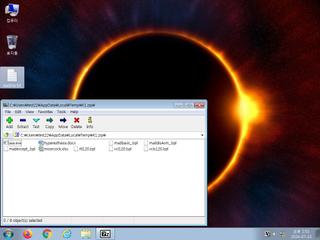
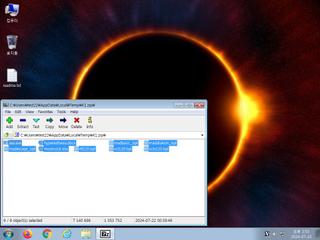
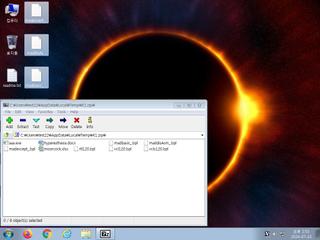
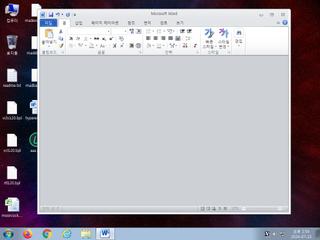
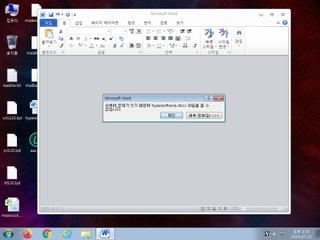
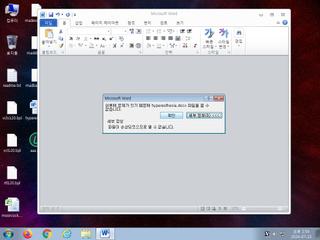
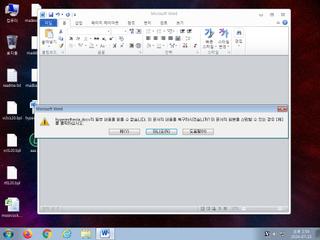
ScreenShot
| Created | 2024.07.23 14:56 | Machine | s1_win7_x6402 |
| Filename | K1.zip | ||
| Type | Zip archive data, at least v2.0 to extract | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 2 detected (ccmw) | ||
| md5 | eb834c6eb71e2a950f9123b506ab4763 | ||
| sha256 | 016b443391531dc4a9bac3127fe82d6149b14ee529ff448de8d60c9868b74602 | ||
| ssdeep | 49152:lm0aitd+JLyeh79YQ+7svv3ujDg8tozVUaIiArjdaCbkq6CYKW7BSIV0:g0Z+td91IsHCdSz+pifCbkIeBFV0 | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (5cnts)
| Level | Description |
|---|---|
| notice | File has been identified by 2 AntiVirus engines on VirusTotal as malicious |
| notice | HTTP traffic contains suspicious features which may be indicative of malware related traffic |
| notice | Performs some HTTP requests |
| notice | Resolves a suspicious Top Level Domain (TLD) |
| notice | Sends data using the HTTP POST Method |
Rules (1cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| info | zip_file_format | ZIP file format | binaries (upload) |
Suricata ids
ET DROP Spamhaus DROP Listed Traffic Inbound group 31
ET MALWARE Cryptbot CnC DGA Domain (eight8)
ET DNS Query to a *.top domain - Likely Hostile
ET MALWARE Win32/Cryptbotv2 CnC Activity (POST) M4
ET INFO HTTP Request to a *.top domain
ET MALWARE Cryptbot CnC DGA Domain (eight8)
ET DNS Query to a *.top domain - Likely Hostile
ET MALWARE Win32/Cryptbotv2 CnC Activity (POST) M4
ET INFO HTTP Request to a *.top domain