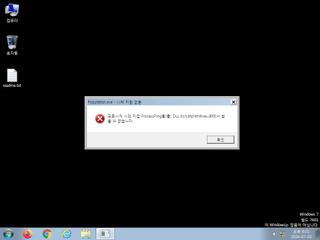
ScreenShot
| Created | 2024.07.20 20:12 | Machine | s1_win7_x6401 |
| Filename | Population.exe | ||
| Type | PE32+ executable (GUI) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : mailcious | ||
| VT API (file) | 41 detected (AIDetectMalware, Malicious, score, Artemis, Save, Attribute, HighConfidence, AGen, MalwareX, CLOUD, cdimk, Outbreak, Detected, ai score=84, Wacatac, Donut, 1Z90E4, ABTrojan, FQOA, Chgt, Gencirc, Static AI, Suspicious PE, confidence) | ||
| md5 | 18bbc3fb86e902afb59c06811a5b01f4 | ||
| sha256 | fa480b199885433840abe9d506ccf32fc75fc1dd771695cce2dcb4f438a98d00 | ||
| ssdeep | 24576:KmUPjztESBDhakdbtl7vq6bknwKTaA9Cpr2r:KmUPv+eldbtl7i6FKeFpy | ||
| imphash | 4fff595be6c7200ce17d7102d4a2a4a9 | ||
| impfuzzy | 96:CfwKzbYBQ3uxrXItrMI9waeAuK+SkhMj/Q:03Cr4t39wEZ+3hMj/Q | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 41 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| notice | The binary likely contains encrypted or compressed data indicative of a packer |
| info | The executable contains unknown PE section names indicative of a packer (could be a false positive) |
| info | This executable has a PDB path |
Rules (8cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Generic_Malware_Zero | Generic Malware | binaries (upload) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (upload) |
| watch | Malicious_Packer_Zero | Malicious Packer | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| notice | anti_vm_detect | Possibly employs anti-virtualization techniques | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
cryptprimitives.dll
0x14004a1c0 ProcessPrng
api-ms-win-core-synch-l1-2-0.dll
0x14004a070 WakeByAddressAll
0x14004a078 WaitOnAddress
0x14004a080 WakeByAddressSingle
kernel32.dll
0x14004a1d0 UnhandledExceptionFilter
0x14004a1d8 LocalFree
0x14004a1e0 GetProcessTimes
0x14004a1e8 GetSystemTimeAsFileTime
0x14004a1f0 GetProcessHeap
0x14004a1f8 HeapFree
0x14004a200 OpenProcess
0x14004a208 GetCurrentThreadId
0x14004a210 GetSystemTimes
0x14004a218 GetProcessIoCounters
0x14004a220 SetUnhandledExceptionFilter
0x14004a228 HeapAlloc
0x14004a230 ReadProcessMemory
0x14004a238 GetSystemInfo
0x14004a240 GetComputerNameExW
0x14004a248 IsProcessorFeaturePresent
0x14004a250 RtlUnwindEx
0x14004a258 EncodePointer
0x14004a260 LoadLibraryExA
0x14004a268 FreeLibrary
0x14004a270 RaiseException
0x14004a278 GetLastError
0x14004a280 WaitForSingleObject
0x14004a288 GetCurrentProcessId
0x14004a290 DeleteCriticalSection
0x14004a298 FormatMessageW
0x14004a2a0 InitializeCriticalSectionAndSpinCount
0x14004a2a8 TlsAlloc
0x14004a2b0 AddVectoredExceptionHandler
0x14004a2b8 SetThreadStackGuarantee
0x14004a2c0 GetCurrentThread
0x14004a2c8 SwitchToThread
0x14004a2d0 CreateWaitableTimerExW
0x14004a2d8 SetWaitableTimer
0x14004a2e0 Sleep
0x14004a2e8 QueryPerformanceCounter
0x14004a2f0 RtlCaptureContext
0x14004a2f8 RtlLookupFunctionEntry
0x14004a300 RtlVirtualUnwind
0x14004a308 SetLastError
0x14004a310 GetCurrentDirectoryW
0x14004a318 GetEnvironmentVariableW
0x14004a320 TlsGetValue
0x14004a328 SetFileInformationByHandle
0x14004a330 TlsSetValue
0x14004a338 TlsFree
0x14004a340 LoadLibraryExW
0x14004a348 InitializeSListHead
0x14004a350 GlobalMemoryStatusEx
0x14004a358 VirtualQueryEx
0x14004a360 RtlPcToFileHeader
0x14004a368 GetStdHandle
0x14004a370 CreateFileW
0x14004a378 TerminateProcess
0x14004a380 GetSystemTimePreciseAsFileTime
0x14004a388 HeapReAlloc
0x14004a390 lstrlenW
0x14004a398 ReleaseMutex
0x14004a3a0 FindClose
0x14004a3a8 GetFileInformationByHandle
0x14004a3b0 GetFileInformationByHandleEx
0x14004a3b8 CloseHandle
0x14004a3c0 CreateDirectoryW
0x14004a3c8 FindFirstFileW
0x14004a3d0 CopyFileExW
0x14004a3d8 CheckRemoteDebuggerPresent
0x14004a3e0 IsDebuggerPresent
0x14004a3e8 GetConsoleMode
0x14004a3f0 VirtualFree
0x14004a3f8 VirtualAlloc
0x14004a400 GetModuleHandleW
0x14004a408 GetModuleFileNameW
0x14004a410 ExitProcess
0x14004a418 MultiByteToWideChar
0x14004a420 WriteConsoleW
0x14004a428 WideCharToMultiByte
0x14004a430 ReadConsoleW
0x14004a438 CreateThread
0x14004a440 GetFullPathNameW
0x14004a448 GetModuleHandleA
0x14004a450 VirtualProtectEx
0x14004a458 WriteProcessMemory
0x14004a460 GetCurrentProcess
0x14004a468 VirtualProtect
0x14004a470 WaitForSingleObjectEx
0x14004a478 CreateMutexA
0x14004a480 GetProcAddress
0x14004a488 LoadLibraryA
0x14004a490 K32GetPerformanceInfo
advapi32.dll
0x14004a000 IsValidSid
0x14004a008 AddAccessAllowedAce
0x14004a010 GetLengthSid
0x14004a018 CopySid
0x14004a020 OpenProcessToken
0x14004a028 SetSecurityInfo
0x14004a030 InitializeAcl
0x14004a038 RegQueryValueExW
0x14004a040 RegOpenKeyExW
0x14004a048 SystemFunction036
0x14004a050 RegSetValueExW
0x14004a058 RegCloseKey
0x14004a060 GetTokenInformation
crypt.dll
0x14004a1b0 BCryptGenRandom
pdh.dll
0x14004a4f8 PdhRemoveCounter
0x14004a500 PdhGetFormattedCounterValue
0x14004a508 PdhCloseQuery
0x14004a510 PdhCollectQueryData
0x14004a518 PdhOpenQueryA
0x14004a520 PdhAddEnglishCounterW
powrprof.dll
0x14004a530 CallNtPowerInformation
ntdll.dll
0x14004a4a0 RtlNtStatusToDosError
0x14004a4a8 RtlGetVersion
0x14004a4b0 NtQuerySystemInformation
0x14004a4b8 NtQueryInformationProcess
0x14004a4c0 NtReadFile
0x14004a4c8 NtWriteFile
psapi.dll
0x14004a540 GetProcessMemoryInfo
0x14004a548 GetModuleFileNameExW
shell32.dll
0x14004a558 CommandLineToArgvW
oleaut32.dll
0x14004a4d8 GetErrorInfo
0x14004a4e0 SysFreeString
0x14004a4e8 SysStringLen
api-ms-win-crt-heap-l1-1-0.dll
0x14004a090 _set_new_mode
0x14004a098 calloc
0x14004a0a0 free
0x14004a0a8 malloc
api-ms-win-crt-string-l1-1-0.dll
0x14004a190 wcslen
0x14004a198 strcpy_s
0x14004a1a0 wcsncmp
api-ms-win-crt-runtime-l1-1-0.dll
0x14004a0d8 _get_initial_narrow_environment
0x14004a0e0 __p___argv
0x14004a0e8 _cexit
0x14004a0f0 _c_exit
0x14004a0f8 _initialize_narrow_environment
0x14004a100 _register_thread_local_exe_atexit_callback
0x14004a108 _exit
0x14004a110 _set_app_type
0x14004a118 exit
0x14004a120 _initialize_onexit_table
0x14004a128 _register_onexit_function
0x14004a130 _crt_atexit
0x14004a138 terminate
0x14004a140 abort
0x14004a148 _seh_filter_exe
0x14004a150 _initterm_e
0x14004a158 _configure_narrow_argv
0x14004a160 _initterm
0x14004a168 __p___argc
api-ms-win-crt-math-l1-1-0.dll
0x14004a0c8 __setusermatherr
api-ms-win-crt-stdio-l1-1-0.dll
0x14004a178 __p__commode
0x14004a180 _set_fmode
api-ms-win-crt-locale-l1-1-0.dll
0x14004a0b8 _configthreadlocale
EAT(Export Address Table) is none
cryptprimitives.dll
0x14004a1c0 ProcessPrng
api-ms-win-core-synch-l1-2-0.dll
0x14004a070 WakeByAddressAll
0x14004a078 WaitOnAddress
0x14004a080 WakeByAddressSingle
kernel32.dll
0x14004a1d0 UnhandledExceptionFilter
0x14004a1d8 LocalFree
0x14004a1e0 GetProcessTimes
0x14004a1e8 GetSystemTimeAsFileTime
0x14004a1f0 GetProcessHeap
0x14004a1f8 HeapFree
0x14004a200 OpenProcess
0x14004a208 GetCurrentThreadId
0x14004a210 GetSystemTimes
0x14004a218 GetProcessIoCounters
0x14004a220 SetUnhandledExceptionFilter
0x14004a228 HeapAlloc
0x14004a230 ReadProcessMemory
0x14004a238 GetSystemInfo
0x14004a240 GetComputerNameExW
0x14004a248 IsProcessorFeaturePresent
0x14004a250 RtlUnwindEx
0x14004a258 EncodePointer
0x14004a260 LoadLibraryExA
0x14004a268 FreeLibrary
0x14004a270 RaiseException
0x14004a278 GetLastError
0x14004a280 WaitForSingleObject
0x14004a288 GetCurrentProcessId
0x14004a290 DeleteCriticalSection
0x14004a298 FormatMessageW
0x14004a2a0 InitializeCriticalSectionAndSpinCount
0x14004a2a8 TlsAlloc
0x14004a2b0 AddVectoredExceptionHandler
0x14004a2b8 SetThreadStackGuarantee
0x14004a2c0 GetCurrentThread
0x14004a2c8 SwitchToThread
0x14004a2d0 CreateWaitableTimerExW
0x14004a2d8 SetWaitableTimer
0x14004a2e0 Sleep
0x14004a2e8 QueryPerformanceCounter
0x14004a2f0 RtlCaptureContext
0x14004a2f8 RtlLookupFunctionEntry
0x14004a300 RtlVirtualUnwind
0x14004a308 SetLastError
0x14004a310 GetCurrentDirectoryW
0x14004a318 GetEnvironmentVariableW
0x14004a320 TlsGetValue
0x14004a328 SetFileInformationByHandle
0x14004a330 TlsSetValue
0x14004a338 TlsFree
0x14004a340 LoadLibraryExW
0x14004a348 InitializeSListHead
0x14004a350 GlobalMemoryStatusEx
0x14004a358 VirtualQueryEx
0x14004a360 RtlPcToFileHeader
0x14004a368 GetStdHandle
0x14004a370 CreateFileW
0x14004a378 TerminateProcess
0x14004a380 GetSystemTimePreciseAsFileTime
0x14004a388 HeapReAlloc
0x14004a390 lstrlenW
0x14004a398 ReleaseMutex
0x14004a3a0 FindClose
0x14004a3a8 GetFileInformationByHandle
0x14004a3b0 GetFileInformationByHandleEx
0x14004a3b8 CloseHandle
0x14004a3c0 CreateDirectoryW
0x14004a3c8 FindFirstFileW
0x14004a3d0 CopyFileExW
0x14004a3d8 CheckRemoteDebuggerPresent
0x14004a3e0 IsDebuggerPresent
0x14004a3e8 GetConsoleMode
0x14004a3f0 VirtualFree
0x14004a3f8 VirtualAlloc
0x14004a400 GetModuleHandleW
0x14004a408 GetModuleFileNameW
0x14004a410 ExitProcess
0x14004a418 MultiByteToWideChar
0x14004a420 WriteConsoleW
0x14004a428 WideCharToMultiByte
0x14004a430 ReadConsoleW
0x14004a438 CreateThread
0x14004a440 GetFullPathNameW
0x14004a448 GetModuleHandleA
0x14004a450 VirtualProtectEx
0x14004a458 WriteProcessMemory
0x14004a460 GetCurrentProcess
0x14004a468 VirtualProtect
0x14004a470 WaitForSingleObjectEx
0x14004a478 CreateMutexA
0x14004a480 GetProcAddress
0x14004a488 LoadLibraryA
0x14004a490 K32GetPerformanceInfo
advapi32.dll
0x14004a000 IsValidSid
0x14004a008 AddAccessAllowedAce
0x14004a010 GetLengthSid
0x14004a018 CopySid
0x14004a020 OpenProcessToken
0x14004a028 SetSecurityInfo
0x14004a030 InitializeAcl
0x14004a038 RegQueryValueExW
0x14004a040 RegOpenKeyExW
0x14004a048 SystemFunction036
0x14004a050 RegSetValueExW
0x14004a058 RegCloseKey
0x14004a060 GetTokenInformation
crypt.dll
0x14004a1b0 BCryptGenRandom
pdh.dll
0x14004a4f8 PdhRemoveCounter
0x14004a500 PdhGetFormattedCounterValue
0x14004a508 PdhCloseQuery
0x14004a510 PdhCollectQueryData
0x14004a518 PdhOpenQueryA
0x14004a520 PdhAddEnglishCounterW
powrprof.dll
0x14004a530 CallNtPowerInformation
ntdll.dll
0x14004a4a0 RtlNtStatusToDosError
0x14004a4a8 RtlGetVersion
0x14004a4b0 NtQuerySystemInformation
0x14004a4b8 NtQueryInformationProcess
0x14004a4c0 NtReadFile
0x14004a4c8 NtWriteFile
psapi.dll
0x14004a540 GetProcessMemoryInfo
0x14004a548 GetModuleFileNameExW
shell32.dll
0x14004a558 CommandLineToArgvW
oleaut32.dll
0x14004a4d8 GetErrorInfo
0x14004a4e0 SysFreeString
0x14004a4e8 SysStringLen
api-ms-win-crt-heap-l1-1-0.dll
0x14004a090 _set_new_mode
0x14004a098 calloc
0x14004a0a0 free
0x14004a0a8 malloc
api-ms-win-crt-string-l1-1-0.dll
0x14004a190 wcslen
0x14004a198 strcpy_s
0x14004a1a0 wcsncmp
api-ms-win-crt-runtime-l1-1-0.dll
0x14004a0d8 _get_initial_narrow_environment
0x14004a0e0 __p___argv
0x14004a0e8 _cexit
0x14004a0f0 _c_exit
0x14004a0f8 _initialize_narrow_environment
0x14004a100 _register_thread_local_exe_atexit_callback
0x14004a108 _exit
0x14004a110 _set_app_type
0x14004a118 exit
0x14004a120 _initialize_onexit_table
0x14004a128 _register_onexit_function
0x14004a130 _crt_atexit
0x14004a138 terminate
0x14004a140 abort
0x14004a148 _seh_filter_exe
0x14004a150 _initterm_e
0x14004a158 _configure_narrow_argv
0x14004a160 _initterm
0x14004a168 __p___argc
api-ms-win-crt-math-l1-1-0.dll
0x14004a0c8 __setusermatherr
api-ms-win-crt-stdio-l1-1-0.dll
0x14004a178 __p__commode
0x14004a180 _set_fmode
api-ms-win-crt-locale-l1-1-0.dll
0x14004a0b8 _configthreadlocale
EAT(Export Address Table) is none