x14000ab90 CreateFileW
0x14000ab98 EnumCalendarInfoW
0x14000aba0 FindClose
0x14000aba8 FindFirstFileW
0x14000abb0 FindNextFileW
0x14000abb8 GetCurrentProcess
0x14000abc0 GetCurrentProcessId
0x14000abc8 GetCurrentThreadId
0x14000abd0 GetFileSize
0x14000abd8 GetModuleFileNameW
0x14000abe0 GetModuleHandleA
0x14000abe8 GetModuleHandleW
0x14000abf0 GetProcAddress
0x14000abf8 GetStartupInfoW
0x14000ac00 GetSystemDirectoryW
0x14000ac08 GetSystemTimeAsFileTime
0x14000ac10 InitializeSListHead
0x14000ac18 IsDebuggerPresent
0x14000ac20 IsProcessorFeaturePresent
0x14000ac28 QueryPerformanceCounter
0x14000ac30 ReadFile
0x14000ac38 RtlCaptureContext
0x14000ac40 RtlLookupFunctionEntry
0x14000ac48 RtlVirtualUnwind
0x14000ac50 SetFilePointer
0x14000ac58 SetUnhandledExceptionFilter
0x14000ac60 TerminateProcess
0x14000ac68 UnhandledExceptionFilter
0x14000ac70 VirtualProtect
0x14000ac78 WriteProcessMemory
MSVCP140.dll
0x14000ac88 ?_Xlength_error@std@@YAXPEBD@Z
api-ms-win-core-path-l1-1-0.dll
0x14000ac98 PathCchRemoveFileSpec
VCRUNTIME140.dll
0x14000aca8 _CxxThrowException
0x14000acb0 __C_specific_handler
0x14000acb8 __CxxFrameHandler3
0x14000acc0 __current_exception
0x14000acc8 __current_exception_context
0x14000acd0 __std_exception_copy
0x14000acd8 __std_exception_destroy
0x14000ace0 memcpy
0x14000ace8 memmove
0x14000acf0 memset
api-ms-win-crt-stdio-l1-1-0.dll
0x14000ad00 __p__commode
0x14000ad08 __stdio_common_vswprintf
0x14000ad10 _set_fmode
api-ms-win-crt-runtime-l1-1-0.dll
0x14000ad20 _c_exit
0x14000ad28 _cexit
0x14000ad30 _configure_narrow_argv
0x14000ad38 _crt_atexit
0x14000ad40 _exit
0x14000ad48 _get_narrow_winmain_command_line
0x14000ad50 _initialize_narrow_environment
0x14000ad58 _initialize_onexit_table
0x14000ad60 _initterm
0x14000ad68 _initterm_e
0x14000ad70 _invalid_parameter_noinfo_noreturn
0x14000ad78 _register_onexit_function
0x14000ad80 _register_thread_local_exe_atexit_callback
0x14000ad88 _seh_filter_exe
0x14000ad90 _set_app_type
0x14000ad98 exit
0x14000ada0 terminate
api-ms-win-crt-string-l1-1-0.dll
0x14000adb0 _stricmp
0x14000adb8 strlen
0x14000adc0 wcscat_s
api-ms-win-crt-heap-l1-1-0.dll
0x14000add0 _callnewh
0x14000add8 _set_new_mode
0x14000ade0 free
0x14000ade8 malloc
api-ms-win-crt-math-l1-1-0.dll
0x14000adf8 __setusermatherr
api-ms-win-crt-locale-l1-1-0.dll
0x14000ae08 _configthreadlocale
EAT(Export Address Table) is none