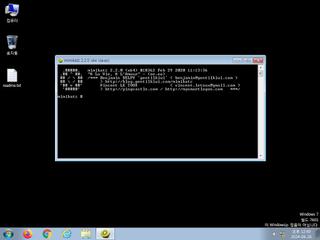
ScreenShot
| Created | 2024.06.28 12:42 | Machine | s1_win7_x6401 |
| Filename | mimikatz.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 65 detected (Common, Windows, Hacktool, Mimikatz, Malicious, score, S13719268, HTool, Marte, Unsafe, uwccg, HacktoolX, Tool, hdegnn, CLASSIC, AGEN, HKTL, MIMIKATZ64, Apteryx, Detected, ai score=100, Malware@#kkm08qefpx7y, WRYM, R290617, TrojanPSW, Neshta, FileInfector, HackingTool, abngN9Oo928, Static AI, Malicious PE, susgen, NetWalker, confidence, 100%) | ||
| md5 | e930b05efe23891d19bc354a4209be3e | ||
| sha256 | 92804faaab2175dc501d73e814663058c78c0a042675a8937266357bcfb96c50 | ||
| ssdeep | 24576:zLrEjqXg4NiXcmHVjIhlIyEeQ37uV3Ugmf4Yl0Q0V7FCR:zLZo1jFyjFJhmf4YlHWk | ||
| imphash | 1355327f6ca3430b3ddbe6e0acda71ea | ||
| impfuzzy | 192:lUQG9i0nAAoMCpdCuGIO3uWGrYGXTf1iyUiWpF/fBaGZ1vBIHdi62G:l/muMCJ9HTapF/r1vBedidG | ||
Network IP location
Signature (3cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 65 AntiVirus engines on VirusTotal as malicious |
| info | Checks amount of memory in system |
| info | Command line console output was observed |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
ADVAPI32.dll
0x1400c4000 CryptSetHashParam
0x1400c4008 CryptGetHashParam
0x1400c4010 CryptExportKey
0x1400c4018 CryptAcquireContextW
0x1400c4020 CryptSetKeyParam
0x1400c4028 CryptGetKeyParam
0x1400c4030 CryptReleaseContext
0x1400c4038 CryptDuplicateKey
0x1400c4040 CryptAcquireContextA
0x1400c4048 CryptGetProvParam
0x1400c4050 CryptImportKey
0x1400c4058 SystemFunction007
0x1400c4060 CryptEncrypt
0x1400c4068 CryptCreateHash
0x1400c4070 CryptGenKey
0x1400c4078 CryptDestroyKey
0x1400c4080 CryptDecrypt
0x1400c4088 CryptDestroyHash
0x1400c4090 CryptHashData
0x1400c4098 CopySid
0x1400c40a0 GetLengthSid
0x1400c40a8 LsaQueryInformationPolicy
0x1400c40b0 LsaOpenPolicy
0x1400c40b8 LsaClose
0x1400c40c0 CreateWellKnownSid
0x1400c40c8 CreateProcessWithLogonW
0x1400c40d0 CreateProcessAsUserW
0x1400c40d8 RegQueryValueExW
0x1400c40e0 RegQueryInfoKeyW
0x1400c40e8 RegEnumValueW
0x1400c40f0 RegOpenKeyExW
0x1400c40f8 RegEnumKeyExW
0x1400c4100 RegCloseKey
0x1400c4108 RegSetValueExW
0x1400c4110 SystemFunction032
0x1400c4118 ConvertSidToStringSidW
0x1400c4120 CreateServiceW
0x1400c4128 CloseServiceHandle
0x1400c4130 DeleteService
0x1400c4138 OpenSCManagerW
0x1400c4140 SetServiceObjectSecurity
0x1400c4148 OpenServiceW
0x1400c4150 BuildSecurityDescriptorW
0x1400c4158 QueryServiceObjectSecurity
0x1400c4160 StartServiceW
0x1400c4168 AllocateAndInitializeSid
0x1400c4170 QueryServiceStatusEx
0x1400c4178 FreeSid
0x1400c4180 ControlService
0x1400c4188 IsTextUnicode
0x1400c4190 OpenProcessToken
0x1400c4198 GetTokenInformation
0x1400c41a0 LookupAccountNameW
0x1400c41a8 LookupAccountSidW
0x1400c41b0 DuplicateTokenEx
0x1400c41b8 CheckTokenMembership
0x1400c41c0 CryptSetProvParam
0x1400c41c8 CryptEnumProvidersW
0x1400c41d0 ConvertStringSidToSidW
0x1400c41d8 LsaFreeMemory
0x1400c41e0 GetSidSubAuthority
0x1400c41e8 GetSidSubAuthorityCount
0x1400c41f0 IsValidSid
0x1400c41f8 SetThreadToken
0x1400c4200 CryptEnumProviderTypesW
0x1400c4208 SystemFunction006
0x1400c4210 CryptGetUserKey
0x1400c4218 OpenEventLogW
0x1400c4220 GetNumberOfEventLogRecords
0x1400c4228 ClearEventLogW
0x1400c4230 SystemFunction001
0x1400c4238 CryptDeriveKey
0x1400c4240 SystemFunction005
0x1400c4248 LsaQueryTrustedDomainInfoByName
0x1400c4250 CryptSignHashW
0x1400c4258 LsaOpenSecret
0x1400c4260 LsaQuerySecret
0x1400c4268 SystemFunction013
0x1400c4270 LsaRetrievePrivateData
0x1400c4278 LsaEnumerateTrustedDomainsEx
0x1400c4280 LookupPrivilegeValueW
0x1400c4288 StartServiceCtrlDispatcherW
0x1400c4290 SetServiceStatus
0x1400c4298 RegisterServiceCtrlHandlerW
0x1400c42a0 LookupPrivilegeNameW
0x1400c42a8 OpenThreadToken
0x1400c42b0 CredFree
0x1400c42b8 CredEnumerateW
0x1400c42c0 SystemFunction025
0x1400c42c8 ConvertStringSecurityDescriptorToSecurityDescriptorW
0x1400c42d0 SystemFunction024
0x1400c42d8 CredIsMarshaledCredentialW
0x1400c42e0 CredUnmarshalCredentialW
Cabinet.dll
0x1400c43c8 None
0x1400c43d0 None
0x1400c43d8 None
0x1400c43e0 None
CRYPT32.dll
0x1400c42f0 CertFindCertificateInStore
0x1400c42f8 CertEnumSystemStore
0x1400c4300 CertEnumCertificatesInStore
0x1400c4308 CertAddCertificateContextToStore
0x1400c4310 CryptDecodeObjectEx
0x1400c4318 CertAddEncodedCertificateToStore
0x1400c4320 CertOpenStore
0x1400c4328 CertFreeCertificateContext
0x1400c4330 CertCloseStore
0x1400c4338 CertSetCertificateContextProperty
0x1400c4340 PFXExportCertStoreEx
0x1400c4348 CryptUnprotectData
0x1400c4350 CryptBinaryToStringW
0x1400c4358 CryptBinaryToStringA
0x1400c4360 CryptStringToBinaryW
0x1400c4368 CryptExportPublicKeyInfo
0x1400c4370 CryptFindOIDInfo
0x1400c4378 CryptAcquireCertificatePrivateKey
0x1400c4380 CertNameToStrW
0x1400c4388 CryptStringToBinaryA
0x1400c4390 CertGetCertificateContextProperty
0x1400c4398 CryptSignAndEncodeCertificate
0x1400c43a0 CryptEncodeObject
0x1400c43a8 CryptProtectData
0x1400c43b0 CryptQueryObject
0x1400c43b8 CertGetNameStringW
cryptdll.dll
0x1400c4e98 MD5Init
0x1400c4ea0 MD5Update
0x1400c4ea8 MD5Final
0x1400c4eb0 CDLocateCSystem
0x1400c4eb8 CDGenerateRandomBits
0x1400c4ec0 CDLocateCheckSum
DNSAPI.dll
0x1400c43f0 DnsFree
0x1400c43f8 DnsQuery_A
FLTLIB.DLL
0x1400c4408 FilterFindFirst
0x1400c4410 FilterFindNext
NETAPI32.dll
0x1400c48b8 NetServerGetInfo
0x1400c48c0 NetStatisticsGet
0x1400c48c8 NetShareEnum
0x1400c48d0 DsEnumerateDomainTrustsW
0x1400c48d8 DsGetDcNameW
0x1400c48e0 NetApiBufferFree
0x1400c48e8 NetRemoteTOD
0x1400c48f0 NetSessionEnum
0x1400c48f8 NetWkstaUserEnum
ole32.dll
0x1400c52b0 CoInitializeEx
0x1400c52b8 CoUninitialize
0x1400c52c0 CoCreateInstance
OLEAUT32.dll
0x1400c4908 VariantInit
0x1400c4910 SysFreeString
0x1400c4918 SysAllocString
RPCRT4.dll
0x1400c4928 RpcMgmtEpEltInqNextW
0x1400c4930 RpcMgmtEpEltInqBegin
0x1400c4938 I_RpcGetCurrentCallHandle
0x1400c4940 NdrClientCall2
0x1400c4948 RpcMgmtEpEltInqDone
0x1400c4950 RpcBindingFromStringBindingW
0x1400c4958 RpcStringBindingComposeW
0x1400c4960 MesEncodeIncrementalHandleCreate
0x1400c4968 RpcBindingSetAuthInfoExW
0x1400c4970 RpcBindingInqAuthClientW
0x1400c4978 RpcBindingSetOption
0x1400c4980 RpcImpersonateClient
0x1400c4988 RpcBindingFree
0x1400c4990 RpcStringFreeW
0x1400c4998 RpcRevertToSelf
0x1400c49a0 MesDecodeIncrementalHandleCreate
0x1400c49a8 MesHandleFree
0x1400c49b0 MesIncrementalHandleReset
0x1400c49b8 NdrMesTypeDecode2
0x1400c49c0 NdrMesTypeAlignSize2
0x1400c49c8 NdrMesTypeFree2
0x1400c49d0 NdrMesTypeEncode2
0x1400c49d8 RpcServerUnregisterIfEx
0x1400c49e0 I_RpcBindingInqSecurityContext
0x1400c49e8 RpcServerInqBindings
0x1400c49f0 RpcServerListen
0x1400c49f8 RpcMgmtWaitServerListen
0x1400c4a00 RpcEpRegisterW
0x1400c4a08 RpcMgmtStopServerListening
0x1400c4a10 RpcBindingToStringBindingW
0x1400c4a18 RpcServerRegisterIf2
0x1400c4a20 RpcServerRegisterAuthInfoW
0x1400c4a28 RpcBindingVectorFree
0x1400c4a30 UuidToStringW
0x1400c4a38 RpcServerUseProtseqEpW
0x1400c4a40 RpcEpUnregister
0x1400c4a48 NdrServerCall2
0x1400c4a50 RpcEpResolveBinding
0x1400c4a58 UuidCreate
SHLWAPI.dll
0x1400c4b58 PathIsDirectoryW
0x1400c4b60 PathCanonicalizeW
0x1400c4b68 PathCombineW
0x1400c4b70 PathFindFileNameW
0x1400c4b78 PathIsRelativeW
SAMLIB.dll
0x1400c4a68 SamEnumerateGroupsInDomain
0x1400c4a70 SamiChangePasswordUser
0x1400c4a78 SamSetInformationUser
0x1400c4a80 SamGetGroupsForUser
0x1400c4a88 SamConnect
0x1400c4a90 SamGetMembersInGroup
0x1400c4a98 SamRidToSid
0x1400c4aa0 SamGetMembersInAlias
0x1400c4aa8 SamEnumerateAliasesInDomain
0x1400c4ab0 SamGetAliasMembership
0x1400c4ab8 SamOpenGroup
0x1400c4ac0 SamQueryInformationUser
0x1400c4ac8 SamCloseHandle
0x1400c4ad0 SamEnumerateDomainsInSamServer
0x1400c4ad8 SamFreeMemory
0x1400c4ae0 SamEnumerateUsersInDomain
0x1400c4ae8 SamOpenUser
0x1400c4af0 SamLookupDomainInSamServer
0x1400c4af8 SamLookupNamesInDomain
0x1400c4b00 SamLookupIdsInDomain
0x1400c4b08 SamOpenDomain
0x1400c4b10 SamOpenAlias
Secur32.dll
0x1400c4b88 QueryContextAttributesW
0x1400c4b90 FreeContextBuffer
0x1400c4b98 LsaConnectUntrusted
0x1400c4ba0 LsaLookupAuthenticationPackage
0x1400c4ba8 LsaDeregisterLogonProcess
0x1400c4bb0 DeleteSecurityContext
0x1400c4bb8 LsaCallAuthenticationPackage
0x1400c4bc0 FreeCredentialsHandle
0x1400c4bc8 EnumerateSecurityPackagesW
0x1400c4bd0 AcquireCredentialsHandleW
0x1400c4bd8 InitializeSecurityContextW
0x1400c4be0 LsaFreeReturnBuffer
SHELL32.dll
0x1400c4b48 CommandLineToArgvW
USER32.dll
0x1400c4bf0 IsCharAlphaNumericW
0x1400c4bf8 GetKeyboardLayout
0x1400c4c00 DispatchMessageW
0x1400c4c08 DefWindowProcW
0x1400c4c10 SetClipboardViewer
0x1400c4c18 SendMessageW
0x1400c4c20 GetClipboardSequenceNumber
0x1400c4c28 OpenClipboard
0x1400c4c30 CreateWindowExW
0x1400c4c38 ChangeClipboardChain
0x1400c4c40 GetClipboardData
0x1400c4c48 RegisterClassExW
0x1400c4c50 TranslateMessage
0x1400c4c58 EnumClipboardFormats
0x1400c4c60 PostMessageW
0x1400c4c68 UnregisterClassW
0x1400c4c70 GetMessageW
0x1400c4c78 CloseClipboard
0x1400c4c80 DestroyWindow
USERENV.dll
0x1400c4c90 CreateEnvironmentBlock
0x1400c4c98 DestroyEnvironmentBlock
VERSION.dll
0x1400c4ca8 VerQueryValueW
0x1400c4cb0 GetFileVersionInfoSizeW
0x1400c4cb8 GetFileVersionInfoW
HID.DLL
0x1400c4420 HidD_GetFeature
0x1400c4428 HidD_GetPreparsedData
0x1400c4430 HidD_GetHidGuid
0x1400c4438 HidD_GetAttributes
0x1400c4440 HidD_FreePreparsedData
0x1400c4448 HidP_GetCaps
0x1400c4450 HidD_SetFeature
SETUPAPI.dll
0x1400c4b20 SetupDiGetDeviceInterfaceDetailW
0x1400c4b28 SetupDiEnumDeviceInterfaces
0x1400c4b30 SetupDiGetClassDevsW
0x1400c4b38 SetupDiDestroyDeviceInfoList
WinSCard.dll
0x1400c4e18 SCardControl
0x1400c4e20 SCardTransmit
0x1400c4e28 SCardDisconnect
0x1400c4e30 SCardGetAttrib
0x1400c4e38 SCardEstablishContext
0x1400c4e40 SCardFreeMemory
0x1400c4e48 SCardListReadersW
0x1400c4e50 SCardReleaseContext
0x1400c4e58 SCardGetCardTypeProviderNameW
0x1400c4e60 SCardListCardsW
0x1400c4e68 SCardConnectW
WINSTA.dll
0x1400c4cc8 WinStationCloseServer
0x1400c4cd0 WinStationOpenServerW
0x1400c4cd8 WinStationFreeMemory
0x1400c4ce0 WinStationConnectW
0x1400c4ce8 WinStationQueryInformationW
0x1400c4cf0 WinStationEnumerateW
WLDAP32.dll
0x1400c4d00 None
0x1400c4d08 None
0x1400c4d10 None
0x1400c4d18 None
0x1400c4d20 None
0x1400c4d28 None
0x1400c4d30 None
0x1400c4d38 None
0x1400c4d40 None
0x1400c4d48 None
0x1400c4d50 None
0x1400c4d58 None
0x1400c4d60 None
0x1400c4d68 None
0x1400c4d70 None
0x1400c4d78 None
0x1400c4d80 None
0x1400c4d88 None
0x1400c4d90 None
0x1400c4d98 None
0x1400c4da0 None
0x1400c4da8 None
0x1400c4db0 None
0x1400c4db8 None
0x1400c4dc0 None
0x1400c4dc8 None
0x1400c4dd0 None
0x1400c4dd8 None
0x1400c4de0 None
0x1400c4de8 None
0x1400c4df0 None
0x1400c4df8 None
0x1400c4e00 None
0x1400c4e08 None
advapi32.dll
0x1400c4e78 A_SHAFinal
0x1400c4e80 A_SHAInit
0x1400c4e88 A_SHAUpdate
msasn1.dll
0x1400c4ed0 ASN1_CreateModule
0x1400c4ed8 ASN1BERDotVal2Eoid
0x1400c4ee0 ASN1_CloseEncoder
0x1400c4ee8 ASN1_CreateDecoder
0x1400c4ef0 ASN1_FreeEncoded
0x1400c4ef8 ASN1_CloseModule
0x1400c4f00 ASN1_CreateEncoder
0x1400c4f08 ASN1_CloseDecoder
ntdll.dll
0x1400c51a8 RtlFreeAnsiString
0x1400c51b0 RtlDowncaseUnicodeString
0x1400c51b8 RtlFreeUnicodeString
0x1400c51c0 RtlInitUnicodeString
0x1400c51c8 RtlEqualUnicodeString
0x1400c51d0 NtQueryObject
0x1400c51d8 RtlCompressBuffer
0x1400c51e0 RtlGetCompressionWorkSpaceSize
0x1400c51e8 NtQuerySystemInformation
0x1400c51f0 RtlGetCurrentPeb
0x1400c51f8 NtQueryInformationProcess
0x1400c5200 RtlUnicodeStringToAnsiString
0x1400c5208 RtlGUIDFromString
0x1400c5210 RtlStringFromGUID
0x1400c5218 NtCompareTokens
0x1400c5220 RtlGetNtVersionNumbers
0x1400c5228 RtlEqualString
0x1400c5230 RtlUpcaseUnicodeString
0x1400c5238 RtlAppendUnicodeStringToString
0x1400c5240 RtlAnsiStringToUnicodeString
0x1400c5248 RtlFreeOemString
0x1400c5250 RtlUpcaseUnicodeStringToOemString
0x1400c5258 NtResumeProcess
0x1400c5260 RtlAdjustPrivilege
0x1400c5268 NtSuspendProcess
0x1400c5270 NtTerminateProcess
0x1400c5278 NtQuerySystemEnvironmentValueEx
0x1400c5280 RtlCreateUserThread
0x1400c5288 NtSetSystemEnvironmentValueEx
0x1400c5290 NtEnumerateSystemEnvironmentValuesEx
0x1400c5298 RtlIpv4AddressToStringW
0x1400c52a0 RtlIpv6AddressToStringW
netapi32.dll
0x1400c5188 I_NetServerAuthenticate2
0x1400c5190 I_NetServerTrustPasswordsGet
0x1400c5198 I_NetServerReqChallenge
KERNEL32.dll
0x1400c4460 GetFullPathNameA
0x1400c4468 GetFullPathNameW
0x1400c4470 GetTimeFormatW
0x1400c4478 WideCharToMultiByte
0x1400c4480 GetSystemTimeAsFileTime
0x1400c4488 SystemTimeToFileTime
0x1400c4490 GetDateFormatW
0x1400c4498 PurgeComm
0x1400c44a0 ClearCommError
0x1400c44a8 RtlVirtualUnwind
0x1400c44b0 SetFilePointerEx
0x1400c44b8 GetProcessId
0x1400c44c0 CreateRemoteThread
0x1400c44c8 WaitForSingleObject
0x1400c44d0 SetLastError
0x1400c44d8 CreateProcessW
0x1400c44e0 SetConsoleOutputCP
0x1400c44e8 GetConsoleOutputCP
0x1400c44f0 CreateFileMappingW
0x1400c44f8 UnmapViewOfFile
0x1400c4500 MapViewOfFile
0x1400c4508 WriteProcessMemory
0x1400c4510 VirtualAllocEx
0x1400c4518 VirtualProtectEx
0x1400c4520 VirtualAlloc
0x1400c4528 ReadProcessMemory
0x1400c4530 VirtualFreeEx
0x1400c4538 VirtualQueryEx
0x1400c4540 VirtualFree
0x1400c4548 VirtualQuery
0x1400c4550 GetComputerNameExW
0x1400c4558 DeviceIoControl
0x1400c4560 DuplicateHandle
0x1400c4568 OpenProcess
0x1400c4570 GetCurrentProcess
0x1400c4578 ExpandEnvironmentStringsW
0x1400c4580 FindNextFileW
0x1400c4588 FindClose
0x1400c4590 GetCurrentDirectoryW
0x1400c4598 GetFileSizeEx
0x1400c45a0 FlushFileBuffers
0x1400c45a8 GetFileAttributesW
0x1400c45b0 FindFirstFileW
0x1400c45b8 lstrlenW
0x1400c45c0 DeleteFileA
0x1400c45c8 GetTempPathA
0x1400c45d0 GetFileInformationByHandle
0x1400c45d8 FileTimeToLocalFileTime
0x1400c45e0 GetCurrentDirectoryA
0x1400c45e8 GetTempFileNameA
0x1400c45f0 SetFilePointer
0x1400c45f8 CreateFileA
0x1400c4600 FileTimeToDosDateTime
0x1400c4608 CreateThread
0x1400c4610 LocalFree
0x1400c4618 CloseHandle
0x1400c4620 LocalAlloc
0x1400c4628 HeapReAlloc
0x1400c4630 CreateFileW
0x1400c4638 ReadFile
0x1400c4640 TerminateThread
0x1400c4648 WriteFile
0x1400c4650 FileTimeToSystemTime
0x1400c4658 Sleep
0x1400c4660 VirtualProtect
0x1400c4668 CreateMutexW
0x1400c4670 HeapCompact
0x1400c4678 SetEndOfFile
0x1400c4680 FreeLibrary
0x1400c4688 HeapAlloc
0x1400c4690 QueryPerformanceCounter
0x1400c4698 HeapFree
0x1400c46a0 UnlockFile
0x1400c46a8 FlushViewOfFile
0x1400c46b0 LockFile
0x1400c46b8 WaitForSingleObjectEx
0x1400c46c0 OutputDebugStringW
0x1400c46c8 GetTickCount
0x1400c46d0 UnlockFileEx
0x1400c46d8 GetProcessHeap
0x1400c46e0 FormatMessageA
0x1400c46e8 LoadLibraryW
0x1400c46f0 GetFileSize
0x1400c46f8 FormatMessageW
0x1400c4700 GetVersionExW
0x1400c4708 HeapDestroy
0x1400c4710 GetFileAttributesA
0x1400c4718 HeapCreate
0x1400c4720 HeapValidate
0x1400c4728 MultiByteToWideChar
0x1400c4730 GetTempPathW
0x1400c4738 GetProcAddress
0x1400c4740 HeapSize
0x1400c4748 LockFileEx
0x1400c4750 GetDiskFreeSpaceW
0x1400c4758 LoadLibraryA
0x1400c4760 CreateFileMappingA
0x1400c4768 GetDiskFreeSpaceA
0x1400c4770 GetSystemInfo
0x1400c4778 GetFileAttributesExW
0x1400c4780 OutputDebugStringA
0x1400c4788 GetVersionExA
0x1400c4790 DeleteFileW
0x1400c4798 GetCurrentProcessId
0x1400c47a0 GetSystemTime
0x1400c47a8 AreFileApisANSI
0x1400c47b0 ExitProcess
0x1400c47b8 RaiseException
0x1400c47c0 SetConsoleCtrlHandler
0x1400c47c8 SetConsoleTitleW
0x1400c47d0 lstrlenA
0x1400c47d8 GlobalSize
0x1400c47e0 GetModuleHandleW
0x1400c47e8 SetHandleInformation
0x1400c47f0 CreatePipe
0x1400c47f8 InitializeCriticalSection
0x1400c4800 LeaveCriticalSection
0x1400c4808 EnterCriticalSection
0x1400c4810 DeleteCriticalSection
0x1400c4818 SetEvent
0x1400c4820 CreateEventW
0x1400c4828 GetSystemDirectoryW
0x1400c4830 GetCurrentThreadId
0x1400c4838 SetUnhandledExceptionFilter
0x1400c4840 UnhandledExceptionFilter
0x1400c4848 TerminateProcess
0x1400c4850 RtlCaptureContext
0x1400c4858 GetLastError
0x1400c4860 RtlLookupFunctionEntry
0x1400c4868 SetConsoleCursorPosition
0x1400c4870 GetTimeZoneInformation
0x1400c4878 GetStdHandle
0x1400c4880 FillConsoleOutputCharacterW
0x1400c4888 GetConsoleScreenBufferInfo
0x1400c4890 GetComputerNameW
0x1400c4898 ProcessIdToSessionId
0x1400c48a0 GetCurrentThread
0x1400c48a8 SetCurrentDirectoryW
msvcrt.dll
0x1400c4f18 isspace
0x1400c4f20 isdigit
0x1400c4f28 calloc
0x1400c4f30 mbtowc
0x1400c4f38 _lseeki64
0x1400c4f40 _write
0x1400c4f48 isleadbyte
0x1400c4f50 isxdigit
0x1400c4f58 localeconv
0x1400c4f60 _snprintf
0x1400c4f68 _itoa
0x1400c4f70 wctomb
0x1400c4f78 ferror
0x1400c4f80 iswctype
0x1400c4f88 wcstombs
0x1400c4f90 _isatty
0x1400c4f98 ungetc
0x1400c4fa0 ?terminate@@YAXXZ
0x1400c4fa8 __badioinfo
0x1400c4fb0 __pioinfo
0x1400c4fb8 _read
0x1400c4fc0 log
0x1400c4fc8 __mb_cur_max
0x1400c4fd0 vwprintf
0x1400c4fd8 __set_app_type
0x1400c4fe0 _fmode
0x1400c4fe8 _commode
0x1400c4ff0 _errno
0x1400c4ff8 free
0x1400c5000 _wcsdup
0x1400c5008 _vsnprintf
0x1400c5010 strrchr
0x1400c5018 _wcsicmp
0x1400c5020 vfwprintf
0x1400c5028 _vscwprintf
0x1400c5030 fflush
0x1400c5038 _wfopen
0x1400c5040 wprintf
0x1400c5048 _fileno
0x1400c5050 _iob
0x1400c5058 memcmp
0x1400c5060 _setmode
0x1400c5068 fclose
0x1400c5070 _stricmp
0x1400c5078 wcsrchr
0x1400c5080 wcschr
0x1400c5088 strtoul
0x1400c5090 _wcsnicmp
0x1400c5098 wcsstr
0x1400c50a0 _vscprintf
0x1400c50a8 memmove
0x1400c50b0 strncmp
0x1400c50b8 malloc
0x1400c50c0 _msize
0x1400c50c8 strcspn
0x1400c50d0 realloc
0x1400c50d8 fgetws
0x1400c50e0 wcstoul
0x1400c50e8 wcstol
0x1400c50f0 towupper
0x1400c50f8 _wpgmptr
0x1400c5100 strstr
0x1400c5108 strchr
0x1400c5110 _wcstoui64
0x1400c5118 wcsncmp
0x1400c5120 getchar
0x1400c5128 memcpy
0x1400c5130 memset
0x1400c5138 __C_specific_handler
0x1400c5140 __wgetmainargs
0x1400c5148 _XcptFilter
0x1400c5150 _exit
0x1400c5158 _cexit
0x1400c5160 exit
0x1400c5168 _initterm
0x1400c5170 _amsg_exit
0x1400c5178 __setusermatherr
EAT(Export Address Table) is none
ADVAPI32.dll
0x1400c4000 CryptSetHashParam
0x1400c4008 CryptGetHashParam
0x1400c4010 CryptExportKey
0x1400c4018 CryptAcquireContextW
0x1400c4020 CryptSetKeyParam
0x1400c4028 CryptGetKeyParam
0x1400c4030 CryptReleaseContext
0x1400c4038 CryptDuplicateKey
0x1400c4040 CryptAcquireContextA
0x1400c4048 CryptGetProvParam
0x1400c4050 CryptImportKey
0x1400c4058 SystemFunction007
0x1400c4060 CryptEncrypt
0x1400c4068 CryptCreateHash
0x1400c4070 CryptGenKey
0x1400c4078 CryptDestroyKey
0x1400c4080 CryptDecrypt
0x1400c4088 CryptDestroyHash
0x1400c4090 CryptHashData
0x1400c4098 CopySid
0x1400c40a0 GetLengthSid
0x1400c40a8 LsaQueryInformationPolicy
0x1400c40b0 LsaOpenPolicy
0x1400c40b8 LsaClose
0x1400c40c0 CreateWellKnownSid
0x1400c40c8 CreateProcessWithLogonW
0x1400c40d0 CreateProcessAsUserW
0x1400c40d8 RegQueryValueExW
0x1400c40e0 RegQueryInfoKeyW
0x1400c40e8 RegEnumValueW
0x1400c40f0 RegOpenKeyExW
0x1400c40f8 RegEnumKeyExW
0x1400c4100 RegCloseKey
0x1400c4108 RegSetValueExW
0x1400c4110 SystemFunction032
0x1400c4118 ConvertSidToStringSidW
0x1400c4120 CreateServiceW
0x1400c4128 CloseServiceHandle
0x1400c4130 DeleteService
0x1400c4138 OpenSCManagerW
0x1400c4140 SetServiceObjectSecurity
0x1400c4148 OpenServiceW
0x1400c4150 BuildSecurityDescriptorW
0x1400c4158 QueryServiceObjectSecurity
0x1400c4160 StartServiceW
0x1400c4168 AllocateAndInitializeSid
0x1400c4170 QueryServiceStatusEx
0x1400c4178 FreeSid
0x1400c4180 ControlService
0x1400c4188 IsTextUnicode
0x1400c4190 OpenProcessToken
0x1400c4198 GetTokenInformation
0x1400c41a0 LookupAccountNameW
0x1400c41a8 LookupAccountSidW
0x1400c41b0 DuplicateTokenEx
0x1400c41b8 CheckTokenMembership
0x1400c41c0 CryptSetProvParam
0x1400c41c8 CryptEnumProvidersW
0x1400c41d0 ConvertStringSidToSidW
0x1400c41d8 LsaFreeMemory
0x1400c41e0 GetSidSubAuthority
0x1400c41e8 GetSidSubAuthorityCount
0x1400c41f0 IsValidSid
0x1400c41f8 SetThreadToken
0x1400c4200 CryptEnumProviderTypesW
0x1400c4208 SystemFunction006
0x1400c4210 CryptGetUserKey
0x1400c4218 OpenEventLogW
0x1400c4220 GetNumberOfEventLogRecords
0x1400c4228 ClearEventLogW
0x1400c4230 SystemFunction001
0x1400c4238 CryptDeriveKey
0x1400c4240 SystemFunction005
0x1400c4248 LsaQueryTrustedDomainInfoByName
0x1400c4250 CryptSignHashW
0x1400c4258 LsaOpenSecret
0x1400c4260 LsaQuerySecret
0x1400c4268 SystemFunction013
0x1400c4270 LsaRetrievePrivateData
0x1400c4278 LsaEnumerateTrustedDomainsEx
0x1400c4280 LookupPrivilegeValueW
0x1400c4288 StartServiceCtrlDispatcherW
0x1400c4290 SetServiceStatus
0x1400c4298 RegisterServiceCtrlHandlerW
0x1400c42a0 LookupPrivilegeNameW
0x1400c42a8 OpenThreadToken
0x1400c42b0 CredFree
0x1400c42b8 CredEnumerateW
0x1400c42c0 SystemFunction025
0x1400c42c8 ConvertStringSecurityDescriptorToSecurityDescriptorW
0x1400c42d0 SystemFunction024
0x1400c42d8 CredIsMarshaledCredentialW
0x1400c42e0 CredUnmarshalCredentialW
Cabinet.dll
0x1400c43c8 None
0x1400c43d0 None
0x1400c43d8 None
0x1400c43e0 None
CRYPT32.dll
0x1400c42f0 CertFindCertificateInStore
0x1400c42f8 CertEnumSystemStore
0x1400c4300 CertEnumCertificatesInStore
0x1400c4308 CertAddCertificateContextToStore
0x1400c4310 CryptDecodeObjectEx
0x1400c4318 CertAddEncodedCertificateToStore
0x1400c4320 CertOpenStore
0x1400c4328 CertFreeCertificateContext
0x1400c4330 CertCloseStore
0x1400c4338 CertSetCertificateContextProperty
0x1400c4340 PFXExportCertStoreEx
0x1400c4348 CryptUnprotectData
0x1400c4350 CryptBinaryToStringW
0x1400c4358 CryptBinaryToStringA
0x1400c4360 CryptStringToBinaryW
0x1400c4368 CryptExportPublicKeyInfo
0x1400c4370 CryptFindOIDInfo
0x1400c4378 CryptAcquireCertificatePrivateKey
0x1400c4380 CertNameToStrW
0x1400c4388 CryptStringToBinaryA
0x1400c4390 CertGetCertificateContextProperty
0x1400c4398 CryptSignAndEncodeCertificate
0x1400c43a0 CryptEncodeObject
0x1400c43a8 CryptProtectData
0x1400c43b0 CryptQueryObject
0x1400c43b8 CertGetNameStringW
cryptdll.dll
0x1400c4e98 MD5Init
0x1400c4ea0 MD5Update
0x1400c4ea8 MD5Final
0x1400c4eb0 CDLocateCSystem
0x1400c4eb8 CDGenerateRandomBits
0x1400c4ec0 CDLocateCheckSum
DNSAPI.dll
0x1400c43f0 DnsFree
0x1400c43f8 DnsQuery_A
FLTLIB.DLL
0x1400c4408 FilterFindFirst
0x1400c4410 FilterFindNext
NETAPI32.dll
0x1400c48b8 NetServerGetInfo
0x1400c48c0 NetStatisticsGet
0x1400c48c8 NetShareEnum
0x1400c48d0 DsEnumerateDomainTrustsW
0x1400c48d8 DsGetDcNameW
0x1400c48e0 NetApiBufferFree
0x1400c48e8 NetRemoteTOD
0x1400c48f0 NetSessionEnum
0x1400c48f8 NetWkstaUserEnum
ole32.dll
0x1400c52b0 CoInitializeEx
0x1400c52b8 CoUninitialize
0x1400c52c0 CoCreateInstance
OLEAUT32.dll
0x1400c4908 VariantInit
0x1400c4910 SysFreeString
0x1400c4918 SysAllocString
RPCRT4.dll
0x1400c4928 RpcMgmtEpEltInqNextW
0x1400c4930 RpcMgmtEpEltInqBegin
0x1400c4938 I_RpcGetCurrentCallHandle
0x1400c4940 NdrClientCall2
0x1400c4948 RpcMgmtEpEltInqDone
0x1400c4950 RpcBindingFromStringBindingW
0x1400c4958 RpcStringBindingComposeW
0x1400c4960 MesEncodeIncrementalHandleCreate
0x1400c4968 RpcBindingSetAuthInfoExW
0x1400c4970 RpcBindingInqAuthClientW
0x1400c4978 RpcBindingSetOption
0x1400c4980 RpcImpersonateClient
0x1400c4988 RpcBindingFree
0x1400c4990 RpcStringFreeW
0x1400c4998 RpcRevertToSelf
0x1400c49a0 MesDecodeIncrementalHandleCreate
0x1400c49a8 MesHandleFree
0x1400c49b0 MesIncrementalHandleReset
0x1400c49b8 NdrMesTypeDecode2
0x1400c49c0 NdrMesTypeAlignSize2
0x1400c49c8 NdrMesTypeFree2
0x1400c49d0 NdrMesTypeEncode2
0x1400c49d8 RpcServerUnregisterIfEx
0x1400c49e0 I_RpcBindingInqSecurityContext
0x1400c49e8 RpcServerInqBindings
0x1400c49f0 RpcServerListen
0x1400c49f8 RpcMgmtWaitServerListen
0x1400c4a00 RpcEpRegisterW
0x1400c4a08 RpcMgmtStopServerListening
0x1400c4a10 RpcBindingToStringBindingW
0x1400c4a18 RpcServerRegisterIf2
0x1400c4a20 RpcServerRegisterAuthInfoW
0x1400c4a28 RpcBindingVectorFree
0x1400c4a30 UuidToStringW
0x1400c4a38 RpcServerUseProtseqEpW
0x1400c4a40 RpcEpUnregister
0x1400c4a48 NdrServerCall2
0x1400c4a50 RpcEpResolveBinding
0x1400c4a58 UuidCreate
SHLWAPI.dll
0x1400c4b58 PathIsDirectoryW
0x1400c4b60 PathCanonicalizeW
0x1400c4b68 PathCombineW
0x1400c4b70 PathFindFileNameW
0x1400c4b78 PathIsRelativeW
SAMLIB.dll
0x1400c4a68 SamEnumerateGroupsInDomain
0x1400c4a70 SamiChangePasswordUser
0x1400c4a78 SamSetInformationUser
0x1400c4a80 SamGetGroupsForUser
0x1400c4a88 SamConnect
0x1400c4a90 SamGetMembersInGroup
0x1400c4a98 SamRidToSid
0x1400c4aa0 SamGetMembersInAlias
0x1400c4aa8 SamEnumerateAliasesInDomain
0x1400c4ab0 SamGetAliasMembership
0x1400c4ab8 SamOpenGroup
0x1400c4ac0 SamQueryInformationUser
0x1400c4ac8 SamCloseHandle
0x1400c4ad0 SamEnumerateDomainsInSamServer
0x1400c4ad8 SamFreeMemory
0x1400c4ae0 SamEnumerateUsersInDomain
0x1400c4ae8 SamOpenUser
0x1400c4af0 SamLookupDomainInSamServer
0x1400c4af8 SamLookupNamesInDomain
0x1400c4b00 SamLookupIdsInDomain
0x1400c4b08 SamOpenDomain
0x1400c4b10 SamOpenAlias
Secur32.dll
0x1400c4b88 QueryContextAttributesW
0x1400c4b90 FreeContextBuffer
0x1400c4b98 LsaConnectUntrusted
0x1400c4ba0 LsaLookupAuthenticationPackage
0x1400c4ba8 LsaDeregisterLogonProcess
0x1400c4bb0 DeleteSecurityContext
0x1400c4bb8 LsaCallAuthenticationPackage
0x1400c4bc0 FreeCredentialsHandle
0x1400c4bc8 EnumerateSecurityPackagesW
0x1400c4bd0 AcquireCredentialsHandleW
0x1400c4bd8 InitializeSecurityContextW
0x1400c4be0 LsaFreeReturnBuffer
SHELL32.dll
0x1400c4b48 CommandLineToArgvW
USER32.dll
0x1400c4bf0 IsCharAlphaNumericW
0x1400c4bf8 GetKeyboardLayout
0x1400c4c00 DispatchMessageW
0x1400c4c08 DefWindowProcW
0x1400c4c10 SetClipboardViewer
0x1400c4c18 SendMessageW
0x1400c4c20 GetClipboardSequenceNumber
0x1400c4c28 OpenClipboard
0x1400c4c30 CreateWindowExW
0x1400c4c38 ChangeClipboardChain
0x1400c4c40 GetClipboardData
0x1400c4c48 RegisterClassExW
0x1400c4c50 TranslateMessage
0x1400c4c58 EnumClipboardFormats
0x1400c4c60 PostMessageW
0x1400c4c68 UnregisterClassW
0x1400c4c70 GetMessageW
0x1400c4c78 CloseClipboard
0x1400c4c80 DestroyWindow
USERENV.dll
0x1400c4c90 CreateEnvironmentBlock
0x1400c4c98 DestroyEnvironmentBlock
VERSION.dll
0x1400c4ca8 VerQueryValueW
0x1400c4cb0 GetFileVersionInfoSizeW
0x1400c4cb8 GetFileVersionInfoW
HID.DLL
0x1400c4420 HidD_GetFeature
0x1400c4428 HidD_GetPreparsedData
0x1400c4430 HidD_GetHidGuid
0x1400c4438 HidD_GetAttributes
0x1400c4440 HidD_FreePreparsedData
0x1400c4448 HidP_GetCaps
0x1400c4450 HidD_SetFeature
SETUPAPI.dll
0x1400c4b20 SetupDiGetDeviceInterfaceDetailW
0x1400c4b28 SetupDiEnumDeviceInterfaces
0x1400c4b30 SetupDiGetClassDevsW
0x1400c4b38 SetupDiDestroyDeviceInfoList
WinSCard.dll
0x1400c4e18 SCardControl
0x1400c4e20 SCardTransmit
0x1400c4e28 SCardDisconnect
0x1400c4e30 SCardGetAttrib
0x1400c4e38 SCardEstablishContext
0x1400c4e40 SCardFreeMemory
0x1400c4e48 SCardListReadersW
0x1400c4e50 SCardReleaseContext
0x1400c4e58 SCardGetCardTypeProviderNameW
0x1400c4e60 SCardListCardsW
0x1400c4e68 SCardConnectW
WINSTA.dll
0x1400c4cc8 WinStationCloseServer
0x1400c4cd0 WinStationOpenServerW
0x1400c4cd8 WinStationFreeMemory
0x1400c4ce0 WinStationConnectW
0x1400c4ce8 WinStationQueryInformationW
0x1400c4cf0 WinStationEnumerateW
WLDAP32.dll
0x1400c4d00 None
0x1400c4d08 None
0x1400c4d10 None
0x1400c4d18 None
0x1400c4d20 None
0x1400c4d28 None
0x1400c4d30 None
0x1400c4d38 None
0x1400c4d40 None
0x1400c4d48 None
0x1400c4d50 None
0x1400c4d58 None
0x1400c4d60 None
0x1400c4d68 None
0x1400c4d70 None
0x1400c4d78 None
0x1400c4d80 None
0x1400c4d88 None
0x1400c4d90 None
0x1400c4d98 None
0x1400c4da0 None
0x1400c4da8 None
0x1400c4db0 None
0x1400c4db8 None
0x1400c4dc0 None
0x1400c4dc8 None
0x1400c4dd0 None
0x1400c4dd8 None
0x1400c4de0 None
0x1400c4de8 None
0x1400c4df0 None
0x1400c4df8 None
0x1400c4e00 None
0x1400c4e08 None
advapi32.dll
0x1400c4e78 A_SHAFinal
0x1400c4e80 A_SHAInit
0x1400c4e88 A_SHAUpdate
msasn1.dll
0x1400c4ed0 ASN1_CreateModule
0x1400c4ed8 ASN1BERDotVal2Eoid
0x1400c4ee0 ASN1_CloseEncoder
0x1400c4ee8 ASN1_CreateDecoder
0x1400c4ef0 ASN1_FreeEncoded
0x1400c4ef8 ASN1_CloseModule
0x1400c4f00 ASN1_CreateEncoder
0x1400c4f08 ASN1_CloseDecoder
ntdll.dll
0x1400c51a8 RtlFreeAnsiString
0x1400c51b0 RtlDowncaseUnicodeString
0x1400c51b8 RtlFreeUnicodeString
0x1400c51c0 RtlInitUnicodeString
0x1400c51c8 RtlEqualUnicodeString
0x1400c51d0 NtQueryObject
0x1400c51d8 RtlCompressBuffer
0x1400c51e0 RtlGetCompressionWorkSpaceSize
0x1400c51e8 NtQuerySystemInformation
0x1400c51f0 RtlGetCurrentPeb
0x1400c51f8 NtQueryInformationProcess
0x1400c5200 RtlUnicodeStringToAnsiString
0x1400c5208 RtlGUIDFromString
0x1400c5210 RtlStringFromGUID
0x1400c5218 NtCompareTokens
0x1400c5220 RtlGetNtVersionNumbers
0x1400c5228 RtlEqualString
0x1400c5230 RtlUpcaseUnicodeString
0x1400c5238 RtlAppendUnicodeStringToString
0x1400c5240 RtlAnsiStringToUnicodeString
0x1400c5248 RtlFreeOemString
0x1400c5250 RtlUpcaseUnicodeStringToOemString
0x1400c5258 NtResumeProcess
0x1400c5260 RtlAdjustPrivilege
0x1400c5268 NtSuspendProcess
0x1400c5270 NtTerminateProcess
0x1400c5278 NtQuerySystemEnvironmentValueEx
0x1400c5280 RtlCreateUserThread
0x1400c5288 NtSetSystemEnvironmentValueEx
0x1400c5290 NtEnumerateSystemEnvironmentValuesEx
0x1400c5298 RtlIpv4AddressToStringW
0x1400c52a0 RtlIpv6AddressToStringW
netapi32.dll
0x1400c5188 I_NetServerAuthenticate2
0x1400c5190 I_NetServerTrustPasswordsGet
0x1400c5198 I_NetServerReqChallenge
KERNEL32.dll
0x1400c4460 GetFullPathNameA
0x1400c4468 GetFullPathNameW
0x1400c4470 GetTimeFormatW
0x1400c4478 WideCharToMultiByte
0x1400c4480 GetSystemTimeAsFileTime
0x1400c4488 SystemTimeToFileTime
0x1400c4490 GetDateFormatW
0x1400c4498 PurgeComm
0x1400c44a0 ClearCommError
0x1400c44a8 RtlVirtualUnwind
0x1400c44b0 SetFilePointerEx
0x1400c44b8 GetProcessId
0x1400c44c0 CreateRemoteThread
0x1400c44c8 WaitForSingleObject
0x1400c44d0 SetLastError
0x1400c44d8 CreateProcessW
0x1400c44e0 SetConsoleOutputCP
0x1400c44e8 GetConsoleOutputCP
0x1400c44f0 CreateFileMappingW
0x1400c44f8 UnmapViewOfFile
0x1400c4500 MapViewOfFile
0x1400c4508 WriteProcessMemory
0x1400c4510 VirtualAllocEx
0x1400c4518 VirtualProtectEx
0x1400c4520 VirtualAlloc
0x1400c4528 ReadProcessMemory
0x1400c4530 VirtualFreeEx
0x1400c4538 VirtualQueryEx
0x1400c4540 VirtualFree
0x1400c4548 VirtualQuery
0x1400c4550 GetComputerNameExW
0x1400c4558 DeviceIoControl
0x1400c4560 DuplicateHandle
0x1400c4568 OpenProcess
0x1400c4570 GetCurrentProcess
0x1400c4578 ExpandEnvironmentStringsW
0x1400c4580 FindNextFileW
0x1400c4588 FindClose
0x1400c4590 GetCurrentDirectoryW
0x1400c4598 GetFileSizeEx
0x1400c45a0 FlushFileBuffers
0x1400c45a8 GetFileAttributesW
0x1400c45b0 FindFirstFileW
0x1400c45b8 lstrlenW
0x1400c45c0 DeleteFileA
0x1400c45c8 GetTempPathA
0x1400c45d0 GetFileInformationByHandle
0x1400c45d8 FileTimeToLocalFileTime
0x1400c45e0 GetCurrentDirectoryA
0x1400c45e8 GetTempFileNameA
0x1400c45f0 SetFilePointer
0x1400c45f8 CreateFileA
0x1400c4600 FileTimeToDosDateTime
0x1400c4608 CreateThread
0x1400c4610 LocalFree
0x1400c4618 CloseHandle
0x1400c4620 LocalAlloc
0x1400c4628 HeapReAlloc
0x1400c4630 CreateFileW
0x1400c4638 ReadFile
0x1400c4640 TerminateThread
0x1400c4648 WriteFile
0x1400c4650 FileTimeToSystemTime
0x1400c4658 Sleep
0x1400c4660 VirtualProtect
0x1400c4668 CreateMutexW
0x1400c4670 HeapCompact
0x1400c4678 SetEndOfFile
0x1400c4680 FreeLibrary
0x1400c4688 HeapAlloc
0x1400c4690 QueryPerformanceCounter
0x1400c4698 HeapFree
0x1400c46a0 UnlockFile
0x1400c46a8 FlushViewOfFile
0x1400c46b0 LockFile
0x1400c46b8 WaitForSingleObjectEx
0x1400c46c0 OutputDebugStringW
0x1400c46c8 GetTickCount
0x1400c46d0 UnlockFileEx
0x1400c46d8 GetProcessHeap
0x1400c46e0 FormatMessageA
0x1400c46e8 LoadLibraryW
0x1400c46f0 GetFileSize
0x1400c46f8 FormatMessageW
0x1400c4700 GetVersionExW
0x1400c4708 HeapDestroy
0x1400c4710 GetFileAttributesA
0x1400c4718 HeapCreate
0x1400c4720 HeapValidate
0x1400c4728 MultiByteToWideChar
0x1400c4730 GetTempPathW
0x1400c4738 GetProcAddress
0x1400c4740 HeapSize
0x1400c4748 LockFileEx
0x1400c4750 GetDiskFreeSpaceW
0x1400c4758 LoadLibraryA
0x1400c4760 CreateFileMappingA
0x1400c4768 GetDiskFreeSpaceA
0x1400c4770 GetSystemInfo
0x1400c4778 GetFileAttributesExW
0x1400c4780 OutputDebugStringA
0x1400c4788 GetVersionExA
0x1400c4790 DeleteFileW
0x1400c4798 GetCurrentProcessId
0x1400c47a0 GetSystemTime
0x1400c47a8 AreFileApisANSI
0x1400c47b0 ExitProcess
0x1400c47b8 RaiseException
0x1400c47c0 SetConsoleCtrlHandler
0x1400c47c8 SetConsoleTitleW
0x1400c47d0 lstrlenA
0x1400c47d8 GlobalSize
0x1400c47e0 GetModuleHandleW
0x1400c47e8 SetHandleInformation
0x1400c47f0 CreatePipe
0x1400c47f8 InitializeCriticalSection
0x1400c4800 LeaveCriticalSection
0x1400c4808 EnterCriticalSection
0x1400c4810 DeleteCriticalSection
0x1400c4818 SetEvent
0x1400c4820 CreateEventW
0x1400c4828 GetSystemDirectoryW
0x1400c4830 GetCurrentThreadId
0x1400c4838 SetUnhandledExceptionFilter
0x1400c4840 UnhandledExceptionFilter
0x1400c4848 TerminateProcess
0x1400c4850 RtlCaptureContext
0x1400c4858 GetLastError
0x1400c4860 RtlLookupFunctionEntry
0x1400c4868 SetConsoleCursorPosition
0x1400c4870 GetTimeZoneInformation
0x1400c4878 GetStdHandle
0x1400c4880 FillConsoleOutputCharacterW
0x1400c4888 GetConsoleScreenBufferInfo
0x1400c4890 GetComputerNameW
0x1400c4898 ProcessIdToSessionId
0x1400c48a0 GetCurrentThread
0x1400c48a8 SetCurrentDirectoryW
msvcrt.dll
0x1400c4f18 isspace
0x1400c4f20 isdigit
0x1400c4f28 calloc
0x1400c4f30 mbtowc
0x1400c4f38 _lseeki64
0x1400c4f40 _write
0x1400c4f48 isleadbyte
0x1400c4f50 isxdigit
0x1400c4f58 localeconv
0x1400c4f60 _snprintf
0x1400c4f68 _itoa
0x1400c4f70 wctomb
0x1400c4f78 ferror
0x1400c4f80 iswctype
0x1400c4f88 wcstombs
0x1400c4f90 _isatty
0x1400c4f98 ungetc
0x1400c4fa0 ?terminate@@YAXXZ
0x1400c4fa8 __badioinfo
0x1400c4fb0 __pioinfo
0x1400c4fb8 _read
0x1400c4fc0 log
0x1400c4fc8 __mb_cur_max
0x1400c4fd0 vwprintf
0x1400c4fd8 __set_app_type
0x1400c4fe0 _fmode
0x1400c4fe8 _commode
0x1400c4ff0 _errno
0x1400c4ff8 free
0x1400c5000 _wcsdup
0x1400c5008 _vsnprintf
0x1400c5010 strrchr
0x1400c5018 _wcsicmp
0x1400c5020 vfwprintf
0x1400c5028 _vscwprintf
0x1400c5030 fflush
0x1400c5038 _wfopen
0x1400c5040 wprintf
0x1400c5048 _fileno
0x1400c5050 _iob
0x1400c5058 memcmp
0x1400c5060 _setmode
0x1400c5068 fclose
0x1400c5070 _stricmp
0x1400c5078 wcsrchr
0x1400c5080 wcschr
0x1400c5088 strtoul
0x1400c5090 _wcsnicmp
0x1400c5098 wcsstr
0x1400c50a0 _vscprintf
0x1400c50a8 memmove
0x1400c50b0 strncmp
0x1400c50b8 malloc
0x1400c50c0 _msize
0x1400c50c8 strcspn
0x1400c50d0 realloc
0x1400c50d8 fgetws
0x1400c50e0 wcstoul
0x1400c50e8 wcstol
0x1400c50f0 towupper
0x1400c50f8 _wpgmptr
0x1400c5100 strstr
0x1400c5108 strchr
0x1400c5110 _wcstoui64
0x1400c5118 wcsncmp
0x1400c5120 getchar
0x1400c5128 memcpy
0x1400c5130 memset
0x1400c5138 __C_specific_handler
0x1400c5140 __wgetmainargs
0x1400c5148 _XcptFilter
0x1400c5150 _exit
0x1400c5158 _cexit
0x1400c5160 exit
0x1400c5168 _initterm
0x1400c5170 _amsg_exit
0x1400c5178 __setusermatherr
EAT(Export Address Table) is none