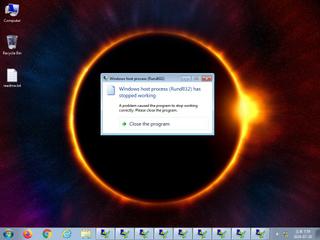
ScreenShot
| Created | 2024.07.20 20:01 | Machine | s1_win7_x6403 |
| Filename | mimilib.dll | ||
| Type | PE32 executable (DLL) (console) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 63 detected (AIDetectMalware, malicious, high confidence, score, HTool, Mimikatz, GenericKD, Unsafe, HackTool, uwccg, Genus, MalwareX, Tool, jritks, CLASSIC, olrti, PassView, CNGF, Apteryx, Detected, ai score=100, Malware@#289lhzuorpj06, Mikatz, Eldorado, R453144, ZedlaF, bu8@aC9ojzni, TrojanPSW, Gencirc, Djq4AkBZt0I, Static AI, Malicious PE, susgen, confidence, 100%) | ||
| md5 | 46e598798bdde4c72e796edcf2317b52 | ||
| sha256 | e60c210687e79347d06f9a144ee84417ba9ac4c1f303720f2fe4509734d670d6 | ||
| ssdeep | 384:ZPqreMGv6SqMDjuPRjL9sapJcos+uOiZESsQDygQ2Unn7PAss3sWqWyXO4hMnAl3:lrEdpJLFiq3GO7bs3sdEFyQejil0Tn | ||
| imphash | 721f5090ab31a091c5b9778028cc974c | ||
| impfuzzy | 24:9vsLRzJ+B6MNklwxv+1BdJ/3i9NDZk1z0SdbViqUXBn:9vi0B21Px3iG0SdpiqUxn | ||
Network IP location
Signature (4cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 63 AntiVirus engines on VirusTotal as malicious |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | Checks if process is being debugged by a debugger |
| info | One or more processes crashed |
Rules (4cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
ADVAPI32.dll
0x10005000 CreateRestrictedToken
0x10005004 CreateProcessAsUserW
0x10005008 ConvertSidToStringSidA
0x1000500c IsTextUnicode
0x10005010 OpenProcessToken
ntdll.dll
0x100050e4 RtlFreeUnicodeString
0x100050e8 RtlStringFromGUID
0x100050ec RtlEqualString
RPCRT4.dll
0x10005094 MesDecodeIncrementalHandleCreate
0x10005098 MesIncrementalHandleReset
0x1000509c NdrMesTypeDecode2
0x100050a0 NdrMesTypeFree2
0x100050a4 MesHandleFree
ole32.dll
0x100050f4 CoCreateInstance
KERNEL32.dll
0x10005018 GetSystemTimeAsFileTime
0x1000501c GetCurrentProcessId
0x10005020 GetCurrentThreadId
0x10005024 GetTickCount
0x10005028 UnhandledExceptionFilter
0x1000502c TerminateProcess
0x10005030 InterlockedCompareExchange
0x10005034 Sleep
0x10005038 RtlUnwind
0x1000503c QueryPerformanceCounter
0x10005040 GetCurrentProcess
0x10005044 CloseHandle
0x10005048 FreeLibrary
0x1000504c LoadLibraryW
0x10005050 lstrlenW
0x10005054 GetProcAddress
0x10005058 InterlockedIncrement
0x1000505c InterlockedDecrement
0x10005060 GetLastError
0x10005064 VirtualProtect
0x10005068 LocalAlloc
0x1000506c LocalFree
0x10005070 GetTimeFormatA
0x10005074 GetDateFormatA
0x10005078 FileTimeToSystemTime
0x1000507c FileTimeToLocalFileTime
0x10005080 RaiseException
0x10005084 InterlockedExchange
0x10005088 LoadLibraryA
0x1000508c SetUnhandledExceptionFilter
msvcrt.dll
0x100050ac fclose
0x100050b0 free
0x100050b4 malloc
0x100050b8 _stricmp
0x100050bc vfwprintf
0x100050c0 fflush
0x100050c4 memset
0x100050c8 memcpy
0x100050cc _XcptFilter
0x100050d0 _initterm
0x100050d4 _amsg_exit
0x100050d8 _wfopen
0x100050dc _except_handler3
EAT(Export Address Table) Library
0x1000111c DhcpNewPktHook
0x100010b4 DhcpServerCalloutEntry
0x1000186d DllCanUnloadNow
0x1000182d DllGetClassObject
0x1000119f DnsPluginCleanup
0x1000119a DnsPluginInitialize
0x100011a2 DnsPluginQuery
0x10002a56 ExtensionApiVersion
0x100011e0 InitializeChangeNotify
0x10001381 Msv1_0SubAuthenticationFilter
0x10001381 Msv1_0SubAuthenticationRoutine
0x1000129e NPGetCaps
0x10001234 NPLogonNotify
0x100011e3 PasswordChangeNotify
0x1000135e SpLsaModeInitialize
0x10002a5c WinDbgExtensionDllInit
0x10002a8d coffee
0x10002a9a mimikatz
0x10001000 startW
ADVAPI32.dll
0x10005000 CreateRestrictedToken
0x10005004 CreateProcessAsUserW
0x10005008 ConvertSidToStringSidA
0x1000500c IsTextUnicode
0x10005010 OpenProcessToken
ntdll.dll
0x100050e4 RtlFreeUnicodeString
0x100050e8 RtlStringFromGUID
0x100050ec RtlEqualString
RPCRT4.dll
0x10005094 MesDecodeIncrementalHandleCreate
0x10005098 MesIncrementalHandleReset
0x1000509c NdrMesTypeDecode2
0x100050a0 NdrMesTypeFree2
0x100050a4 MesHandleFree
ole32.dll
0x100050f4 CoCreateInstance
KERNEL32.dll
0x10005018 GetSystemTimeAsFileTime
0x1000501c GetCurrentProcessId
0x10005020 GetCurrentThreadId
0x10005024 GetTickCount
0x10005028 UnhandledExceptionFilter
0x1000502c TerminateProcess
0x10005030 InterlockedCompareExchange
0x10005034 Sleep
0x10005038 RtlUnwind
0x1000503c QueryPerformanceCounter
0x10005040 GetCurrentProcess
0x10005044 CloseHandle
0x10005048 FreeLibrary
0x1000504c LoadLibraryW
0x10005050 lstrlenW
0x10005054 GetProcAddress
0x10005058 InterlockedIncrement
0x1000505c InterlockedDecrement
0x10005060 GetLastError
0x10005064 VirtualProtect
0x10005068 LocalAlloc
0x1000506c LocalFree
0x10005070 GetTimeFormatA
0x10005074 GetDateFormatA
0x10005078 FileTimeToSystemTime
0x1000507c FileTimeToLocalFileTime
0x10005080 RaiseException
0x10005084 InterlockedExchange
0x10005088 LoadLibraryA
0x1000508c SetUnhandledExceptionFilter
msvcrt.dll
0x100050ac fclose
0x100050b0 free
0x100050b4 malloc
0x100050b8 _stricmp
0x100050bc vfwprintf
0x100050c0 fflush
0x100050c4 memset
0x100050c8 memcpy
0x100050cc _XcptFilter
0x100050d0 _initterm
0x100050d4 _amsg_exit
0x100050d8 _wfopen
0x100050dc _except_handler3
EAT(Export Address Table) Library
0x1000111c DhcpNewPktHook
0x100010b4 DhcpServerCalloutEntry
0x1000186d DllCanUnloadNow
0x1000182d DllGetClassObject
0x1000119f DnsPluginCleanup
0x1000119a DnsPluginInitialize
0x100011a2 DnsPluginQuery
0x10002a56 ExtensionApiVersion
0x100011e0 InitializeChangeNotify
0x10001381 Msv1_0SubAuthenticationFilter
0x10001381 Msv1_0SubAuthenticationRoutine
0x1000129e NPGetCaps
0x10001234 NPLogonNotify
0x100011e3 PasswordChangeNotify
0x1000135e SpLsaModeInitialize
0x10002a5c WinDbgExtensionDllInit
0x10002a8d coffee
0x10002a9a mimikatz
0x10001000 startW