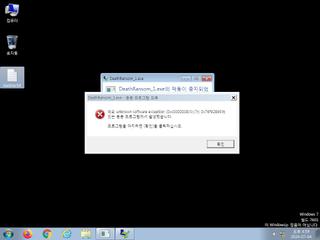
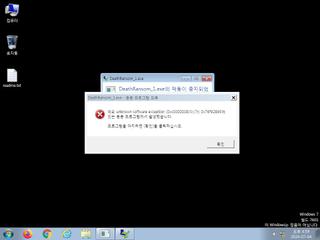
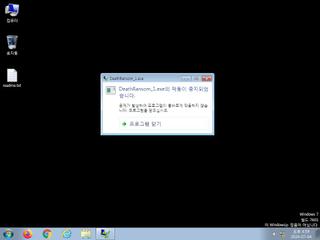
ScreenShot
| Created | 2024.07.04 17:08 | Machine | s1_win7_x6401 |
| Filename | DeathRansom_1.exe | ||
| Type | PE32 executable (GUI) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 66 detected (AIDetectMalware, DeathRansom, Windows, Ransomware, Hellokitty, Malicious, score, Unsafe, Death, Filecoder, ali2000010, giysar, CLASSIC, pgzbl, THKBOAIA, Real Protect, eivkk, Detected, ai score=100, Fuerboos, Malware@#rlp7bi2rrhwy, MacOS, EXIH, BScope, GdSda, Gencirc, KlggoVlN79A, susgen, confidence, 100%) | ||
| md5 | a35596ed0bfb34de4e512a3225f8300a | ||
| sha256 | 7c2dbad516d18d2c1c21ecc5792bc232f7b34dadc1bc19e967190d79174131d1 | ||
| ssdeep | 1536:gZVYb2bbBisyEcPC00h7sBvvKk+jTc7+T8l7RJV62CzVDL+oWB27evMCUQ:EV+GiVEc6RsMJQ | ||
| imphash | 3078147a4b21d62a2ff5d0ed67f98e73 | ||
| impfuzzy | 24:tkm+gWDYoprB0D+3/mdQBrMAzZYzud2VKwM1cT3wxbEkEQn:tkm+gR6rCda1ZYqmK77gNQ | ||
Network IP location
Signature (9cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 66 AntiVirus engines on VirusTotal as malicious |
| warning | Appends a new file extension or content to 150 files indicative of a ransomware file encryption process |
| warning | Performs 150 file moves indicative of a ransomware file encryption process |
| watch | Attempts to detect Cuckoo Sandbox through the presence of a file |
| watch | Writes a potential ransom message to disk |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | Checks amount of memory in system |
| info | One or more processes crashed |
| info | Queries for the computername |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
SHLWAPI.dll
0x40c0b8 StrStrW
0x40c0bc wnsprintfA
0x40c0c0 wnsprintfW
MSVCRT.dll
0x40c098 memcpy
0x40c09c memset
SHELL32.dll
0x40c0b0 SHEmptyRecycleBinA
MPR.dll
0x40c088 WNetEnumResourceW
0x40c08c WNetCloseEnum
0x40c090 WNetOpenEnumW
KERNEL32.dll
0x40c018 ExitProcess
0x40c01c GetLogicalDriveStringsW
0x40c020 GetUserDefaultLangID
0x40c024 LoadLibraryA
0x40c028 GetProcAddress
0x40c02c GetModuleHandleA
0x40c030 lstrlenW
0x40c034 HeapFree
0x40c038 HeapReAlloc
0x40c03c HeapAlloc
0x40c040 GetProcessHeap
0x40c044 ReadFile
0x40c048 WriteFile
0x40c04c QueueUserWorkItem
0x40c050 Sleep
0x40c054 InterlockedExchangeAdd
0x40c058 CloseHandle
0x40c05c SetFilePointerEx
0x40c060 lstrlenA
0x40c064 FindFirstFileW
0x40c068 FindNextFileW
0x40c06c FindClose
0x40c070 CreateFileW
0x40c074 GetCurrentProcess
0x40c078 lstrcmpW
0x40c07c MoveFileW
0x40c080 lstrcpyW
USER32.dll
0x40c0c8 CharLowerW
0x40c0cc GetKeyboardLayoutList
ADVAPI32.dll
0x40c000 RegSetValueExA
0x40c004 RegOpenKeyExA
0x40c008 RegCreateKeyA
0x40c00c RegCloseKey
0x40c010 RegQueryValueExA
ole32.dll
0x40c0d4 CoSetProxyBlanket
0x40c0d8 CoCreateInstance
OLEAUT32.dll
0x40c0a4 VariantInit
0x40c0a8 VariantClear
EAT(Export Address Table) is none
SHLWAPI.dll
0x40c0b8 StrStrW
0x40c0bc wnsprintfA
0x40c0c0 wnsprintfW
MSVCRT.dll
0x40c098 memcpy
0x40c09c memset
SHELL32.dll
0x40c0b0 SHEmptyRecycleBinA
MPR.dll
0x40c088 WNetEnumResourceW
0x40c08c WNetCloseEnum
0x40c090 WNetOpenEnumW
KERNEL32.dll
0x40c018 ExitProcess
0x40c01c GetLogicalDriveStringsW
0x40c020 GetUserDefaultLangID
0x40c024 LoadLibraryA
0x40c028 GetProcAddress
0x40c02c GetModuleHandleA
0x40c030 lstrlenW
0x40c034 HeapFree
0x40c038 HeapReAlloc
0x40c03c HeapAlloc
0x40c040 GetProcessHeap
0x40c044 ReadFile
0x40c048 WriteFile
0x40c04c QueueUserWorkItem
0x40c050 Sleep
0x40c054 InterlockedExchangeAdd
0x40c058 CloseHandle
0x40c05c SetFilePointerEx
0x40c060 lstrlenA
0x40c064 FindFirstFileW
0x40c068 FindNextFileW
0x40c06c FindClose
0x40c070 CreateFileW
0x40c074 GetCurrentProcess
0x40c078 lstrcmpW
0x40c07c MoveFileW
0x40c080 lstrcpyW
USER32.dll
0x40c0c8 CharLowerW
0x40c0cc GetKeyboardLayoutList
ADVAPI32.dll
0x40c000 RegSetValueExA
0x40c004 RegOpenKeyExA
0x40c008 RegCreateKeyA
0x40c00c RegCloseKey
0x40c010 RegQueryValueExA
ole32.dll
0x40c0d4 CoSetProxyBlanket
0x40c0d8 CoCreateInstance
OLEAUT32.dll
0x40c0a4 VariantInit
0x40c0a8 VariantClear
EAT(Export Address Table) is none