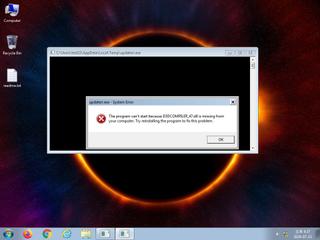
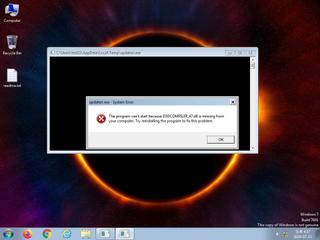
ScreenShot
| Created | 2024.07.15 16:42 | Machine | s1_win7_x6403 |
| Filename | updaterr.exe | ||
| Type | PE32+ executable (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 48 detected (Common, GameHack, malicious, high confidence, score, GenericKD, Unsafe, Hacktool, Vzlr, Attribute, HighConfidence, AGen, Artemis, TrojanX, oxM8JQn3x8U, Tool, GameHackAGen, R002C0DFD24, GenKD, Detected, ai score=86, Casdet, ABTrojan, ZXNS, R657512, Static AI, Suspicious PE, confidence) | ||
| md5 | 4ac882ebdbc1431cdd3ab45e1712ada1 | ||
| sha256 | b13f23643fddce3f41b6908a00051b6688788668c81d698994c140bf6290c2d6 | ||
| ssdeep | 24576:65MOrT+F0sIE9JqsC6mVFyCsffzMS6pcsP9Qtce0TBs/lPsoCyEbDb7Br5oANn90:+bjnS | ||
| imphash | 5397e91e3bea53fd788a5ca1224e7738 | ||
| impfuzzy | 96:/jG6fWaLaIZRbdQVR1qICjFnniu6QWJ3dagBixUQ8poognAoSEdjLDUJ9FI6CNT6:FW4jbdQVKyu6QgavXgrvjTurO | ||
Network IP location
Signature (2cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 48 AntiVirus engines on VirusTotal as malicious |
| info | This executable has a PDB path |
Rules (7cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| danger | Win32_Trojan_Gen_1_0904B0_Zero | Win32 Trojan Emotet | binaries (upload) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x1400ac068 InitializeCriticalSectionEx
0x1400ac070 CreateFileW
0x1400ac078 GetCurrentThreadId
0x1400ac080 GetLastError
0x1400ac088 CloseHandle
0x1400ac090 DeleteCriticalSection
0x1400ac098 GetCurrentProcessId
0x1400ac0a0 GetTempPathW
0x1400ac0a8 Process32First
0x1400ac0b0 SetLastError
0x1400ac0b8 SetConsoleTitleA
0x1400ac0c0 CreateToolhelp32Snapshot
0x1400ac0c8 Sleep
0x1400ac0d0 Process32Next
0x1400ac0d8 CreateThread
0x1400ac0e0 DeviceIoControl
0x1400ac0e8 OutputDebugStringW
0x1400ac0f0 InitializeSListHead
0x1400ac0f8 GetSystemTimeAsFileTime
0x1400ac100 GetModuleHandleW
0x1400ac108 IsDebuggerPresent
0x1400ac110 SleepConditionVariableSRW
0x1400ac118 WakeAllConditionVariable
0x1400ac120 AcquireSRWLockExclusive
0x1400ac128 ReleaseSRWLockExclusive
0x1400ac130 IsProcessorFeaturePresent
0x1400ac138 TerminateProcess
0x1400ac140 GetCurrentProcess
0x1400ac148 SetUnhandledExceptionFilter
0x1400ac150 UnhandledExceptionFilter
0x1400ac158 VirtualAlloc
0x1400ac160 VirtualFree
0x1400ac168 QueryPerformanceCounter
0x1400ac170 LoadLibraryA
0x1400ac178 GetModuleHandleA
0x1400ac180 GlobalUnlock
0x1400ac188 WideCharToMultiByte
0x1400ac190 GlobalLock
0x1400ac198 GlobalFree
0x1400ac1a0 GlobalAlloc
0x1400ac1a8 FreeLibrary
0x1400ac1b0 GetProcAddress
0x1400ac1b8 QueryPerformanceFrequency
0x1400ac1c0 MultiByteToWideChar
USER32.dll
0x1400ac320 SetCapture
0x1400ac328 SetCursor
0x1400ac330 GetClientRect
0x1400ac338 IsWindowUnicode
0x1400ac340 GetWindowThreadProcessId
0x1400ac348 DispatchMessageA
0x1400ac350 GetWindowRect
0x1400ac358 DestroyWindow
0x1400ac360 SetWindowPos
0x1400ac368 GetSystemMetrics
0x1400ac370 ShowWindow
0x1400ac378 GetAsyncKeyState
0x1400ac380 SetWindowLongA
0x1400ac388 GetWindowLongA
0x1400ac390 EnumWindows
0x1400ac398 DefWindowProcA
0x1400ac3a0 CreateWindowExA
0x1400ac3a8 TranslateMessage
0x1400ac3b0 PeekMessageA
0x1400ac3b8 PostQuitMessage
0x1400ac3c0 GetDesktopWindow
0x1400ac3c8 FindWindowA
0x1400ac3d0 RegisterClassExA
0x1400ac3d8 UpdateWindow
0x1400ac3e0 SetForegroundWindow
0x1400ac3e8 UnregisterClassA
0x1400ac3f0 GetKeyState
0x1400ac3f8 OpenClipboard
0x1400ac400 LoadCursorA
0x1400ac408 ScreenToClient
0x1400ac410 GetCapture
0x1400ac418 ClientToScreen
0x1400ac420 TrackMouseEvent
0x1400ac428 ReleaseCapture
0x1400ac430 GetForegroundWindow
0x1400ac438 SetCursorPos
0x1400ac440 GetCursorPos
0x1400ac448 CloseClipboard
0x1400ac450 EmptyClipboard
0x1400ac458 GetClipboardData
0x1400ac460 SetClipboardData
ADVAPI32.dll
0x1400ac000 RegOpenKeyW
0x1400ac008 RegCreateKeyW
0x1400ac010 RegDeleteKeyW
0x1400ac018 RegCloseKey
0x1400ac020 RegSetKeyValueW
IMM32.dll
0x1400ac040 ImmSetCompositionWindow
0x1400ac048 ImmReleaseContext
0x1400ac050 ImmGetContext
0x1400ac058 ImmSetCandidateWindow
D3DCOMPILER_47.dll
0x1400ac030 D3DCompile
dwmapi.dll
0x1400ac798 DwmExtendFrameIntoClientArea
MSVCP140.dll
0x1400ac1d0 _Query_perf_frequency
0x1400ac1d8 ?good@ios_base@std@@QEBA_NXZ
0x1400ac1e0 _Query_perf_counter
0x1400ac1e8 ?cin@std@@3V?$basic_istream@DU?$char_traits@D@std@@@1@A
0x1400ac1f0 ?clear@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x1400ac1f8 ?_Random_device@std@@YAIXZ
0x1400ac200 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@P6AAEAV01@AEAV01@@Z@Z
0x1400ac208 ?sputc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHD@Z
0x1400ac210 ?flush@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@XZ
0x1400ac218 ??1_Lockit@std@@QEAA@XZ
0x1400ac220 ??0_Lockit@std@@QEAA@H@Z
0x1400ac228 ?_Getgloballocale@locale@std@@CAPEAV_Locimp@12@XZ
0x1400ac230 ?id@?$codecvt@DDU_Mbstatet@@@std@@2V0locale@2@A
0x1400ac238 ?_Fiopen@std@@YAPEAU_iobuf@@PEB_WHH@Z
0x1400ac240 ?_Xlength_error@std@@YAXPEBD@Z
0x1400ac248 ?_Getcat@?$codecvt@DDU_Mbstatet@@@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
0x1400ac250 ?unshift@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEAD1AEAPEAD@Z
0x1400ac258 ??0?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1400ac260 ?getloc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEBA?AVlocale@2@XZ
0x1400ac268 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXXZ
0x1400ac270 ?in@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1400ac278 ?out@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1400ac280 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x1400ac288 ??0?$basic_ios@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1400ac290 ??0?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x1400ac298 ??1?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400ac2a0 ?showmanyc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JXZ
0x1400ac2a8 ?xsgetn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEAD_J@Z
0x1400ac2b0 ?xsputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEBD_J@Z
0x1400ac2b8 ??1?$basic_ios@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400ac2c0 ??1?$basic_ostream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400ac2c8 ?write@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@PEBD_J@Z
0x1400ac2d0 ??7ios_base@std@@QEBA_NXZ
0x1400ac2d8 ?always_noconv@codecvt_base@std@@QEBA_NXZ
0x1400ac2e0 ??Bid@locale@std@@QEAA_KXZ
0x1400ac2e8 ?cout@std@@3V?$basic_ostream@DU?$char_traits@D@std@@@1@A
0x1400ac2f0 ?uncaught_exception@std@@YA_NXZ
0x1400ac2f8 ?_Osfx@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAXXZ
0x1400ac300 ?sputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAA_JPEBD_J@Z
0x1400ac308 ?widen@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBADD@Z
0x1400ac310 ?put@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@D@Z
ntdll.dll
0x1400ac7a8 RtlInitUnicodeString
0x1400ac7b0 RtlCaptureContext
0x1400ac7b8 RtlLookupFunctionEntry
0x1400ac7c0 RtlVirtualUnwind
0x1400ac7c8 NtQuerySystemInformation
d3d11.dll
0x1400ac788 D3D11CreateDeviceAndSwapChain
VCRUNTIME140_1.dll
0x1400ac4e0 __CxxFrameHandler4
VCRUNTIME140.dll
0x1400ac470 memmove
0x1400ac478 memset
0x1400ac480 _CxxThrowException
0x1400ac488 __std_terminate
0x1400ac490 strstr
0x1400ac498 memcpy
0x1400ac4a0 memcmp
0x1400ac4a8 memchr
0x1400ac4b0 __current_exception_context
0x1400ac4b8 __current_exception
0x1400ac4c0 __C_specific_handler
0x1400ac4c8 __std_exception_copy
0x1400ac4d0 __std_exception_destroy
api-ms-win-crt-stdio-l1-1-0.dll
0x1400ac668 __acrt_iob_func
0x1400ac670 __p__commode
0x1400ac678 _set_fmode
0x1400ac680 __stdio_common_vsnprintf_s
0x1400ac688 fflush
0x1400ac690 ftell
0x1400ac698 __stdio_common_vsprintf
0x1400ac6a0 __stdio_common_vsprintf_s
0x1400ac6a8 _get_stream_buffer_pointers
0x1400ac6b0 _fseeki64
0x1400ac6b8 fsetpos
0x1400ac6c0 ungetc
0x1400ac6c8 fclose
0x1400ac6d0 fseek
0x1400ac6d8 setvbuf
0x1400ac6e0 fgetpos
0x1400ac6e8 fgetc
0x1400ac6f0 __stdio_common_vfprintf
0x1400ac6f8 fwrite
0x1400ac700 fputc
0x1400ac708 _wfopen
0x1400ac710 __stdio_common_vsscanf
0x1400ac718 fread
api-ms-win-crt-utility-l1-1-0.dll
0x1400ac768 srand
0x1400ac770 rand
0x1400ac778 qsort
api-ms-win-crt-string-l1-1-0.dll
0x1400ac728 strcpy_s
0x1400ac730 strncmp
0x1400ac738 _stricmp
0x1400ac740 strncpy
0x1400ac748 strcmp
api-ms-win-crt-heap-l1-1-0.dll
0x1400ac520 malloc
0x1400ac528 free
0x1400ac530 _set_new_mode
0x1400ac538 _callnewh
api-ms-win-crt-convert-l1-1-0.dll
0x1400ac4f0 atof
api-ms-win-crt-filesystem-l1-1-0.dll
0x1400ac500 _unlock_file
0x1400ac508 _lock_file
0x1400ac510 _wremove
api-ms-win-crt-time-l1-1-0.dll
0x1400ac758 _time64
api-ms-win-crt-runtime-l1-1-0.dll
0x1400ac5c0 _initialize_narrow_environment
0x1400ac5c8 _initialize_onexit_table
0x1400ac5d0 _register_onexit_function
0x1400ac5d8 _crt_atexit
0x1400ac5e0 _cexit
0x1400ac5e8 _seh_filter_exe
0x1400ac5f0 _set_app_type
0x1400ac5f8 terminate
0x1400ac600 _get_initial_narrow_environment
0x1400ac608 _initterm
0x1400ac610 _initterm_e
0x1400ac618 _exit
0x1400ac620 system
0x1400ac628 __p___argc
0x1400ac630 __p___argv
0x1400ac638 _c_exit
0x1400ac640 _register_thread_local_exe_atexit_callback
0x1400ac648 _configure_narrow_argv
0x1400ac650 exit
0x1400ac658 _invalid_parameter_noinfo_noreturn
api-ms-win-crt-math-l1-1-0.dll
0x1400ac558 ceilf
0x1400ac560 atan2f
0x1400ac568 fmodf
0x1400ac570 asinf
0x1400ac578 cosf
0x1400ac580 atanf
0x1400ac588 sqrtf
0x1400ac590 acosf
0x1400ac598 sinf
0x1400ac5a0 __setusermatherr
0x1400ac5a8 powf
0x1400ac5b0 tanf
api-ms-win-crt-locale-l1-1-0.dll
0x1400ac548 _configthreadlocale
EAT(Export Address Table) is none
KERNEL32.dll
0x1400ac068 InitializeCriticalSectionEx
0x1400ac070 CreateFileW
0x1400ac078 GetCurrentThreadId
0x1400ac080 GetLastError
0x1400ac088 CloseHandle
0x1400ac090 DeleteCriticalSection
0x1400ac098 GetCurrentProcessId
0x1400ac0a0 GetTempPathW
0x1400ac0a8 Process32First
0x1400ac0b0 SetLastError
0x1400ac0b8 SetConsoleTitleA
0x1400ac0c0 CreateToolhelp32Snapshot
0x1400ac0c8 Sleep
0x1400ac0d0 Process32Next
0x1400ac0d8 CreateThread
0x1400ac0e0 DeviceIoControl
0x1400ac0e8 OutputDebugStringW
0x1400ac0f0 InitializeSListHead
0x1400ac0f8 GetSystemTimeAsFileTime
0x1400ac100 GetModuleHandleW
0x1400ac108 IsDebuggerPresent
0x1400ac110 SleepConditionVariableSRW
0x1400ac118 WakeAllConditionVariable
0x1400ac120 AcquireSRWLockExclusive
0x1400ac128 ReleaseSRWLockExclusive
0x1400ac130 IsProcessorFeaturePresent
0x1400ac138 TerminateProcess
0x1400ac140 GetCurrentProcess
0x1400ac148 SetUnhandledExceptionFilter
0x1400ac150 UnhandledExceptionFilter
0x1400ac158 VirtualAlloc
0x1400ac160 VirtualFree
0x1400ac168 QueryPerformanceCounter
0x1400ac170 LoadLibraryA
0x1400ac178 GetModuleHandleA
0x1400ac180 GlobalUnlock
0x1400ac188 WideCharToMultiByte
0x1400ac190 GlobalLock
0x1400ac198 GlobalFree
0x1400ac1a0 GlobalAlloc
0x1400ac1a8 FreeLibrary
0x1400ac1b0 GetProcAddress
0x1400ac1b8 QueryPerformanceFrequency
0x1400ac1c0 MultiByteToWideChar
USER32.dll
0x1400ac320 SetCapture
0x1400ac328 SetCursor
0x1400ac330 GetClientRect
0x1400ac338 IsWindowUnicode
0x1400ac340 GetWindowThreadProcessId
0x1400ac348 DispatchMessageA
0x1400ac350 GetWindowRect
0x1400ac358 DestroyWindow
0x1400ac360 SetWindowPos
0x1400ac368 GetSystemMetrics
0x1400ac370 ShowWindow
0x1400ac378 GetAsyncKeyState
0x1400ac380 SetWindowLongA
0x1400ac388 GetWindowLongA
0x1400ac390 EnumWindows
0x1400ac398 DefWindowProcA
0x1400ac3a0 CreateWindowExA
0x1400ac3a8 TranslateMessage
0x1400ac3b0 PeekMessageA
0x1400ac3b8 PostQuitMessage
0x1400ac3c0 GetDesktopWindow
0x1400ac3c8 FindWindowA
0x1400ac3d0 RegisterClassExA
0x1400ac3d8 UpdateWindow
0x1400ac3e0 SetForegroundWindow
0x1400ac3e8 UnregisterClassA
0x1400ac3f0 GetKeyState
0x1400ac3f8 OpenClipboard
0x1400ac400 LoadCursorA
0x1400ac408 ScreenToClient
0x1400ac410 GetCapture
0x1400ac418 ClientToScreen
0x1400ac420 TrackMouseEvent
0x1400ac428 ReleaseCapture
0x1400ac430 GetForegroundWindow
0x1400ac438 SetCursorPos
0x1400ac440 GetCursorPos
0x1400ac448 CloseClipboard
0x1400ac450 EmptyClipboard
0x1400ac458 GetClipboardData
0x1400ac460 SetClipboardData
ADVAPI32.dll
0x1400ac000 RegOpenKeyW
0x1400ac008 RegCreateKeyW
0x1400ac010 RegDeleteKeyW
0x1400ac018 RegCloseKey
0x1400ac020 RegSetKeyValueW
IMM32.dll
0x1400ac040 ImmSetCompositionWindow
0x1400ac048 ImmReleaseContext
0x1400ac050 ImmGetContext
0x1400ac058 ImmSetCandidateWindow
D3DCOMPILER_47.dll
0x1400ac030 D3DCompile
dwmapi.dll
0x1400ac798 DwmExtendFrameIntoClientArea
MSVCP140.dll
0x1400ac1d0 _Query_perf_frequency
0x1400ac1d8 ?good@ios_base@std@@QEBA_NXZ
0x1400ac1e0 _Query_perf_counter
0x1400ac1e8 ?cin@std@@3V?$basic_istream@DU?$char_traits@D@std@@@1@A
0x1400ac1f0 ?clear@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x1400ac1f8 ?_Random_device@std@@YAIXZ
0x1400ac200 ??6?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV01@P6AAEAV01@AEAV01@@Z@Z
0x1400ac208 ?sputc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAAHD@Z
0x1400ac210 ?flush@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@XZ
0x1400ac218 ??1_Lockit@std@@QEAA@XZ
0x1400ac220 ??0_Lockit@std@@QEAA@H@Z
0x1400ac228 ?_Getgloballocale@locale@std@@CAPEAV_Locimp@12@XZ
0x1400ac230 ?id@?$codecvt@DDU_Mbstatet@@@std@@2V0locale@2@A
0x1400ac238 ?_Fiopen@std@@YAPEAU_iobuf@@PEB_WHH@Z
0x1400ac240 ?_Xlength_error@std@@YAXPEBD@Z
0x1400ac248 ?_Getcat@?$codecvt@DDU_Mbstatet@@@std@@SA_KPEAPEBVfacet@locale@2@PEBV42@@Z
0x1400ac250 ?unshift@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEAD1AEAPEAD@Z
0x1400ac258 ??0?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1400ac260 ?getloc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEBA?AVlocale@2@XZ
0x1400ac268 ?_Init@?$basic_streambuf@DU?$char_traits@D@std@@@std@@IEAAXXZ
0x1400ac270 ?in@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1400ac278 ?out@?$codecvt@DDU_Mbstatet@@@std@@QEBAHAEAU_Mbstatet@@PEBD1AEAPEBDPEAD3AEAPEAD@Z
0x1400ac280 ?setstate@?$basic_ios@DU?$char_traits@D@std@@@std@@QEAAXH_N@Z
0x1400ac288 ??0?$basic_ios@DU?$char_traits@D@std@@@std@@IEAA@XZ
0x1400ac290 ??0?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAA@PEAV?$basic_streambuf@DU?$char_traits@D@std@@@1@_N@Z
0x1400ac298 ??1?$basic_streambuf@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400ac2a0 ?showmanyc@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JXZ
0x1400ac2a8 ?xsgetn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEAD_J@Z
0x1400ac2b0 ?xsputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@MEAA_JPEBD_J@Z
0x1400ac2b8 ??1?$basic_ios@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400ac2c0 ??1?$basic_ostream@DU?$char_traits@D@std@@@std@@UEAA@XZ
0x1400ac2c8 ?write@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@PEBD_J@Z
0x1400ac2d0 ??7ios_base@std@@QEBA_NXZ
0x1400ac2d8 ?always_noconv@codecvt_base@std@@QEBA_NXZ
0x1400ac2e0 ??Bid@locale@std@@QEAA_KXZ
0x1400ac2e8 ?cout@std@@3V?$basic_ostream@DU?$char_traits@D@std@@@1@A
0x1400ac2f0 ?uncaught_exception@std@@YA_NXZ
0x1400ac2f8 ?_Osfx@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAXXZ
0x1400ac300 ?sputn@?$basic_streambuf@DU?$char_traits@D@std@@@std@@QEAA_JPEBD_J@Z
0x1400ac308 ?widen@?$basic_ios@DU?$char_traits@D@std@@@std@@QEBADD@Z
0x1400ac310 ?put@?$basic_ostream@DU?$char_traits@D@std@@@std@@QEAAAEAV12@D@Z
ntdll.dll
0x1400ac7a8 RtlInitUnicodeString
0x1400ac7b0 RtlCaptureContext
0x1400ac7b8 RtlLookupFunctionEntry
0x1400ac7c0 RtlVirtualUnwind
0x1400ac7c8 NtQuerySystemInformation
d3d11.dll
0x1400ac788 D3D11CreateDeviceAndSwapChain
VCRUNTIME140_1.dll
0x1400ac4e0 __CxxFrameHandler4
VCRUNTIME140.dll
0x1400ac470 memmove
0x1400ac478 memset
0x1400ac480 _CxxThrowException
0x1400ac488 __std_terminate
0x1400ac490 strstr
0x1400ac498 memcpy
0x1400ac4a0 memcmp
0x1400ac4a8 memchr
0x1400ac4b0 __current_exception_context
0x1400ac4b8 __current_exception
0x1400ac4c0 __C_specific_handler
0x1400ac4c8 __std_exception_copy
0x1400ac4d0 __std_exception_destroy
api-ms-win-crt-stdio-l1-1-0.dll
0x1400ac668 __acrt_iob_func
0x1400ac670 __p__commode
0x1400ac678 _set_fmode
0x1400ac680 __stdio_common_vsnprintf_s
0x1400ac688 fflush
0x1400ac690 ftell
0x1400ac698 __stdio_common_vsprintf
0x1400ac6a0 __stdio_common_vsprintf_s
0x1400ac6a8 _get_stream_buffer_pointers
0x1400ac6b0 _fseeki64
0x1400ac6b8 fsetpos
0x1400ac6c0 ungetc
0x1400ac6c8 fclose
0x1400ac6d0 fseek
0x1400ac6d8 setvbuf
0x1400ac6e0 fgetpos
0x1400ac6e8 fgetc
0x1400ac6f0 __stdio_common_vfprintf
0x1400ac6f8 fwrite
0x1400ac700 fputc
0x1400ac708 _wfopen
0x1400ac710 __stdio_common_vsscanf
0x1400ac718 fread
api-ms-win-crt-utility-l1-1-0.dll
0x1400ac768 srand
0x1400ac770 rand
0x1400ac778 qsort
api-ms-win-crt-string-l1-1-0.dll
0x1400ac728 strcpy_s
0x1400ac730 strncmp
0x1400ac738 _stricmp
0x1400ac740 strncpy
0x1400ac748 strcmp
api-ms-win-crt-heap-l1-1-0.dll
0x1400ac520 malloc
0x1400ac528 free
0x1400ac530 _set_new_mode
0x1400ac538 _callnewh
api-ms-win-crt-convert-l1-1-0.dll
0x1400ac4f0 atof
api-ms-win-crt-filesystem-l1-1-0.dll
0x1400ac500 _unlock_file
0x1400ac508 _lock_file
0x1400ac510 _wremove
api-ms-win-crt-time-l1-1-0.dll
0x1400ac758 _time64
api-ms-win-crt-runtime-l1-1-0.dll
0x1400ac5c0 _initialize_narrow_environment
0x1400ac5c8 _initialize_onexit_table
0x1400ac5d0 _register_onexit_function
0x1400ac5d8 _crt_atexit
0x1400ac5e0 _cexit
0x1400ac5e8 _seh_filter_exe
0x1400ac5f0 _set_app_type
0x1400ac5f8 terminate
0x1400ac600 _get_initial_narrow_environment
0x1400ac608 _initterm
0x1400ac610 _initterm_e
0x1400ac618 _exit
0x1400ac620 system
0x1400ac628 __p___argc
0x1400ac630 __p___argv
0x1400ac638 _c_exit
0x1400ac640 _register_thread_local_exe_atexit_callback
0x1400ac648 _configure_narrow_argv
0x1400ac650 exit
0x1400ac658 _invalid_parameter_noinfo_noreturn
api-ms-win-crt-math-l1-1-0.dll
0x1400ac558 ceilf
0x1400ac560 atan2f
0x1400ac568 fmodf
0x1400ac570 asinf
0x1400ac578 cosf
0x1400ac580 atanf
0x1400ac588 sqrtf
0x1400ac590 acosf
0x1400ac598 sinf
0x1400ac5a0 __setusermatherr
0x1400ac5a8 powf
0x1400ac5b0 tanf
api-ms-win-crt-locale-l1-1-0.dll
0x1400ac548 _configthreadlocale
EAT(Export Address Table) is none