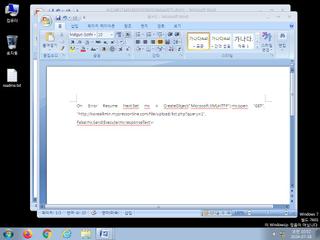
ScreenShot
| Created | 2024.07.18 10:54 | Machine | s1_win7_x6401 |
| Filename | 4c12d617aa51bb0c0108242da6aa0071.docm | ||
| Type | Microsoft Word 2007+ | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 25 detected (malicious, high confidence, score, EmoooDldr, Save, Kimsuky, Obfuscated, Valyria, Dnldr, elyanu, TOPIS, 6BMNDE24csN, PBMD, modification of W97M, Detected, ai score=81) | ||
| md5 | 4c12d617aa51bb0c0108242da6aa0071 | ||
| sha256 | ee088f55e7cbc5d797c5b030f880b96708d86103e60d2e89fbc6b8bf2cdf6130 | ||
| ssdeep | 1536:ZZvvDiCRMOeIF7fankKddtXFMrI3eP40fcyD:zve7MUkK1O4qX | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (10cnts)
| Level | Description |
|---|---|
| danger | The process winword.exe wrote an executable file to disk which it then attempted to execute |
| warning | File has been identified by 25 AntiVirus engines on VirusTotal as malicious |
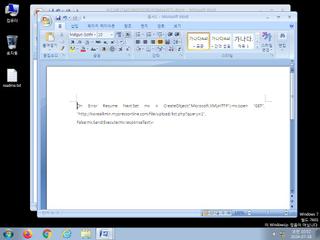
| watch | Creates suspicious VBA object |
| watch | Libraries known to be associated with a CVE were requested (may be False Positive) |
| watch | One or more non-whitelisted processes were created |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates (office) documents on the filesystem |
| notice | Creates a suspicious process |
| notice | Creates hidden or system file |
| info | Command line console output was observed |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Contains_VBA_macro_code | Detect a MS Office document with embedded VBA macro code [binaries] | binaries (upload) |
| info | docx | Word 2007 file format detection | binaries (upload) |
| info | zip_file_format | ZIP file format | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|