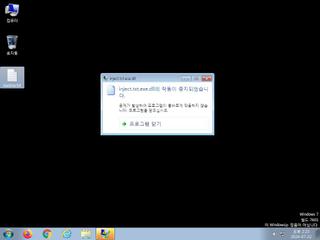
ScreenShot
| Created | 2024.07.22 14:26 | Machine | s1_win7_x6401 |
| Filename | inject.txt.exe | ||
| Type | PE32+ executable (DLL) (console) x86-64, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 53 detected (AIDetectMalware, Marte, malicious, high confidence, score, Artemis, Unsafe, Rozena, Vm7w, Meterpreter, MetasploitEncod, CLOUD, xxkgf, SWRORT, YXEGUZ, Detected, ai score=89, ABTrojan, DITB, GdSda, Gencirc, confidence, 100%) | ||
| md5 | 03bed904291f531fc5381307e361b70f | ||
| sha256 | 15665af2e4efa5f4f5a25bdb36090961b92818d01f40f90b9eaa4cc5a97902e3 | ||
| ssdeep | 1536:S8yZzfkJ6CQ1bvbrrySCIiaC6yiJikvEDSbvz4+zeGI8ZZwZdXhXOkUWTohlqeCg:BEzsqxE2t0puoC | ||
| imphash | 6490015bd77f7aa9aab54479cf5a74a0 | ||
| impfuzzy | 12:YRJRibJ2cDzARZqRLAEqVlaRa91Kq0iZn:8fiFlDIcLslP91PLZn | ||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| danger | Connects to IP addresses that are no longer responding to requests (legitimate services will remain up-and-running usually) |
| danger | File has been identified by 53 AntiVirus engines on VirusTotal as malicious |
| watch | Communicates with host for which no DNS query was performed |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| info | One or more processes crashed |
Rules (3cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | IsDLL | (no description) | binaries (upload) |
| info | IsPE64 | (no description) | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x1fe54a124 DeleteCriticalSection
0x1fe54a12c EnterCriticalSection
0x1fe54a134 FreeLibrary
0x1fe54a13c GetLastError
0x1fe54a144 GetModuleHandleA
0x1fe54a14c GetProcAddress
0x1fe54a154 InitializeCriticalSection
0x1fe54a15c LeaveCriticalSection
0x1fe54a164 LoadLibraryA
0x1fe54a16c Sleep
0x1fe54a174 TlsGetValue
0x1fe54a17c VirtualAlloc
0x1fe54a184 VirtualProtect
0x1fe54a18c VirtualQuery
msvcrt.dll
0x1fe54a19c __iob_func
0x1fe54a1a4 _amsg_exit
0x1fe54a1ac _initterm
0x1fe54a1b4 _lock
0x1fe54a1bc _unlock
0x1fe54a1c4 abort
0x1fe54a1cc calloc
0x1fe54a1d4 free
0x1fe54a1dc fwrite
0x1fe54a1e4 realloc
0x1fe54a1ec strlen
0x1fe54a1f4 strncmp
0x1fe54a1fc vfprintf
EAT(Export Address Table) Library
0x1fe543020 buf
KERNEL32.dll
0x1fe54a124 DeleteCriticalSection
0x1fe54a12c EnterCriticalSection
0x1fe54a134 FreeLibrary
0x1fe54a13c GetLastError
0x1fe54a144 GetModuleHandleA
0x1fe54a14c GetProcAddress
0x1fe54a154 InitializeCriticalSection
0x1fe54a15c LeaveCriticalSection
0x1fe54a164 LoadLibraryA
0x1fe54a16c Sleep
0x1fe54a174 TlsGetValue
0x1fe54a17c VirtualAlloc
0x1fe54a184 VirtualProtect
0x1fe54a18c VirtualQuery
msvcrt.dll
0x1fe54a19c __iob_func
0x1fe54a1a4 _amsg_exit
0x1fe54a1ac _initterm
0x1fe54a1b4 _lock
0x1fe54a1bc _unlock
0x1fe54a1c4 abort
0x1fe54a1cc calloc
0x1fe54a1d4 free
0x1fe54a1dc fwrite
0x1fe54a1e4 realloc
0x1fe54a1ec strlen
0x1fe54a1f4 strncmp
0x1fe54a1fc vfprintf
EAT(Export Address Table) Library
0x1fe543020 buf