ScreenShot
| Created | 2024.07.04 09:44 | Machine | s1_win7_x6403 |
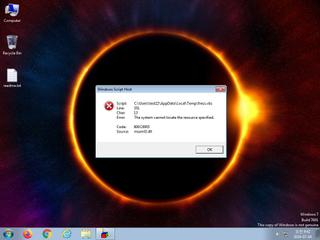
| Filename | fress.vbs | ||
| Type | Little-endian UTF-16 Unicode text, with CRLF, CR line terminators | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 12 detected (gen40, AAKW, druvzi, TOPIS, rHcE8wIYbGF, Detected, AgentTesla) | ||
| md5 | eadbe0d07dc98f935224d3ccea5c6b96 | ||
| sha256 | 770ad73ae81183ddcf34dc4b20048c867d26f7796e893b467d050452e1be769d | ||
| ssdeep | 384:4gEKm2eZIaRmYm0zfbEXJFay4c+n2/0LKj1LnNLzhDR:A2QfYZFay4c+n2/0LKj1LnNLzh1 | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| danger | Connects to an IP address that is no longer responding to requests (legitimate services will remain up-and-running usually) |
| watch | File has been identified by 12 AntiVirus engines on VirusTotal as malicious |
| watch | Network communications indicative of a potential document or script payload download was initiated by the process wscript.exe |
| watch | Wscript.exe initiated network communications indicative of a script based payload download |
| watch | wscript.exe-based dropper (JScript |
Rules (0cnts)
| Level | Name | Description | Collection |
|---|