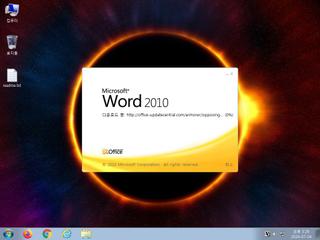
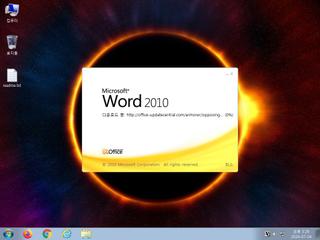
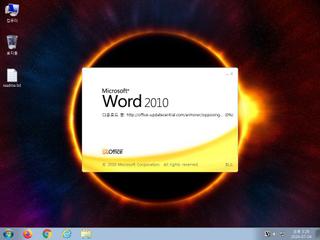
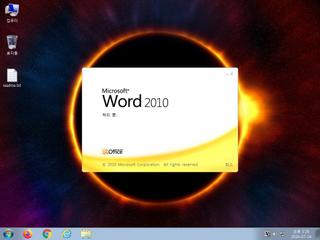
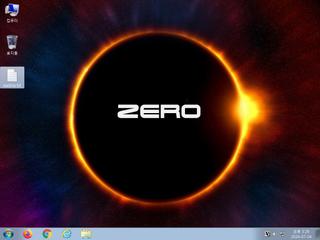
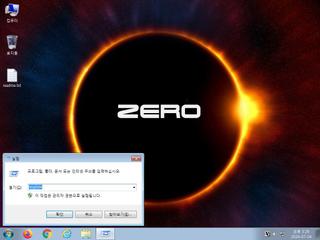
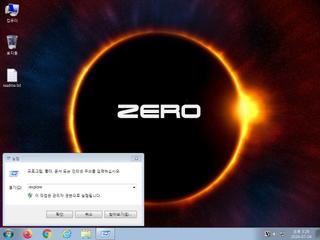
ScreenShot
| Created | 2024.07.24 15:30 | Machine | s1_win7_x6402 |
| Filename | scan0001.doc | ||
| Type | Zip archive data, at least v2.0 to extract | ||
| AI Score | Not founds | Behavior Score |
|
| ZERO API | file : clean | ||
| VT API (file) | 7 detected (Malicious, score, CVE-2017-0199, equmby, W2000, uppyf, 4PF354, Probably Heur, W97OleLink) | ||
| md5 | e96e2ed88e2f2fb80d02e7cd99a1420d | ||
| sha256 | dc747e9846ecb4c232b2e36007abdadc6d608272a8ea4305c89931ed0979944b | ||
| ssdeep | 768:3Tkbd5YLRTk1RqpsWOBFI7j5jJ3OGMXSdCoa3UcDeSHNLQgwXt1KtJBZUrAK1UO0:3TkbIVk1YTT/iR3UEeQ7ot1K1Zeu9z | ||
| imphash | |||
| impfuzzy | |||
Network IP location
Signature (9cnts)
| Level | Description |
|---|---|
| watch | Communicates with host for which no DNS query was performed |
| notice | Allocates read-write-execute memory (usually to unpack itself) |
| notice | Creates (office) documents on the filesystem |
| notice | Creates executable files on the filesystem |
| notice | Creates hidden or system file |
| notice | Drops an executable to the user AppData folder |
| notice | File has been identified by 7 AntiVirus engines on VirusTotal as malicious |
| notice | One or more potentially interesting buffers were extracted |
| notice | Performs some HTTP requests |
Rules (12cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| warning | Doc_XML_Downloader | Detect a MS Office document with embedded XML Downloader | binaries (upload) |
| warning | Generic_Malware_Zero | Generic Malware | binaries (download) |
| watch | Malicious_Library_Zero | Malicious_Library | binaries (download) |
| watch | UPX_Zero | UPX packed file | binaries (download) |
| info | docx | Word 2007 file format detection | binaries (upload) |
| info | Is_DotNET_DLL | (no description) | binaries (download) |
| info | IsDLL | (no description) | binaries (download) |
| info | IsPE32 | (no description) | binaries (download) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (download) |
| info | PE_Header_Zero | PE File Signature | binaries (download) |
| info | Rich_Text_Format_Zero | Rich Text Format Signature Zero | binaries (download) |
| info | zip_file_format | ZIP file format | binaries (upload) |
Network (11cnts) ?
Suricata ids
SSLBL: Malicious JA3 SSL-Client Fingerprint detected (Tofsee)
ET DROP Spamhaus DROP Listed Traffic Inbound group 15
ET INFO TLS Handshake Failure
ET USER_AGENTS Microsoft Office Existence Discovery User-Agent
ET WEB_CLIENT DRIVEBY GENERIC ShellExecute in Hex No Seps
ET DROP Spamhaus DROP Listed Traffic Inbound group 15
ET INFO TLS Handshake Failure
ET USER_AGENTS Microsoft Office Existence Discovery User-Agent
ET WEB_CLIENT DRIVEBY GENERIC ShellExecute in Hex No Seps