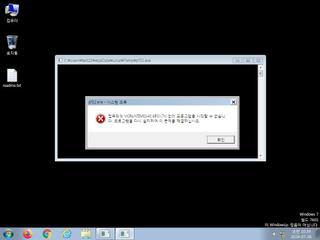
ScreenShot
| Created | 2024.07.26 10:56 | Machine | s1_win7_x6401 |
| Filename | pf32.exe | ||
| Type | PE32 executable (console) Intel 80386, for MS Windows | ||
| AI Score |
|
Behavior Score |
|
| ZERO API | file : malware | ||
| VT API (file) | 58 detected (AIDetectMalware, PrintSpoofer, Windows, FakePipe, Malicious, score, Unsafe, Hacktool, Vjqs, Attribute, HighConfidence, GenericRXAA, ExploitX, Printer, dPySkdZtye, njyhi, Tool, R002C0GL523, Static AI, Suspicious PE, Detected, ai score=81, Malware@#2aytu59dcgnz, Skeeyah, ABTrojan, RRGN, R358767, GdSda, Gencirc, LoXxUTKSAHg, susgen, grayware, confidence, 100%) | ||
| md5 | 2a74db17b50025d13a63d947d8a8f828 | ||
| sha256 | 47c9eff8142490a2c341701aab7aaebc355eed1540eed534a8317dd1e65614b2 | ||
| ssdeep | 384:UnalV17j7+ejwtdaNVOpAdoahiqjOOhLSqDtd7+SlopNAL:ky17j7WdaNosdKnpNAL | ||
| imphash | c8bf48e03c8c37268b47f1d2591aa6fd | ||
| impfuzzy | 48:58veLNH2o1uj0V+JEkuTCNi0LSQSwtZq+9qJUxBSA:58veLx2WMomELCNd94yV | ||
Network IP location
Signature (1cnts)
| Level | Description |
|---|---|
| danger | File has been identified by 58 AntiVirus engines on VirusTotal as malicious |
Rules (5cnts)
| Level | Name | Description | Collection |
|---|---|---|---|
| watch | Antivirus | Contains references to security software | binaries (upload) |
| watch | UPX_Zero | UPX packed file | binaries (upload) |
| info | IsPE32 | (no description) | binaries (upload) |
| info | OS_Processor_Check_Zero | OS Processor Check | binaries (upload) |
| info | PE_Header_Zero | PE File Signature | binaries (upload) |
Network (0cnts) ?
| Request | CC | ASN Co | IP4 | Rule ? | ZERO ? |
|---|
Suricata ids
PE API
IAT(Import Address Table) Library
KERNEL32.dll
0x403038 ConnectNamedPipe
0x40303c GetComputerNameW
0x403040 CreateThread
0x403044 CloseHandle
0x403048 GetCurrentThread
0x40304c GetLastError
0x403050 CreateEventW
0x403054 GetSystemDirectoryW
0x403058 WaitForSingleObject
0x40305c CreateNamedPipeW
0x403060 GetCurrentProcess
0x403064 IsDebuggerPresent
0x403068 InitializeSListHead
0x40306c GetSystemTimeAsFileTime
0x403070 GetCurrentThreadId
0x403074 GetCurrentProcessId
0x403078 QueryPerformanceCounter
0x40307c IsProcessorFeaturePresent
0x403080 TerminateProcess
0x403084 SetUnhandledExceptionFilter
0x403088 UnhandledExceptionFilter
0x40308c GetModuleHandleW
ADVAPI32.dll
0x403000 OpenThreadToken
0x403004 AdjustTokenPrivileges
0x403008 RevertToSelf
0x40300c SetTokenInformation
0x403010 LookupPrivilegeNameW
0x403014 CreateProcessWithTokenW
0x403018 OpenProcessToken
0x40301c ImpersonateNamedPipeClient
0x403020 InitializeSecurityDescriptor
0x403024 CreateProcessAsUserW
0x403028 ConvertStringSecurityDescriptorToSecurityDescriptorW
0x40302c DuplicateTokenEx
0x403030 GetTokenInformation
RPCRT4.dll
0x403094 UuidCreate
0x403098 RpcBindingFree
0x40309c RpcStringFreeW
0x4030a0 RpcStringBindingComposeW
0x4030a4 UuidToStringW
0x4030a8 RpcBindingFromStringBindingW
0x4030ac NdrClientCall2
USERENV.dll
0x4030b4 CreateEnvironmentBlock
0x4030b8 DestroyEnvironmentBlock
VCRUNTIME140.dll
0x4030c0 memset
0x4030c4 __current_exception_context
0x4030c8 __current_exception
0x4030cc _except_handler4_common
api-ms-win-crt-stdio-l1-1-0.dll
0x40314c __stdio_common_vfwprintf
0x403150 __p__commode
0x403154 _set_fmode
0x403158 __acrt_iob_func
0x40315c __stdio_common_vswprintf
0x403160 fflush
api-ms-win-crt-string-l1-1-0.dll
0x403168 _wcsicmp
api-ms-win-crt-convert-l1-1-0.dll
0x4030d4 wcstoul
api-ms-win-crt-heap-l1-1-0.dll
0x4030dc malloc
0x4030e0 _set_new_mode
0x4030e4 free
api-ms-win-crt-runtime-l1-1-0.dll
0x4030fc _c_exit
0x403100 _register_thread_local_exe_atexit_callback
0x403104 __p___argc
0x403108 _initterm_e
0x40310c _set_app_type
0x403110 _cexit
0x403114 _seh_filter_exe
0x403118 _register_onexit_function
0x40311c _crt_atexit
0x403120 _controlfp_s
0x403124 terminate
0x403128 _configure_wide_argv
0x40312c _initterm
0x403130 _exit
0x403134 _initialize_wide_environment
0x403138 __p___wargv
0x40313c _initialize_onexit_table
0x403140 _get_initial_wide_environment
0x403144 exit
api-ms-win-crt-math-l1-1-0.dll
0x4030f4 __setusermatherr
api-ms-win-crt-locale-l1-1-0.dll
0x4030ec _configthreadlocale
EAT(Export Address Table) is none
KERNEL32.dll
0x403038 ConnectNamedPipe
0x40303c GetComputerNameW
0x403040 CreateThread
0x403044 CloseHandle
0x403048 GetCurrentThread
0x40304c GetLastError
0x403050 CreateEventW
0x403054 GetSystemDirectoryW
0x403058 WaitForSingleObject
0x40305c CreateNamedPipeW
0x403060 GetCurrentProcess
0x403064 IsDebuggerPresent
0x403068 InitializeSListHead
0x40306c GetSystemTimeAsFileTime
0x403070 GetCurrentThreadId
0x403074 GetCurrentProcessId
0x403078 QueryPerformanceCounter
0x40307c IsProcessorFeaturePresent
0x403080 TerminateProcess
0x403084 SetUnhandledExceptionFilter
0x403088 UnhandledExceptionFilter
0x40308c GetModuleHandleW
ADVAPI32.dll
0x403000 OpenThreadToken
0x403004 AdjustTokenPrivileges
0x403008 RevertToSelf
0x40300c SetTokenInformation
0x403010 LookupPrivilegeNameW
0x403014 CreateProcessWithTokenW
0x403018 OpenProcessToken
0x40301c ImpersonateNamedPipeClient
0x403020 InitializeSecurityDescriptor
0x403024 CreateProcessAsUserW
0x403028 ConvertStringSecurityDescriptorToSecurityDescriptorW
0x40302c DuplicateTokenEx
0x403030 GetTokenInformation
RPCRT4.dll
0x403094 UuidCreate
0x403098 RpcBindingFree
0x40309c RpcStringFreeW
0x4030a0 RpcStringBindingComposeW
0x4030a4 UuidToStringW
0x4030a8 RpcBindingFromStringBindingW
0x4030ac NdrClientCall2
USERENV.dll
0x4030b4 CreateEnvironmentBlock
0x4030b8 DestroyEnvironmentBlock
VCRUNTIME140.dll
0x4030c0 memset
0x4030c4 __current_exception_context
0x4030c8 __current_exception
0x4030cc _except_handler4_common
api-ms-win-crt-stdio-l1-1-0.dll
0x40314c __stdio_common_vfwprintf
0x403150 __p__commode
0x403154 _set_fmode
0x403158 __acrt_iob_func
0x40315c __stdio_common_vswprintf
0x403160 fflush
api-ms-win-crt-string-l1-1-0.dll
0x403168 _wcsicmp
api-ms-win-crt-convert-l1-1-0.dll
0x4030d4 wcstoul
api-ms-win-crt-heap-l1-1-0.dll
0x4030dc malloc
0x4030e0 _set_new_mode
0x4030e4 free
api-ms-win-crt-runtime-l1-1-0.dll
0x4030fc _c_exit
0x403100 _register_thread_local_exe_atexit_callback
0x403104 __p___argc
0x403108 _initterm_e
0x40310c _set_app_type
0x403110 _cexit
0x403114 _seh_filter_exe
0x403118 _register_onexit_function
0x40311c _crt_atexit
0x403120 _controlfp_s
0x403124 terminate
0x403128 _configure_wide_argv
0x40312c _initterm
0x403130 _exit
0x403134 _initialize_wide_environment
0x403138 __p___wargv
0x40313c _initialize_onexit_table
0x403140 _get_initial_wide_environment
0x403144 exit
api-ms-win-crt-math-l1-1-0.dll
0x4030f4 __setusermatherr
api-ms-win-crt-locale-l1-1-0.dll
0x4030ec _configthreadlocale
EAT(Export Address Table) is none