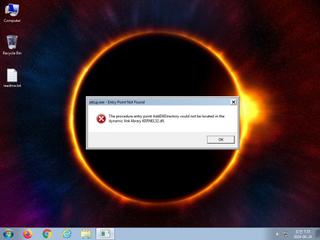
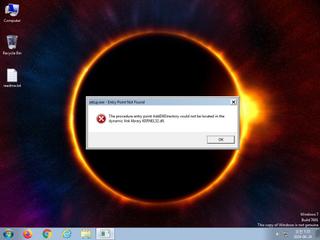
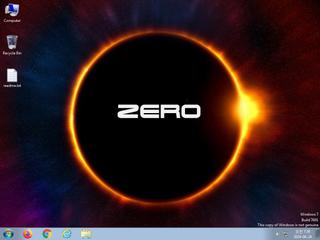
ScreenShot
| Created | 2024.06.24 07:39 | Machine | s1_win7_x6403 |
| Filename | setup.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 13 detected (AIDetectMalware, malicious, high confidence, Attribute, HighConfidence, GenKryptik, GYHY, DropperX, nkirr, Detected, Sabsik, MxResIcn) | ||
| md5 | 0e12bdd2a8200d4c1f368750e2c87bfe | ||
| sha256 | af77c0b6a10ac159b0e3c87c02e16a2b44daab8e67fe097327e90ae48f814403 | ||
| ssdeep | 393216:sYJEy4Te0rrigZ9BCbZPBKAgKBXSTzdOskYXXDeycerzHP+THt+/nDSpQg:sYJcrlZ9BGfg8XIJOkXXPCTV | ||
| imphash | e7d70664c989c41305a1d8de5286f298 | ||
| impfuzzy | 96:hW5+tmXXTSx6nme9Lywp6UB8bLG4xmwJXTXwwJ5i7ieKU4xkCNCP2QLPVd9jSZ:hWTjSxC9LHLejz8EkiCD4 | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| watch | Communicates with host for which no DNS query was performed |
| watch | File has been identified by 13 AntiVirus engines on VirusTotal as malicious |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | ASPack_Zero | ASPack packed file | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x1421e6a28 AcquireSRWLockExclusive
0x1421e6a30 AddDllDirectory
0x1421e6a38 AddVectoredContinueHandler
0x1421e6a40 AreFileApisANSI
0x1421e6a48 AssignProcessToJobObject
0x1421e6a50 Beep
0x1421e6a58 CancelIoEx
0x1421e6a60 CancelSynchronousIo
0x1421e6a68 CloseHandle
0x1421e6a70 CopyFileW
0x1421e6a78 CreateDirectoryExW
0x1421e6a80 CreateDirectoryW
0x1421e6a88 CreateEventA
0x1421e6a90 CreateEventW
0x1421e6a98 CreateFileW
0x1421e6aa0 CreateIoCompletionPort
0x1421e6aa8 CreateJobObjectW
0x1421e6ab0 CreateNamedPipeW
0x1421e6ab8 CreatePipe
0x1421e6ac0 CreateProcessW
0x1421e6ac8 CreateSymbolicLinkW
0x1421e6ad0 CreateThread
0x1421e6ad8 CreateTimerQueue
0x1421e6ae0 CreateTimerQueueTimer
0x1421e6ae8 CreateToolhelp32Snapshot
0x1421e6af0 DefineDosDeviceW
0x1421e6af8 DeleteCriticalSection
0x1421e6b00 DeleteFileW
0x1421e6b08 DeleteTimerQueueEx
0x1421e6b10 DeleteTimerQueueTimer
0x1421e6b18 DeviceIoControl
0x1421e6b20 DuplicateHandle
0x1421e6b28 EnterCriticalSection
0x1421e6b30 ExitThread
0x1421e6b38 FileTimeToLocalFileTime
0x1421e6b40 FileTimeToSystemTime
0x1421e6b48 FindClose
0x1421e6b50 FindCloseChangeNotification
0x1421e6b58 FindFirstChangeNotificationW
0x1421e6b60 FindFirstFileW
0x1421e6b68 FindNextChangeNotification
0x1421e6b70 FindNextFileW
0x1421e6b78 FlushConsoleInputBuffer
0x1421e6b80 FlushFileBuffers
0x1421e6b88 FormatMessageA
0x1421e6b90 FormatMessageW
0x1421e6b98 FreeEnvironmentStringsA
0x1421e6ba0 FreeEnvironmentStringsW
0x1421e6ba8 FreeLibrary
0x1421e6bb0 GenerateConsoleCtrlEvent
0x1421e6bb8 GetACP
0x1421e6bc0 GetActiveProcessorCount
0x1421e6bc8 GetActiveProcessorGroupCount
0x1421e6bd0 GetBinaryTypeW
0x1421e6bd8 GetCPInfo
0x1421e6be0 GetCommandLineW
0x1421e6be8 GetConsoleCP
0x1421e6bf0 GetConsoleMode
0x1421e6bf8 GetConsoleOutputCP
0x1421e6c00 GetConsoleScreenBufferInfo
0x1421e6c08 GetConsoleScreenBufferInfoEx
0x1421e6c10 GetCurrentDirectoryW
0x1421e6c18 GetCurrentProcess
0x1421e6c20 GetCurrentProcessId
0x1421e6c28 GetCurrentThread
0x1421e6c30 GetCurrentThreadId
0x1421e6c38 GetDiskFreeSpaceW
0x1421e6c40 GetEnvironmentStrings
0x1421e6c48 GetEnvironmentStringsW
0x1421e6c50 GetEnvironmentVariableW
0x1421e6c58 GetExitCodeProcess
0x1421e6c60 GetExitCodeThread
0x1421e6c68 GetFileAttributesA
0x1421e6c70 GetFileAttributesExW
0x1421e6c78 GetFileAttributesW
0x1421e6c80 GetFileInformationByHandle
0x1421e6c88 GetFileSizeEx
0x1421e6c90 GetFileTime
0x1421e6c98 GetFileType
0x1421e6ca0 GetFinalPathNameByHandleW
0x1421e6ca8 GetFullPathNameW
0x1421e6cb0 GetLastError
0x1421e6cb8 GetLocalTime
0x1421e6cc0 GetLogicalDrives
0x1421e6cc8 GetLongPathNameW
0x1421e6cd0 GetModuleFileNameW
0x1421e6cd8 GetModuleHandleA
0x1421e6ce0 GetModuleHandleW
0x1421e6ce8 GetNumaHighestNodeNumber
0x1421e6cf0 GetNumaNodeProcessorMask
0x1421e6cf8 GetNumberOfConsoleInputEvents
0x1421e6d00 GetOEMCP
0x1421e6d08 GetOverlappedResult
0x1421e6d10 GetProcAddress
0x1421e6d18 GetProcessAffinityMask
0x1421e6d20 GetProcessId
0x1421e6d28 GetProcessTimes
0x1421e6d30 GetQueuedCompletionStatusEx
0x1421e6d38 GetShortPathNameW
0x1421e6d40 GetStartupInfoA
0x1421e6d48 GetStdHandle
0x1421e6d50 GetSystemDirectoryW
0x1421e6d58 GetSystemInfo
0x1421e6d60 GetSystemTime
0x1421e6d68 GetSystemTimeAdjustment
0x1421e6d70 GetSystemTimeAsFileTime
0x1421e6d78 GetTempFileNameW
0x1421e6d80 GetTempPathW
0x1421e6d88 GetThreadTimes
0x1421e6d90 GetTickCount
0x1421e6d98 GetTickCount64
0x1421e6da0 GetTimeFormatEx
0x1421e6da8 GetTimeFormatW
0x1421e6db0 GetTimeZoneInformation
0x1421e6db8 GetWindowsDirectoryW
0x1421e6dc0 GlobalMemoryStatusEx
0x1421e6dc8 InitializeConditionVariable
0x1421e6dd0 InitializeCriticalSection
0x1421e6dd8 InitializeSRWLock
0x1421e6de0 IsDBCSLeadByteEx
0x1421e6de8 K32EnumProcessModules
0x1421e6df0 K32GetModuleFileNameExW
0x1421e6df8 K32GetModuleInformation
0x1421e6e00 LeaveCriticalSection
0x1421e6e08 LoadLibraryExW
0x1421e6e10 LoadLibraryW
0x1421e6e18 LocalFileTimeToFileTime
0x1421e6e20 LocalFree
0x1421e6e28 LockFileEx
0x1421e6e30 Module32FirstW
0x1421e6e38 Module32NextW
0x1421e6e40 MoveFileExW
0x1421e6e48 MoveFileW
0x1421e6e50 MultiByteToWideChar
0x1421e6e58 OpenProcess
0x1421e6e60 OpenThread
0x1421e6e68 OutputDebugStringA
0x1421e6e70 PeekConsoleInputA
0x1421e6e78 PeekNamedPipe
0x1421e6e80 PostQueuedCompletionStatus
0x1421e6e88 Process32FirstW
0x1421e6e90 Process32NextW
0x1421e6e98 QueryInformationJobObject
0x1421e6ea0 QueryPerformanceCounter
0x1421e6ea8 QueryPerformanceFrequency
0x1421e6eb0 ReadConsoleInputA
0x1421e6eb8 ReadConsoleInputW
0x1421e6ec0 ReadConsoleW
0x1421e6ec8 ReadFile
0x1421e6ed0 ReleaseSRWLockExclusive
0x1421e6ed8 RemoveDirectoryW
0x1421e6ee0 RemoveDllDirectory
0x1421e6ee8 RemoveVectoredContinueHandler
0x1421e6ef0 ResetEvent
0x1421e6ef8 ResumeThread
0x1421e6f00 RtlAddFunctionTable
0x1421e6f08 RtlDeleteFunctionTable
0x1421e6f10 SearchPathW
0x1421e6f18 SetConsoleCP
0x1421e6f20 SetConsoleCtrlHandler
0x1421e6f28 SetConsoleCursorPosition
0x1421e6f30 SetConsoleMode
0x1421e6f38 SetConsoleOutputCP
0x1421e6f40 SetConsoleScreenBufferSize
0x1421e6f48 SetCurrentDirectoryW
0x1421e6f50 SetEndOfFile
0x1421e6f58 SetEnvironmentVariableW
0x1421e6f60 SetEvent
0x1421e6f68 SetFileApisToANSI
0x1421e6f70 SetFileApisToOEM
0x1421e6f78 SetFileAttributesW
0x1421e6f80 SetFileCompletionNotificationModes
0x1421e6f88 SetFilePointerEx
0x1421e6f90 SetFileTime
0x1421e6f98 SetHandleCount
0x1421e6fa0 SetHandleInformation
0x1421e6fa8 SetInformationJobObject
0x1421e6fb0 SetLastError
0x1421e6fb8 SetLocalTime
0x1421e6fc0 SetNamedPipeHandleState
0x1421e6fc8 SetSystemTime
0x1421e6fd0 SetSystemTimeAdjustment
0x1421e6fd8 SetThreadAffinityMask
0x1421e6fe0 SetThreadGroupAffinity
0x1421e6fe8 SetUnhandledExceptionFilter
0x1421e6ff0 SetVolumeLabelW
0x1421e6ff8 Sleep
0x1421e7000 SleepConditionVariableSRW
0x1421e7008 SwitchToThread
0x1421e7010 SystemTimeToFileTime
0x1421e7018 TerminateJobObject
0x1421e7020 TerminateProcess
0x1421e7028 TlsAlloc
0x1421e7030 TlsFree
0x1421e7038 TlsGetValue
0x1421e7040 TlsSetValue
0x1421e7048 TryAcquireSRWLockExclusive
0x1421e7050 UnlockFileEx
0x1421e7058 UnmapViewOfFile
0x1421e7060 VirtualAlloc
0x1421e7068 VirtualAllocExNuma
0x1421e7070 VirtualFree
0x1421e7078 VirtualProtect
0x1421e7080 VirtualQuery
0x1421e7088 WaitForSingleObject
0x1421e7090 WakeAllConditionVariable
0x1421e7098 WakeConditionVariable
0x1421e70a0 WideCharToMultiByte
0x1421e70a8 WriteConsoleW
0x1421e70b0 WriteFile
0x1421e70b8 __C_specific_handler
api-ms-win-crt-heap-l1-1-0.dll
0x1421e70c8 _aligned_free
0x1421e70d0 _aligned_malloc
0x1421e70d8 _set_new_mode
0x1421e70e0 calloc
0x1421e70e8 free
0x1421e70f0 malloc
0x1421e70f8 realloc
api-ms-win-crt-private-l1-1-0.dll
0x1421e7108 memchr
0x1421e7110 memcmp
0x1421e7118 memcpy
0x1421e7120 memmove
0x1421e7128 strrchr
0x1421e7130 strstr
api-ms-win-crt-runtime-l1-1-0.dll
0x1421e7140 __p___argc
0x1421e7148 __p___argv
0x1421e7150 __p___wargv
0x1421e7158 __p__acmdln
0x1421e7160 _assert
0x1421e7168 _beginthreadex
0x1421e7170 _cexit
0x1421e7178 _configure_narrow_argv
0x1421e7180 _configure_wide_argv
0x1421e7188 _crt_at_quick_exit
0x1421e7190 _crt_atexit
0x1421e7198 _errno
0x1421e71a0 _fpreset
0x1421e71a8 _getpid
0x1421e71b0 _initialize_narrow_environment
0x1421e71b8 _initialize_wide_environment
0x1421e71c0 _initterm
0x1421e71c8 _set_app_type
0x1421e71d0 _set_invalid_parameter_handler
0x1421e71d8 _wassert
0x1421e71e0 abort
0x1421e71e8 exit
0x1421e71f0 raise
0x1421e71f8 signal
0x1421e7200 strerror
api-ms-win-crt-stdio-l1-1-0.dll
0x1421e7210 __acrt_iob_func
0x1421e7218 __p__commode
0x1421e7220 __p__fmode
0x1421e7228 __stdio_common_vfprintf
0x1421e7230 __stdio_common_vfwprintf
0x1421e7238 __stdio_common_vswprintf
0x1421e7240 __stdio_common_vswprintf_s
0x1421e7248 _chsize_s
0x1421e7250 _close
0x1421e7258 _creat
0x1421e7260 _dup
0x1421e7268 _dup2
0x1421e7270 _fileno
0x1421e7278 _get_osfhandle
0x1421e7280 _isatty
0x1421e7288 _lseeki64
0x1421e7290 _open_osfhandle
0x1421e7298 _pipe
0x1421e72a0 _read
0x1421e72a8 _setmode
0x1421e72b0 _wfdopen
0x1421e72b8 _write
0x1421e72c0 fclose
0x1421e72c8 feof
0x1421e72d0 fflush
0x1421e72d8 fputc
0x1421e72e0 fputwc
0x1421e72e8 fread
0x1421e72f0 fseek
0x1421e72f8 ftell
0x1421e7300 fwrite
0x1421e7308 getc
0x1421e7310 puts
0x1421e7318 ungetc
api-ms-win-crt-string-l1-1-0.dll
0x1421e7328 _strdup
0x1421e7330 _wcsdup
0x1421e7338 isspace
0x1421e7340 isxdigit
0x1421e7348 mbrlen
0x1421e7350 memset
0x1421e7358 strcmp
0x1421e7360 strcpy
0x1421e7368 strlen
0x1421e7370 strncmp
0x1421e7378 strncpy
0x1421e7380 strtok
0x1421e7388 tolower
0x1421e7390 wcscat
0x1421e7398 wcscmp
0x1421e73a0 wcscpy
0x1421e73a8 wcslen
0x1421e73b0 wcsncmp
SHELL32.dll
0x1421e73c0 CommandLineToArgvW
0x1421e73c8 SHGetFolderPathW
api-ms-win-crt-environment-l1-1-0.dll
0x1421e73d8 __p__environ
0x1421e73e0 __p__wenviron
0x1421e73e8 getenv
api-ms-win-crt-convert-l1-1-0.dll
0x1421e73f8 atof
0x1421e7400 atoi
0x1421e7408 mbrtowc
0x1421e7410 mbstowcs
0x1421e7418 strtol
0x1421e7420 strtoll
0x1421e7428 strtoul
0x1421e7430 strtoull
0x1421e7438 wcrtomb
api-ms-win-crt-locale-l1-1-0.dll
0x1421e7448 _configthreadlocale
0x1421e7450 localeconv
0x1421e7458 setlocale
api-ms-win-crt-math-l1-1-0.dll
0x1421e7468 __setusermatherr
0x1421e7470 acos
0x1421e7478 acosh
0x1421e7480 acoshf
0x1421e7488 asin
0x1421e7490 asinh
0x1421e7498 asinhf
0x1421e74a0 atan
0x1421e74a8 atanh
0x1421e74b0 atanhf
0x1421e74b8 cosh
0x1421e74c0 exp2
0x1421e74c8 expm1
0x1421e74d0 expm1f
0x1421e74d8 log1p
0x1421e74e0 log1pf
0x1421e74e8 log2
0x1421e74f0 sinh
0x1421e74f8 tan
0x1421e7500 tanh
0x1421e7508 tanhf
api-ms-win-crt-time-l1-1-0.dll
0x1421e7518 __daylight
0x1421e7520 __timezone
0x1421e7528 __tzname
0x1421e7530 _ctime64
0x1421e7538 _time64
0x1421e7540 _tzset
0x1421e7548 _utime64
0x1421e7550 clock
ADVAPI32.dll
0x1421e7560 GetUserNameW
ole32.dll
0x1421e7570 CoCreateGuid
RPCRT4.dll
0x1421e7580 RpcStringFreeW
0x1421e7588 UuidToStringW
WS2_32.dll
0x1421e7598 WSACreateEvent
0x1421e75a0 WSAEventSelect
0x1421e75a8 closesocket
0x1421e75b0 recv
0x1421e75b8 select
0x1421e75c0 send
USER32.dll
0x1421e75d0 ClipCursor
0x1421e75d8 ExitWindowsEx
0x1421e75e0 GetClipCursor
0x1421e75e8 GetCursorPos
0x1421e75f0 GetLastInputInfo
0x1421e75f8 KillTimer
0x1421e7600 LoadAcceleratorsW
0x1421e7608 LoadCursorW
0x1421e7610 LoadIconW
0x1421e7618 MessageBeep
0x1421e7620 MessageBoxA
0x1421e7628 MessageBoxW
0x1421e7630 SetCursorPos
0x1421e7638 SetTimer
WINMM.dll
0x1421e7648 timeGetTime
api-ms-win-crt-utility-l1-1-0.dll
0x1421e7658 qsort
api-ms-win-crt-filesystem-l1-1-0.dll
0x1421e7668 _access
0x1421e7670 _chmod
0x1421e7678 _fstat64
0x1421e7680 _lock_file
0x1421e7688 _mkdir
0x1421e7690 _umask
0x1421e7698 _unlink
0x1421e76a0 _unlock_file
0x1421e76a8 _wsplitpath_s
0x1421e76b0 _wstat64
dbghelp.dll
0x1421e76c0 MiniDumpWriteDump
0x1421e76c8 StackWalk64
0x1421e76d0 SymFromAddr
0x1421e76d8 SymFunctionTableAccess64
0x1421e76e0 SymGetLineFromAddr64
0x1421e76e8 SymGetModuleBase64
0x1421e76f0 SymInitialize
ntdll.dll
0x1421e7700 NtQueryObject
GDI32.dll
0x1421e7710 DeleteObject
0x1421e7718 Polygon
EAT(Export Address Table) is none
KERNEL32.dll
0x1421e6a28 AcquireSRWLockExclusive
0x1421e6a30 AddDllDirectory
0x1421e6a38 AddVectoredContinueHandler
0x1421e6a40 AreFileApisANSI
0x1421e6a48 AssignProcessToJobObject
0x1421e6a50 Beep
0x1421e6a58 CancelIoEx
0x1421e6a60 CancelSynchronousIo
0x1421e6a68 CloseHandle
0x1421e6a70 CopyFileW
0x1421e6a78 CreateDirectoryExW
0x1421e6a80 CreateDirectoryW
0x1421e6a88 CreateEventA
0x1421e6a90 CreateEventW
0x1421e6a98 CreateFileW
0x1421e6aa0 CreateIoCompletionPort
0x1421e6aa8 CreateJobObjectW
0x1421e6ab0 CreateNamedPipeW
0x1421e6ab8 CreatePipe
0x1421e6ac0 CreateProcessW
0x1421e6ac8 CreateSymbolicLinkW
0x1421e6ad0 CreateThread
0x1421e6ad8 CreateTimerQueue
0x1421e6ae0 CreateTimerQueueTimer
0x1421e6ae8 CreateToolhelp32Snapshot
0x1421e6af0 DefineDosDeviceW
0x1421e6af8 DeleteCriticalSection
0x1421e6b00 DeleteFileW
0x1421e6b08 DeleteTimerQueueEx
0x1421e6b10 DeleteTimerQueueTimer
0x1421e6b18 DeviceIoControl
0x1421e6b20 DuplicateHandle
0x1421e6b28 EnterCriticalSection
0x1421e6b30 ExitThread
0x1421e6b38 FileTimeToLocalFileTime
0x1421e6b40 FileTimeToSystemTime
0x1421e6b48 FindClose
0x1421e6b50 FindCloseChangeNotification
0x1421e6b58 FindFirstChangeNotificationW
0x1421e6b60 FindFirstFileW
0x1421e6b68 FindNextChangeNotification
0x1421e6b70 FindNextFileW
0x1421e6b78 FlushConsoleInputBuffer
0x1421e6b80 FlushFileBuffers
0x1421e6b88 FormatMessageA
0x1421e6b90 FormatMessageW
0x1421e6b98 FreeEnvironmentStringsA
0x1421e6ba0 FreeEnvironmentStringsW
0x1421e6ba8 FreeLibrary
0x1421e6bb0 GenerateConsoleCtrlEvent
0x1421e6bb8 GetACP
0x1421e6bc0 GetActiveProcessorCount
0x1421e6bc8 GetActiveProcessorGroupCount
0x1421e6bd0 GetBinaryTypeW
0x1421e6bd8 GetCPInfo
0x1421e6be0 GetCommandLineW
0x1421e6be8 GetConsoleCP
0x1421e6bf0 GetConsoleMode
0x1421e6bf8 GetConsoleOutputCP
0x1421e6c00 GetConsoleScreenBufferInfo
0x1421e6c08 GetConsoleScreenBufferInfoEx
0x1421e6c10 GetCurrentDirectoryW
0x1421e6c18 GetCurrentProcess
0x1421e6c20 GetCurrentProcessId
0x1421e6c28 GetCurrentThread
0x1421e6c30 GetCurrentThreadId
0x1421e6c38 GetDiskFreeSpaceW
0x1421e6c40 GetEnvironmentStrings
0x1421e6c48 GetEnvironmentStringsW
0x1421e6c50 GetEnvironmentVariableW
0x1421e6c58 GetExitCodeProcess
0x1421e6c60 GetExitCodeThread
0x1421e6c68 GetFileAttributesA
0x1421e6c70 GetFileAttributesExW
0x1421e6c78 GetFileAttributesW
0x1421e6c80 GetFileInformationByHandle
0x1421e6c88 GetFileSizeEx
0x1421e6c90 GetFileTime
0x1421e6c98 GetFileType
0x1421e6ca0 GetFinalPathNameByHandleW
0x1421e6ca8 GetFullPathNameW
0x1421e6cb0 GetLastError
0x1421e6cb8 GetLocalTime
0x1421e6cc0 GetLogicalDrives
0x1421e6cc8 GetLongPathNameW
0x1421e6cd0 GetModuleFileNameW
0x1421e6cd8 GetModuleHandleA
0x1421e6ce0 GetModuleHandleW
0x1421e6ce8 GetNumaHighestNodeNumber
0x1421e6cf0 GetNumaNodeProcessorMask
0x1421e6cf8 GetNumberOfConsoleInputEvents
0x1421e6d00 GetOEMCP
0x1421e6d08 GetOverlappedResult
0x1421e6d10 GetProcAddress
0x1421e6d18 GetProcessAffinityMask
0x1421e6d20 GetProcessId
0x1421e6d28 GetProcessTimes
0x1421e6d30 GetQueuedCompletionStatusEx
0x1421e6d38 GetShortPathNameW
0x1421e6d40 GetStartupInfoA
0x1421e6d48 GetStdHandle
0x1421e6d50 GetSystemDirectoryW
0x1421e6d58 GetSystemInfo
0x1421e6d60 GetSystemTime
0x1421e6d68 GetSystemTimeAdjustment
0x1421e6d70 GetSystemTimeAsFileTime
0x1421e6d78 GetTempFileNameW
0x1421e6d80 GetTempPathW
0x1421e6d88 GetThreadTimes
0x1421e6d90 GetTickCount
0x1421e6d98 GetTickCount64
0x1421e6da0 GetTimeFormatEx
0x1421e6da8 GetTimeFormatW
0x1421e6db0 GetTimeZoneInformation
0x1421e6db8 GetWindowsDirectoryW
0x1421e6dc0 GlobalMemoryStatusEx
0x1421e6dc8 InitializeConditionVariable
0x1421e6dd0 InitializeCriticalSection
0x1421e6dd8 InitializeSRWLock
0x1421e6de0 IsDBCSLeadByteEx
0x1421e6de8 K32EnumProcessModules
0x1421e6df0 K32GetModuleFileNameExW
0x1421e6df8 K32GetModuleInformation
0x1421e6e00 LeaveCriticalSection
0x1421e6e08 LoadLibraryExW
0x1421e6e10 LoadLibraryW
0x1421e6e18 LocalFileTimeToFileTime
0x1421e6e20 LocalFree
0x1421e6e28 LockFileEx
0x1421e6e30 Module32FirstW
0x1421e6e38 Module32NextW
0x1421e6e40 MoveFileExW
0x1421e6e48 MoveFileW
0x1421e6e50 MultiByteToWideChar
0x1421e6e58 OpenProcess
0x1421e6e60 OpenThread
0x1421e6e68 OutputDebugStringA
0x1421e6e70 PeekConsoleInputA
0x1421e6e78 PeekNamedPipe
0x1421e6e80 PostQueuedCompletionStatus
0x1421e6e88 Process32FirstW
0x1421e6e90 Process32NextW
0x1421e6e98 QueryInformationJobObject
0x1421e6ea0 QueryPerformanceCounter
0x1421e6ea8 QueryPerformanceFrequency
0x1421e6eb0 ReadConsoleInputA
0x1421e6eb8 ReadConsoleInputW
0x1421e6ec0 ReadConsoleW
0x1421e6ec8 ReadFile
0x1421e6ed0 ReleaseSRWLockExclusive
0x1421e6ed8 RemoveDirectoryW
0x1421e6ee0 RemoveDllDirectory
0x1421e6ee8 RemoveVectoredContinueHandler
0x1421e6ef0 ResetEvent
0x1421e6ef8 ResumeThread
0x1421e6f00 RtlAddFunctionTable
0x1421e6f08 RtlDeleteFunctionTable
0x1421e6f10 SearchPathW
0x1421e6f18 SetConsoleCP
0x1421e6f20 SetConsoleCtrlHandler
0x1421e6f28 SetConsoleCursorPosition
0x1421e6f30 SetConsoleMode
0x1421e6f38 SetConsoleOutputCP
0x1421e6f40 SetConsoleScreenBufferSize
0x1421e6f48 SetCurrentDirectoryW
0x1421e6f50 SetEndOfFile
0x1421e6f58 SetEnvironmentVariableW
0x1421e6f60 SetEvent
0x1421e6f68 SetFileApisToANSI
0x1421e6f70 SetFileApisToOEM
0x1421e6f78 SetFileAttributesW
0x1421e6f80 SetFileCompletionNotificationModes
0x1421e6f88 SetFilePointerEx
0x1421e6f90 SetFileTime
0x1421e6f98 SetHandleCount
0x1421e6fa0 SetHandleInformation
0x1421e6fa8 SetInformationJobObject
0x1421e6fb0 SetLastError
0x1421e6fb8 SetLocalTime
0x1421e6fc0 SetNamedPipeHandleState
0x1421e6fc8 SetSystemTime
0x1421e6fd0 SetSystemTimeAdjustment
0x1421e6fd8 SetThreadAffinityMask
0x1421e6fe0 SetThreadGroupAffinity
0x1421e6fe8 SetUnhandledExceptionFilter
0x1421e6ff0 SetVolumeLabelW
0x1421e6ff8 Sleep
0x1421e7000 SleepConditionVariableSRW
0x1421e7008 SwitchToThread
0x1421e7010 SystemTimeToFileTime
0x1421e7018 TerminateJobObject
0x1421e7020 TerminateProcess
0x1421e7028 TlsAlloc
0x1421e7030 TlsFree
0x1421e7038 TlsGetValue
0x1421e7040 TlsSetValue
0x1421e7048 TryAcquireSRWLockExclusive
0x1421e7050 UnlockFileEx
0x1421e7058 UnmapViewOfFile
0x1421e7060 VirtualAlloc
0x1421e7068 VirtualAllocExNuma
0x1421e7070 VirtualFree
0x1421e7078 VirtualProtect
0x1421e7080 VirtualQuery
0x1421e7088 WaitForSingleObject
0x1421e7090 WakeAllConditionVariable
0x1421e7098 WakeConditionVariable
0x1421e70a0 WideCharToMultiByte
0x1421e70a8 WriteConsoleW
0x1421e70b0 WriteFile
0x1421e70b8 __C_specific_handler
api-ms-win-crt-heap-l1-1-0.dll
0x1421e70c8 _aligned_free
0x1421e70d0 _aligned_malloc
0x1421e70d8 _set_new_mode
0x1421e70e0 calloc
0x1421e70e8 free
0x1421e70f0 malloc
0x1421e70f8 realloc
api-ms-win-crt-private-l1-1-0.dll
0x1421e7108 memchr
0x1421e7110 memcmp
0x1421e7118 memcpy
0x1421e7120 memmove
0x1421e7128 strrchr
0x1421e7130 strstr
api-ms-win-crt-runtime-l1-1-0.dll
0x1421e7140 __p___argc
0x1421e7148 __p___argv
0x1421e7150 __p___wargv
0x1421e7158 __p__acmdln
0x1421e7160 _assert
0x1421e7168 _beginthreadex
0x1421e7170 _cexit
0x1421e7178 _configure_narrow_argv
0x1421e7180 _configure_wide_argv
0x1421e7188 _crt_at_quick_exit
0x1421e7190 _crt_atexit
0x1421e7198 _errno
0x1421e71a0 _fpreset
0x1421e71a8 _getpid
0x1421e71b0 _initialize_narrow_environment
0x1421e71b8 _initialize_wide_environment
0x1421e71c0 _initterm
0x1421e71c8 _set_app_type
0x1421e71d0 _set_invalid_parameter_handler
0x1421e71d8 _wassert
0x1421e71e0 abort
0x1421e71e8 exit
0x1421e71f0 raise
0x1421e71f8 signal
0x1421e7200 strerror
api-ms-win-crt-stdio-l1-1-0.dll
0x1421e7210 __acrt_iob_func
0x1421e7218 __p__commode
0x1421e7220 __p__fmode
0x1421e7228 __stdio_common_vfprintf
0x1421e7230 __stdio_common_vfwprintf
0x1421e7238 __stdio_common_vswprintf
0x1421e7240 __stdio_common_vswprintf_s
0x1421e7248 _chsize_s
0x1421e7250 _close
0x1421e7258 _creat
0x1421e7260 _dup
0x1421e7268 _dup2
0x1421e7270 _fileno
0x1421e7278 _get_osfhandle
0x1421e7280 _isatty
0x1421e7288 _lseeki64
0x1421e7290 _open_osfhandle
0x1421e7298 _pipe
0x1421e72a0 _read
0x1421e72a8 _setmode
0x1421e72b0 _wfdopen
0x1421e72b8 _write
0x1421e72c0 fclose
0x1421e72c8 feof
0x1421e72d0 fflush
0x1421e72d8 fputc
0x1421e72e0 fputwc
0x1421e72e8 fread
0x1421e72f0 fseek
0x1421e72f8 ftell
0x1421e7300 fwrite
0x1421e7308 getc
0x1421e7310 puts
0x1421e7318 ungetc
api-ms-win-crt-string-l1-1-0.dll
0x1421e7328 _strdup
0x1421e7330 _wcsdup
0x1421e7338 isspace
0x1421e7340 isxdigit
0x1421e7348 mbrlen
0x1421e7350 memset
0x1421e7358 strcmp
0x1421e7360 strcpy
0x1421e7368 strlen
0x1421e7370 strncmp
0x1421e7378 strncpy
0x1421e7380 strtok
0x1421e7388 tolower
0x1421e7390 wcscat
0x1421e7398 wcscmp
0x1421e73a0 wcscpy
0x1421e73a8 wcslen
0x1421e73b0 wcsncmp
SHELL32.dll
0x1421e73c0 CommandLineToArgvW
0x1421e73c8 SHGetFolderPathW
api-ms-win-crt-environment-l1-1-0.dll
0x1421e73d8 __p__environ
0x1421e73e0 __p__wenviron
0x1421e73e8 getenv
api-ms-win-crt-convert-l1-1-0.dll
0x1421e73f8 atof
0x1421e7400 atoi
0x1421e7408 mbrtowc
0x1421e7410 mbstowcs
0x1421e7418 strtol
0x1421e7420 strtoll
0x1421e7428 strtoul
0x1421e7430 strtoull
0x1421e7438 wcrtomb
api-ms-win-crt-locale-l1-1-0.dll
0x1421e7448 _configthreadlocale
0x1421e7450 localeconv
0x1421e7458 setlocale
api-ms-win-crt-math-l1-1-0.dll
0x1421e7468 __setusermatherr
0x1421e7470 acos
0x1421e7478 acosh
0x1421e7480 acoshf
0x1421e7488 asin
0x1421e7490 asinh
0x1421e7498 asinhf
0x1421e74a0 atan
0x1421e74a8 atanh
0x1421e74b0 atanhf
0x1421e74b8 cosh
0x1421e74c0 exp2
0x1421e74c8 expm1
0x1421e74d0 expm1f
0x1421e74d8 log1p
0x1421e74e0 log1pf
0x1421e74e8 log2
0x1421e74f0 sinh
0x1421e74f8 tan
0x1421e7500 tanh
0x1421e7508 tanhf
api-ms-win-crt-time-l1-1-0.dll
0x1421e7518 __daylight
0x1421e7520 __timezone
0x1421e7528 __tzname
0x1421e7530 _ctime64
0x1421e7538 _time64
0x1421e7540 _tzset
0x1421e7548 _utime64
0x1421e7550 clock
ADVAPI32.dll
0x1421e7560 GetUserNameW
ole32.dll
0x1421e7570 CoCreateGuid
RPCRT4.dll
0x1421e7580 RpcStringFreeW
0x1421e7588 UuidToStringW
WS2_32.dll
0x1421e7598 WSACreateEvent
0x1421e75a0 WSAEventSelect
0x1421e75a8 closesocket
0x1421e75b0 recv
0x1421e75b8 select
0x1421e75c0 send
USER32.dll
0x1421e75d0 ClipCursor
0x1421e75d8 ExitWindowsEx
0x1421e75e0 GetClipCursor
0x1421e75e8 GetCursorPos
0x1421e75f0 GetLastInputInfo
0x1421e75f8 KillTimer
0x1421e7600 LoadAcceleratorsW
0x1421e7608 LoadCursorW
0x1421e7610 LoadIconW
0x1421e7618 MessageBeep
0x1421e7620 MessageBoxA
0x1421e7628 MessageBoxW
0x1421e7630 SetCursorPos
0x1421e7638 SetTimer
WINMM.dll
0x1421e7648 timeGetTime
api-ms-win-crt-utility-l1-1-0.dll
0x1421e7658 qsort
api-ms-win-crt-filesystem-l1-1-0.dll
0x1421e7668 _access
0x1421e7670 _chmod
0x1421e7678 _fstat64
0x1421e7680 _lock_file
0x1421e7688 _mkdir
0x1421e7690 _umask
0x1421e7698 _unlink
0x1421e76a0 _unlock_file
0x1421e76a8 _wsplitpath_s
0x1421e76b0 _wstat64
dbghelp.dll
0x1421e76c0 MiniDumpWriteDump
0x1421e76c8 StackWalk64
0x1421e76d0 SymFromAddr
0x1421e76d8 SymFunctionTableAccess64
0x1421e76e0 SymGetLineFromAddr64
0x1421e76e8 SymGetModuleBase64
0x1421e76f0 SymInitialize
ntdll.dll
0x1421e7700 NtQueryObject
GDI32.dll
0x1421e7710 DeleteObject
0x1421e7718 Polygon
EAT(Export Address Table) is none